Layer 6 Presentation Layer
De/Encryption, Encoding, String representation
The presentation layer (data presentation layer, data provision level) sets the system-dependent representation of the data (for example, ASCII, EBCDIC) into an independent form, enabling the syntactically correct data exchange between different systems. Also, functions such as data compression and encryption are guaranteed that data to be sent by the application layer of a system that can be read by the application layer of another system to the layer 6. The presentation layer. If necessary, the presentation layer acts as a translator between different data formats, by making an understandable for both systems data format, the ASN.1 (Abstract Syntax Notation One) used.

OSI Layer 6 - Presentation Layer
The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file. The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. "thisisastring\0"). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest. Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer. Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted. In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer. Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer. In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format. Wikipedia
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
The Presentation OSI Layer is usually composed of 2 sublayers that are:
CASE common application service element
| ACSE | Association Control Service Element |
|---|---|
| ROSE | Remote Operation Service Element |
| CCR | Commitment Concurrency and Recovery |
| RTSE | Reliable Transfer Service Element |
SASE specific application service element
| FTAM | File Transfer, Access and Manager |
|---|---|
| VT | Virtual Terminal |
| MOTIS | Message Oriented Text Interchange Standard |
| CMIP | Common Management Information Protocol |
| JTM | Job Transfer and Manipulation |
| MMS | Manufacturing Messaging Service |
| RDA | Remote Database Access |
| DTP | Distributed Transaction Processing |
Layer 7 Application Layer
Layer 6 presentation layer, layer 5 session layer, layer 4 transport layer, layer 3 network layer, layer 2 data link layer, layer 1 physical layer.
The OSI Model’s 7 Layers, Explained
The seven layers in the Open Systems Interconnection (OSI) model each serve a specific function and work together to create an efficient network communication system.
The Open Systems Interconnection (OSI) model is a framework in network communication that simplifies complex network interactions into a structured format.
What Is the OSI Model?
The Open Systems Interconnection model is a framework in network communication designed to simplify complex network interactions into a structured format. This architecture has seven layers, each of which serves a specific function. All seven layers work together to create a robust and efficient network communication system.
Each of its seven layers has a distinct role, ensuring efficient data transfer from one device to another . The OSI model is essential for understanding how data is transmitted in a network and is also a practical guide for network protocol design and problem solving.
learn more about cybersecurity An Introduction to Microsegmentation in Network Security
The OSI model, developed by the International Organization for Standardization , outlines the essential functions of networking and telecommunications systems for practical application. It plays a crucial role in telecommunications, where vendors use it to define the features and capabilities of their products and services.
This approach allows for a detailed explanation of different aspects of network communication, including transport protocols, addressing schemes and data packaging methods. As a result, the OSI model resolves the complexities of network communication and fosters a more integrated and coherent digital world .
The 7 Layers of the OSI Model
Each layer of the OSI model serves a specific function, yet they work in harmony to create a robust and efficient network communication system. Understanding these layers provides valuable insights into the complexities of network design and operation, showcasing the intricate nature of modern digital communication.
Layer 7: Application Layer
Functionality: The Application Layer is the closest to the end user. It facilitates user interaction with networked systems, providing interfaces and protocols for web browsers, email clients and other applications.
Key protocols: Protocols like HTTP, FTP and SMTP operate at this layer, enabling services such as web browsing, file transfers and email communications.
Layer 6: Presentation Layer
Role: The Presentation Layer acts as a translator, converting data formats from the application layer into a network-compatible format and vice versa. It ensures that data sent from one system is readable by another.
Data formatting: This layer is responsible for data encryption and compression, playing a significant role in maintaining data privacy and efficient transmission.
Layer 5: Session Layer
Managing sessions: It establishes, manages and terminates sessions between applications. This layer ensures that sessions are maintained for the duration of the communication.
Coordination: The Session Layer coordinates communication between systems, managing dialogues and synchronizing data exchange.
Layer 4: Transport Layer
Data segmentation and control: The Transport Layer is crucial for segmenting data into smaller packets. It ensures end-to-end data integrity and delivery, managing flow control, error correction and sequencing.
Protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are key protocols in this layer, differing in their approach to data transmission.
Layer 3: Network Layer
Routing and addressing: This layer is responsible for logical addressing and routing data packets across different networks. It determines the best path for data to travel from source to destination.
Internet protocol: The Internet Protocol (IP), fundamental for internet data exchange, operates at this layer.
Layer 2: Data Link Layer
Framing and MAC addressing: The Data Link Layer frames data into packets. It handles physical addressing through MAC addresses, ensuring that data is directed to the correct hardware.
Error detection: This layer is also involved in error detection and handling, improving overall data transmission reliability.
Layer 1: Physical Layer
Physical transmission: The Physical Layer deals with the physical aspects of data transmission, including cable types, electrical signals and data rates.
Hardware components: It involves hardware components like cables, switches and network interface cards, forming the foundation of network communication.
How Data Flows in the OSI Model
Understanding this data flow process is crucial for professionals, as it aids in diagnosing and troubleshooting network issues, designing efficient network solutions and ensuring robust data security and management.
Encapsulation Process
When data is sent, it begins at the Application Layer and moves down through the layers. At each stage, it is encapsulated with the necessary headers, trailers, and other control information relevant to that layer. For instance, at the Transport Layer, data is segmented and encapsulated with port numbers, while at the Network Layer, IP addresses are added.
Each layer plays a role in preparing the data for transmission. The Presentation Layer may encrypt the data for security, while the Data Link Layer ensures it is formatted into frames suitable for physical transmission.
Data Transmission Across the Network
The Physical Layer transmits the raw bits over a physical medium, such as a cable or wireless network. This transmission is the actual movement of data across the network. In cases where data must move across different networks, the Network Layer’s routing functionalities become crucial. It ensures that data packets find the most efficient path to their destination.
Decapsulation Process
Upon reaching the destination, the data moves up the OSI model, with each layer removing its respective encapsulation. The Data Link Layer, for instance, removes framing, and the Transport Layer checks for transmission errors and reassembles the data segments. Once the data reaches the Application Layer, it is in its original format and ready to be used by the receiving application, whether it’s an email client, a web browser or any other networked software.
Seamless Data Flow
The OSI model ensures that each layer only communicates with its immediate upper and lower layers, creating a seamless flow. This layered approach means changes in one layer’s protocols or functionalities can occur without disrupting the entire network.
OSI Model Advantages
The OSI model is a cornerstone in network architecture for several reasons:
Simplification of network design
The OSI model’s layered approach breaks down complex network processes, making design and operation more manageable. Each layer focuses on a specific aspect of communication, allowing for independent development and easier troubleshooting.
Standardization and interoperability
It establishes universal standards for network communication, enabling different technologies to interact seamlessly. This interoperability is crucial for the efficient functioning of diverse network devices and applications.
Flexibility and Scalability
Adaptable to technological advancements, the OSI model allows individual layers to evolve without overhauling the entire system. This scalability makes it suitable for various network sizes and types.
Enhanced Security
Security measures are integrated at multiple layers, providing a robust defense against threats. Each layer can address specific security concerns, leading to comprehensive network protection.
Real-World Applications of the OSI Model
The OSI model’s influence extends well beyond theoretical concepts, playing a crucial role in various practical aspects of networking:
Network Design and Protocol Development
Network professionals use the OSI model as a blueprint for structuring and developing robust networks. It guides the creation of new protocols, ensuring seamless integration and functionality across different network layers.
Efficient Troubleshooting and Management
In troubleshooting, the OSI model provides a systematic approach for identifying issues, from physical connectivity to application-level errors. It also aids in network maintenance and performance optimization, addressing each layer to enhance overall efficiency.
Cybersecurity Strategy
The model is foundational in crafting layered security strategies . By implementing security measures at different layers, it offers comprehensive protection against various cyber threats. Understanding the OSI layers is key in detecting and mitigating attacks targeting specific network segments.
Educational and Training Tool
It serves as an essential framework in networking education, helping students and professionals alike understand complex network operations. The OSI model is a cornerstone in training programs , emphasizing the intricacies of network architecture and security.
safety first When and How to Run a Phishing Simulation
OSI Model vs. TCP/IP Model
While the OSI model offers a detailed conceptual framework, the TCP/IP model is recognized for its practical application in today’s internet-driven world.
Structural Differences
OSI model : Introduced as a comprehensive, protocol-independent framework, the OSI model details seven distinct layers, offering a more granular approach to network communication.
TCP/IP model : Developed earlier by the U.S. Department of Defense, the TCP/IP model consists of four layers (Application, Transport, Internet and Network Access), combining certain OSI layers.
Theoretical vs. Practical Approach
OSI model : Developed as a theoretical and universal networking model, it’s used more for educational purposes to explain how networks operate.
TCP/IP model : This model is designed around specific standard protocols, focusing on solving practical communication issues. It leaves sequencing and acknowledgment functions to the transport layer, differing from the OSI approach.
Adoption and Use
OSI model: While not widely implemented in its entirety, the OSI model’s clear layer separation is influential in protocol design and network education; simpler applications in the OSI framework may not utilize all seven layers, with only the first three layers (Physical, Data Link, and Network) being mandatory for basic data communication.
TCP/IP model : The dominant model used in most network architectures today, especially in internet-related communications. In TCP/IP, most applications engage all layers for communication.
Frequently Asked Questions
Why is the osi model important.
The OSI model is crucial for standardizing network communication and ensuring interoperability between various devices and systems. It simplifies network design and troubleshooting and serves as a fundamental educational tool in networking.
What are the 7 layers of the OSI model?
Layer 1: Physical Layer — Transmits raw data.
Layer 2: Data Link Layer — Manages direct links and framing.
Layer 3: Network Layer — Handles addressing and routing.
Layer 4: Transport Layer — Ensures reliable data transfer.
Layer 5: Session Layer — Manages connections.
Layer 6: Presentation Layer — Translates data formats.
Layer 7: Application Layer — Interfaces with applications.
Recent Network Security Articles

How to Create a Modern Web Application Architecture?

Creating a modern web application architecture is crucial for businesses to remain competitive and meet the growing demands of users. A well-designed architecture ensures flexibility, scalability, maintainability, security, and high performance.
As an experienced web development company, Integrio will provide an overview of the architecture components, layers, types, and best practices. We will also share success stories from clients like 123Signup, Volo Innovations, and CareOregon.
What Is Web Application Architecture?
Web application architecture refers to the structural design and organization of the client-side and server-side components. It typically comprises multiple layers that work together to provide a complete solution to the end users.
While constructing a modern web application architecture, consider scalability, reliability, security, and maintainability.
How Do Modern Web Applications Work?
We prepared a simplified description of how web solutions typically work:
The user opens a web browser and enters the URL for the web application.
The browser sends an HTTP request to the server hosting the web application.
The server receives the request and uses the appropriate server-side component to process the request.
The server-side component retrieves data from a database and generates an appropriate response.
The response is sent back to the browser as an HTTP response.
The browser receives the response and uses the appropriate client-side components (such as HTML, CSS, and JavaScript) to render the response as a user interface.
The user interacts with the user interface, triggering additional HTTP requests to the server.
The server receives each request and processes it using the appropriate server-side component.
The server generates an appropriate response and sends it back to the browser as an HTTP response.
The browser receives the response and updates the user interface accordingly.
The process continues until the user completes their web application task.
Components of Web Application Architecture
The web application has two sides — front-end and back-end.
The front-end is part of a web application that ' s visible and accessible to the user and includes user interface (UI) elements, such as buttons, forms, and menus.
The back-end is part of a web application that runs on the server. It typically consists of the server and the database.

Let ' s discuss the components of modern web application architecture and their functions.
User Interface (UI)
The UI is the web application component that interacts with the user, displays the content, and receives input. It can be implemented using various technologies, such as:
HTML — to structure the web page ' s content
CSS — to style the page and make it visually appealing
JavaScript — to add interactivity and functionality to the UI
Good UI design involves understanding the user ' s needs and preferences, organizing the UI elements logically and intuitively, and making the application easy to use and navigate.
The web server handles incoming client requests and sends back responses. It hosts the web application and serves HTML pages, images, and other static content. It also manages connections, sessions, and cookies and implements security mechanisms, such as SSL/TLS encryption, to protect against attacks.
Popular web servers: Apache, Nginx, Microsoft IIS, and Google Web Server.
Database Server
The database server stores and manages data for the web application. Its functions include creating, updating, deleting, and querying data, ensuring its integrity and security.
To improve the performance of web applications, database servers use caching and indexing techniques. They also implement backup and recovery mechanisms to protect against data loss and ensure its availability in the event of a failure.
Popular database servers: MySQL, Oracle, and MongoDB.
The Domain Name System (DNS) is a critical component of web application architecture. It translates human-readable domain names (such as www.example.com) into IP addresses (such as 192.0.2.1) that computers can understand.
Its main function is to provide a way for users to access web resources using easy-to-remember domain names while facilitating communication between web servers and clients.
Messaging Middleware
Messaging middleware enables communication between different software components or systems, allowing them to exchange messages and data with each other. It can handle a variety of communication patterns, such as point-to-point, publish-subscribe, and request-response.
Popular messaging middleware solutions: Apache Kafka, RabbitMQ, and ActiveMQ.
Load Balancer
A load balancer distributes incoming traffic across multiple servers to optimize resource utilization, maximize throughput, and minimize response time. As a result, it improves the performance and reliability of the web application.
Popular load balancers: HAProxy, NGINX, and F5.
The cache is an infrastructure component that stores frequently accessed data or resources in a fast-access memory or storage location. Its primary purpose is to improve performance and scalability.
Popular caching solutions: Redis, Memcached, and Varnish.
The Content Delivery Network (CDN) is a network of globally distributed servers that delivers content to users from the server closest to them. It improves the performance and availability of the web application by reducing latency and network congestion.
Popular CDNs: Cloudflare, Akamai, and Amazon CloudFront.
There are several models of web application components, including the client-server, peer-to-peer, and the hybrid model.
Web Application Architecture Diagram
This diagram will help you visualize the application architecture by combining everything we discussed:

Layers of Web App Architecture

Here is a description of the four layers of a modern web app architecture:
Presentation Layer
The presentation layer manages the app user interface, dealing with HTML, CSS, and JavaScript. It also receives user input and sends it to the business layer for processing, interacting through APIs or interfaces. The presentation layer typically includes web components such as controllers, views, and templates.
Business Layer
The business (or application) layer handles the web application ' s business logic. It contains controllers, services, and models responsible for performing the necessary actions to fulfill user requests. The business layer interacts with the data access layer to retrieve or manipulate data as needed.
Data Access Layer
The data access (or persistence) layer translates application data into a format that can be stored and retrieved from a data store. It contains the components that interact with the database, such as data access objects (DAOs), object-relational mappers (ORMs), and stored procedures.
Database Layer
The database layer includes the database management system (DBMS) and the data stored in the database. This layer stores data in a structured format that can be easily queried and manipulated by the data access layer.
Here is an algorithmic representation of how the layers work together:
The user interacts with the presentation layer by providing input through the user interface.
The presentation layer receives the user input and sends it to the business layer.
The business layer processes the user input, performs the necessary actions, and retrieves or updates data through the data access layer.
The data access layer retrieves or updates data from the database layer and sends it back to the business layer.
The business layer processes the retrieved data and generates a response to the presentation layer.
The presentation layer receives the response from the business layer and updates the user interface accordingly.
The process repeats as the user provides further input or navigates through the application.
Types of Web Application Architecture
When it comes to designing and developing web applications, there are different types of architectures to choose from.
Single-Page Applications (SPAs)
In SPAs, the web application loads only once and then dynamically updates the content as the user interacts. The data is loaded asynchronously through APIs, making it more responsive and reducing the server ' s load. This architecture is suitable for applications that require a lot of user interaction and real-time data updates.
Examples: Gmail, Trello, Spotify, and Twitter.

Server-Side Rendered Application (SSR)
In SSR, the server generates HTML pages for each request, and the client only receives the final result. This architecture is suitable for applications that require fast loading times and good SEO, but it can be slower than SPAs.
Examples: WordPress, Airbnb, Shopify.

Progressive web application (PWA)
A PWA behaves like a native mobile application, with features like offline access, push notifications, and full-screen mode. This architecture is suitable for solutions that need to be accessible on mobile devices and have the same user experience as native applications.
Examples: Starbucks, Pinterest, Forbes, Uber, and Twitter Lite.

Microservices
In a microservices architecture, the backend is divided into small, independent services that communicate with each other through APIs. Each service is responsible for a specific function: authentication, payments, or messaging. This highly scalable architecture allows for more granular control over individual components but can be complex to manage.
Examples: Netflix, Amazon, Uber, and Airbnb.

Serverless Architecture
In this architecture, the backend is built using cloud-based solutions, such as AWS or Azure. Each function is responsible for tasks like registering users or sending email notifications. It is highly scalable and cost-effective but difficult to manage and debug.
Examples: Coca-Cola, Capital One, The New York Times, and Fender.

Precise Web Application Architecture Best Practices
Working on web app architecture, developers need to consider a range of factors:
Scalability — to handle increasing loads and scale horizontally or vertically
Modularity — to provide easy testing, modifications, and bug fixes
Security — to protect sensitive data and prevent unauthorized access
Performance — to guarantee a responsive and fast user experience
Availability — to ensure the application is available even during failures
Extensibility — to allow for future changes and updates
Standardization — to ensure consistency and ease of maintenance
Flexibility — to adapt to changing requirements and improvements over time
Documentation — to improve collaboration, reduce errors, and simplify maintenance
Why Integrio Is the Trusted Modern Web App Architecture Service Vendor
Integrio is a reliable modern web application architecture vendor with:
20 years of experience in developing web apps for startups, small and mid-sized companies, and enterprises
Expertise in various industries, including aviation, transportation, manufacturing, real estate, telecommunications, digital marketing, health, and fitness
Cutting-edge technologies, such as Artificial Intelligence (AI) and Machine Learning (ML)
Flexible cooperation and pricing models: project outsourcing (fixed price, time & material) and dedicated team (monthly retainer)
See the specific cases our company worked on:
For Volo Innovations , we developed software for managing gyms and fitness centers. Its functionality includes scheduling, invoicing, marketing activities, reporting, and more. The company was later acquired by Member Solutions, a subsidiary of Jonas Software, and the source code has successfully passed an independent audit for scalability and security.
US health insurance provider CareOregon conducted a member satisfaction survey. Our task was to create a program that could structure a huge amount of data and display it in the form of diagrams and tables. Such a platform had to be safe and reliable. As a result, the company increased its revenues and improved overall customer satisfaction and even can track its level in real time.
Collaboration with 123Signup started with the source code recovery and modernization of the legacy components of their event and association management solution. We also added modules for membership, event planning, and donations, as well as reporting and analytics. It helped clients improve their experience and run events with fewer staff.
Modern web application architecture is essential for creating scalable, secure, and maintainable solutions. By following best practices and choosing the appropriate components, layers, and types of architecture, developers can create applications that meet clients ' business needs and provide a seamless user experience.
Contact Integrio to learn how we can help you create an advanced web app with modern architecture.
What is a modern web app architecture?
A modern web application architecture is a software design approach that leverages cloud computing and microservices to build scalable, flexible, and efficient web applications. It also includes infrastructure components like containerization, load balancing, and caching.
How to create a modern web app architecture?
First, you need to understand the requirements of your application and select the appropriate technologies and infrastructure components to meet those needs. This involves careful planning, collaboration between development and operations teams, and a focus on scalability, security, and efficiency.
What should I consider when choosing web application architecture for my project?
To evaluate modern web app architecture, you must consider scalability, security, performance, and complexity. It ' s important to analyze your specific requirements, such as the number of users, the complexity of your application, and your budget. Consulting with Integrio experts can also be helpful.
I reviewed and agree to Integrio Systems Privacy Statement

We use cookies and other tracking technologies to improve your browsing experience on our website. By browsing our website, you consent to our use of cookies and other tracking technologies.
Application Architecture Guide - Chapter 10 - Presentation Layer Guidelines
Note - The patterns & practices Microsoft Application Architecture Guide, 2nd Edition is now live at http://msdn.microsoft.com/en-us/library/dd673617.aspx .
- J.D. Meier, Alex Homer, David Hill, Jason Taylor, Prashant Bansode, Lonnie Wall, Rob Boucher Jr, Akshay Bogawat
- 1 Objectives
- 3 Presentation Layer Components
- 5 Design Considerations
- 6 Presentation Layer Frame
- 8 Composition
- 9 Exception Management
- 12 Navigation
- 13 Presentation Entities
- 14 Request Processing
- 15 User Experience
- 16 UI Components
- 17 UI Process Components
- 18 Validation
- 19 Pattern Map
- 20 Pattern Descriptions
- 21.1 Mobile Applications
- 21.2 Rich Client Applications
- 21.3 Rich Internet Applications (RIA)
- 21.4 Web Applications
- 22 patterns & practices Solution Assets
- 23 Additional Resources
- Understand how the presentation layer fits into typical application architecture.
- Understand the components of the presentation layer.
- Learn the steps for designing the presentation layer.
- Learn the common issues faced while designing the presentation layer.
- Learn the key guidelines for designing the presentation layer.
- Learn the key patterns and technology considerations for designing the presentation layer.
The presentation layer contains the components that implement and display the user interface and manage user interaction. This layer includes controls for user input and display, in addition to components that organize user interaction. Figure 1 shows how the presentation layer fits into a common application architecture.

Figure 1 A typical application showing the presentation layer and the components it may contain
Presentation Layer Components
- User interface (UI) components . User interface components provide a way for users to interact with the application. They render and format data for users. They also acquire and validate data input by the user.
- User process components . User process components synchronize and orchestrate user interactions. Separate user process components may be useful if you have a complicated UI. Implementing common user interaction patterns as separate user process components allows you to reuse them in multiple UIs.
The following steps describe the process you should adopt when designing the presentation layer for your application. This approach will ensure that you consider all of the relevant factors as you develop your architecture:
- Identify your client type . Choose a client type that satisfies your requirements and adheres to the infrastructure and deployment constraints of your organization. For instance, if your users are on mobile devices and will be intermittently connected to the network, a mobile rich client is probably your best choice.
- Determine how you will present data . Choose the data format for your presentation layer and decide how you will present the data in your UI.
- Determine your data-validation strategy . Use data-validation techniques to protect your system from untrusted input.
- Determine your business logic strategy . Factor out your business logic to decouple it from your presentation layer code.
- Determine your strategy for communication with other layers . If your application has multiple layers, such as a data access layer and a business layer, determine a strategy for communication between your presentation layer and other layers.
Design Considerations
There are several key factors that you should consider when designing your presentation layer. Use the following principles to ensure that your design meets the requirements for your application, and follows best practices:
- Choose the appropriate UI technology. Determine if you will implement a rich (smart) client, a Web client, or a rich Internet application (RIA). Base your decision on application requirements, and on organizational and infrastructure constraints.
- Use the relevant patterns. Review the presentation layer patterns for proven solutions to common presentation problems.
- Design for separation of concerns. Use dedicated UI components that focus on rendering and display. Use dedicated presentation entities to manage the data required to present your views. Use dedicated UI process components to manage the processing of user interaction.
- Consider human interface guidelines. Review your organization’s guidelines for UI design. Review established UI guidelines based on the client type and technologies that you have chosen.
- Adhere to user-driven design principles. Before designing your presentation layer, understand your customer. Use surveys, usability studies, and interviews to determine the best presentation design to meet your customer’s requirements.
Presentation Layer Frame
There are several common issues that you must consider as your develop your design. These issues can be categorized into specific areas of the design. The following table lists the common issues for each category where mistakes are most often made.
Table 1 Presentation Layer Frame
| * Caching volatile data. | |
| * Failing to consider use of patterns and libraries that support dynamic layout and injection of views and presentation at runtime. | |
| * Failing to catch unhandled exceptions. | |
| * Failing to design for intuitive use, or implementing overly complex interfaces. | |
| * Using an inappropriate layout style for Web pages. | |
| * Inconsistent navigation. | |
| * Defining entities that are not necessary. | |
| * Blocking the UI during long-running requests. | |
| * Displaying unhelpful error messages. | |
| * Creating custom components that are not necessary. | |
| * Implementing UI process components when not necessary. | |
| * Failing to validate all input. |
Caching is one of the best mechanisms you can use to improve application performance and UI responsiveness. Use data caching to optimize data lookups and avoid network round trips. Cache the results of expensive or repetitive processes to avoid unnecessary duplicate processing.
Consider the following guidelines when designing your caching strategy:
- Do not cache volatile data.
- Consider using ready-to-use cache data when working with an in-memory cache. For example, use a specific object instead of caching raw database data.
- Do not cache sensitive data unless you encrypt it.
- If your application is deployed in Web farm, avoid using local caches that need to be synchronized; instead, consider using a transactional resource manager such as Microsoft SQL Server® or a product that supports distributed caching.
- Do not depend on data still being in your cache. It may have been removed.
Composition
Consider whether your application will be easier to develop and maintain if the presentation layer uses independent modules and views that are easily composed at run time. Composition patterns support the creation of views and the presentation layout at run time. These patterns also help to minimize code and library dependencies that would otherwise force recompilation and redeployment of a module when the dependencies change. Composition patterns help you to implement sharing, reuse, and replacement of presentation logic and views.
Consider the following guidelines when designing your composition strategy:
- Avoid using dynamic layouts. They can be difficult to load and maintain.
- Be careful with dependencies between components. For example, use abstraction patterns when possible to avoid issues with maintainability.
- Consider creating templates with placeholders. For example, use the Template View pattern to compose dynamic Web pages in order to ensure reuse and consistency.
- Consider composing views from reusable modular parts. For example, use the Composite View pattern to build a view from modular, atomic component parts.
- If you need to allow communication between presentation components, consider implementing the Publish/Subscribe pattern. This will lower the coupling between the components and improve testability.
Exception Management
Design a centralized exception-management mechanism for your application that catches and throws exceptions consistently. Pay particular attention to exceptions that propagate across layer or tier boundaries, as well as exceptions that cross trust boundaries. Design for unhandled exceptions so they do not impact application reliability or expose sensitive information.
Consider the following guidelines when designing your exception management strategy:
- Use user-friendly error messages to notify users of errors in the application.
- Avoid exposing sensitive data in error pages, error messages, log files, and audit files.
- Design a global exception handler that displays a global error page or an error message for all unhandled exceptions.
- Differentiate between system exceptions and business errors. In the case of business errors, display a user-friendly error message and allow the user to retry the operation. In the case of system exceptions, check to see if the exception was caused by issues such as system or database failure, display a user-friendly error message, and log the error message, which will help in troubleshooting.
- Avoid using exceptions to control application logic.
Design a user input strategy based on your application input requirements. For maximum usability, follow the established guidelines defined in your organization, and the many established industry usability guidelines based on years of user research into input design and mechanisms.
Consider the following guidelines when designing your input collection strategy:
- Use forms-based input controls for normal data-collection tasks.
- Use a document-based input mechanism for collecting input in Microsoft Office–style documents.
- Implement a wizard-based approach for more complex data collection tasks, or for input that requires a workflow.
- Design to support localization by avoiding hard-coded strings and using external resources for text and layout.
- Consider accessibility in your design. You should consider users with disabilities when designing your input strategy; for example, implement text-to-speech software for blind users, or enlarge text and images for users with poor sight. Support keyboard-only scenarios where possible for users who cannot manipulate a pointing device.
Design your UI layout so that the layout mechanism itself is separate from the individual UI components and UI process components. When choosing a layout strategy, consider whether you will have a separate team of designers building the layout, or whether the development team will create the UI. If designers will be creating the UI, choose a layout approach that does not require code or the use of development-focused tools.
Consider the following guidelines when designing your layout strategy:
- Use templates to provide a common look and feel to all of the UI screens.
- Use a common look and feel for all elements of your UI to maximize accessibility and ease of use.
- Consider device-dependent input, such as touch screens, ink, or speech, in your layout. For example, with touch-screen input you will typically use larger buttons with more spacing between them than you would with mouse or keyboard inputs.
- When building a Web application, consider using Cascading Style Sheets (CSS) for layout. This will improve rendering performance and maintainability.
- Use design patterns, such as Model-View-Presenter (MVP), to separate the layout design from interface processing.
Design your navigation strategy so that users can navigate easily through your screens or pages, and so that you can separate navigation from presentation and UI processing. Ensure that you display navigation links and controls in a consistent way throughout your application to reduce user confusion and hide application complexity.
Consider the following guidelines when designing your navigation strategy:
- Use well-known design patterns to decouple the UI from the navigation logic where this logic is complex.
- Design toolbars and menus to help users find functionality provided by the UI.
- Consider using wizards to implement navigation between forms in a predictable way.
- Determine how you will preserve navigation state if the application must preserve this state between sessions.
- Consider using the Command Pattern to handle common actions from multiple sources.
Presentation Entities
Use presentation entities to store the data you will use in your presentation layer to manage your views. Presentation entities are not always necessary; use them only if your datasets are sufficiently large and complex to require separate storage from the UI controls.
Consider the following guidelines when designing presentation entities:
- Determine if you require presentation entities. Typically, you may require presentation entities only if the data or the format to be displayed is specific to the presentation layer.
- If you are working with data-bound controls, consider using custom objects, collections, or datasets as your presentation entity format.
- If you want to map data directly to business entities, use a custom class for your presentation entities.
- Do not add business logic to presentation entities.
- If you need to perform data type validation, consider adding it in your presentation entities.
Request Processing
Design your request processing with user responsiveness in mind, as well as code maintainability and testability.
Consider the following guidelines when designing request processing:
- Use asynchronous operations or worker threads to avoid blocking the UI for long-running actions.
- Avoid mixing your UI processing and rendering logic.
- Consider using the Passive View pattern (a variant of MVP) for interfaces that do not manage a lot of data.
- Consider using the Supervising Controller pattern (a variant of MVP) for interfaces that manage large amounts of data.
User Experience
Good user experience can make the difference between a usable and unusable application. Carry out usability studies, surveys, and interviews to understand what users require and expect from your application, and design with these results in mind.
Consider the following guidelines when designing for user experience:
- When developing a rich Internet application (RIA), avoid synchronous processing where possible.
- When developing a Web application, consider using Asynchronous JavaScript and XML (AJAX) to improve responsiveness and to reduce post backs and page reloads.
- Do not design overloaded or overly complex interfaces. Provide a clear path through the application for each key user scenario.
- Design to support user personalization, localization, and accessibility.
- Design for user empowerment. Allow the user to control how he or she interacts with the application, and how it displays data to them.
UI Components
UI components are the controls and components used to display information to the user and accept user input. Be careful not to create custom controls unless it is necessary for specialized display or data collection.
Consider the following guidelines when designing UI components:
- Take advantage of the data-binding features of the controls you use in the UI.
- Create custom controls or use third-party controls only for specialized display and data-collection tasks.
- When creating custom controls, extend existing controls if possible instead of creating a new control.
- Consider implementing designer support for custom controls to make it easier to develop with them.
- Consider maintaining the state of controls as the user interacts with the application instead of reloading controls with each action.
UI Process Components
UI process components synchronize and orchestrate user interactions. UI processing components are not always necessary; create them only if you need to perform significant processing in the presentation layer that must be separated from the UI controls. Be careful not to mix business and display logic within the process components; they should be focused on organizing user interactions with your UI.
Consider the following guidelines when designing UI processing components:
- Do not create UI process components unless you need them.
- If your UI requires complex processing or needs to talk to other layers, use UI process components to decouple this processing from the UI.
- Consider dividing UI processing into three distinct roles: Model, View, and Controller/Presenter, by using the MVC or MVP pattern.
- Avoid business rules, with the exception of input and data validation, in UI processing components.
- Consider using abstraction patterns, such as dependency inversion, when UI processing behavior needs to change based on the run-time environment.
- Where the UI requires complex workflow support, create separate workflow components that use a workflow system such as Windows Workflow or a custom mechanism.
Designing an effective input and data-validation strategy is critical to the security of your application. Determine the validation rules for user input as well as for business rules that exist in the presentation layer.
Consider the following guidelines when designing your input and data validation strategy:
- Validate all input data on the client side where possible to improve interactivity and reduce errors caused by invalid data.
- Do not rely on client-side validation only. Always use server-side validation to constrain input for security purposes and to make security-related decisions.
- Design your validation strategy to constrain, reject, and sanitize malicious input.
- Use the built-in validation controls where possible, when working with .NET Framework.
- In Web applications, consider using AJAX to provide real-time validation.
Pattern Map
Key patterns are organized by key categories, as detailed in the Presentation Layer Frame in the following table. Consider using these patterns when making design decisions for each category.
Table 2 Pattern Map
| * Cache Dependency | |
| * Composite View | |
| * Exception Shielding | |
| * Template View | |
| * Front Controller | |
| * Entity Translator | |
| * Asynchronous Callback | |
| * Model-View-Controller (MVC) |
- For more information on the Page Cache pattern, see “Enterprise Solution Patterns Using Microsoft .NET” at http://msdn.microsoft.com/en-us/library/ms998469.aspx
- For more information on the Model-View-Controller (MVC), Page Controller, Front Controller, Template View, Transform View, and Two-Step View patterns, see “Patterns of Enterprise Application Architecture (P of EAA)” at http://martinfowler.com/eaaCatalog/
- For more information on the Composite View, Supervising Controller, and Presentation Model patterns, see “Patterns in the Composite Application Library” at http://msdn.microsoft.com/en-us/library/cc707841.aspx
- For more information on the Chain of responsibility and Command pattern, see “data & object factory” at http://www.dofactory.com/Patterns/Patterns.aspx
- For more information on the Asynchronous Callback pattern, see “Creating a Simplified Asynchronous Call Pattern for Windows Forms Applications” at http://msdn.microsoft.com/en-us/library/ms996483.aspx
- For more information on the Exception Shielding and Entity Translator patterns, see “Useful Patterns for Services” at http://msdn.microsoft.com/en-us/library/cc304800.aspx
Pattern Descriptions
- Asynchronous Callback. Execute long-running tasks on a separate thread that executes in the background, and provide a function for the thread to call back into when the task is complete.
- Cache Dependency. Use external information to determine the state of data stored in a cache.
- Chain of Responsibility. Avoid coupling the sender of a request to its receiver by giving more than one object a chance to handle the request.
- Composite View . Combine individual views into a composite representation.
- Command Pattern. Encapsulate request processing in a separate command object with a common execution interface.
- Entity Translator. An object that transforms message data types into business types for requests, and reverses the transformation for responses.
- Exception Shielding. Prevent a service from exposing information about its internal implementation when an exception occurs.
- Front Controller . Consolidate request handling by channeling all requests through a single handler object, which can be modified at run time with decorators.
- Model-View-Controller . Separate the UI code into three separate units: Model (data), View (interface), and Presenter (processing logic), with a focus on the View. Two variations on this pattern include Passive View and Supervising Controller, which define how the View interacts with the Model.
- Page Cache. Improve the response time for dynamic Web pages that are accessed frequently but change less often and consume a large amount of system resources to construct.
- Page Controller . Accept input from the request and handle it for a specific page or action on a Web site.
- Passive View . Reduce the view to the absolute minimum by allowing the controller to process user input and maintain the responsibility for updating the view.
- Presentation Model . Move all view logic and state out of the view, and render the view through data-binding and templates.
- Supervising Controller . A variation of the MVC pattern in which the controller handles complex logic, in particular coordinating between views, but the view is responsible for simple view-specific logic.
- Template View . Implement a common template view, and derive or construct views using this template view.
- Transform View . Transform the data passed to the presentation tier into HTML for display in the UI.
- Two-Step View . Transform the model data into a logical presentation without any specific formatting, and then convert that logical presentation to add the actual formatting required.
Technology Considerations
The following guidelines will help you to choose an appropriate implementation technology. The guidelines also contain suggestions for common patterns that are useful for specific types of application and technology.
Mobile Applications
Consider the following guidelines when designing a mobile application:
- If you want to build full-featured connected, occasionally connected, and disconnected executable applications that run on a wide range of Microsoft Windows®–based devices, consider using the Microsoft Windows Compact Framework.
- If you want to build connected applications that require Wireless Application Protocol (WAP), compact HTML (cHTML), or similar rendering formats, consider using ASP.NET Mobile Forms and Mobile Controls.
- If you want to build applications that support rich media and interactivity, consider using Microsoft Silverlight® for Mobile.
Rich Client Applications
Consider the following guidelines when designing a rich client application:
- If you want to build applications with good performance and interactivity, and have design support in Microsoft Visual Studio®, consider using Windows Forms.
- If you want to build applications that fully support rich media and graphics, consider using Windows Presentation Foundation (WPF).
- If you want to build applications that are downloaded from a Web server and then execute on the client, consider using XAML Browser Applications (XBAP).
- If you want to build applications that are predominantly document-based, or are used for reporting, consider designing a Microsoft Office Business Application.
- If you decide to use Windows Forms and you are designing composite interfaces, consider using the Smart Client Software Factory.
- If you decide to use WPF and you are designing composite interfaces, consider using the Composite Application Guidance for WPF.
- If you decide to use WPF, consider using the Presentation Model (Model-View-ViewModel) pattern.
- If you decide to use WPF, consider using WPF Commands to communicate between your View and your Presenter or ViewModel.
- If you decide to use WPF, consider implementing the Presentation Model pattern by using DataTemplates over User Controls to give designers more control.

Rich Internet Applications (RIA)
Consider the following guidelines when designing an RIA:
- If you want to build browser-based, connected applications that have broad cross-platform reach, are highly graphical, and support rich media and presentation features, consider using Silverlight.
- If you decide to use Silverlight, consider using the Presentation Model (Model-View-ViewModel) pattern.
Web Applications
Consider the following guidelines when designing a Web application:
- If you want to build applications that are accessed through a Web browser or specialist user agent, consider using ASP.NET.
- If you want to build applications that provide increased interactivity and background processing, with fewer page reloads, consider using ASP.NET with AJAX.
- If you want to build applications that include islands of rich media content and interactivity, consider using ASP.NET with Silverlight controls.
- If you are using ASP.NET and want to implement a control-centric model with separate controllers and improved testability, consider using the ASP.NET MVC Framework.
- If you are using ASP.NET, consider using master pages to simplify development and implement a consistent UI across all pages.
patterns & practices Solution Assets
- Web Client Software Factory at http://msdn.microsoft.com/en-us/library/bb264518.aspx
- Smart Client Software Factory at http://msdn.microsoft.com/en-us/library/aa480482.aspx
- Composite Application Guidance for WPF at http://msdn.microsoft.com/en-us/library/cc707819.aspx
- Smart Client - Composite UI Application Block at http://msdn.microsoft.com/en-us/library/aa480450.aspx
Additional Resources
- For more information, see Microsoft Inductive User Interface Guidelines at http://msdn.microsoft.com/en-us/library/ms997506.aspx .
- For more information, see User Interface Control Guidelines at http://msdn.microsoft.com/en-us/library/bb158625.aspx .
- For more information, see User Interface Text Guidelines at http://msdn.microsoft.com/en-us/library/bb158574.aspx .
- For more information, see Design and Implementation Guidelines for Web Clients at http://msdn.microsoft.com/en-us/library/ms978631.aspx .
- For more information, see Web Presentation Patterns at http://msdn.microsoft.com/en-us/library/ms998516.aspx .
Navigation menu
Page actions.
- View source
Personal tools
- Community portal
- Current events
- Recent changes
- Random page
- What links here
- Related changes
- Special pages
- Printable version
- Permanent link
- Page information
- This page was last edited on 22 January 2010, at 02:50.
- Privacy policy
- About Guidance Share
- Disclaimers

Computer Network
- Operating Systems
- Computer Fundamentals
- Interview Q
Physical Layer
Data link layer, network layer, routing algorithm, transport layer, application layer, application protocols, network security.
Interview Questions
| The presentation layer is the 6 layer from the bottom in the OSI model. This layer presents the incoming data from the application layer of the sender machine to the receiver machine. It converts one format of data to another format of data if both sender and receiver understand different formats; hence this layer is also called the translation layer. It deals with the semantics and syntax of the data, so this layer is also called the syntax layer. It uses operations such as data compression, data encryption & decryption, data conversion, etc. Data is sent from sender to receiver, but what if the sender device and receiver device understand different formats of code? For example, suppose one device understands ASCII code and another device understands EBCDIC code. In that case, the data must be translated into a code that the recipient understands to determine what data has been sent. The presentation layer is responsible for translating ASCII codes to EBCDIC or vice versa. With the help of the presentation layer, the receiver understands the data effectively and uses it efficiently. Whatever data is being transmitted between the sender and the receiver, that data must be secure because an intruder can hack the data passing between the sender and the receiver. Hackers can modify the data and send the modified data to the receiver to create false communication. The presentation layer is responsible for encrypting and decrypting data to avoid data leakage and data modification.The plaintext data at the source is encrypted into ciphertext (unreadable format), then it is sent to the receiver, where the ciphertext is decrypted into plaintext. Now, if the hacker tries to hack the data, the hacker receives an encrypted, unreadable form, and if the hacker tries to send modified data, the receiver can detect the modification during decryption; thereby, the data remains safe. If the file size is large, it becomes difficult to transmit the large file over the network. File size can be decreased by compressing the file for easy transmission of data. Compression is the method of diminishing the size of a file to transmit data easily in less time. When the compressed data reaches the receiver, the data is reconstructed back to the original size, and this process is called decompression. The presentation layer in the OSI model is classified into two sublayers: This sublayer offers services to layer-7, i.e., the application layer, and requests services from layer-5, i.e., the session layer. It supports various application services, such as Reliable Transfer Service Element (RTSE), Remote Operation Service Element (ROSE), Association Control Service Element (ACSE), and Commitment Concurrency and Recovery (CCR). This sublayer offers application-specific protocols, such as Message Oriented Text Interchange Standard (MOTIS), Remote Database Access (RDA), File Transfer Access and Manager (FTAM), Common Management Information Protocol (CMIP), Virtual Terminal (VT), Distributed Transaction Processing (DTP), Job Transfer and Manipulation (JTM), and others. It is a presentation layer protocol in the OSI model, which was formed by Citrix Systems. It is used for transferring data from server to client. It is a very thin protocol as it does not require much overhead in order to transmit data from the server over to the client. It is well-optimized for the WAN. It is the protocol that is used to implement the presentation layer of the OSI model. It provides different kinds of data representation, such as images, video, audio, numbers, etc. It is used for Microsoft Remote Procedure Call (Microsoft RPC) and Distributed Computing Environment (DCE) / Remote Procedure Calls (RPC). It is a communication protocol that was specifically designed for macOS by Apple, Inc. It provides file services for Classic Mac OS and macOS. This protocol is used to share files over the network. It is a protocol that is associated with the client-server operating system. The user can access the directory, print, message, file, clock synchronization, etc., with the help of this protocol. It supports many platforms, such as Linux, Classic Mac OS, Windows NT, Mac OS X, and Microsoft Windows. It is a telecommunications equipment that splits a stream of data into separate packets and formats packet headers for asynchronous communication on X.25 networks. It receives packets from the network and converts them into a stream of data. The PAD provides many asynchronous terminal connectivities to a host computer. It is a computer network protocol that is used to transfer data between two systems. It was first published in 1987. XDR is used by various systems such as NDMP, Network File System, NetCDF, ZFS, Open Network Computer Remote Procedure Call, and others. It is a protocol that offers ISO presentation services over TCP/IP based networks. This protocol explains an approach to provide stream-line support for OSI over TCP/IP based networks. |

- Send your Feedback to [email protected]
Help Others, Please Share

Learn Latest Tutorials
Transact-SQL
Reinforcement Learning
R Programming
React Native
Python Design Patterns
Python Pillow
Python Turtle
Preparation

Verbal Ability

Company Questions
Trending Technologies
Artificial Intelligence
Cloud Computing
Data Science
Machine Learning
B.Tech / MCA
Data Structures
Operating System
Compiler Design
Computer Organization
Discrete Mathematics
Ethical Hacking
Computer Graphics
Software Engineering
Web Technology
Cyber Security
C Programming
Control System
Data Mining
Data Warehouse

Software Architecture Patterns by
Get full access to Software Architecture Patterns and 60K+ other titles, with a free 10-day trial of O'Reilly.
There are also live events, courses curated by job role, and more.
Chapter 1. Layered Architecture
The most common architecture pattern is the layered architecture pattern, otherwise known as the n-tier architecture pattern. This pattern is the de facto standard for most Java EE applications and therefore is widely known by most architects, designers, and developers. The layered architecture pattern closely matches the traditional IT communication and organizational structures found in most companies, making it a natural choice for most business application development efforts.
Pattern Description
Components within the layered architecture pattern are organized into horizontal layers, each layer performing a specific role within the application (e.g., presentation logic or business logic). Although the layered architecture pattern does not specify the number and types of layers that must exist in the pattern, most layered architectures consist of four standard layers: presentation, business, persistence, and database ( Figure 1-1 ). In some cases, the business layer and persistence layer are combined into a single business layer, particularly when the persistence logic (e.g., SQL or HSQL) is embedded within the business layer components. Thus, smaller applications may have only three layers, whereas larger and more complex business applications may contain five or more layers.
Each layer of the layered architecture pattern has a specific role and responsibility within the application. For example, a presentation layer would be responsible for handling all user interface and browser communication logic, whereas a business layer would be responsible for executing specific business rules associated with the request. Each layer in the architecture forms an abstraction around the work that needs to be done to satisfy a particular business request. For example, the presentation layer doesn’t need to know or worry about how to get customer data; it only needs to display that information on a screen in particular format. Similarly, the business layer doesn’t need to be concerned about how to format customer data for display on a screen or even where the customer data is coming from; it only needs to get the data from the persistence layer, perform business logic against the data (e.g., calculate values or aggregate data), and pass that information up to the presentation layer.
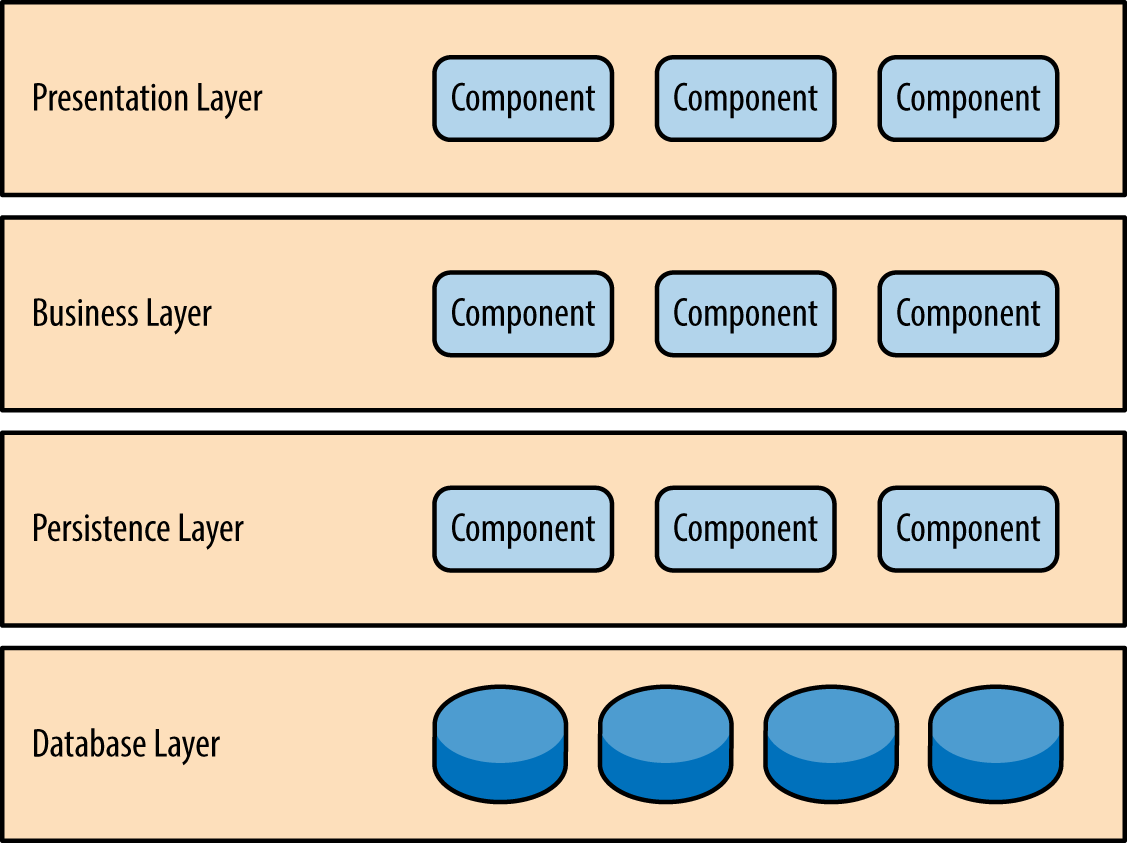
Figure 1-1. Layered architecture pattern
One of the powerful features of the layered architecture pattern is the separation of concerns among components. Components within a specific layer deal only with logic that pertains to that layer. For example, components in the presentation layer deal only with presentation logic, whereas components residing in the business layer deal only with business logic. This type of component classification makes it easy to build effective roles and responsibility models into your architecture, and also makes it easy to develop, test, govern, and maintain applications using this architecture pattern due to well-defined component interfaces and limited component scope.
Key Concepts
Notice in Figure 1-2 that each of the layers in the architecture is marked as being closed . This is a very important concept in the layered architecture pattern. A closed layer means that as a request moves from layer to layer, it must go through the layer right below it to get to the next layer below that one. For example, a request originating from the presentation layer must first go through the business layer and then to the persistence layer before finally hitting the database layer.
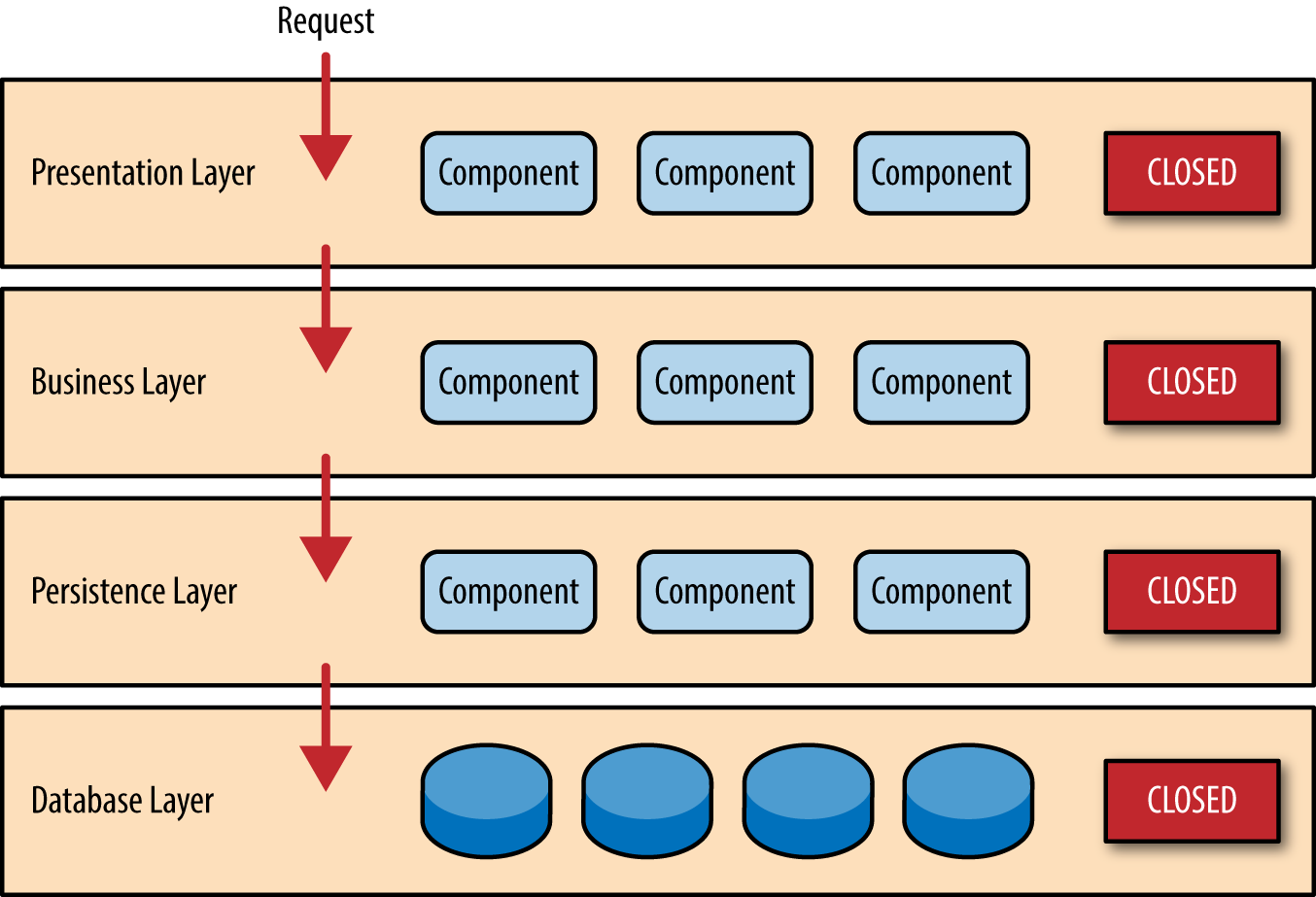
Figure 1-2. Closed layers and request access
So why not allow the presentation layer direct access to either the persistence layer or database layer? After all, direct database access from the presentation layer is much faster than going through a bunch of unnecessary layers just to retrieve or save database information. The answer to this question lies in a key concept known as layers of isolation .
The layers of isolation concept means that changes made in one layer of the architecture generally don’t impact or affect components in other layers: the change is isolated to the components within that layer, and possibly another associated layer (such as a persistence layer containing SQL). If you allow the presentation layer direct access to the persistence layer, then changes made to SQL within the persistence layer would impact both the business layer and the presentation layer, thereby producing a very tightly coupled application with lots of interdependencies between components. This type of architecture then becomes very hard and expensive to change.
The layers of isolation concept also means that each layer is independent of the other layers, thereby having little or no knowledge of the inner workings of other layers in the architecture. To understand the power and importance of this concept, consider a large refactoring effort to convert the presentation framework from JSP (Java Server Pages) to JSF (Java Server Faces). Assuming that the contracts (e.g., model) used between the presentation layer and the business layer remain the same, the business layer is not affected by the refactoring and remains completely independent of the type of user-interface framework used by the presentation layer.
While closed layers facilitate layers of isolation and therefore help isolate change within the architecture, there are times when it makes sense for certain layers to be open. For example, suppose you want to add a shared-services layer to an architecture containing common service components accessed by components within the business layer (e.g., data and string utility classes or auditing and logging classes). Creating a services layer is usually a good idea in this case because architecturally it restricts access to the shared services to the business layer (and not the presentation layer). Without a separate layer, there is nothing architecturally that restricts the presentation layer from accessing these common services, making it difficult to govern this access restriction.
In this example, the new services layer would likely reside below the business layer to indicate that components in this services layer are not accessible from the presentation layer. However, this presents a problem in that the business layer is now required to go through the services layer to get to the persistence layer, which makes no sense at all. This is an age-old problem with the layered architecture, and is solved by creating open layers within the architecture.
As illustrated in Figure 1-3 , the services layer in this case is marked as open, meaning requests are allowed to bypass this open layer and go directly to the layer below it. In the following example, since the services layer is open, the business layer is now allowed to bypass it and go directly to the persistence layer, which makes perfect sense.
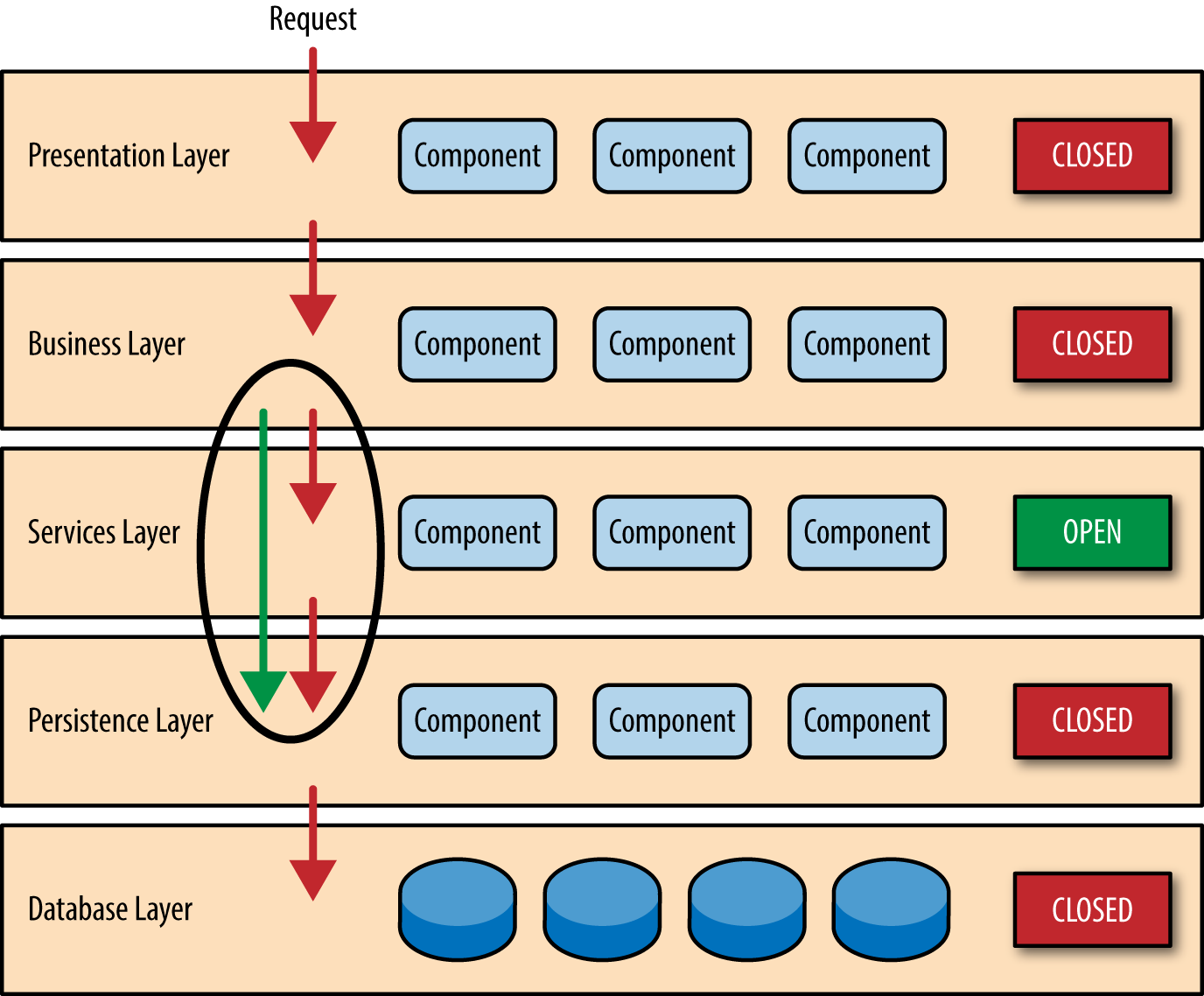
Figure 1-3. Open layers and request flow
Leveraging the concept of open and closed layers helps define the relationship between architecture layers and request flows and also provides designers and developers with the necessary information to understand the various layer access restrictions within the architecture. Failure to document or properly communicate which layers in the architecture are open and closed (and why) usually results in tightly coupled and brittle architectures that are very difficult to test, maintain, and deploy.
Pattern Example
To illustrate how the layered architecture works, consider a request from a business user to retrieve customer information for a particular individual as illustrated in Figure 1-4 . The black arrows show the request flowing down to the database to retrieve the customer data, and the red arrows show the response flowing back up to the screen to display the data. In this example, the customer information consists of both customer data and order data (orders placed by the customer).
The customer screen is responsible for accepting the request and displaying the customer information. It does not know where the data is, how it is retrieved, or how many database tables must be queries to get the data. Once the customer screen receives a request to get customer information for a particular individual, it then forwards that request onto the customer delegate module. This module is responsible for knowing which modules in the business layer can process that request and also how to get to that module and what data it needs (the contract). The customer object in the business layer is responsible for aggregating all of the information needed by the business request (in this case to get customer information). This module calls out to the customer dao (data access object) module in the persistence layer to get customer data, and also the order dao module to get order information. These modules in turn execute SQL statements to retrieve the corresponding data and pass it back up to the customer object in the business layer. Once the customer object receives the data, it aggregates the data and passes that information back up to the customer delegate, which then passes that data to the customer screen to be presented to the user.
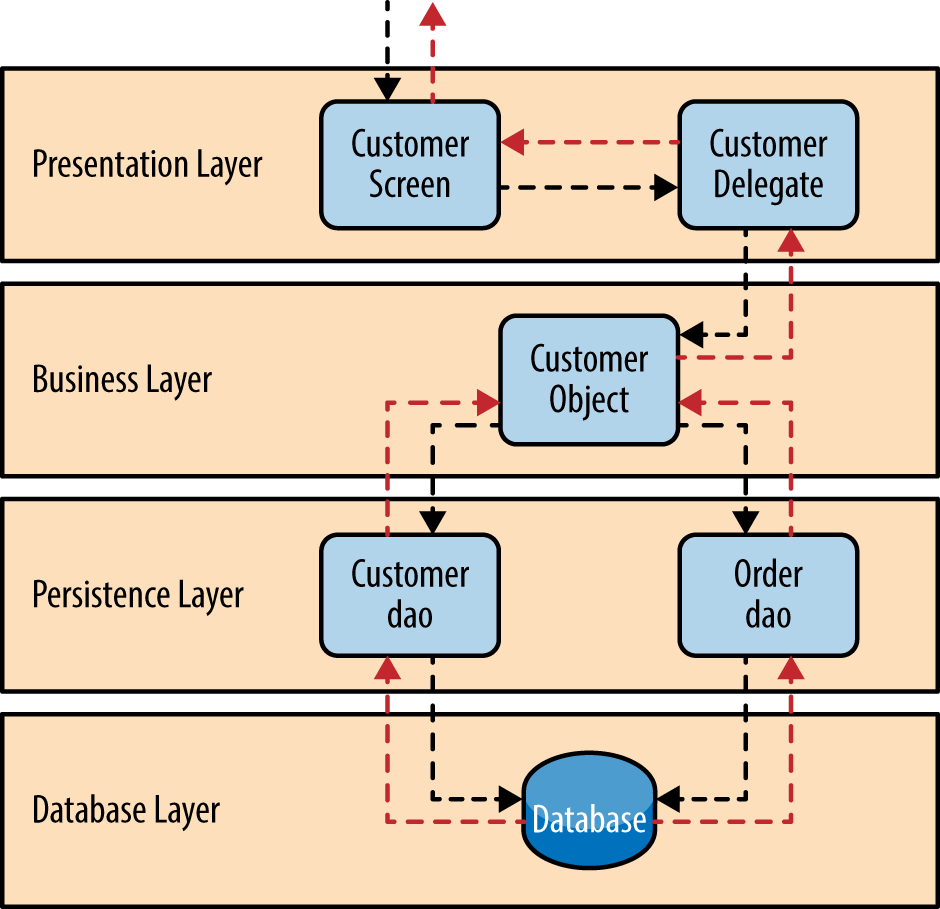
Figure 1-4. Layered architecture example
From a technology perspective, there are literally dozens of ways these modules can be implemented. For example, in the Java platform, the customer screen can be a (JSF) Java Server Faces screen coupled with the customer delegate as the managed bean component. The customer object in the business layer can be a local Spring bean or a remote EJB3 bean. The data access objects illustrated in the previous example can be implemented as simple POJO’s (Plain Old Java Objects), MyBatis XML Mapper files, or even objects encapsulating raw JDBC calls or Hibernate queries. From a Microsoft platform perspective, the customer screen can be an ASP (active server pages) module using the .NET framework to access C# modules in the business layer, with the customer and order data access modules implemented as ADO (ActiveX Data Objects).
Considerations
The layered architecture pattern is a solid general-purpose pattern, making it a good starting point for most applications, particularly when you are not sure what architecture pattern is best suited for your application. However, there are a couple of things to consider from an architecture standpoint when choosing this pattern.
The first thing to watch out for is what is known as the architecture sinkhole anti-pattern . This anti-pattern describes the situation where requests flow through multiple layers of the architecture as simple pass-through processing with little or no logic performed within each layer. For example, assume the presentation layer responds to a request from the user to retrieve customer data. The presentation layer passes the request to the business layer, which simply passes the request to the persistence layer, which then makes a simple SQL call to the database layer to retrieve the customer data. The data is then passed all the way back up the stack with no additional processing or logic to aggregate, calculate, or transform the data.
Every layered architecture will have at least some scenarios that fall into the architecture sinkhole anti-pattern. The key, however, is to analyze the percentage of requests that fall into this category. The 80-20 rule is usually a good practice to follow to determine whether or not you are experiencing the architecture sinkhole anti-pattern. It is typical to have around 20 percent of the requests as simple pass-through processing and 80 percent of the requests having some business logic associated with the request. However, if you find that this ratio is reversed and a majority of your requests are simple pass-through processing, you might want to consider making some of the architecture layers open, keeping in mind that it will be more difficult to control change due to the lack of layer isolation.
Another consideration with the layered architecture pattern is that it tends to lend itself toward monolithic applications, even if you split the presentation layer and business layers into separate deployable units. While this may not be a concern for some applications, it does pose some potential issues in terms of deployment, general robustness and reliability, performance, and scalability.
Pattern Analysis
The following table contains a rating and analysis of the common architecture characteristics for the layered architecture pattern. The rating for each characteristic is based on the natural tendency for that characteristic as a capability based on a typical implementation of the pattern, as well as what the pattern is generally known for. For a side-by-side comparison of how this pattern relates to other patterns in this report, please refer to Appendix A at the end of this report.
Get Software Architecture Patterns now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.
Don’t leave empty-handed
Get Mark Richards’s Software Architecture Patterns ebook to better understand how to design components—and how they should interact.
It’s yours, free.

Check it out now on O’Reilly
Dive in for free with a 10-day trial of the O’Reilly learning platform—then explore all the other resources our members count on to build skills and solve problems every day.


- Data Structure
- Coding Problems
- C Interview Programs
- C++ Aptitude
- Java Aptitude
- C# Aptitude
- PHP Aptitude
- Linux Aptitude
- DBMS Aptitude
- Networking Aptitude
- AI Aptitude
- MIS Executive
- Web Technologie MCQs
- CS Subjects MCQs
- Databases MCQs
- Programming MCQs
- Testing Software MCQs
- Digital Mktg Subjects MCQs
- Cloud Computing S/W MCQs
- Engineering Subjects MCQs
- Commerce MCQs
- More MCQs...
- Machine Learning/AI
- Operating System
- Computer Network
- Software Engineering
- Discrete Mathematics
- Digital Electronics
- Data Mining
- Embedded Systems
- Cryptography
- CS Fundamental
- More Tutorials...
- Tech Articles
- Code Examples
- Programmer's Calculator
- XML Sitemap Generator
- Tools & Generators

Computer Network Tutorial
- Computer Network - Home
- Computer Network - Overview
- Computer Network - Applications
- Computer Network - TCP/IP
- Computer Network - OSI Model
- Computer Network - Transport, Network, & Application Layers
- Computer Network - Network Protocols & Network Software
- Computer Network - TopologiesTypes
- Computer Network - Hub
- Computer Network - Routing
- Computer Network - Routers
- Computer Network - Dynamic Routing Protocols
- Computer Network - Router
- Computer Network - Populating a Routing Table
- Computer Network - Switches
- Computer Network - Layer 2 Switching
- Computer Network - Configure Cisco Switch
- Computer Network - ICMP
- Computer Network - ICMP Messages
- Computer Network - Addressing
- Computer Network - Classless Addressing
- Computer Network - IPV4 Addressing
- Computer Network - IPV6 Addressing
- Computer Network - Logical Addressing, Notations
- Computer Network - Classful & Classless Addressing
- Computer Network - Subnetting & Supernetting
- Computer Network - Network Address Translation
- Computer Network - FLSM & VLSM
- Computer Network - Line Configuration
- Transmission Computer Network - Modes
- Computer Network - Data Link Layer
- Computer Network - Physical Layer
- Computer Network - Network Layer
- Computer Network - Session Layer
- Computer Network - Transport Layer
- Computer Network - Application Layer
- Computer Network - Presentation Layer
- Computer Network - Coaxial Cable
- Computer Network - Optical Fiber
- Computer Network - Unguided Transmission Media
- Computer Network - Virtual LAN (VLAN)
- Computer Network - VSAN
- Computer Network - Multiple Access Protocol
- Computer Network - Random Access methods
- Computer Network - Aloha Network
- Computer Network - CSMA
- Computer Network - FDMA & TDMA
- Computer Network - CDMA
- Computer Network - Ethernet Technology
- Computer Network - Types of Network Topology
- Computer Network - Data Transmission
- Computer Network - Switching Techniques
- Computer Network - Transmission Impairment
- Computer Network - Synchronous & Asynchronous Transmission
- Computer Network - Intent-Based Networking
- Computer Network - Software-Defined Networking
- Computer Network - Wireless Personal Area Network
- Computer Network - Wireless Wide Area Network
- Computer Network - P2P File Sharing
- Computer Network - Packet Switching
- Computer Network - PGP - Authentication & Confidentiality
- Computer Network - PGP - Encryption & Compression
- Computer Network - Phishing Attacks
- Computer Network - ICMP Ping
- Computer Network - Pipelining in Packet Switching
- Computer Network - Plaintext Vs. Cleartext Encryption
- Computer Network - Platform as a Service (PaaS)
- Computer Network - GPRS Architecture
- Computer Network - Identify & Prevent Phishing & Pharming
- Computer Network - Change MAC Address
- Computer Network - Network Administrator Vs. Network Engineer
Difference B/W Articles
- Computer Network - Phishing & Pharming
- Computer Network - Ping Vs. Traceroute
- Computer Network - Network Vs. System Administrator
- Computer Network - Network & Application Layer Protocols
- Computer Network - Network Security Vs. Network Administration
- Computer Network - Network Vs. Internet
- Computer Network - PDH Vs. SDH
- Computer Network - PCI Vs. PCI express
- Computer Network - PCI-E Vs. PCI-X
- Computer Network - OT Vs. IT Networks
Computer Network Practice
- Computer Network - MCQs
- Computer Network - Aptitude Questions
Home » Computer Network
Presentation Layer: What It Is, Design Issues, Functionalities
Description and Functions of Presentation Layer in the OSI model: In this tutorial, we are going to learn what the Presentation layer is and the Functions of the Presentation Layer in the OSI model in Computer Networking. We will also discuss the Design issues with the Presentation Layer and the working of the Presentation Layer with the help of its diagram. By Monika Jha Last updated : May 05, 2023
What is Presentation Layer?
The Presentation Layer is concerned with the syntax and semantics of the information exchanged between two communicating devices.
- The presentation layer takes care that the data is sent in that way the receiver of the data will understand the information (data) and will be able to use the data.
- Languages that are syntax can be different from the two communicating machines. In this condition, the presentation layer plays the role of translator between them.
- It is possible for two machines to communicate with different data representations, data structures to be exchanged can be defined in an abstract way.
- These abstract data structures will be managed by the presentation layer and this layer allows higher-level data structures (For example banking records), to be defined and exchanged.
This figure shows the relationship of the presentation layer to the session layer and application layer.

Design Issues with Presentation Layer
The following are the design issues with presentation layer:
- To manage and maintain the Syntax and Semantics of the information transmitted.
- Encoding data in a standard agreed-upon way just like a string, double, date, etc.
- It Performs Standard Encoding scheme on the wire.
Functionalities of the Presentation Layer
Specific functionalities of the presentation layer are as follows:
1. Translation
- The processes or running programs in two machines are usually exchanging the information in the form of numbers, character strings and so on before being transmitted. The information should be changed to bitstreams because different computers use different encoding schemes.
- The Presentation layer is responsible for compatibility between these encoding methods.
- The Presentation layer at the sender's side changes the information from its sender dependent format.
- The Presentation layer at the receiving machine changes the common format into its receivers dependent format.
Example: Convert ASCII code to EBCDIC code.
2. Encryption
- The system must be able to assure privacy regarding the message or information as it also carries sensitive information.
- Encryption means that the sender transforms the original information or message to another form, this data after encryption is known as the ciphertext and this ciphertext sends the resulting message out over the network.
- Decryption concerned with the transform of the message back to its original form. This decrypted data is known as plain text.
3. Compression
- Data Compression means reduces the number of bits to be transmitted by this reduce the bandwidth of the data.
- Data Compression becomes particularly important in the transmission of multimedia such as audio, video, text, etc.
Related Tutorials
- IPV4 Addressing | Classful and Classless Addressing
- Subnetting and Supernetting in Computer Network
- Network Address Translation (NAT) in Computer Network
- Fixed Length and Variable Length Subnet Mask (FLSM & VLSM)
- Line Configuration in Computer Network
- Transmission Modes in Computer Network
- Data Link Layer: What It Is, Sublayers, Design Issues, Functions
- Physical Layer: What It Is, Design Issues, Functions
- Network Layer: What It Is, Design Issues, Responsibilities
- Session Layer: What It Is, Design Issues, Functionalities
- Transport Layer: What It Is, Design Issues, Functions, and Example
- Optical Fiber (Fiber Optics) in Computer Network
- Unguided Transmission Media in Computer Network
- Virtual LAN (VLAN) in Computer Network
- Virtual Storage Area Networking (VSAN)
Comments and Discussions!
Load comments ↻
- Marketing MCQs
- Blockchain MCQs
- Artificial Intelligence MCQs
- Data Analytics & Visualization MCQs
- Python MCQs
- C++ Programs
- Python Programs
- Java Programs
- D.S. Programs
- Golang Programs
- C# Programs
- JavaScript Examples
- jQuery Examples
- CSS Examples
- C++ Tutorial
- Python Tutorial
- ML/AI Tutorial
- MIS Tutorial
- Software Engineering Tutorial
- Scala Tutorial
- Privacy policy
- Certificates
- Content Writers of the Month
Copyright © 2024 www.includehelp.com. All rights reserved.
Presentation Domain Data Layering
26 August 2015
Martin Fowler
team organization
encapsulation
application architecture
web development
One of the most common ways to modularize an information-rich program is to separate it into three broad layers: presentation (UI), domain logic (aka business logic), and data access. So you often see web applications divided into a web layer that knows about handling HTTP requests and rendering HTML, a business logic layer that contains validations and calculations, and a data access layer that sorts out how to manage persistent data in a database or remote services.
On the whole I've found this to be an effective form of modularization for many applications and one that I regularly use and encourage. It's biggest advantage (for me) is that it allows me to reduce the scope of my attention by allowing me to think about the three topics relatively independently. When I'm working on domain logic code I can mostly ignore the UI and treat any interaction with data sources as an abstract set of functions that give me the data I need and update it as I wish. When I'm working on the data access layer I focus on the details of wrangling the data into the form required by my interface. When I'm working on the presentation I can focus on the UI behavior, treating any data to display or update as magically appearing by function calls. By separating these elements I narrow the scope of my thinking in each piece, which makes it easier for me to follow what I need to do.
This narrowing of scope doesn't imply any sequence to programming them - I usually find I need to iterate between the layers. I might build the data and domain layers off my initial understanding of the UX, but when refining the UX I need to change the domain which necessitates a change to the data layer. But even with that kind of cross-layer iteration, I find it easier to focus on one layer at a time as I make changes. It's similar to the switching of thinking modes you get with refactoring's two hats .
Another reason to modularize is to allow me to substitute different implementations of modules. This separation allows me to build multiple presentations on top of the same domain logic without duplicating it. Multiple presentations could be separate pages in a web app, having a web app plus mobile native apps, an API for scripting purposes, or even an old fashioned command line interface. Modularizing the data source allows me to cope gracefully with a change in database technology, or to support services for persistence that may change with little notice. However I have to mention that while I often hear about data access substitution being a driver for separating the data source layer, I rarely hear of someone actually doing it.
Modularity also supports testability, which naturally appeals to me as a big fan of SelfTestingCode . Module boundaries expose seams that are good affordance for testing . UI code is often tricky to test, so it's good to get as much logic as you can into a domain layer which is easily tested without having to do gymnastics to access the program through a UI 1 . Data access is often slow and awkward, so using TestDoubles around the data layer often makes domain logic testing much easier and responsive.
1: A PageObject is also an important tool to help testing around UIs.
While substitutability and testability are certainly benefits of this layering, I must stress that even without either of these reasons I would still divide into layers like this. The reduced scope of attention reason is sufficient on its own.
When talking about this we can either look at it as one pattern (presentation-domain-data) or split it into two patterns (presentation-domain, and domain-data). Both points of view are useful - I think of presentation-domain-data as a composite of presentation-domain and domain-data.
I consider these layers to be a form of module, which is a generic word I use for how we clump our software into relatively independent pieces. Exactly how this corresponds to code depends on the programming environment we're in. Usually the lowest level is some form of subroutine or function. An object-oriented language will have a notion of class that collects functions and data structure. Most languages have some form of higher level called packages or namespaces, which often can be formed into a hierarchy. Modules may correspond to separately deployable units: libraries, or services, but they don't have to.
Layering can occur at any of these levels. A small program may just put separate functions for the layers into different files. A larger system may have layers corresponding to namespaces with many classes in each.
I've mentioned three layers here, but it's common to see architectures with more than three layers. A common variation is to put a service layer between the domain and presentation, or to split the presentation layer into separate layers with something like Presentation Model . I don't find that more layers breaks the essential pattern, since the core separations still remain.
The dependencies generally run from top to bottom through the layer stack: presentation depends on the domain, which then depends on the data source. A common variation is to arrange things so that the domain does not depend on its data sources by introducing a mapper between the domain and data source layers. This approach is often referred to as a Hexagonal Architecture .
These layers are logical layers not physical tiers. I can run all three layers on my laptop, I can run the presentation and domain model in a desktop with a database on a server, I can split the presentation with a rich client in the browser and a Backed For Frontend on the server. In that case I treat the BFF as a presentation layer as it's focused on supporting a particular presentation option.
Although presentation-domain-data separation is a common approach, it should only be applied at a relatively small granularity. As an application grows, each layer can get sufficiently complex on its own that you need to modularize further. When this happens it's usually not best to use presentation-domain-data as the higher level of modules. Often frameworks encourage you to have something like view-model-data as the top level namespaces; that's OK for smaller systems, but once any of these layers gets too big you should split your top level into domain oriented modules which are internally layered.
Developers don't have to be full-stack but teams should be.
One common way I've seen this layering lead organizations astray is the AntiPattern of separating development teams by these layers. This looks appealing because front-end and back-end development require different frameworks (or even languages) making it easy for developers to specialize in one or the other. Putting those people with common skills together supports skill sharing and allows the organization to treat the team as a provider of a single, well-delineated type of work. In the same way, putting all the database specialists together fits in with the common centralization of databases and schemas. But the rich interplay between these layers necessitates frequent swapping between them. This isn't too hard when you have specialists in the same team who can casually collaborate, but team boundaries add considerable friction, as well as reducing an individual's motivation to develop the important cross-layer understanding of a system. Worse, separating the layers into teams adds distance between developers and users. Developers don't have to be full-stack (although that is laudable) but teams should be.
Further Reading
I've written about this separation from a number of different angles elsewhere. This layering drives the structure of P of EAA and chapter 1 of that book talks more about this layering. I didn't make this layering a pattern in its own right in that book but have toyed with that territory with Separated Presentation and PresentationDomainSeparation .
For more on why presentation-domain-data shouldn't be the highest level modules in a larger system, take a look at the writing and speaking of Simon Brown . I also agree with him that software architecture should be embedded in code.
I had a fascinating discussion with my colleague Badri Janakiraman about the nature of hexagonal architectures. The context was mostly around applications using Ruby on Rails, but much of the thinking applies to other cases when you may be considering this approach.
Acknowledgements
Web Application Architecture: How the Web Works
- Engineering
- Published: 25 Jul, 2019
- No comments Share
What is Web Application Architecture?
- addresses a particular problem, even if it’s simply finding some information
- is as interactive as a desktop application
- has a Content Management System
How does the web request work?
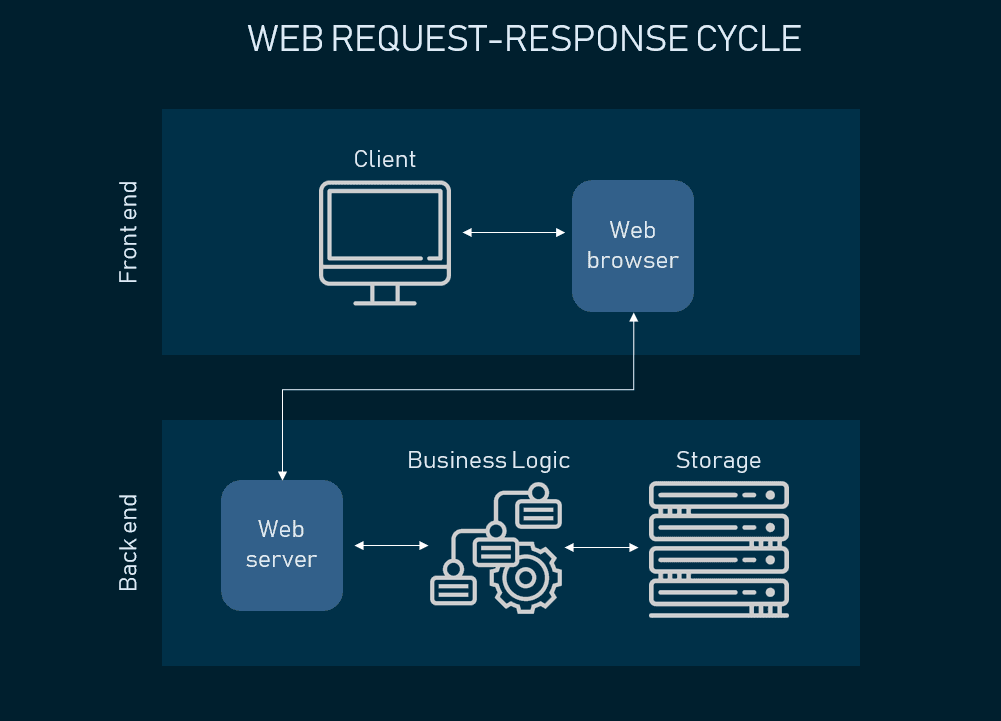
Web request-response cycle
Web application architecture components and Three-Tier Architecture
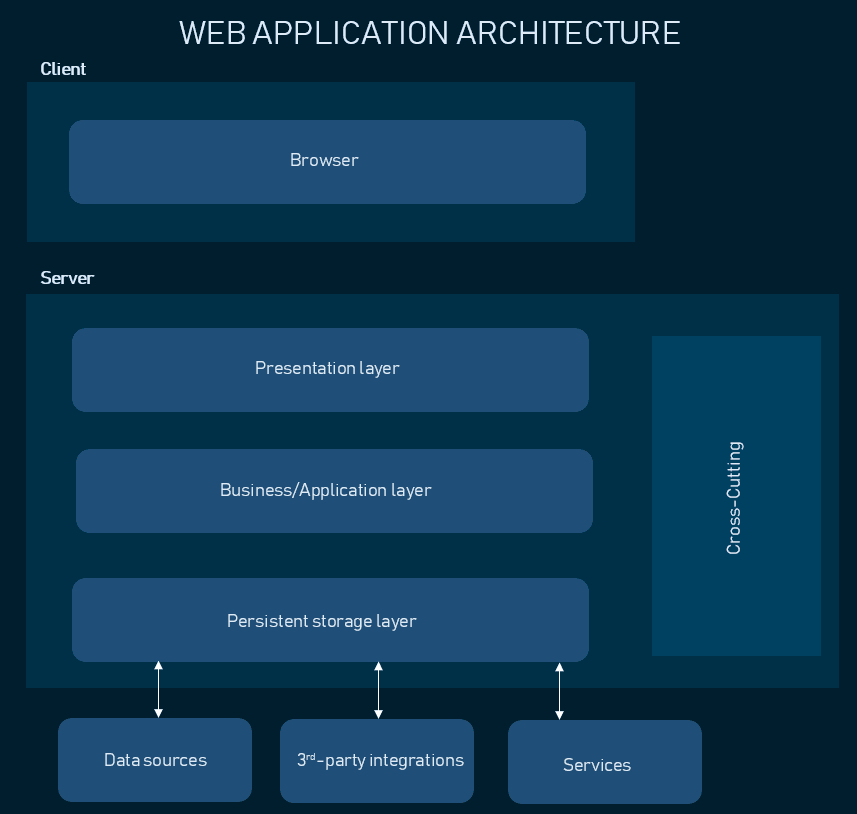
Web application architecture following the three-tier pattern
Presentation layer
Business layer, persistence layer, example #1. dynamic web pages, spas, and mpas, single page applications.
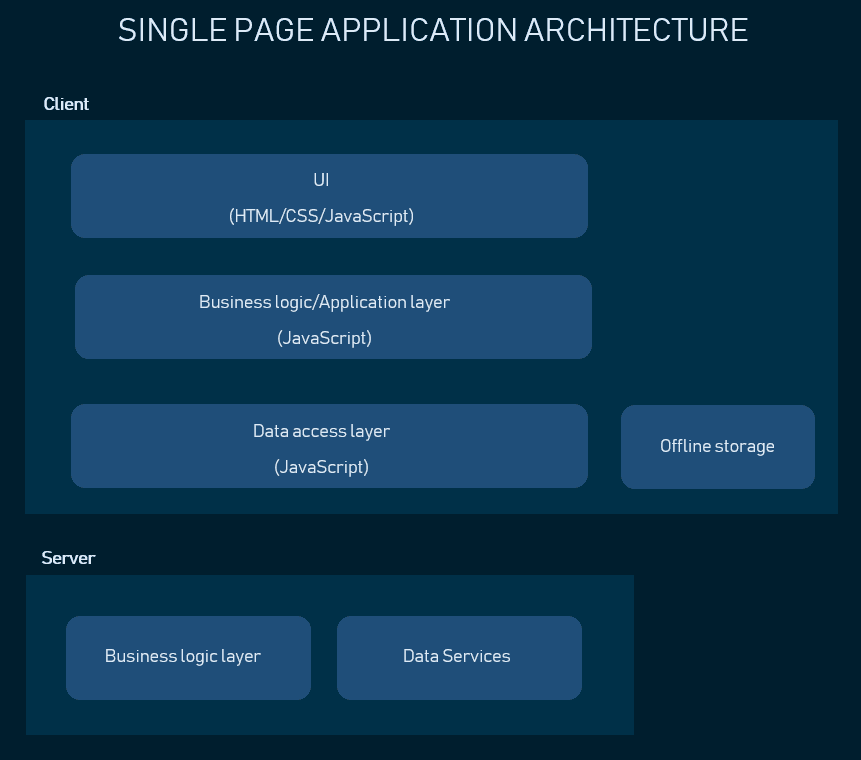
Single Page Application architecture
Multi-Page Applications
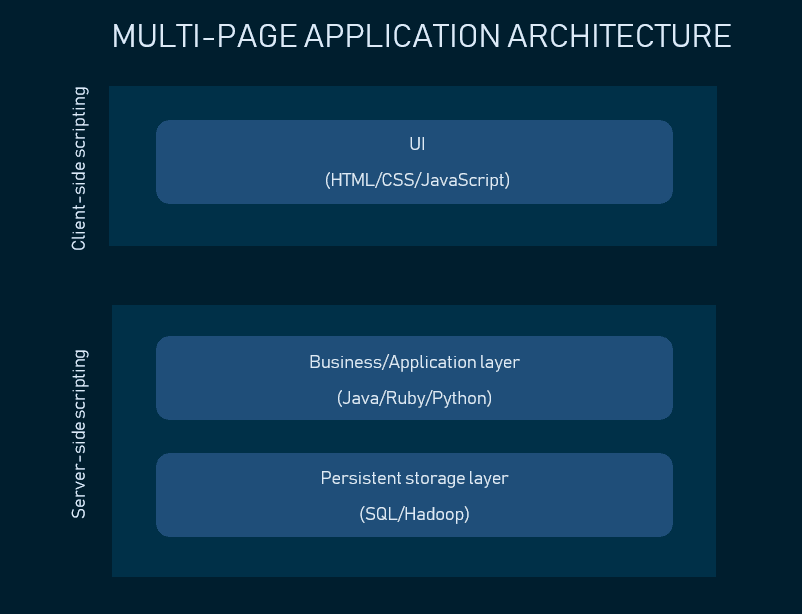
MPA architecture
Example #2. Enterprise applications
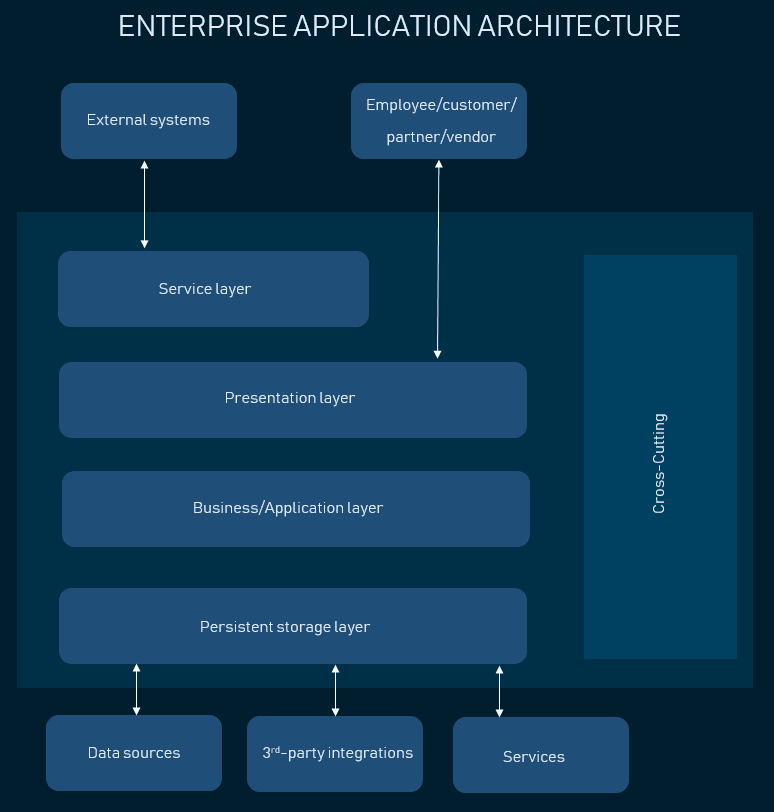
Enterprise application architecture
To conclude

INLS161-002 Spring 2017 Tools for Information Literacy Manning 117 M-W 3:35pm - 4:50 pm
Class Sessions
- Jan 11 | Intro
- Jan 16 | MLK Day
- Jan 18 | Clients
- Jan 23 | Servers
- Jan 25 | Networks
- Web Development
- Jan 30 | HTML
- Feb 01 | CSS
- Feb 06 | Practice
- Feb 08 | Scripting
- Feb 13 | XML (& JSON)
- Feb 15 | Images
- Feb 20 | Lab
- | Task 2.2a Final Instructions
- Document Markup
- Feb 22 | Object Layers
- Feb 27 | Graphics
- Mar 01 | Lab
- Dec 31 | Workflow
- Spreadsheets
- Mar 06 | Intro
- Mar 08 | Data Display
- Mar 13 | Spring Break
- Mar 15 | Spring Break
- Mar 20 | DB Tools
- Mar 22 | Lab
- Mar 27 | RDBMS
- Mar 29 | Tables
- Apr 03 | Relationships
- Apr 05 | Input/Output
- Apr 10 | SQL Queries
- Apr 12 | Complex Queries
- Apr 17 | Lab
- Presentations
- Apr 19 | Design
- Apr 24 | Delivery
- Apr 26 | Lab
- May 08 | Presentation Due
School Information
- ITS Security
- ITS Basic Security Checklist
- ITS Support
- Academic Calendar
- Carolina Events Calendar
Session Date: Wednesday Feb 01, 2017
CSS: The Presentation Layer of Web Design
Preparation for this session.

For the presentational layer class, read from Learning web design : a beginner's guide to HTML, CSS, Javascript, and web graphics , 4th Edition.
Look over Chapter 11. Cascading Style Sheets Orientation
If you wish, you may also want to look over Chapter 12. Formatting Text: (Plus More selectors) through Chapter 18. CSS Techniques, but you are not required to read them prior to class. We will touch on some of the topics, but will spend more time on the Chapter 11 topics.
the W3C discussion of CSS
× [ top/reload prep panel ]
Take a look at this example on the codepen site. Play around with the CSS. See if you can change the background color, font color and text sizes. We will go over more CSS examples in this session. Here's a flipped out CSS example using CSS3, just to show you how complicated CSS can get. Example "C" will mess with your head the most, I think. You will not be required to code CSS beyond the basics.
See the Pen CSS Introduction by Lawrence Jones ( @lblakej ) on CodePen .
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
The Presentation Layer of OSI Model
The presentation layer (Layer 6) ensures that the message is presented to the upper layer in a standardized format. It deals with the syntax and the semantics of the messages.
The main functions of the presentation layer are as follows −
- It encodes the messages from the user dependent format to the common format and vice versa, for communication among dissimilar systems.
- It is responsible for data encryption and decryption of sensitive data before they are transmitted over common channels.
- It is also responsible for data compression. Data compression is done at the source to reduce the number of bits to be transmitted. It reduces the storage space and increases the file transfer rate. It is particularly useful for transmission of large multimedia files.
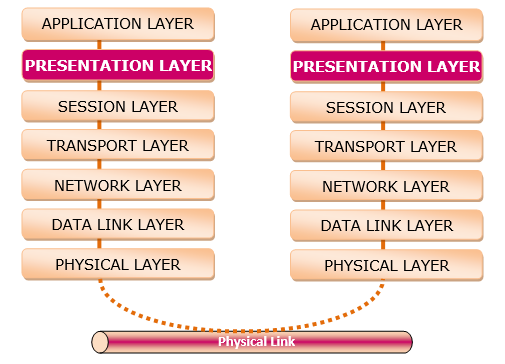
Related Articles
- The Physical Layer of OSI Model
- The Network Layer of OSI Model
- The Transport Layer of OSI Model
- The Session Layer of OSI Model
- The Application Layer of OSI Model
- The Data Link Layer of OSI Model
- Explain the functions of Presentation Layer.
- What is Presentation Layer?
- The OSI Reference Model
- What is a presentation layer?
- Advantages and Disadvantages of the OSI Model
- Computer Networks – Layers of OSI Model
- What is the OSI Reference Model?
- OSI Model in Computer Networking
- Why Does the OSI Reference Model Matter?
Kickstart Your Career
Get certified by completing the course
| Chapter 4. Layered Architecture for Web Applications | ||
|---|---|---|
| Part II. Architectures for the Web | ||
Chapter 4. Layered Architecture for Web Applications
Table of Contents
The first question that should be answered: Why the web is suitable for developing applications? It is not a difficult question, of course. In the World Wide Web Consortium (W3C) Architecture of the Web Recommendation paper various examples are given, notably one about a user who wants to see the weather in a place where she wants to travel to. The nature of the Internet - trafficking data over protocols from network to network - is a powerful resource that make communication between different places very fast and easy. This way computer programs can be made to improve the relation between systems and people, and what is seen today is that it happened.
Web applications are distributed applications, and hence are at least two-tiered. They act as a special kind of client-server applications, where a large portion of the functionality is “pushed” back to the server side despite the fact that the Web does not define what is behind the server.

The Web relies strongly in the client-server model, and it uses markup languages such as HTML and XML to transfer and represent data. Under it there are many programming and scripting languages that can dynamically process, modify and generate data, or give an user interface. This way, the development of Web applications can be put under the cover of software engineering but need to be extended. Web applications are multidisciplinary (software engineering, database modeling techniques, network computing, and effective interface design). They are built in a continuously changing environment where requirements are unstable and the user community is wider than before. Web applications handle information from various sources (text, graphics, video, audio) dealing with structuring, processing, storing and presenting this information.
The Three Layers Model
The nature of the Web is layered: it has formats over protocols and uses a client-server model. Therefore, it is natural that a layered architecture would be suitable for developing to the Web. We learnt that this model overcame the two layered client-server because of its scalability. Many different approaches to the aim of developing applications with different layers had been used along the years, but a clear pattern seems to appear frequently in various of them: the Three Layers Model (according to Kappel et al. 2006).

This model of web application development is very similar to the Service Layer/Domain Model/Data Source Layer set of design patterns from Martin Fowler’s collection, but receiving different names . In fact, the idea ( usually named 3-tier architecture, or expanded into n-tier architecture) is very general and widespread, so in this paper only the most common assumptions and uses are examined. [1]
Its conception is three layers, one over the other, being the application the set of them working together. The most external of them is the View Layer, that is the visible part of the application, the one that interacts with the user. The layer in the middle is the Business Logic Layer, which serves as an intermediate between the View (or presentation) and the innermost layer, that is the Data Layer. This last one is where all the data used by the application is stored.
The benefits of using layered models in software development are in the way that it is easier to know exactly what each part of the application does. It makes easier to construct the application, to debug it, and to maintain and reuse the code. For example, if it is needed to exchange some details in the presentation of the content but the business rules and data models do not change, only one layer is affected. Even for more complicated changes involving all of the application architecture there are benefices, so a plan can be created in the overall but specifying exactly where the changes need to be done.
The View Layer
The outermost layer in this kind of model deals with the presentation of the content and interaction with the user. It can be called view, presentation, UI. In this layer the application shows to the user what is needed to be seen and gives the tools for interaction. The exact kind of interaction depends on the application; one can create a web app that only shows information to the user without any kind of interaction, not even hyperlinks to be clicked, but such a case does not need an advanced architecture. In most cases the user will generate some input, send it for processing and then receive a feedback, that can be the final result or a step for further operations.
Following the example by W3C of the user that wants to see the weather in her trip destination, the presentation is where she sees the actual content. The content display is shown, and the user can interact with the provided controls to, for example, see weather in different periods of time or another places, and see pictures of it.
The technologies usually involved in this layer on the web development context are mainly the markup that is processed by the browser (HTML/ XHTML/ ...), the style of the page (CSS) and client-side scripts (Javascript/ Flash/ ...). All of these tools together can produce a rich environment for user interaction and content display. Of course it can be said that server-side scripts can be used to generate content, but at the final level these scripts produce the HTML that will be shown be the browser, so this role of the development can be subdivided: the content generation is created by the business logic layer (the next topic to be discussed) and then it is passed to the view layer, maintaining the logical division of the application. The browser shows the content initially written or produced by the server-side scripts, and the client-side scripts are able to modify that content. A Javascript code, for example, can be used to validate form data or even to create drag and drop interfaces. It interacts with HTML through a DOM tree, that is a representation of the document in memory. HTML5, the present (2014) trend for web development is praised for its flexibility, specially where it touches the concept of responsiveness, that is the ability to change the content disposition according to the screen size. This matters because, in current days, the availability of a page in different screen sizes and devices is extremely important. Having many possibilities like desktops, tablets, smartphones, wearable devices and even augmented reality or voice user interface, the range of technologies and targets for the view layer is very wide, and it shows both the importance of it to the user and reinforce the need of a logical division of the application for supporting such variety.
This layer communicates with the business logic layer under it, passing the information from the user and controlling it, then giving back any response it produces, not leaving any decisions of the application’s logic to be resolved by the UI. This passing of information is usually done through forms, like a user log-in in a system by giving username and password, but there are other ways. AJAX is an asynchronous way to pass information to the server and get responses. The cited a-synchronicity comes from the fact that in a form the content needs to be passed and then the response will come after a page refresh, but with AJAX the requested information, that is the result of the user’s action will come in the actual page. It saves time and gives to the user the impression that the application is really interacting with him.
The Business Logic Layer
The central layer of the model deals with the logic of the program. It receives data from the upper level and transforms it, using in the inner application logics. It also retrieves data from the deepest data level and uses it to the logics. And, by integrating these two processes, it can do modifications in both levels as well.
The Business Logic Layer contains the determinant part of the application logic. It includes:
performing all required calculations and validations
managing workflow
state management: to keep track of application execution
session management: to distinguish among application instances
user identification
service access: to provide application services in a consistent way
managing all data access for the presentation layer
The Business Logic Layer is generally implemented inside an Application server (like Microsoft Transaction Server, Oracle Application Server, or IBM WebSphere). The Application server generally automates a number of services like transactions, security, persistence, connection pooling, messaging and name services.
Using the same example of the last session, of the user that wants to see the weather in a specific place, when the information is given by the user the application retrieves it and process. For example, the user wants to see the weather forecast for two days. The application receives its request from the UI and the data is sent to the server. A PHP script catches it and then make the calls for the lower level to get the needed data. When a response comes, being it the desired information or a failed request, it is dealt and then prepared to be sent again to the upper level.
The tools used in this level are usually server-side scripts like PHP,ASP.NET, Ruby or CGI. There is even a solution that uses server-side Javascript, called node.js. These technologies, following the information feeding that comes from the upper level, can do any computational pro- cessing that is needed. The CGI (Common Gateway Interface) scripts are an older technology that defines communication way between a server and the content-generated program, in this context called CGI script. One of the most remembered languages when talking about CGI scripts is Perl. The other languages here cited have a similar approach, by running inside a server. PHP is related to Perl, being as well a scripting language and having similar philosophies. It is one of the most popular languages, being the implementation language of important content management systems as Drupal or Wordpress. Ruby have a large popularity too, especially with the framework Ruby on Rails. Applications as Github or Redmine are built using it. There are many others, of course, and different uses of them, one example being C used as CGI or the Java Server Pages (JSP).
The Data Layer
The deepest level in the layered architecture, the data layer deals with data retrieval from its sources. It is an abstraction to get the plain data, that can be in a wide variety of forms. Once again, it plays a huge role on the reusability and exchange of technologies: if one data source is changed to another, but the proper data is still the same, a good layered design can help by providing the same data to the upper level with the same interfaces, changing only its inner logic.
In the example given in this paper of the weather forecast, the requirement by the user for the next days forecast will come to this level as a request for the forecasts that it may have. Then a search will be made in the data using the given parameters, and then the data (or some information about not getting it) will be sent again to the upper level.
The technologies used in this layer are database management systems like MySQL or PostgreSQL for relational databases, NoSQL management systems like MongoDB or Apache Cassandra, or even plain XML files or text files. For the management systems usually an API will be used for making queries and retrieving data, and for the plain text ones a script will do the needed operations. Inside it there can be any level of sophistication desired by the application designer, so there can be integrity checks, stored procedures, and virtually anything needed to maintain the data in the desired state.
Deepest in the Data Layer: NoSQL and NewSQL
Inside the Data Layer, as it was outlined, many different technologies can be used. Most of the web applications currently active use relational databases, but now the market is seeing a change of paradigm in the form of the NoSQL. NoSQL is a general way to identify non-relational databases. Fowler summarises some common characteristics that NoSQL databases share:
Not using the relational model
Running well on clusters
Open-source
Built for the 21st century web estates
The key points NoSQL supporters use to justify the need for it is that relational databases are not the best solution for any kind of problem, being a problem of its own the uses. They say it is heavy, slow, and non-scalable to use the relational databases, so the use of NoSQL can be a good way to solve these kinds of problems. The use of NoSQL nowadays seems related to startups that use innovating new technology and social web services such as Facebook and Amazon, that have a great amount of data [2] to deal with and have the need to find new ways to use it.
In fact, that is this demand of large data processing. Under the label of big data lies the concept of large quantities of data generated in the last few years and from different sources and in a variety of different formats. The processing of this kind of data leads to a wide range of uses, from healthcare to criminalistics inferences. Of course, new challenges arises with this perspective. The drawbacks come from the nature of the data - massive, disperse, heterogeneous. This is why NoSQL can be seen as a solution - it thinks about this kind of problem, trying to solve it.
As of 2014, there are four important categories of NoSQL databases:
key-value stores , that are basically hash tables
column family stores , which aim is to deal with vast collections of data spread amongst many different machines
document databases , versioned documents that are collections of other key-value collections
and graph databases , where the data is presented as a graph, and then it is possible to divide easily into different machines and the queries are more data-specific than the relational ones
A topic that attracts attention when it comes to the issue of scalability and performance of databases is the so-called NewSQL. It is more a way to recognise “ the various emerging database products at this particular point in time”. The authors writing about it use the term as an identification of vendors that provide SQL databases that are high-performance and scalable, in the market that is also aimed by NoSQL providers. The aims of NewSQL are also related to the Big Data paradigm. [3]
[1] Sometimes tier is different from layer. For it, layers mean the logical distinction of the applications integral parts, and tiers mean the physical structures in where the application runs (networks, computers, servers). But in this work the two words are used as synonyms, and with the meaning of layer, not being the objective to discuss physical tiers.
[2] “The increasing amount of data in the web is a problem which has to be considered by successful web pages like the ones of Facebook, Amazon and Google. Besides dealing with tera- and petabytes of data, massive read and write requests have to be responded without any noticeable latency”
HECHT, Robin and JABLONSKI, Stefan. NoSQL Evaluation, A Use Case Oriented Survey.
[3] “The NoSQL projects were developed in response to the failure of existing suppliers to address the performance, scalability and flexibility requirements of large-scale data processing, particularly for Web and cloud computing applications. NewSQL and data-grid products have emerged to meet similar requirements among enterprises, a sector that is now also being targeted by NoSQL vendors.”
ASLETT, Matthew. NoSQL, NewSQL and Beyond: The answer to SPRAINed relational databases.
| Part II. Architectures for the Web | The MVC pattern - useful but not a silver bullet |
The OSI Model
What is the osi model.
How a single bit travels from one computer to the next is a complex concept. In 1984, the open systems interconnection (OSI) model was published as a framework for network communication. The model breaks down computer network communication into seven layers. All of the layers work together to create a digital message. The message is built as it moves down the protocol stack. However, it is not sent to another network until it reaches the physical layer.
The model helps IT, computer science, and cybersecurity professionals understand how a single bit travels from one computer to the next by breaking the system into these layers.
From physical devices to user interfaces (UI), this model explains the communication role of each layer in overall computer networking. This article will start by introducing the Physical Layer (Layer 1).
Layer 1: the physical layer
The physical layer is where data moves across network interfaces as digital signals. Additionally, this is where the transmitting and receiving of network communication occurs. Starting with the Application Layer the message moves down the OSI model, and it eventually reaches the Physical Layer for transmission. When the message is received by the physical layer, the message will then move up the OSI layers until it reaches the final application layer.
Layer 2: data-link layer
Electrical signals received (or transmitted) to the physical layer are linked and translated to digital logic in the data-Link layer . Computer devices may be networked at the Data-Link layer, but only as a Local Area Network (LAN). Connecting a LAN to another LAN occurs at Layer 3.
Within Layer 2, the Protocol Data Unit (PDU) known as a frame consists of a header, footer, and data. Understanding how a frame is structured is important for network traffic analysis.
Additionally, within Layer 2, physical addresses are assigned and are also known as MAC addresses and/or hardware addresses in networking. MAC addresses are unique to each device on a local network. They are 48-bits in length and are assigned in hexadecimal characters.
Some other things to note about Layer 2 is that there are a few protocols that reside in it that we should know about:
- Ethernet : The most common type of LAN, Ethernet is the standard used to connect computing devices, routers, and switches in a wired network.
- IEEE 802.11 : “Wi-Fi” or “Wireless LAN.”
- Fiber Distributed Data Interface (FDDI) : Network standard for fiber optic LAN connections.
- Link Layer Discovery Protocol (LLDP) : A Link Layer protocol used for advertising neighbors, identity, and capabilities on a LAN.
- Address Resolution Protocol (ARP) : Converts and links Internet Protocol (IP) addresses to MAC addresses on a LAN.
- Cisco Discovery Protocol (CDP) : Similar to LLDP, but Cisco proprietary. The protocol collects neighbor information of directly connected LAN devices.
Additionally, Layer 2 is split into two sublayers:
- Logical Link Control (LLC) : Responsible for establishing the logical link between devices on a local network.
- Media Access Control (MAC) : Responsible for the procedures used by devices across a network medium.
Layer 3: network layer
When we think of the internet, we are thinking of interconnected networks. Interconnecting networks refer to a Local Area Network (LAN) connection to neighboring or remote networks. Layer 3 of the OSI model, the network layer , is where internetworking takes place and is where logical addresses are assigned to networked devices. A primary function of this layer is to route network packets from one LAN to another. Routing requires IP addresses and logical mapping of other networks across the internet to properly deliver messages. Another important function of Layer 3 is its ability to fragment and reassemble large communication. When Layer 3 passes a message down to Layer 2 for transmission, message length limits may be encountered in some cases.
Additionally, Layer 3 is the layer where the protocols used to route communication between networks reside. A few common network protocols are:
- Internet Protocol (IP) : IPv4 and IPv6 are two versions of IP, and IPv4 is the most common protocol of the Internet .
- Internet Protocol Secure (IPSec) : A more secure version of IP which leverages cryptography.
- Routing Information Protocol (RIP) : Distance-vector routing protocol that uses hop count as a metric of routing.
- Enhanced Interior Gateway Routing Protocol (EiGRP) : Cisco proprietary. A distance-vectoring protocol used for automating network configurations and routing decisions.
- Internet Control Message Protocol (ICMP) : Network protocol used for error reporting of network issues.
- Border Gateway Protocol (BGP) : A routing protocol designed to exchange routing information automatically on the internet.
Within Layer 3, the Protocol Data Unit (PDU) is the packet . Packets encapsulate data intended for transmission with header and footer data.
The IPv4 protocol encapsulates data with IPv4 header information necessary for delivery. For example, the 32-bit packet format contains the source address, the destination address, protocol, time-to-live (TTL), etc. in the IPv4 header data.
Layer 4: transport layer
The transport layer , Layer 4, is responsible for being the go-between the abstract layers of the OSI model (Layers 7-5) and the concrete communication layers (Layers 3-1).
Depending on the type of application, the transportation of that application’s communication will need to be handled in a specific way. For example, basic web browsing communication uses Hypertext Transfer Protocol (HTTP) . HTTP communicates via a specific connection service type and port. The transport layer is responsible for delivering/receiving the HTTP communication and maintaining the connection throughout the HTTP communication.
The Protocol Data Unit (PDU) at Layer 4 is known as a data segment . Segmentation is the process of dividing raw data into smaller pieces. Once the raw data is packaged from the higher application layers it is segmented at the transport layer before being passed to the Network Layer.
The transport layer protocols are divided into two categories depending on their connection service type:
Connection-oriented services
This connection type establishes a logical connection between two devices prior to beginning communication across a network. Connection-oriented protocols typically maintain service connection by following a set of rules that initiate, negotiate, manage, and terminate the communication. The Transport Layer protocols will also retransmit any data that is received without acknowledgment. The most common Connection-Oriented protocol is the Transmission Control Protocol (TCP) and its process to manage a connection between two devices is called the Three-Way Handshake . In TCP communication, the communicating devices typically share a client/server relationship where a client initiates communication with a service. The handshake involves the process of sending special TCP messages to synchronize a state of negotiated connection in communication.
Connectionless services
In connectionless communication, the protocol does not establish a connection between client and server. Instead, once a request is made to the server, the server sends all data without initiation, negotiation, or management of connection. Connectionless protocols also do not attempt to correct any interruptions in data transmission. Once the server sends the data, the server is not concerned if the client receives it.
When TCP or UDP are used to establish communication, the communication is assigned a port as the Layer 4 address. A port is a logical assignment given to processes and their respective application protocols on a computing system. A few important facts to memorize about ports are:
- There are 65,535 valid port numbers available to assign to a communication process.
- Ports 0 - 1023 are Well-Known Ports : Assigned to universal TCP/IP application protocols. These protocols are the most common such as HTTPS, SSH, FTP, DNS, and the list goes on. They are registered to these protocols by a global
- Ports 1024 - 49,151 are Registered Ports : Reserved for application protocols that are not specified as universal TCP/IP application protocols.
- Ports 49,152 - 65,535 are Private/Dynamic Ports : These ports may be used for any process without the need to register the port with the global assigning authority.
- When TCP and IP are used together, a Layer 4 port and a Layer 3 IP address are assigned to the connection. This is called a socket. For example, 8.8.8.8:443 is a socket indicating that communication to IP address 8.8.8.8 is to connect to port 443 on the server.
Layer 5: session layer
The session layer starts, manages, and terminates sessions between end-user application processes. Sessions are considered the persistent connection between devices. A session is application-focused; sessions are not concerned with layers 1-4. Instead, the session layer controls dialog between two networked devices. It is considered to facilitate host-to-host communication. Sessions dialog may be controlled through synchronization checkpoints, and through management of communication modes. There are two modes of communication permitted at Layer 5:
- Half-Duplex : Communication travels in both directions between sender and receiver, but only one device may transmit a message at a time.
- Full-Duplex : Communication travels in both directions between sender and receiver, and messages may be sent simultaneously in either direction.
The session layer resembles a phone conversation. For example, when a person picks up a phone and calls someone else a session is created. Once the communication on the call is completed, the session is terminated by hanging up the phone. In computing, software applications are making the phone call and establishing a session.
Two common Layer 5 protocols still used today are:
- Remote Procedure Call (RPC)
Layer 6: presentation layer
The presentation layer is primarily responsible for presenting data so that the recipient will understand the data. Data formatting and encoding protocols apply at Layer 6 to ensure data is legible and presented properly in the application receiving it. Data compression is also a function of Layer 6. If necessary, data may be compressed to improve data throughput over network communication.
Some common Layer 6 protocols are ASCII , JPEG , GIF , MPEG , and PNG .
Another main function of the presentation layer is the encryption and decryption of data sent across a network. Most encryption communication protocols straddle multiple layers of the OSI model, but the actual encryption function is Layer 6.
Two of the most common secure communication protocols are:
- Transport Layer Security (TLS)
- Secure Socket Layer (SSL)
Layer 7: application layer
The topmost layer of the OSI model is the application layer . On computer systems, applications display information to the user via the UI.
Note : Software applications running on a computer are NOT considered to reside in the application layer. Instead, they leverage application layer services and protocols that enable network communication.
For example, the user can craft messages and access the network from the application layer. A web browser application allows a user to access a web page. The user may input information and receive information through the web browser. However, the application layer protocol HTTP performs the network communication function. The web browser and HTTP work closely together, and the distinction between the two may be subtle. Yet, HTTP is the web browsing protocol for all web browser applications. In contrast, no single web browser software exclusively utilizes HTTP.
HTTP is one of many common application layer protocols. Below are a few additional protocols to know. It is also good practice to memorize the associated port assigned to the protocols:
| Protocol | Port Number(s) | Description |
|---|---|---|
| (DNS) | 53 | Translates internet names to their globally registered IP addresses. For example, “google.com” is registered in global DNS as IP address 8.8.8.8. |
| (HTTPS) | 443 | Sends data to and from web browsers and web servers, but securely with the Secure Socket Layer (SSL) protocol. |
| FTP | 20, 21 | Transfers files from a client to a server and vice versa. |
| (SSH) | 22 | Connects to computers remotely and in a secure, encrypted way. |
| (SMTP) | 25 | Sends and receives email. |
| (DHCP) | 67 | Automatically assigns IP addresses to devices on a network. |
| (IRC) | 194 | Used in a client/server method. IRC clients communicate through an IRC server. |
| (POP3) | 110 (unsecured), 995 (secured) | Used for email where the client receives mail by downloading it locally to a computer from a server mailbox. |
The OSI model breaks down computer network communication into seven layers. All of the layers work together to create a digital message. Understanding the OSI model will help you communicate with other network technologists. Computer networking may seem complex, but, with a bit of study, you can gain this knowledge to become an effective Cybersecurity Analyst.
Learn More on Codecademy
Cybersecurity analyst interview prep, code foundations.
The Three Layers of Web Design
All websites combine structure, style, and behaviors
- Why Separate the Layers
HTML: The Structure Layer
Css: the styles layer, javascript: the behavior layer.
- PHP Programming
- Java Programming
- Javascript Programming
- Delphi Programming
- C & C++ Programming
- Ruby Programming
- Visual Basic
Jennifer Kyrnin is a professional web developer who assists others in learning web design, HTML, CSS, and XML.
- University of California
- University of Washington
People who work in the web design industry liken front-end website development to a three-legged stool. These three legs—the three layers of web development—comprise the structure, style, and behaviors of a site.
Why Should You Separate the Layers?
When you're creating a web page, its structure should be relegated to your HTML, visual styles to the CSS , and behaviors to scripts. Some of the benefits of separating the layers are:
- Shared resources : When you write an external CSS or JavaScript file, any page on the site can use that file. If you need to make a change to that file, perhaps to update some typographic styles on the website, every page that uses that stylesheet will get the change. There is no need to edit every page of the website individually, which could be a grueling undertaking for a large website.
- Faster downloads : After the script or stylesheet has been downloaded by your customer for the first time, it is cached by the web browser. Because these shared resources are now contained in the browser cache , other pages that are requested in the browser load more quickly, which improves overall page speed and performance.
- Multi-person teams : If you have more than one person working on a website at once, use version-control systems that allow files to be checked in and out to ensure that everyone is working with the latest versions . This process is much harder to do if styles and behaviors are intertwined with structure documents.
- SEO : A site that demonstrates a clear separation of style and structure is likely to perform better for search engines because they can crawl that content more effectively and understand the page without getting bogged down in visual-style and behavior information.
- Accessibility : External style sheets and script files are more accessible to people and to browsers. Software such as screen readers can process content from the structure layer more easily without dealing with styles that they cannot use anyway.
- Backward compatibility : A site that is designed with separate development layers is more likely to be backward-compatible because browsers and devices that can't use certain CSS styles or that have JavaScript disabled can still view the HTML. You can then enhance your website progressively with features for the browsers that support them.
The structure or content layer of a web page is the underlying HTML code of that page. Just as a house's frame creates a strong foundation upon which the rest of the house is built, a solid foundation of HTML creates a platform upon which a website can be created.
The structure layer is where you store all the content that your customers want to read or look at. HTML structure can consist of text and images, and it includes the hyperlinks that visitors will use to navigate around the website. This information is coded in standards-compliant HTML5 and can include text, images, and multimedia (video, audio, etc.).
Every aspect of a site's content should be represented in the structure layer. This separation allows customers who have JavaScript turned off or who can't view CSS access to the entire website, if not all of its functionality.
This layer dictates how a structured HTML document will look to a site's visitors and is defined by CSS (Cascading Style Sheets). These files contain stylistic instructions for how the document should be displayed in a web browser. The style layer usually includes media queries that change a site's display based on screen size and device .
All visual styles for a website should reside in an external stylesheet. You can use multiple stylesheets, but every CSS file requires an HTTP request to fetch it, affecting site performance .
The behavior layer makes a website interactive, allowing the page to respond to user actions or to change based on a set of conditions. JavaScript is the most commonly used language for the behavior layer, but CGI and PHP are very frequently used, too.
When developers refer to the behavior layer, most of them mean the layer that is activated directly in the web browser. Use this layer to interact directly with the Document Object Model. Writing valid HTML in the content layer is important for DOM interactions in the behavior layer. When you build in the behavior layer, you should use external script files, just as with CSS, to optimize speed and performance.
- What Is CSS and Where Is It Used?
- The Correct Usage of the HTML P and BR Elements
- The 7 Best Programming Languages to Learn for Beginners
- Tips for Creating a Background Watermark on a Web Page
- Understanding the 3 Types of CSS Styles
- How to Insert a CSS Comment
- Styling a Notepad Created Web Page with CSS
- How to Wrap Text Around an Image
- Web Design: Understanding Common Abbreviations
- Top 10 Must-Have Web Designer Job Skills
- What Is 'Graceful Degradation' in Web Design?
- Avoiding Inline Styles for CSS Design
- The Benefits of Cascading Style Sheets
- Show and Hide Text or Images With CSS and JavaScript
- How to Block a Web Page From Printing With CSS
- How to Detect Hits From Mobile Devices on Web Pages
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
Design Issues in Presentation Layer
- Design issues in Session Layer
- Design Issues in Network Layer
- Design Issues in Physical Layer
- Design Issues in Data Link Layer
- Presentation Layer in OSI model
- What is Juxtaposition in Design?
- Design Iteration
- Layout and Views in Presentation Tool
- What is Universal Design in UX?
- Industrial Designer Jobs in Spain
- Inclusive Design Best Practices
- Mediator Design Pattern in Java
- What is Typography in UI Design?
- Difference Between Presentation and Representation
- How to Edit a Powerpoint Presentation?
- Design a Layered Image Page Template using HTML and CSS
- Hero Section in UI Design
- What are Presentation Graphics?
- Mediator design pattern
The syntax and the semantics of the information exchanged between two communication systems is managed by the presentation layer of the OSI Model .
Before going through the design issues in the presentation layer, some of its main functions are:
- Translation – It is necessary that the information which is in the form of numbers, characters and symbols needs to be changed to the bit streams. The presentation layer handles the different encoding methods used by different machines .It manages the translation of data between the format of network requires and computer.
- Encryption – The data encryption at the transmission end as well as the decryption at the receiver end is managed by the presentation layer.
- Compression – In order to reduce the number of bits to be transmitted, the presentation layer performs the data compression. It increases efficiency in case of multimedia files such as audio, video etc.
Design issues with Presentation Layer :
- Standard way of encoding data – The presentation layer follows a standard way to encode data when it needs to be transmitted. This encoded data is represented as character strings, integers, floating point numbers, and data structures composed of simple components. It is handled differently by different machines based on the encoding methods followed by them.
- Maintaining the Syntax and Semantics of distributed information – The presentation layer manages and maintains the syntax as well as logic and meaning of the information that is distributed.
- Standard Encoding on the wire – The data structures that are defined to be exchanged need to be abstract along with the standard encoding to be used “on the wire”.
Please Login to comment...
Similar reads, improve your coding skills with practice.
What kind of Experience do you want to share?
Lesson 2: Content, Structure, Presentation, and Behavior
Earlier in this course you learned to control the presentation of your web content using Cascading Style Sheets (CSS). In this lesson, you will learn how to control web page presentation using your web authoring software. Some web authoring software provides direct support for CSS, while other products handle presentation in other ways. which may or may not be compliant with web standards. Which category does your web authoring software fall into? How could its support for CSS be improved?
Learner Outcome
At the completion of this exercise, you will be able to:
- control and manipulate the style of HTML elements on a web page using web authoring software.
Examples of Style Techniques in Common Web Authoring Tools
CSS is integrated tightly into Dreamweaver, so there are many ways to define and edit styles and assign them to various elements on the page. Here are a few tips:
- From the main menu, select Format > CSS Styles, then you can either select "New..." to create a new style sheet, or "Attach Style Sheet..." to load an existing one.
- From the main menu, select Modify > CSS Styles. A window appears that shows all styles that apply to the page, or to the selected content. Double-clicking any CSS selector within this window brings up a CSS Rule Definition window like the one shown below. This window can be used to define styles simply by selecting options. You don't have to remember the names of all those CSS properties!
- To assign a class to an element, just right click on any element on your web page, then select "CSS Styles" from the menu that pops up. If a style sheet has been associated with the web page, you will see a list of CSS classes and can select the one you want to apply to that element.
Like Dreamweaver, KompoZer includes a dialog box from which you can create CSS style definitions by selecting values for various properties. As of version 0.8b3, this feature is accessed from the main menu by selecting Tools > CSS Editor.
After you've defined CSS classes, these appear in a dropdown list on the toolbar, so they can easily be assigned to any element just by selecting the element, then choosing the desired class from the toolbar.
Below is a screen shot of the CSS Editor in KompoZer:
Other Web Authoring Software
- If a web authoring tool supports CSS, it is typically easy to find in the menus or toolbars. If you can't find any options related to CSS in your software, or you can't figure out how to use them, try searching the software's Help system for "CSS", and explore the matching help pages to learn about techniques.
- If a web authoring tool has little or no documentation concerning CSS, it probably has little or no support for CSS, and is instead relying on outdated non-standard techniques for controlling the presentation of web content. Web authoring tools that don't support CSS should be avoided.
- Make a copy of your portfolio, including all files, especially the CSS file. Then, using your web authoring software, open the home page of the new copy using your web authoring software. Important! Be sure you open the copy, not the original.
- Now play with your web authoring tool's CSS features. Try to find and modify as many CSS properties as possible to change the appearance of your web page. Try to make your web page look better, but if you already had the perfect design, just try to make it look different .
- When you're satisfied with the look of your new page, save all related files (most web authoring software has an option in the File menu for this).
Share your newly stylized portfolio home page with your instructor. Be prepared to explain to the instructor which styles you changed and how, in order to attain the current look and feel of your web page. When you're finished, proceed to the next lesson .

IMAGES
VIDEO
COMMENTS
Prerequisite : OSI Model. Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required ...
The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified ...
Key protocols: Protocols like HTTP, FTP and SMTP operate at this layer, enabling services such as web browsing, file transfers and email communications. Layer 6: Presentation Layer. Role: The Presentation Layer acts as a translator, converting data formats from the application layer into a network-compatible format and vice versa. It ensures ...
The Web Presentation Layer, also known as the user interface layer, is the web application layer responsible for presenting data and interacting with users. The Model-View-Controller (MVC) pattern ...
Presentation layer: This is the user interface of the web application. It is responsible for the visual aspects of the web application, such as the design of the user interface, the layout of the ...
The presentation layer typically includes web components such as controllers, views, and templates. Business Layer. The business (or application) layer handles the web application 's business logic. It contains controllers, services, and models responsible for performing the necessary actions to fulfill user requests.
Presentation Layer: Responsible for handling user input and displaying the user interface. Business Logic Layer: Contains the application's business rules and logic.
The presentation layer contains the components that implement and display the user interface and manage user interaction. This layer includes controls for user input and display, in addition to components that organize user interaction. Figure 1 shows how the presentation layer fits into a common application architecture.
The presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. On the sending system it is responsible for conversion to standard, transmittable formats. [7] On the receiving system it is responsible for the translation, formatting, and delivery of ...
The presentation layer is the 6 th layer from the bottom in the OSI model. This layer presents the incoming data from the application layer of the sender machine to the receiver machine. It converts one format of data to another format of data if both sender and receiver understand different formats; hence this layer is also called the ...
Each layer of the layered architecture pattern has a specific role and responsibility within the application. For example, a presentation layer would be responsible for handling all user interface and browser communication logic, whereas a business layer would be responsible for executing specific business rules associated with the request.
Functionalities of the Presentation Layer. Specific functionalities of the presentation layer are as follows: 1. Translation. The processes or running programs in two machines are usually exchanging the information in the form of numbers, character strings and so on before being transmitted. The information should be changed to bitstreams ...
web development. One of the most common ways to modularize an information-rich program is to separate it into three broad layers: presentation (UI), domain logic (aka business logic), and data access. So you often see web applications divided into a web layer that knows about handling HTTP requests and rendering HTML, a business logic layer ...
Most web applications are developed by separating its main functions into layers, or tiers. This allows you to easily replace and upgrade each layer independently. This architectural pattern is called Multi- or Three-Tier Architecture. Web application architecture following the three-tier pattern. Presentation layer
For the presentational layer class, read from Learning web design : a beginner's guide to HTML, CSS, Javascript, and web graphics, 4th Edition. Look over Chapter 11. Cascading Style Sheets Orientation. If you wish, you may also want to look over Chapter 12. Formatting Text: (Plus More selectors) through Chapter 18.
The Presentation Layer of OSI Model. The presentation layer (Layer 6) ensures that the message is presented to the upper layer in a standardized format. It deals with the syntax and the semantics of the messages. The main functions of the presentation layer are as follows −. It encodes the messages from the user dependent format to the common ...
The nature of the Web is layered: it has formats over protocols and uses a client-server model. Therefore, it is natural that a layered architecture would be suitable for developing to the Web. We learnt that this model overcame the two layered client-server because of its scalability. Many different approaches to the aim of developing ...
In Domain-Driven Design (DDD), a layered architecture is often used to organize the solution domain into different parts. For example, it may consist of a presentation layer, an application layer, a domain layer, and an infrastructure layer. The presentation layer handles user interaction, the application layer implements the use cases and ...
The transport layer, Layer 4, is responsible for being the go-between the abstract layers of the OSI model (Layers 7-5) and the concrete communication layers (Layers 3-1). Depending on the type of application, the transportation of that application's communication will need to be handled in a specific way.
The Three Layers of Web Design. All websites combine structure, style, and behaviors. People who work in the web design industry liken front-end website development to a three-legged stool. These three legs—the three layers of web development—comprise the structure, style, and behaviors of a site.
Prerequisite - Layers of OSI Model Data-link layer is the second layer after the physical layer. The data link layer is responsible for maintaining the data link between two hosts or nodes. Before going through the design issues in the data link layer. Some of its sub-layers and their functions are as following below. The data link layer is divided
From the main menu, select Modify > CSS Styles. A window appears that shows all styles that apply to the page, or to the selected content. Double-clicking any CSS selector within this window brings up a CSS Rule Definition window like the one shown below. This window can be used to define styles simply by selecting options.