History Cooperative

Who Invented the Internet? The Origin and History of the Internet
The Internet has become an essential part of modern life, a global network that connects billions of computers and devices, allowing people to access data, communicate, and share information worldwide.
Table of Contents
Who Invented the Internet and What is the Internet?
The Internet was invented by Vint Cerf and Robert Kahn , who were crucial in creating the Transmission Control Protocol (TCP/IP), which allowed different computers to communicate on a single network. Their work laid the foundational protocols that enable the Internet to function.
READ MORE: The First Computer: Technology that Changed the World
The Internet is a vast global network that connects computers across the world, allowing them to share data and resources. It’s not the work of a single person or entity; rather, it was developed through the contributions of many computer scientists and engineers. The question of “who invented the Internet” is complex because the Internet as we know it today was built on a series of technological advancements and innovations.
The Internet’s origins can be traced back to the Advanced Research Projects Agency (ARPA) of the United States Department of Defense in the late 1960s. The project, known as ARPANET, initially connected four university computer science departments in California, Los Angeles, and Stanford University, allowing computer users to access data and resources from other networks. This was the first workable prototype of the Internet, which utilized packet-switching technology to facilitate transmitting messages between computers on the network. ARPANET’s success demonstrated the potential of a communication network to link computers across vast distances.
As technology evolved, computer networks expanded beyond military and academic circles into the public and commercial domains. The introduction of the domain name system and the World Wide Web by Tim Berners-Lee in the early 1990s transformed the Internet from a niche tool for computer scientists into a powerful medium for the online world, accessing web pages and transmitting data.
READ MORE: Who Invented the World Wide Web? True Story of the Internet
Berners-Lee’s work made it easier for computer users to navigate the Internet, leading to the explosive growth of web content and Internet access around the globe.
Paul Baran played a key role in the development of the Internet, particularly through his work on packet switching, a fundamental technology that enables the Internet to send and receive data across computer networks. As a computer scientist working at the RAND Corporation during the Cold War , Baran proposed a communication network designed to survive nuclear attacks.
His idea was revolutionary: instead of using traditional communication methods, data would be broken into small blocks, or packets, and sent across a network through various paths, ensuring the information could still be received even if parts of the network were destroyed.
Baran’s concept of packet switching was crucial for the Internet, as it laid the groundwork for TCP/IP, the transmission control protocol/Internet protocol that would become the standard for data transmission across global networks.
Though his ideas were initially met with skepticism, they eventually gained traction among computer scientists and engineers looking to create a robust and flexible communication network.
Lawrence Roberts
Lawrence Roberts was another key figure who invented the Internet, taking the theoretical work of others, like Paul Baran, and turning it into a reality. As the chief scientist of the Advanced Research Projects Agency (ARPA), Roberts was responsible for the development of ARPANET, the precursor to the modern Internet. Roberts was introduced to Baran’s packet-switching concept and was immediately convinced of its viability and potential to create a computer network that could connect research institutions across the country.
In 1967, Roberts led the team that designed ARPANET’s architecture , applying packet-switching technology to create a network that could efficiently share data between computers at different locations. This network laid the foundational structure for the Internet, demonstrating the feasibility of wide-area networking. ARPANET went live in 1969, connecting four university computer science departments and marking the birth of networked computing. Roberts’ leadership and vision were critical in overcoming the technical challenges of the time , proving that a global network of computers was not only possible but also practical.
Leonard Kleinrock
Leonard Kleinrock is renowned for his foundational work in the field of computer networking, particularly for developing the mathematical theory of packet switching, which is a core principle of Internet technology. Working at the University of California Los Angeles (UCLA), Kleinrock’s research laid the groundwork for data communication over networks. His doctoral thesis, titled “ Information Flow in Large Communication Nets ,” proposed the use of packet switching for network communication, a concept that would later become crucial to the operation of the Internet.
Kleinrock’s contributions were instrumental when UCLA became the first node on ARPANET, the precursor to the modern Internet. His lab sent the first message over the network to Stanford Research Institute, marking a crucial moment in the history of the Internet. This event demonstrated the practicality of packet switching for computer communication, validating Kleinrock’s theoretical work.
His insights into data transmission and network efficiency have influenced the development of Internet protocols and the expansion of global Internet infrastructure, making him a key figure among the pioneering scientists who invented the Internet.
Donald Davies
Donald Davies, a British computer scientist, played a critical role in the invention and development of the Internet through his independent conception of packet switching. Working at the National Physical Laboratory in the UK, Davies coined the term packet switching and developed a concept similar to Paul Baran’s, albeit arrived at independently and almost simultaneously. Davies envisioned a network where data could be divided into small packets that could be routed independently across a network, optimizing efficiency and reducing congestion.
His work led to the development of the UK’s National Physical Laboratory Network (NPL Network), which was one of the first networks to implement packet switching and served as a proof of concept for packet-switched networks. Although the NPL Network was not directly connected to ARPANET, Davies’ ideas and the success of his network provided significant validation of packet switching as a viable method for computer networks, influencing the design and implementation of ARPANET and, subsequently, the TCP/IP protocols that underpin the Internet.
Davies’ contributions to computer networking and his pioneering work in packet switching are fundamental to the global network that the Internet has become today.
Bob Kahn and Vint Cerf
Bob Kahn and Vint Cerf are often referred to as the “fathers of the Internet” for their monumental contributions to its development, particularly for inventing the Transmission Control Protocol/Internet Protocol (TCP/IP), which became the foundational technology allowing different computers to communicate over a network.
In the early 1970s, Kahn, while working at the Advanced Research Projects Agency (ARPA), envisioned a network that could connect multiple networks (or “net of networks”) to allow for seamless data communication across them.
To realize this vision, he collaborated with Cerf, then a professor at Stanford University, to develop a set of protocols that could manage the data transmission over this interconnected network.
Their work on TCP/IP addressed how data could be packetized, addressed, transmitted, routed, and received across a network of networks. This protocol suite made it possible for computers to send and receive data regardless of the underlying network infrastructure, leading to the Internet becoming a global communication network.
Kahn and Cerf’s contribution laid the groundwork for the Internet’s scalability and universal adoption, making it possible for the Internet to grow beyond its initial academic and military use to become the essential global system of interconnected computer networks that we rely on today.
Paul Mockapetris and Jon Postel
Paul Mockapetris and Jon Postel played crucial roles in the invention and development of the Internet by introducing the Domain Name System (DNS), which is fundamental to how the Internet operates today. In the early 1980s, as the Internet began to expand, the need for a more scalable and user-friendly method of addressing computers on the network became apparent. The existing system of manually maintaining a host file, which mapped computer names to their numerical IP addresses, was becoming untenable due to the rapid growth of the network.
Mockapetris, with guidance from Postel, developed the DNS in 1983, which introduced a hierarchical domain name system to replace the host file. This system allowed users to access computers on the Internet using easy-to-remember domain names (like www.example.com) instead of numerical IP addresses. Postel, who was heavily involved in the development of the Internet and served as the editor of the Request for Comments (RFC) document series, played a key role in overseeing the implementation of DNS and was instrumental in the governance of Internet standards.
The DNS revolutionized the way computers were accessed and made the Internet much more user-friendly, contributing significantly to its widespread adoption and growth.
The work of Mockapetris and Postel on the DNS is a cornerstone of Internet infrastructure, enabling the seamless and intuitive access to networks and resources that most people take for granted today.
Tim Berners-Lee
Tim Berners-Lee, a British computer scientist, made an indelible mark on human history by inventing the World Wide Web (WWW) , a system that revolutionized the internet and how most people access information. His invention, while working at CERN in the late 1980s, was initially conceived to meet the demand for automated information-sharing between scientists in universities and institutes around the world. Berners-Lee’s world’s first web server and browser, which he also created, utilized the Internet as the underlying network to allow computers to access data and web pages stored on other networks.
The World Wide Web provided a user-friendly layer on top of the Internet, employing hypertext markup language (HTML) for creating web pages, the Uniform Resource Locator (URL) for addressing them, and the Hypertext Transfer Protocol (HTTP) for communicating between web browsers and servers.
Tim Berners-Lee’s invention was an important moment in the Internet’s history, making it accessible and useful to billions of people by enabling easy navigation and access to information. This development led to an exponential increase in Internet usage and was instrumental in shaping the modern Internet.
Marc Andreessen
Marc Andreessen played a significant role in the evolution of the Internet through the development of the Mosaic web browser . At the same time, he was a student at the University of Illinois Urbana-Champaign. Mosaic was one of the first web browsers to support images and a graphical user interface, making the World Wide Web significantly more accessible and user-friendly to the general public.
This innovation was a key factor in the Internet’s rapid expansion into public and commercial domains beyond its academic and military origins.
Andreessen’s work on Mosaic laid the foundation for the Netscape Navigator, a browser that further accelerated the web’s growth and helped establish the Internet as a central medium for communication, business, and entertainment. The development of these browsers was critical in transitioning the Internet from a tool primarily used by computer scientists and researchers to a global network that is integral to modern life.
Andreessen’s contributions were crucial in democratizing Internet access, allowing people to explore the vast web of information with ease, thus playing a significant part in the digital revolution that has defined the contemporary era.
When Was the Internet Invented?
The Internet was invented in the late 1960s, with the first practical schematics for the Internet starting to come together in the early 1960s.
A rough timeline:
- 1960s: The concept of a global network of computers was proposed.
- 1969: The ARPANET, the first computer network to implement packet switching, was launched.
- 1974: The Transmission Control Protocol/Internet Protocol (TCP/IP), was introduced.
- 1983: ARPANET adopted TCP/IP, marking the birth of the Internet.
- 1990: Tim Berners-Lee invented the World Wide Web.
Hence, the Internet’s roots are in the 1960s when computer scientists began exploring the potential of linking computers together to share data and resources. This period was crucial for laying the groundwork for communication networks that could span the globe.
In 1969, the United States Department of Defense’s Advanced Research Projects Agency (ARPA) launched ARPANET, the first network to successfully use packet switching to allow multiple computers to communicate on a single network. This was a significant breakthrough in communications technology, demonstrating the feasibility of a new way to transmit data across long distances. ARPANET’s success paved the way for further innovations in networking technology.
The introduction of TCP/IP in 1974 by Vint Cerf and Bob Kahn came next. This protocol suite became the standard framework for data transmission across networks, enabling the interconnection of networks into an international network. TCP/IP’s adoption by ARPANET in 1983 essentially marked the birth of the Internet, establishing a global network that could support communication across diverse operating systems and network architectures.
Tim Berners-Lee’s invention of the World Wide Web in 1990 significantly expanded the Internet’s usability and appeal. The Web made the Internet accessible to ordinary people, not just computer scientists and researchers. By creating a system for publishing and accessing hyperlinked documents (web pages), Berners-Lee transformed the Internet into a powerful medium for sharing and accessing the world’s information.
What Was the First Message Sent Over the Internet?
The first message sent over the Internet was “LO-,” which was initially intended to be the word “login.” Leonard Kleinrock, a professor at UCLA, and his team were tasked with sending this first message .
They started by typing “L” and “O” to log into the SRI computer. However, the system crashed after the first two letters were successfully sent, making “LO” the actual first message transmitted over the ARPANET, the precursor to the modern Internet.
This historic event occurred on October 29, 1969, when ARPANET computers at the University of California, Los Angeles (UCLA), attempted to send a message to the Stanford Research Institute (SRI).
Despite the initial hiccup, this event was a significant success. It demonstrated the feasibility of high-speed, distance-independent communication between two computers via a network. This first message was a practical test of the ARPANET, proving that packet switching was a viable method for data transmission across multiple nodes in a network.
How Was the Internet Created?
The Internet was created through the innovative integration of multiple technologies, including packet switching, TCP/IP, and the World Wide Web.
To make the exact technologies clearer, these were the ones that were mostly leveraged, and laid out in detail.
Packet switching, the technology enabling the Internet, was developed as a method to transmit data across a network efficiently . Unlike traditional circuit-switching systems used for telephone communications, which establish a single, dedicated path for the duration of a call, packet switching breaks down data into small blocks, or packets, that are sent independently over various paths and reassembled at the destination.
READ MORE: The Complete History of Phones from the Last 500 Years
This method significantly improves the efficiency and robustness of data transmission, allowing for the dynamic routing of information around damaged or busy nodes. The development of packet switching was crucial for ARPANET, the first network to implement this technology, setting the stage for the Internet.
The Transmission Control Protocol/Internet Protocol (TCP/IP) in the 1970s by Vint Cerf and Bob Kahn provided a standard method for computers to communicate over the Internet, regardless of their underlying hardware or operating systems. TCP ensures reliable data transmission across the network, while IP handles data packet routing. The adoption of TCP/IP by ARPANET in 1983 marked the beginning of the modern Internet, facilitating the interconnection of disparate networks into a single, global network.
Creating the Internet today, with current technology, would leverage advanced communications technology, including fiber optics, 5G wireless systems , and cloud computing.
The Internet’s infrastructure would likely be built on even more efficient packet-switching protocols and high-speed data transmission technologies, allowing for greater data capacity and lower latency. Additionally, security and privacy technologies would be integral from the outset, addressing contemporary challenges in cybersecurity.
The evolution of Internet technology continues, with innovations such as quantum computing and blockchain offering the potential for future enhancements to network efficiency, security, and decentralization.
Why Did Tim Berners-Lee Make the Internet Free?
Tim Berners-Lee made the World Wide Web freely available to ensure it could be universally accessed and used to foster innovation, collaboration, and information sharing across the globe. Berners-Lee prioritized the Web’s potential as a universal medium over personal or institutional gain by not patenting his invention and instead placing it in the public domain. This decision had profound effects on the development and evolution of the Internet.
The decision to make the World Wide Web free opened up countless opportunities for innovation and growth in the digital landscape. It allowed developers and entrepreneurs around the world to create web services and platforms without the barriers of licensing fees or proprietary restrictions.
This led to an explosion of content and applications , ranging from web browsers to e-commerce sites, social media platforms, and much more. The Web became a canvas for creativity and a foundation for building the modern digital economy.
Making the Internet freely available has been crucial in democratizing access to information, a milestone in human history. It has enabled most people to obtain knowledge, learn new skills, and connect with others worldwide. Educational resources, scientific research, and cultural content have become accessible to a broader audience, contributing to global literacy and learning.
This open access has been especially significant for developed countries, where the Internet can be a great equalizer, offering opportunities for economic and social advancement.
When Did the Internet Become Popular?
The Internet became popular in the early 1990s. This period marked a significant turning point in its adoption and use, driven largely by the advent of the World Wide Web and web browsers that made navigating the Internet more user-friendly.
The invention of the World Wide Web, coupled with the launch of the first web browser, Mosaic, in 1993, made the Internet far more accessible to the general public. By the mid-1990s, the Internet was growing at an unprecedented rate as businesses, educational institutions, and individuals began to recognize its potential for communication, commerce, and information sharing.
The late 1990s and early 2000s saw the Internet boom, often referred to as the dot-com bubble. This era was characterized by a rapid increase in the number of people accessing the Internet and the establishment of many online businesses. Although the bubble eventually burst, leading to the collapse of numerous dot-com companies, it did not slow down the Internet’s growth. Instead, it paved the way for the emergence of major tech companies that dominate the digital landscape today.
Throughout the 2000s, the Internet continued to evolve with advancements in technology, including the rise of broadband connections, which replaced slower dial-up connections, making the Internet faster and more accessible. Social media platforms, video-sharing sites, and online shopping became mainstream, further integrating the Internet into daily life. The introduction of smartphones and mobile Internet access revolutionized how people used the Web, making it possible to stay connected anywhere and anytime.
READ MORE: Who Invented Smartphone? Unraveling the History of Mobile Technology
Today, the Internet is an integral part of modern society, influencing almost every aspect of our lives. It has become the primary source of information, a global platform for communication, and a critical space for commerce. As of now, the Internet hosts billions of web pages and is supported by millions of servers worldwide.
The Internet continues to grow, with current estimates suggesting that several billion devices are connected to it.
Beranek, L. (2000). Roots of the Internet: A Personal History. Massachusetts Historical Review, 2, 55–75. http://www.jstor.org/stable/25081152
Denning, P. J. (1989). The Science of Computing: The ARPANET after Twenty Years. American Scientist, 77(6), 530–534. http://www.jstor.org/stable/27856002
Rosenzweig, R. (1998). Wizards, Bureaucrats, Warriors, and Hackers: Writing the History of the Internet. The American Historical Review, 103(5), 1530–1552. https://doi.org/10.2307/2649970
L. Kleinrock, “Information Flow in Large Communication Nets,” Ph.D. Thesis, Massachu-Setts Institute of Technology, Cambridge, 1961. http://www.lk.cs.ucla.edu/LK/Bib/REPORT/PhD/
DENARDIS, L. (2014). Controlling Internet Resources. In The Global War for Internet Governance (pp. 33–62). Yale University Press. https://doi.org/10.2307/j.ctt5vkz4n.4
Kernighan, B. W. (2017). The World Wide Web. In Understanding the Digital World: What You Need to Know about Computers, the Internet, Privacy, and Security (pp. 163–182). Princeton University Press. https://doi.org/10.2307/j.ctvc775pg.19
Canales, J. (2017). Mosaic: The First Point-and-Click Internet Browser. In F. E. Hoxie (Ed.), The University of Illinois: Engine of Innovation (pp. 152–158). University of Illinois Press. http://www.jstor.org/stable/10.5406/j.ctt1m3217b.36
Cole, R. (1982). An introduction to packet switched computer networks. Science Progress (1933- ), 68(269), 127–142. http://www.jstor.org/stable/43420557
Shah, R. (2020). What is 5G? In Ensuring a trusted 5G ecosystem of vendors and technology (pp. 04–06). Australian Strategic Policy Institute. http://www.jstor.org/stable/resrep26116.6
Tan, M., & Teo, T. S. H. (1998). Factors Influencing the Adoption of the Internet. International Journal of Electronic Commerce, 2(3), 5–18. http://www.jstor.org/stable/27750854
DeNardis, L., & GLOBAL COMMISSION ON INTERNET GOVERNANCE. (2017). INTRODUCTION: THE SHIFTING GEOPOLITICS OF INTERNET ACCESS. In The Shifting Geopolitics of Internet Access: From Broadband and Net Neutrality to Zero-rating (pp. 1–4). Centre for International Governance Innovation. http://www.jstor.org/stable/resrep05240.5
How to Cite this Article
There are three different ways you can cite this article.
1. To cite this article in an academic-style article or paper , use:
<a href=" https://historycooperative.org/who-invented-the-internet/ ">Who Invented the Internet? The Origin and History of the Internet</a>
Leave a Comment Cancel reply
- History Classics
- Your Profile
- Find History on Facebook (Opens in a new window)
- Find History on Twitter (Opens in a new window)
- Find History on YouTube (Opens in a new window)
- Find History on Instagram (Opens in a new window)
- Find History on TikTok (Opens in a new window)
- This Day In History
- History Podcasts
- History Vault
The Invention of the Internet
By: History.com Editors
Published: June 11, 2024

Unlike technologies such as the phonograph or the safety pin, the internet has no single “inventor.” Instead, it has evolved over time. The internet got its start in the United States in the late 1960s as a military defense system in the Cold War. For years, scientists and researchers used it to communicate and share data with one another. Today, we use the internet for almost everything, and for many people it would be impossible to imagine life without it.
The Sputnik Scare
On October 4, 1957, the Soviet Union launched the world’s first artificial satellite into orbit. The satellite, known as Sputnik, did not do much: It relayed blips and bleeps from its radio transmitters as it circled the Earth. Still, to many Americans, the beach ball-sized Sputnik was proof of something alarming: While the U.S. economy was booming and its consumer technologies were advancing, the Soviets had been focusing on training scientists—and were positioned to win the Space Race , and possibly the Cold War , because of it.
Did you know? Nearly two-thirds of the world’s 8 billion people used the internet in 2023.
After Sputnik’s launch, many Americans began to think more seriously about science and technology. Schools added courses on subjects like chemistry, physics and calculus. Universities and corporations took government grants and invested them in scientific research and development. And the federal government itself formed new agencies, such as the National Aeronautics and Space Administration (NASA) and the Department of Defense’s Advanced Research Projects Agency (ARPA), to develop space-age technologies such as rockets, weapons and computers.
The Birth of the ARPAnet
Scientists and military experts were especially concerned about what might happen in the event of a Soviet attack on the nation’s telephone system. Just one missile, they feared, could destroy the whole network of lines and wires that made efficient long-distance communication possible.
In 1962, a scientist from ARPA named J.C.R. Licklider proposed a solution to this problem: a “ intergalactic network ” of computers that could talk to one another. Such a network would enable government leaders to communicate even if the Soviets destroyed the telephone system.
In 1965, Donald Davies, a scientist at Britain’s National Physical Laboratory developed a way of sending information from one computer to another that he called “packet switching.” Packet switching breaks data down into blocks, or packets, before sending it to its destination. That way, each packet can take its own route from place to place. Without packet switching, the government’s computer network—now known as the Arpanet—would have been just as vulnerable to enemy attacks as the phone system.
On October 29, 1969, Arpanet delivered its first message: a “node-to-node” communication from one computer to another. (The first computer was located in a research lab at UCLA and the second was at Stanford; each one was the size of a large room .) The message—“LOGIN”—was short and simple, but it crashed the fledgling Arpanet anyway: The Stanford computer only received the note’s first two letters.
The Network Grows
By the end of 1969, just four computers were connected to the Arpanet, but the network grew steadily during the 1970s.
In 1972, it added the University of Hawaii’s ALOHAnet, and a year later it added networks at London’s University College and the Norwegian Seismic Array. As packet-switched computer networks multiplied, however, it became more difficult for them to integrate into a single worldwide “internet.”
By the mid-1970s, a computer scientist named Vinton Cerf had begun to solve this problem by developing a way for all of the computers on all of the world’s mini-networks to communicate with one another. He called his invention “Transmission Control Protocol,” or TCP. (Later, he added an additional protocol, known as “Internet Protocol.” The acronym we use to refer to these today is TCP/IP.) One writer describes Cerf’s protocol as “the ‘handshake’ that introduces distant and different computers to each other in a virtual space.”
The World Wide Web
Cerf’s protocol transformed the internet into a worldwide network. Throughout the 1980s, researchers and scientists used it to send files and data from one computer to another. However, in 1991 the internet changed again. That year, a computer programmer working at the CERN research center on the Swiss-French border named Tim Berners-Lee introduced the World Wide Web: an internet that was not simply a way to send files from one place to another but was itself a “web” of linked information that anyone on the Internet could retrieve. Berners-Lee created the Internet that we know today.
In 1992, a group of students and researchers at the University of Illinois developed a sophisticated browser that they called Mosaic. (It later became Netscape.) Mosaic offered a user-friendly way to search the Web: It allowed users to see words and pictures on the same page for the first time and to navigate using scrollbars and clickable links.
That same year, Congress authorized the National Science Foundation to connect the country’s research- and education-focused internet services to commercial networks. As a result, companies of all kinds hurried to set up websites of their own, and e-commerce entrepreneurs began to use the internet to sell goods directly to customers. By the 2000s, companies including Amazon and eBay emerged as dominant players in the online retail space.
In the first decade of the 2000s, social media platforms such as Facebook, Twitter and Instagram emerged, changing the way people connected, created and shared content. By around 2015, more people accessed the internet from smartphones than from other kinds of computers. By the early 2020s, companies, including OpenAI, Google, Microsoft and others starting rolling out advanced artificial intelligence systems to the public.

HISTORY Vault: 101 Inventions That Changed the World
Take a closer look at the inventions that have transformed our lives far beyond our homes (the steam engine), our planet (the telescope) and our wildest dreams (the internet).

Sign up for Inside History
Get HISTORY’s most fascinating stories delivered to your inbox three times a week.
By submitting your information, you agree to receive emails from HISTORY and A+E Networks. You can opt out at any time. You must be 16 years or older and a resident of the United States.
More details : Privacy Notice | Terms of Use | Contact Us

A Brief History of the Internet
Introduction, published 1997.
Barry M. Leiner, Vinton G. Cerf, David D. Clark, Robert E. Kahn, Leonard Kleinrock, Daniel C. Lynch, Jon Postel, Larry G. Roberts, Stephen Wolff
The Internet has revolutionized the computer and communications world like nothing before. The invention of the telegraph, telephone, radio, and computer set the stage for this unprecedented integration of capabilities. The Internet is at once a world-wide broadcasting capability, a mechanism for information dissemination, and a medium for collaboration and interaction between individuals and their computers without regard for geographic location. The Internet represents one of the most successful examples of the benefits of sustained investment and commitment to research and development of information infrastructure. Beginning with the early research in packet switching, the government, industry and academia have been partners in evolving and deploying this exciting new technology. Today, terms like “ [email protected] ” and “ http://www.acm.org ” trip lightly off the tongue of the random person on the street. 1
This is intended to be a brief, necessarily cursory and incomplete history. Much material currently exists about the Internet, covering history, technology, and usage. A trip to almost any bookstore will find shelves of material written about the Internet. 2
Learn more about how we are building a bigger, stronger Internet.
In this paper, 3 several of us involved in the development and evolution of the Internet share our views of its origins and history. This history revolves around four distinct aspects. There is the technological evolution that began with early research on packet switching and the ARPANET (and related technologies), and where current research continues to expand the horizons of the infrastructure along several dimensions, such as scale, performance, and higher-level functionality. There is the operations and management aspect of a global and complex operational infrastructure. There is the social aspect, which resulted in a broad community of Internauts working together to create and evolve the technology. And there is the commercialization aspect, resulting in an extremely effective transition of research results into a broadly deployed and available information infrastructure.
The Internet today is a widespread information infrastructure, the initial prototype of what is often called the National (or Global or Galactic) Information Infrastructure. Its history is complex and involves many aspects – technological, organizational, and community. And its influence reaches not only to the technical fields of computer communications but throughout society as we move toward increasing use of online tools to accomplish electronic commerce, information acquisition, and community operations.
Origins of the Internet
The first recorded description of the social interactions that could be enabled through networking was a series of memos written by J.C.R. Licklider of MIT in August 1962 discussing his “Galactic Network” concept. He envisioned a globally interconnected set of computers through which everyone could quickly access data and programs from any site. In spirit, the concept was very much like the Internet of today. Licklider was the first head of the computer research program at DARPA, 4 starting in October 1962. While at DARPA he convinced his successors at DARPA, Ivan Sutherland, Bob Taylor, and MIT researcher Lawrence G. Roberts, of the importance of this networking concept.
Leonard Kleinrock at MIT published the first paper on packet switching theory in July 1961 and the first book on the subject in 1964. Kleinrock convinced Roberts of the theoretical feasibility of communications using packets rather than circuits, which was a major step along the path towards computer networking. The other key step was to make the computers talk together. To explore this, in 1965 working with Thomas Merrill, Roberts connected the TX-2 computer in Mass. to the Q-32 in California with a low speed dial-up telephone line creating the first (however small) wide-area computer network ever built . The result of this experiment was the realization that the time-shared computers could work well together, running programs and retrieving data as necessary on the remote machine, but that the circuit switched telephone system was totally inadequate for the job. Kleinrock’s conviction of the need for packet switching was confirmed.
In late 1966 Roberts went to DARPA to develop the computer network concept and quickly put together his plan for the “ARPANET” , publishing it in 1967. At the conference where he presented the paper, there was also a paper on a packet network concept from the UK by Donald Davies and Roger Scantlebury of NPL. Scantlebury told Roberts about the NPL work as well as that of Paul Baran and others at RAND. The RAND group had written a paper on packet switching networks for secure voice in the military in 1964. It happened that the work at MIT (1961-1967), at RAND (1962-1965), and at NPL (1964-1967) had all proceeded in parallel without any of the researchers knowing about the other work. The word “packet” was adopted from the work at NPL and the proposed line speed to be used in the ARPANET design was upgraded from 2.4 kbps to 50 kbps. 5
In August 1968, after Roberts and the DARPA funded community had refined the overall structure and specifications for the ARPANET, an RFQ was released by DARPA for the development of one of the key components, the packet switches called Interface Message Processors (IMP’s). The RFQ was won in December 1968 by a group headed by Frank Heart at Bolt Beranek and Newman (BBN). As the BBN team worked on the IMP’s with Bob Kahn playing a major role in the overall ARPANET architectural design, the network topology and economics were designed and optimized by Roberts working with Howard Frank and his team at Network Analysis Corporation, and the network measurement system was prepared by Kleinrock’s team at UCLA. 6
Due to Kleinrock’s early development of packet switching theory and his focus on analysis, design and measurement, his Network Measurement Center at UCLA was selected to be the first node on the ARPANET. All this came together in September 1969 when BBN installed the first IMP at UCLA and the first host computer was connected. Doug Engelbart’s project on “Augmentation of Human Intellect” (which included NLS, an early hypertext system) at Stanford Research Institute (SRI) provided a second node. SRI supported the Network Information Center, led by Elizabeth (Jake) Feinler and including functions such as maintaining tables of host name to address mapping as well as a directory of the RFC’s.
One month later, when SRI was connected to the ARPANET, the first host-to-host message was sent from Kleinrock’s laboratory to SRI. Two more nodes were added at UC Santa Barbara and University of Utah. These last two nodes incorporated application visualization projects, with Glen Culler and Burton Fried at UCSB investigating methods for display of mathematical functions using storage displays to deal with the problem of refresh over the net, and Robert Taylor and Ivan Sutherland at Utah investigating methods of 3-D representations over the net. Thus, by the end of 1969, four host computers were connected together into the initial ARPANET, and the budding Internet was off the ground. Even at this early stage, it should be noted that the networking research incorporated both work on the underlying network and work on how to utilize the network. This tradition continues to this day.
Computers were added quickly to the ARPANET during the following years, and work proceeded on completing a functionally complete Host-to-Host protocol and other network software. In December 1970 the Network Working Group (NWG) working under S. Crocker finished the initial ARPANET Host-to-Host protocol, called the Network Control Protocol (NCP). As the ARPANET sites completed implementing NCP during the period 1971-1972, the network users finally could begin to develop applications.
In October 1972, Kahn organized a large, very successful demonstration of the ARPANET at the International Computer Communication Conference (ICCC). This was the first public demonstration of this new network technology to the public. It was also in 1972 that the initial “hot” application, electronic mail, was introduced. In March Ray Tomlinson at BBN wrote the basic email message send and read software, motivated by the need of the ARPANET developers for an easy coordination mechanism. In July, Roberts expanded its utility by writing the first email utility program to list, selectively read, file, forward, and respond to messages. From there email took off as the largest network application for over a decade. This was a harbinger of the kind of activity we see on the World Wide Web today, namely, the enormous growth of all kinds of “people-to-people” traffic.
The Initial Internetting Concepts
The original ARPANET grew into the Internet. Internet was based on the idea that there would be multiple independent networks of rather arbitrary design, beginning with the ARPANET as the pioneering packet switching network, but soon to include packet satellite networks, ground-based packet radio networks and other networks. The Internet as we now know it embodies a key underlying technical idea, namely that of open architecture networking. In this approach, the choice of any individual network technology was not dictated by a particular network architecture but rather could be selected freely by a provider and made to interwork with the other networks through a meta-level “Internetworking Architecture”. Up until that time there was only one general method for federating networks. This was the traditional circuit switching method where networks would interconnect at the circuit level, passing individual bits on a synchronous basis along a portion of an end-to-end circuit between a pair of end locations. Recall that Kleinrock had shown in 1961 that packet switching was a more efficient switching method. Along with packet switching, special purpose interconnection arrangements between networks were another possibility. While there were other limited ways to interconnect different networks, they required that one be used as a component of the other, rather than acting as a peer of the other in offering end-to-end service.
In an open-architecture network, the individual networks may be separately designed and developed and each may have its own unique interface which it may offer to users and/or other providers. including other Internet providers. Each network can be designed in accordance with the specific environment and user requirements of that network. There are generally no constraints on the types of network that can be included or on their geographic scope, although certain pragmatic considerations will dictate what makes sense to offer.
The idea of open-architecture networking was first introduced by Kahn shortly after having arrived at DARPA in 1972. This work was originally part of the packet radio program, but subsequently became a separate program in its own right. At the time, the program was called “Internetting”. Key to making the packet radio system work was a reliable end-end protocol that could maintain effective communication in the face of jamming and other radio interference, or withstand intermittent blackout such as caused by being in a tunnel or blocked by the local terrain. Kahn first contemplated developing a protocol local only to the packet radio network, since that would avoid having to deal with the multitude of different operating systems, and continuing to use NCP.
However, NCP did not have the ability to address networks (and machines) further downstream than a destination IMP on the ARPANET and thus some change to NCP would also be required. (The assumption was that the ARPANET was not changeable in this regard). NCP relied on ARPANET to provide end-to-end reliability. If any packets were lost, the protocol (and presumably any applications it supported) would come to a grinding halt. In this model NCP had no end-end host error control, since the ARPANET was to be the only network in existence and it would be so reliable that no error control would be required on the part of the hosts. Thus, Kahn decided to develop a new version of the protocol which could meet the needs of an open-architecture network environment. This protocol would eventually be called the Transmission Control Protocol/Internet Protocol (TCP/IP). While NCP tended to act like a device driver, the new protocol would be more like a communications protocol.
Four ground rules were critical to Kahn’s early thinking:
- Each distinct network would have to stand on its own and no internal changes could be required to any such network to connect it to the Internet.
- Communications would be on a best effort basis. If a packet didn’t make it to the final destination, it would shortly be retransmitted from the source.
- Black boxes would be used to connect the networks; these would later be called gateways and routers. There would be no information retained by the gateways about the individual flows of packets passing through them, thereby keeping them simple and avoiding complicated adaptation and recovery from various failure modes.
- There would be no global control at the operations level.
Other key issues that needed to be addressed were:
- Algorithms to prevent lost packets from permanently disabling communications and enabling them to be successfully retransmitted from the source.
- Providing for host-to-host “pipelining” so that multiple packets could be enroute from source to destination at the discretion of the participating hosts, if the intermediate networks allowed it.
- Gateway functions to allow it to forward packets appropriately. This included interpreting IP headers for routing, handling interfaces, breaking packets into smaller pieces if necessary, etc.
- The need for end-end checksums, reassembly of packets from fragments and detection of duplicates, if any.
- The need for global addressing
- Techniques for host-to-host flow control.
- Interfacing with the various operating systems
- There were also other concerns, such as implementation efficiency, internetwork performance, but these were secondary considerations at first.
Kahn began work on a communications-oriented set of operating system principles while at BBN and documented some of his early thoughts in an internal BBN memorandum entitled “ Communications Principles for Operating Systems “. At this point he realized it would be necessary to learn the implementation details of each operating system to have a chance to embed any new protocols in an efficient way. Thus, in the spring of 1973, after starting the internetting effort, he asked Vint Cerf (then at Stanford) to work with him on the detailed design of the protocol. Cerf had been intimately involved in the original NCP design and development and already had the knowledge about interfacing to existing operating systems. So armed with Kahn’s architectural approach to the communications side and with Cerf’s NCP experience, they teamed up to spell out the details of what became TCP/IP.
The give and take was highly productive and the first written version of the resulting approach was distributed as INWG#39 at a special meeting of the International Network Working Group (INWG) at Sussex University in September 1973. Subsequently a refined version was published in 1974 7 . The INWG was created at the October 1972 International Computer Communications Conference organized by Bob Kahn, et al, and Cerf was invited to chair this group.
Some basic approaches emerged from this collaboration between Kahn and Cerf:
- Communication between two processes would logically consist of a very long stream of bytes (they called them octets). The position of any octet in the stream would be used to identify it.
- Flow control would be done by using sliding windows and acknowledgments (acks). The destination could select when to acknowledge and each ack returned would be cumulative for all packets received to that point.
- It was left open as to exactly how the source and destination would agree on the parameters of the windowing to be used. Defaults were used initially.
- Although Ethernet was under development at Xerox PARC at that time, the proliferation of LANs were not envisioned at the time, much less PCs and workstations. The original model was national level networks like ARPANET of which only a relatively small number were expected to exist. Thus a 32 bit IP address was used of which the first 8 bits signified the network and the remaining 24 bits designated the host on that network. This assumption, that 256 networks would be sufficient for the foreseeable future, was clearly in need of reconsideration when LANs began to appear in the late 1970s.
The original Cerf/Kahn paper on the Internet described one protocol, called TCP, which provided all the transport and forwarding services in the Internet. Kahn had intended that the TCP protocol support a range of transport services, from the totally reliable sequenced delivery of data (virtual circuit model) to a datagram service in which the application made direct use of the underlying network service, which might imply occasional lost, corrupted or reordered packets. However, the initial effort to implement TCP resulted in a version that only allowed for virtual circuits. This model worked fine for file transfer and remote login applications, but some of the early work on advanced network applications, in particular packet voice in the 1970s, made clear that in some cases packet losses should not be corrected by TCP, but should be left to the application to deal with. This led to a reorganization of the original TCP into two protocols, the simple IP which provided only for addressing and forwarding of individual packets, and the separate TCP, which was concerned with service features such as flow control and recovery from lost packets. For those applications that did not want the services of TCP, an alternative called the User Datagram Protocol (UDP) was added in order to provide direct access to the basic service of IP.
A major initial motivation for both the ARPANET and the Internet was resource sharing – for example allowing users on the packet radio networks to access the time sharing systems attached to the ARPANET. Connecting the two together was far more economical that duplicating these very expensive computers. However, while file transfer and remote login (Telnet) were very important applications, electronic mail has probably had the most significant impact of the innovations from that era. Email provided a new model of how people could communicate with each other, and changed the nature of collaboration, first in the building of the Internet itself (as is discussed below) and later for much of society.
There were other applications proposed in the early days of the Internet, including packet based voice communication (the precursor of Internet telephony), various models of file and disk sharing, and early “worm” programs that showed the concept of agents (and, of course, viruses). A key concept of the Internet is that it was not designed for just one application, but as a general infrastructure on which new applications could be conceived, as illustrated later by the emergence of the World Wide Web. It is the general purpose nature of the service provided by TCP and IP that makes this possible.
Proving the Ideas
DARPA let three contracts to Stanford (Cerf), BBN (Ray Tomlinson) and UCL (Peter Kirstein) to implement TCP/IP (it was simply called TCP in the Cerf/Kahn paper but contained both components). The Stanford team, led by Cerf, produced the detailed specification and within about a year there were three independent implementations of TCP that could interoperate.
This was the beginning of long term experimentation and development to evolve and mature the Internet concepts and technology. Beginning with the first three networks (ARPANET, Packet Radio, and Packet Satellite) and their initial research communities, the experimental environment has grown to incorporate essentially every form of network and a very broad-based research and development community. [REK78] With each expansion has come new challenges.
The early implementations of TCP were done for large time sharing systems such as Tenex and TOPS 20. When desktop computers first appeared, it was thought by some that TCP was too big and complex to run on a personal computer. David Clark and his research group at MIT set out to show that a compact and simple implementation of TCP was possible. They produced an implementation, first for the Xerox Alto (the early personal workstation developed at Xerox PARC) and then for the IBM PC. That implementation was fully interoperable with other TCPs, but was tailored to the application suite and performance objectives of the personal computer, and showed that workstations, as well as large time-sharing systems, could be a part of the Internet. In 1976, Kleinrock published the first book on the ARPANET . It included an emphasis on the complexity of protocols and the pitfalls they often introduce. This book was influential in spreading the lore of packet switching networks to a very wide community.
Widespread development of LANS, PCs and workstations in the 1980s allowed the nascent Internet to flourish. Ethernet technology, developed by Bob Metcalfe at Xerox PARC in 1973, is now probably the dominant network technology in the Internet and PCs and workstations the dominant computers. This change from having a few networks with a modest number of time-shared hosts (the original ARPANET model) to having many networks has resulted in a number of new concepts and changes to the underlying technology. First, it resulted in the definition of three network classes (A, B, and C) to accommodate the range of networks. Class A represented large national scale networks (small number of networks with large numbers of hosts); Class B represented regional scale networks; and Class C represented local area networks (large number of networks with relatively few hosts).
A major shift occurred as a result of the increase in scale of the Internet and its associated management issues. To make it easy for people to use the network, hosts were assigned names, so that it was not necessary to remember the numeric addresses. Originally, there were a fairly limited number of hosts, so it was feasible to maintain a single table of all the hosts and their associated names and addresses. The shift to having a large number of independently managed networks (e.g., LANs) meant that having a single table of hosts was no longer feasible, and the Domain Name System (DNS) was invented by Paul Mockapetris of USC/ISI. The DNS permitted a scalable distributed mechanism for resolving hierarchical host names (e.g. www.acm.org ) into an Internet address.
The increase in the size of the Internet also challenged the capabilities of the routers. Originally, there was a single distributed algorithm for routing that was implemented uniformly by all the routers in the Internet. As the number of networks in the Internet exploded, this initial design could not expand as necessary, so it was replaced by a hierarchical model of routing, with an Interior Gateway Protocol (IGP) used inside each region of the Internet, and an Exterior Gateway Protocol (EGP) used to tie the regions together. This design permitted different regions to use a different IGP, so that different requirements for cost, rapid reconfiguration, robustness and scale could be accommodated. Not only the routing algorithm, but the size of the addressing tables, stressed the capacity of the routers. New approaches for address aggregation, in particular classless inter-domain routing (CIDR), have recently been introduced to control the size of router tables.
As the Internet evolved, one of the major challenges was how to propagate the changes to the software, particularly the host software. DARPA supported UC Berkeley to investigate modifications to the Unix operating system, including incorporating TCP/IP developed at BBN. Although Berkeley later rewrote the BBN code to more efficiently fit into the Unix system and kernel, the incorporation of TCP/IP into the Unix BSD system releases proved to be a critical element in dispersion of the protocols to the research community. Much of the CS research community began to use Unix BSD for their day-to-day computing environment. Looking back, the strategy of incorporating Internet protocols into a supported operating system for the research community was one of the key elements in the successful widespread adoption of the Internet.
One of the more interesting challenges was the transition of the ARPANET host protocol from NCP to TCP/IP as of January 1, 1983. This was a “flag-day” style transition, requiring all hosts to convert simultaneously or be left having to communicate via rather ad-hoc mechanisms. This transition was carefully planned within the community over several years before it actually took place and went surprisingly smoothly (but resulted in a distribution of buttons saying “I survived the TCP/IP transition”).
TCP/IP was adopted as a defense standard three years earlier in 1980. This enabled defense to begin sharing in the DARPA Internet technology base and led directly to the eventual partitioning of the military and non- military communities. By 1983, ARPANET was being used by a significant number of defense R&D and operational organizations. The transition of ARPANET from NCP to TCP/IP permitted it to be split into a MILNET supporting operational requirements and an ARPANET supporting research needs.
Thus, by 1985, Internet was already well established as a technology supporting a broad community of researchers and developers, and was beginning to be used by other communities for daily computer communications. Electronic mail was being used broadly across several communities, often with different systems, but interconnection between different mail systems was demonstrating the utility of broad based electronic communications between people.
Transition to Widespread Infrastructure
At the same time that the Internet technology was being experimentally validated and widely used amongst a subset of computer science researchers, other networks and networking technologies were being pursued. The usefulness of computer networking – especially electronic mail – demonstrated by DARPA and Department of Defense contractors on the ARPANET was not lost on other communities and disciplines, so that by the mid-1970s computer networks had begun to spring up wherever funding could be found for the purpose. The U.S. Department of Energy (DoE) established MFENet for its researchers in Magnetic Fusion Energy, whereupon DoE’s High Energy Physicists responded by building HEPNet. NASA Space Physicists followed with SPAN, and Rick Adrion, David Farber, and Larry Landweber established CSNET for the (academic and industrial) Computer Science community with an initial grant from the U.S. National Science Foundation (NSF). AT&T’s free-wheeling dissemination of the UNIX computer operating system spawned USENET, based on UNIX’ built-in UUCP communication protocols, and in 1981 Ira Fuchs and Greydon Freeman devised BITNET, which linked academic mainframe computers in an “email as card images” paradigm.
With the exception of BITNET and USENET, these early networks (including ARPANET) were purpose-built – i.e., they were intended for, and largely restricted to, closed communities of scholars; there was hence little pressure for the individual networks to be compatible and, indeed, they largely were not. In addition, alternate technologies were being pursued in the commercial sector, including XNS from Xerox, DECNet, and IBM’s SNA. 8 It remained for the British JANET (1984) and U.S. NSFNET (1985) programs to explicitly announce their intent to serve the entire higher education community, regardless of discipline. Indeed, a condition for a U.S. university to receive NSF funding for an Internet connection was that “… the connection must be made available to ALL qualified users on campus.”
In 1985, Dennis Jennings came from Ireland to spend a year at NSF leading the NSFNET program. He worked with the community to help NSF make a critical decision – that TCP/IP would be mandatory for the NSFNET program. When Steve Wolff took over the NSFNET program in 1986, he recognized the need for a wide area networking infrastructure to support the general academic and research community, along with the need to develop a strategy for establishing such infrastructure on a basis ultimately independent of direct federal funding. Policies and strategies were adopted (see below) to achieve that end.
NSF also elected to support DARPA’s existing Internet organizational infrastructure, hierarchically arranged under the (then) Internet Activities Board (IAB). The public declaration of this choice was the joint authorship by the IAB’s Internet Engineering and Architecture Task Forces and by NSF’s Network Technical Advisory Group of RFC 985 (Requirements for Internet Gateways ), which formally ensured interoperability of DARPA’s and NSF’s pieces of the Internet.
In addition to the selection of TCP/IP for the NSFNET program, Federal agencies made and implemented several other policy decisions which shaped the Internet of today.
- Federal agencies shared the cost of common infrastructure, such as trans-oceanic circuits. They also jointly supported “managed interconnection points” for interagency traffic; the Federal Internet Exchanges (FIX-E and FIX-W) built for this purpose served as models for the Network Access Points and “*IX” facilities that are prominent features of today’s Internet architecture.
- To coordinate this sharing, the Federal Networking Council 9 was formed. The FNC also cooperated with other international organizations, such as RARE in Europe, through the Coordinating Committee on Intercontinental Research Networking, CCIRN, to coordinate Internet support of the research community worldwide.
- This sharing and cooperation between agencies on Internet-related issues had a long history. An unprecedented 1981 agreement between Farber, acting for CSNET and the NSF, and DARPA’s Kahn, permitted CSNET traffic to share ARPANET infrastructure on a statistical and no-metered-settlements basis.
- Subsequently, in a similar mode, the NSF encouraged its regional (initially academic) networks of the NSFNET to seek commercial, non-academic customers, expand their facilities to serve them, and exploit the resulting economies of scale to lower subscription costs for all.
- On the NSFNET Backbone – the national-scale segment of the NSFNET – NSF enforced an “Acceptable Use Policy” (AUP) which prohibited Backbone usage for purposes “not in support of Research and Education.” The predictable (and intended) result of encouraging commercial network traffic at the local and regional level, while denying its access to national-scale transport, was to stimulate the emergence and/or growth of “private”, competitive, long-haul networks such as PSI, UUNET, ANS CO+RE, and (later) others. This process of privately-financed augmentation for commercial uses was thrashed out starting in 1988 in a series of NSF-initiated conferences at Harvard’s Kennedy School of Government on “The Commercialization and Privatization of the Internet” – and on the “com-priv” list on the net itself.
- In 1988, a National Research Council committee, chaired by Kleinrock and with Kahn and Clark as members, produced a report commissioned by NSF titled “Towards a National Research Network”. This report was influential on then Senator Al Gore, and ushered in high speed networks that laid the networking foundation for the future information superhighway.
- In 1994, a National Research Council report, again chaired by Kleinrock (and with Kahn and Clark as members again), Entitled “Realizing The Information Future: The Internet and Beyond” was released. This report, commissioned by NSF, was the document in which a blueprint for the evolution of the information superhighway was articulated and which has had a lasting affect on the way to think about its evolution. It anticipated the critical issues of intellectual property rights, ethics, pricing, education, architecture and regulation for the Internet.
- NSF’s privatization policy culminated in April, 1995, with the defunding of the NSFNET Backbone. The funds thereby recovered were (competitively) redistributed to regional networks to buy national-scale Internet connectivity from the now numerous, private, long-haul networks.
The backbone had made the transition from a network built from routers out of the research community (the “Fuzzball” routers from David Mills) to commercial equipment. In its 8 1/2 year lifetime, the Backbone had grown from six nodes with 56 kbps links to 21 nodes with multiple 45 Mbps links. It had seen the Internet grow to over 50,000 networks on all seven continents and outer space, with approximately 29,000 networks in the United States.
Such was the weight of the NSFNET program’s ecumenism and funding ($200 million from 1986 to 1995) – and the quality of the protocols themselves – that by 1990 when the ARPANET itself was finally decommissioned 10 , TCP/IP had supplanted or marginalized most other wide-area computer network protocols worldwide, and IP was well on its way to becoming THE bearer service for the Global Information Infrastructure.
The Role of Documentation
A key to the rapid growth of the Internet has been the free and open access to the basic documents, especially the specifications of the protocols.
The beginnings of the ARPANET and the Internet in the university research community promoted the academic tradition of open publication of ideas and results. However, the normal cycle of traditional academic publication was too formal and too slow for the dynamic exchange of ideas essential to creating networks.
In 1969 a key step was taken by S. Crocker (then at UCLA) in establishing the Request for Comments (or RFC) series of notes. These memos were intended to be an informal fast distribution way to share ideas with other network researchers. At first the RFCs were printed on paper and distributed via snail mail. As the File Transfer Protocol (FTP) came into use, the RFCs were prepared as online files and accessed via FTP. Now, of course, the RFCs are easily accessed via the World Wide Web at dozens of sites around the world. SRI, in its role as Network Information Center, maintained the online directories. Jon Postel acted as RFC Editor as well as managing the centralized administration of required protocol number assignments, roles that he continued to play until his death, October 16, 1998.
The effect of the RFCs was to create a positive feedback loop, with ideas or proposals presented in one RFC triggering another RFC with additional ideas, and so on. When some consensus (or a least a consistent set of ideas) had come together a specification document would be prepared. Such a specification would then be used as the base for implementations by the various research teams.
Over time, the RFCs have become more focused on protocol standards (the “official” specifications), though there are still informational RFCs that describe alternate approaches, or provide background information on protocols and engineering issues. The RFCs are now viewed as the “documents of record” in the Internet engineering and standards community.
The open access to the RFCs (for free, if you have any kind of a connection to the Internet) promotes the growth of the Internet because it allows the actual specifications to be used for examples in college classes and by entrepreneurs developing new systems.
Email has been a significant factor in all areas of the Internet, and that is certainly true in the development of protocol specifications, technical standards, and Internet engineering. The very early RFCs often presented a set of ideas developed by the researchers at one location to the rest of the community. After email came into use, the authorship pattern changed – RFCs were presented by joint authors with common view independent of their locations.
The use of specialized email mailing lists has been long used in the development of protocol specifications, and continues to be an important tool. The IETF now has in excess of 75 working groups, each working on a different aspect of Internet engineering. Each of these working groups has a mailing list to discuss one or more draft documents under development. When consensus is reached on a draft document it may be distributed as an RFC.
As the current rapid expansion of the Internet is fueled by the realization of its capability to promote information sharing, we should understand that the network’s first role in information sharing was sharing the information about its own design and operation through the RFC documents. This unique method for evolving new capabilities in the network will continue to be critical to future evolution of the Internet.
Formation of the Broad Community
The Internet is as much a collection of communities as a collection of technologies, and its success is largely attributable to both satisfying basic community needs as well as utilizing the community in an effective way to push the infrastructure forward. This community spirit has a long history beginning with the early ARPANET. The early ARPANET researchers worked as a close-knit community to accomplish the initial demonstrations of packet switching technology described earlier. Likewise, the Packet Satellite, Packet Radio and several other DARPA computer science research programs were multi-contractor collaborative activities that heavily used whatever available mechanisms there were to coordinate their efforts, starting with electronic mail and adding file sharing, remote access, and eventually World Wide Web capabilities. Each of these programs formed a working group, starting with the ARPANET Network Working Group. Because of the unique role that ARPANET played as an infrastructure supporting the various research programs, as the Internet started to evolve, the Network Working Group evolved into Internet Working Group.
In the late 1970s, recognizing that the growth of the Internet was accompanied by a growth in the size of the interested research community and therefore an increased need for coordination mechanisms, Vint Cerf, then manager of the Internet Program at DARPA, formed several coordination bodies – an International Cooperation Board (ICB), chaired by Peter Kirstein of UCL, to coordinate activities with some cooperating European countries centered on Packet Satellite research, an Internet Research Group which was an inclusive group providing an environment for general exchange of information, and an Internet Configuration Control Board (ICCB), chaired by Clark. The ICCB was an invitational body to assist Cerf in managing the burgeoning Internet activity.
In 1983, when Barry Leiner took over management of the Internet research program at DARPA, he and Clark recognized that the continuing growth of the Internet community demanded a restructuring of the coordination mechanisms. The ICCB was disbanded and in its place a structure of Task Forces was formed, each focused on a particular area of the technology (e.g. routers, end-to-end protocols, etc.). The Internet Activities Board (IAB) was formed from the chairs of the Task Forces.
It of course was only a coincidence that the chairs of the Task Forces were the same people as the members of the old ICCB, and Dave Clark continued to act as chair. After some changing membership on the IAB, Phill Gross became chair of a revitalized Internet Engineering Task Force (IETF), at the time merely one of the IAB Task Forces. As we saw above, by 1985 there was a tremendous growth in the more practical/engineering side of the Internet. This growth resulted in an explosion in the attendance at the IETF meetings, and Gross was compelled to create substructure to the IETF in the form of working groups.
This growth was complemented by a major expansion in the community. No longer was DARPA the only major player in the funding of the Internet. In addition to NSFNet and the various US and international government-funded activities, interest in the commercial sector was beginning to grow. Also in 1985, both Kahn and Leiner left DARPA and there was a significant decrease in Internet activity at DARPA. As a result, the IAB was left without a primary sponsor and increasingly assumed the mantle of leadership.
The growth continued, resulting in even further substructure within both the IAB and IETF. The IETF combined Working Groups into Areas, and designated Area Directors. An Internet Engineering Steering Group (IESG) was formed of the Area Directors. The IAB recognized the increasing importance of the IETF, and restructured the standards process to explicitly recognize the IESG as the major review body for standards. The IAB also restructured so that the rest of the Task Forces (other than the IETF) were combined into an Internet Research Task Force (IRTF) chaired by Postel, with the old task forces renamed as research groups.
The growth in the commercial sector brought with it increased concern regarding the standards process itself. Starting in the early 1980’s and continuing to this day, the Internet grew beyond its primarily research roots to include both a broad user community and increased commercial activity. Increased attention was paid to making the process open and fair. This coupled with a recognized need for community support of the Internet eventually led to the formation of the Internet Society in 1991, under the auspices of Kahn’s Corporation for National Research Initiatives (CNRI) and the leadership of Cerf, then with CNRI.
In 1992, yet another reorganization took place. In 1992, the Internet Activities Board was re-organized and re-named the Internet Architecture Board operating under the auspices of the Internet Society. A more “peer” relationship was defined between the new IAB and IESG, with the IETF and IESG taking a larger responsibility for the approval of standards. Ultimately, a cooperative and mutually supportive relationship was formed between the IAB, IETF, and Internet Society, with the Internet Society taking on as a goal the provision of service and other measures which would facilitate the work of the IETF.
The recent development and widespread deployment of the World Wide Web has brought with it a new community, as many of the people working on the WWW have not thought of themselves as primarily network researchers and developers. A new coordination organization was formed, the World Wide Web Consortium (W3C). Initially led from MIT’s Laboratory for Computer Science by Tim Berners-Lee (the inventor of the WWW) and Al Vezza, W3C has taken on the responsibility for evolving the various protocols and standards associated with the Web.
Thus, through the over two decades of Internet activity, we have seen a steady evolution of organizational structures designed to support and facilitate an ever-increasing community working collaboratively on Internet issues.
Commercialization of the Technology
Commercialization of the Internet involved not only the development of competitive, private network services, but also the development of commercial products implementing the Internet technology. In the early 1980s, dozens of vendors were incorporating TCP/IP into their products because they saw buyers for that approach to networking. Unfortunately they lacked both real information about how the technology was supposed to work and how the customers planned on using this approach to networking. Many saw it as a nuisance add-on that had to be glued on to their own proprietary networking solutions: SNA, DECNet, Netware, NetBios. The DoD had mandated the use of TCP/IP in many of its purchases but gave little help to the vendors regarding how to build useful TCP/IP products.
In 1985, recognizing this lack of information availability and appropriate training, Dan Lynch in cooperation with the IAB arranged to hold a three day workshop for ALL vendors to come learn about how TCP/IP worked and what it still could not do well. The speakers came mostly from the DARPA research community who had both developed these protocols and used them in day-to-day work. About 250 vendor personnel came to listen to 50 inventors and experimenters. The results were surprises on both sides: the vendors were amazed to find that the inventors were so open about the way things worked (and what still did not work) and the inventors were pleased to listen to new problems they had not considered, but were being discovered by the vendors in the field. Thus a two-way discussion was formed that has lasted for over a decade.
After two years of conferences, tutorials, design meetings and workshops, a special event was organized that invited those vendors whose products ran TCP/IP well enough to come together in one room for three days to show off how well they all worked together and also ran over the Internet. In September of 1988 the first Interop trade show was born. 50 companies made the cut. 5,000 engineers from potential customer organizations came to see if it all did work as was promised. It did. Why? Because the vendors worked extremely hard to ensure that everyone’s products interoperated with all of the other products – even with those of their competitors. The Interop trade show has grown immensely since then and today it is held in 7 locations around the world each year to an audience of over 250,000 people who come to learn which products work with each other in a seamless manner, learn about the latest products, and discuss the latest technology.
In parallel with the commercialization efforts that were highlighted by the Interop activities, the vendors began to attend the IETF meetings that were held 3 or 4 times a year to discuss new ideas for extensions of the TCP/IP protocol suite. Starting with a few hundred attendees mostly from academia and paid for by the government, these meetings now often exceed a thousand attendees, mostly from the vendor community and paid for by the attendees themselves. This self-selected group evolves the TCP/IP suite in a mutually cooperative manner. The reason it is so useful is that it is composed of all stakeholders: researchers, end users and vendors.
Network management provides an example of the interplay between the research and commercial communities. In the beginning of the Internet, the emphasis was on defining and implementing protocols that achieved interoperation.
As the network grew larger, it became clear that the sometime ad hoc procedures used to manage the network would not scale. Manual configuration of tables was replaced by distributed automated algorithms, and better tools were devised to isolate faults. In 1987 it became clear that a protocol was needed that would permit the elements of the network, such as the routers, to be remotely managed in a uniform way. Several protocols for this purpose were proposed, including Simple Network Management Protocol or SNMP (designed, as its name would suggest, for simplicity, and derived from an earlier proposal called SGMP) , HEMS (a more complex design from the research community) and CMIP (from the OSI community). A series of meeting led to the decisions that HEMS would be withdrawn as a candidate for standardization, in order to help resolve the contention, but that work on both SNMP and CMIP would go forward, with the idea that the SNMP could be a more near-term solution and CMIP a longer-term approach. The market could choose the one it found more suitable. SNMP is now used almost universally for network-based management.
In the last few years, we have seen a new phase of commercialization. Originally, commercial efforts mainly comprised vendors providing the basic networking products, and service providers offering the connectivity and basic Internet services. The Internet has now become almost a “commodity” service, and much of the latest attention has been on the use of this global information infrastructure for support of other commercial services. This has been tremendously accelerated by the widespread and rapid adoption of browsers and the World Wide Web technology, allowing users easy access to information linked throughout the globe. Products are available to facilitate the provisioning of that information and many of the latest developments in technology have been aimed at providing increasingly sophisticated information services on top of the basic Internet data communications.
History of the Future
On October 24, 1995, the FNC unanimously passed a resolution defining the term Internet. This definition was developed in consultation with members of the internet and intellectual property rights communities. RESOLUTION: The Federal Networking Council (FNC) agrees that the following language reflects our definition of the term “Internet”. “Internet” refers to the global information system that — (i) is logically linked together by a globally unique address space based on the Internet Protocol (IP) or its subsequent extensions/follow-ons; (ii) is able to support communications using the Transmission Control Protocol/Internet Protocol (TCP/IP) suite or its subsequent extensions/follow-ons, and/or other IP-compatible protocols; and (iii) provides, uses or makes accessible, either publicly or privately, high level services layered on the communications and related infrastructure described herein.
The Internet has changed much in the two decades since it came into existence. It was conceived in the era of time-sharing, but has survived into the era of personal computers, client-server and peer-to-peer computing, and the network computer. It was designed before LANs existed, but has accommodated that new network technology, as well as the more recent ATM and frame switched services. It was envisioned as supporting a range of functions from file sharing and remote login to resource sharing and collaboration, and has spawned electronic mail and more recently the World Wide Web. But most important, it started as the creation of a small band of dedicated researchers, and has grown to be a commercial success with billions of dollars of annual investment.
One should not conclude that the Internet has now finished changing. The Internet, although a network in name and geography, is a creature of the computer, not the traditional network of the telephone or television industry. It will, indeed it must, continue to change and evolve at the speed of the computer industry if it is to remain relevant. It is now changing to provide new services such as real time transport, in order to support, for example, audio and video streams.
The availability of pervasive networking (i.e., the Internet) along with powerful affordable computing and communications in portable form (i.e., laptop computers, two-way pagers, PDAs, cellular phones), is making possible a new paradigm of nomadic computing and communications. This evolution will bring us new applications – Internet telephone and, slightly further out, Internet television. It is evolving to permit more sophisticated forms of pricing and cost recovery, a perhaps painful requirement in this commercial world. It is changing to accommodate yet another generation of underlying network technologies with different characteristics and requirements, e.g. broadband residential access and satellites. New modes of access and new forms of service will spawn new applications, which in turn will drive further evolution of the net itself.
The most pressing question for the future of the Internet is not how the technology will change, but how the process of change and evolution itself will be managed. As this paper describes, the architecture of the Internet has always been driven by a core group of designers, but the form of that group has changed as the number of interested parties has grown. With the success of the Internet has come a proliferation of stakeholders – stakeholders now with an economic as well as an intellectual investment in the network.
We now see, in the debates over control of the domain name space and the form of the next generation IP addresses, a struggle to find the next social structure that will guide the Internet in the future. The form of that structure will be harder to find, given the large number of concerned stakeholders. At the same time, the industry struggles to find the economic rationale for the large investment needed for the future growth, for example to upgrade residential access to a more suitable technology. If the Internet stumbles, it will not be because we lack for technology, vision, or motivation. It will be because we cannot set a direction and march collectively into the future.
Did you find this resource helpful? By donating any amount, you help fund more research and content like this.
1 Perhaps this is an exaggeration based on the lead author’s residence in Silicon Valley. 2 On a recent trip to a Tokyo bookstore, one of the authors counted 14 English language magazines devoted to the Internet. 3 An abbreviated version of this article appears in the 50th anniversary issue of the CACM, Feb. 97. The authors would like to express their appreciation to Andy Rosenbloom, CACM Senior Editor, for both instigating the writing of this article and his invaluable assistance in editing both this and the abbreviated version. 4 The Advanced Research Projects Agency (ARPA) changed its name to Defense Advanced Research Projects Agency (DARPA) in 1971, then back to ARPA in 1993, and back to DARPA in 1996. We refer throughout to DARPA, the current name. 5 It was from the RAND study that the false rumor started claiming that the ARPANET was somehow related to building a network resistant to nuclear war. This was never true of the ARPANET, only the unrelated RAND study on secure voice considered nuclear war. However, the later work on Internetting did emphasize robustness and survivability, including the capability to withstand losses of large portions of the underlying networks. 6 Including amongst others Vint Cerf, Steve Crocker, and Jon Postel. Joining them later were David Crocker who was to play an important role in documentation of electronic mail protocols, and Robert Braden, who developed the first NCP and then TCP for IBM mainframes and also was to play a long term role in the ICCB and IAB. 7 This was subsequently published as V. G. Cerf and R. E. Kahn, “A protocol for packet network intercommunication”, IEEE Trans. Comm. Tech., vol. COM-22, V 5, pp. 627-641, May 1974. 8 The desirability of email interchange, however, led to one of the first “Internet books”: !%@:: A Directory of Electronic Mail Addressing and Networks, by Frey and Adams, on email address translation and forwarding. 9 Originally named Federal Research Internet Coordinating Committee, FRICC. The FRICC was originally formed to coordinate U.S. research network activities in support of the international coordination provided by the CCIRN. 10 The decommissioning of the ARPANET was commemorated on its 20th anniversary by a UCLA symposium in 1989.
P. Baran, “On Distributed Communications Networks”, IEEE Trans. Comm. Systems, March 1964. V. G. Cerf and R. E. Kahn, “A protocol for packet network interconnection”, IEEE Trans. Comm. Tech., vol. COM-22, V 5, pp. 627-641, May 1974. S. Crocker, RFC001 Host software, Apr-07-1969. R. Kahn, Communications Principles for Operating Systems. Internal BBN memorandum, Jan. 1972. Proceedings of the IEEE, Special Issue on Packet Communication Networks, Volume 66, No. 11, November 1978. (Guest editor: Robert Kahn, associate guest editors: Keith Uncapher and Harry van Trees) L. Kleinrock, “Information Flow in Large Communication Nets”, RLE Quarterly Progress Report, July 1961. L. Kleinrock, Communication Nets: Stochastic Message Flow and Delay, Mcgraw-Hill (New York), 1964. L. Kleinrock, Queueing Systems: Vol II, Computer Applications, John Wiley and Sons (New York), 1976 J.C.R. Licklider & W. Clark, “On-Line Man Computer Communication”, August 1962. L. Roberts & T. Merrill, “Toward a Cooperative Network of Time-Shared Computers”, Fall AFIPS Conf., Oct. 1966. L. Roberts, “Multiple Computer Networks and Intercomputer Communication”, ACM Gatlinburg Conf., October 1967.
Barry M. Leiner was Director of the Research Institute for Advanced Computer Science . He passed away in April 2003. Vinton G. Cerf is Vice President and Chief Internet Evangelist at Google . David D. Clark is Senior Research Scientist at the MIT Laboratory for Computer Science . Robert E. Kahn is President of the Corporation for National Research Initiatives . Leonard Kleinrock is a Distinguished Professor of Computer Science at the University of California, Los Angeles, and is a Founder of Linkabit Corp., TTI/Vanguard, Nomadix Inc., and Platformation Inc. Daniel C. Lynch is a founder of the Interop networking trade show and conferences . Jon Postel served as Director of the Computer Networks Division of the Information Sciences Institute of the University of Southern California until his untimely death October 16, 1998. Dr. Lawrence G. Roberts was CEO, President, and Chairman of Anagran, Inc . He passed away in December 2019. Stephen Wolff is Principal Scientist of Internet2 .

Early Internet
History of the internet.
The history of the Internet is a story of contributions by men and women such as J.C.R. Linklider, Leonard Kleinrock, Vint Cerf, Elizabeth (Jake) Feinler, Tim Berners-Lee, Bob Kahn, and so many others. It’s also the story of previously (and perhaps hereafter) unknown collaborations between government agencies, academia, and corporations. Most importantly, it’s the story about the creation of the most impactful technological advance the world has known to date, and the genesis of all technological advancements that will follow in its wake.
The Beginning of Network Communication
The story of the Internet begins in 1958. President Dwight D. Eisenhower created the Defense Advanced Research Projects Agency, or DARPA, to develop technologies in response to the Soviet launching of Sputnik. After research into space and rocket technology was transferred to the newly created National Aeronautics and Space Administration (NASA), computer research became a priority of DARPA. It was then that J.C.R. Linklider, head of the computer research program at DARPA, realized the possibility and importance of creating a network that allowed computers to share information between government agencies. This led to the concept of a computer network, to be called ARPANET, in 1967.
The Importance of Interface Message Processors for Network Communication
A major step towards making a computer network feasible involved breaking data into small blocks, or packets, and transmitting the packets over digital networks and reassembling the data upon arrival at the destination computer. Leonard Kleinrock introduced this packet switching theory while he was at MIT in 1964, and research on the theory continued at MIT, the RAND Corporation, and NPL throughout the mid-1960s.
In 1968, DARPA issued an RFQ to create packet switches, which the agency called Interface Message Processors (IMPs). The contract was awarded to Bolt, Beranek and Newman (BBN), an American research and development company based in Massachusetts. BBN created a team that included Bob Kahn of BBN, Lawrence Roberts of MIT, Howard Frank and others at Network Analysis Corporation, and Kleinrock (now at UCLA) and his team at UCLA’s Samueli School of Engineering.
Once developed, the IMP allowed communication between nodes networks at Kleinrock’s Network Measurement Center at UCLA and the Network Information Center led by Elizabeth Feinler at Stanford University to the ARPANET. On October 29, 1969, the first ARPANET transmission was sent, although only the letters “LO” of “HELLO” went through before the system crashed. Regardless, it showed that computers could talk to each other over a network. By the end of 1969, two more host computers, at UC Santa Barbara and the University of Utah, were connected through ARPANET.
ARPANET Goes Public
In 1972, Kahn gave the first public demonstration of the capabilities of ARPANET at the International Computer Communication Conference. Also in 1972, Ray Tomlinson of BBN wrote the first email send-and-read software to make communication between developers more efficient. For the first time, communication was not only conducted computer-to-computer, but also person-to person. This became the most widespread network application throughout the rest of the decade. Computer networks were poised to move from limited applications for sharing research between government agencies and universities into a means of communication to be accessed throughout society at large.
ARPANET Becomes the Internet
The next great development in the growth of computer networks sprung from the idea of multiple independent computer networks through “internetworking architecture”, that allowed network providers to have their own interface that could interwork with other network interfaces. Thus the single computer network of ARPANET gave way for the interconnected Internet that we know today. This development was made possible by the creation of a new version of network protocols that could operate within the environment of an open-network architecture. Bob Kahn and Vint Cerf of Stanford University designed this protocol, dubbed Transmission Control Protocol/Internet Protocol (TCP/IP). Among the features of TCP/IP was the connection of networks through what would eventually be called gateways and routers. In addition, Kahn insisted that there be no global control of the protocols at the operations level.
Other key developments soon followed. These include the:
- Introduction of the World Wide Web, a global connection of documents using Uniform
- Resource Locators (URLs) and hypertext markup language (HTL).
- Appearance of Local Area Networks (LANs) that connected computers within a limited geographic area.
- Emergence of the desktop computers that brought the Internet directly into people’s homes and offices.
- Invention of the Domain Name System (DNS) that permitted hierarchical host names to be identified as Internet addresses.
- Introduction of the UNIX operating system.
Thus the Internet became a general infrastructure that allowed for new applications to be developed and deployed by anyone on the planet who can create new software code and programs.
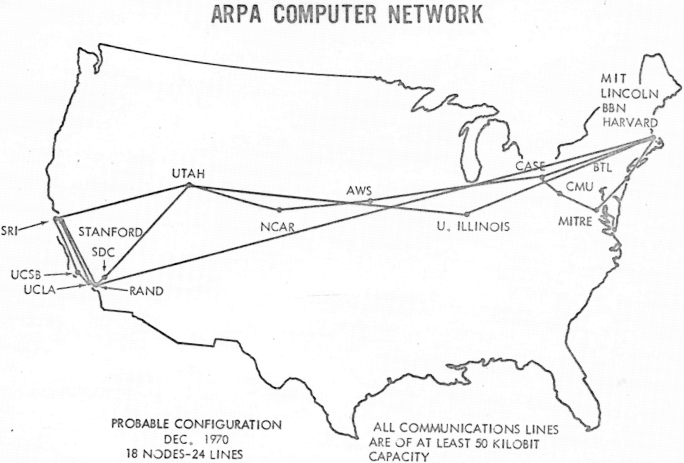
Map of ARPANET from December 1970. Courtesy of WikiCommons.
Javascript is disabled
- We are changing
- Accessible screenings
- Sound and Vision
- Objects and stories
- Researchers
- Access to our collection
- Research help
- Research directory
- Donate an object
- Science Museum Group Journal
- Press office
- Support the museum
- Volunteering
- Corporate sponsorship
National Science and Media Museum Bradford BD1 1NQ
The museum, IMAX and Pictureville are temporarily closed. Find out about our major transformation .
A short history of the internet
Published: 3 December 2020
Read about the history of the internet, from its 1950s origins to the World Wide Web’s explosion in popularity in the late 1990s and the ‘dotcom bubble’.
The origins of the internet
The origins of the internet are rooted in the USA of the 1950s. The Cold War was at its height and huge tensions existed between North America and the Soviet Union. Both superpowers were in possession of deadly nuclear weapons, and people lived in fear of long-range surprise attacks. The US realised it needed a communications system that could not be affected by a Soviet nuclear attack.
At this time, computers were large, expensive machines exclusively used by military scientists and university staff.
These machines were powerful but limited in numbers, and researchers grew increasingly frustrated: they required access to the technology, but had to travel great distances to use it.
To solve this problem, researchers started ‘time-sharing’. This meant that users could simultaneously access a mainframe computer through a series of terminals, although individually they had only a fraction of the computer’s actual power at their command.
The difficulty of using such systems led various scientists, engineers and organisations to research the possibility of a large-scale computer network.
Who invented the internet?
No one person invented the internet. When networking technology was first developed, a number of scientists and engineers brought their research together to create the ARPANET . Later, other inventors’ creations paved the way for the web as we know it today.
• PAUL BARAN (1926–2011)
An engineer whose work overlapped with ARPA’s research. In 1959 he joined an American think tank, the RAND Corporation, and was asked to research how the US Air Force could keep control of its fleet if a nuclear attack ever happened. In 1964 Baran proposed a communication network with no central command point. If one point was destroyed, all surviving points would still be able to communicate with each other. He called this a distributed network.
• LAWRENCE ROBERTS (1937–2018)
Chief scientist at ARPA, responsible for developing computer networks. Paul Baran’s idea appealed to Roberts, and he began to work on the creation of a distributed network.
• LEONARD KLEINROCK (1934–)
An American scientist who worked towards the creation of a distributed network alongside Lawrence Roberts.
• DONALD DAVIES (1924–2000)
A British scientist who, at the same time as Roberts and Kleinrock, was developing similar technology at the National Physical Laboratory in Middlesex.
• BOB KAHN (1938–) AND VINT CERF (1943–)
American computer scientists who developed TCP/IP , the set of protocols that governs how data moves through a network. This helped the ARPANET evolve into the internet we use today. Vint Cerf is credited with the first written use of the word ‘internet’.
When asked to explain my role in the creation of the internet, I generally use the example of a city. I helped to build the roads—the infrastructure that gets things from point A to point B. —Vint Cerf, 2007
• PAUL MOCKAPETRIS (1948–) AND JON POSTEL (1943–98)
Inventors of DNS , the ‘phone book of the internet’.
• TIM BERNERS-LEE (1955–)
Creator of the World Wide Web who developed many of the principles we still use today, such as HTML, HTTP, URLs and web browsers.
There was no “Eureka!” moment. It was not like the legendary apple falling on Newton’s head to demonstrate the concept of gravity. Inventing the World Wide Web involved my growing realisation that there was a power in arranging ideas in an unconstrained, weblike way. And that awareness came to me through precisely that kind of process. The Web arose as the answer to an open challenge, through the swirling together of influences, ideas, and realisations from many sides. —Tim Berners-Lee, Weaving the Web , 1999
• MARC ANDREESSEN (1971–)
Inventor of Mosaic, the first widely-used web browser.
The first use of a computer network
In 1965, Lawrence Roberts made two separate computers in different places ‘talk’ to each other for the first time. This experimental link used a telephone line with an acoustically coupled modem, and transferred digital data using packets.
When the first packet-switching network was developed, Leonard Kleinrock was the first person to use it to send a message. He used a computer at UCLA to send a message to a computer at Stanford. Kleinrock tried to type ‘login’ but the system crashed after the letters ‘L’ and ‘O’ had appeared on the Stanford monitor.
A second attempt proved successful and more messages were exchanged between the two sites. The ARPANET was born.
The life and death of the ARPANET
President Dwight D. Eisenhower formed the Advanced Research Projects Agency (ARPA) in 1958, bringing together some of the best scientific minds in the country. Their aim was to help American military technology stay ahead of its enemies and prevent surprises, such as the launch of the satellite Sputnik 1, happening again. Among ARPA’s projects was a remit to test the feasibility of a large-scale computer network.
Lawrence Roberts was responsible for developing computer networks at ARPA, working with scientist Leonard Kleinrock. Roberts was the first person to connect two computers. When the first packet-switching network was developed in 1969, Kleinrock successfully used it to send messages to another site, and the ARPA Network—or ARPANET—was born.
Once ARPANET was up and running, it quickly expanded. By 1973, 30 academic, military and research institutions had joined the network, connecting locations including Hawaii, Norway and the UK.
As ARPANET grew, a set of rules for handling data packets needed to be put in place. In 1974, computer scientists Bob Kahn and Vint Cerf invented a new method called transmission-control protocol, popularly known as TCP/IP , which essentially allowed computers to speak the same language.
After the introduction of TCP/IP, ARPANET quickly grew to become a global interconnected network of networks, or ‘Internet’.
The ARPANET was decommissioned in 1990.
What is packet switching?
‘Packet switching’ is a method of splitting and sending data. A computer file is effectively broken up into thousands of small segments called ‘packets’—each typically around 1500 bytes—distributed across a network, and then reordered back into a single file at their destination. The packet switching method is very reliable and allows data to be sent securely, even over damaged networks; it also uses bandwidth very efficiently and doesn’t need a single dedicated link, like a telephone call does.
The world’s first packet-switching computer network was produced in 1969. Computers at four American universities were connected using separate minicomputers known as ‘Interface Message Processors’ or ‘IMPs’. The IMPs acted as gateways for the packets and have since evolved into what we now call ‘routers’.
Packet switching is the basis on which the internet still works today.
What is TCP/IP?
TCP/IP stands for Transmission Control Protocol/Internet Protocol. The term is used to describe a set of protocols that govern how data moves through a network.
After the creation of ARPANET, more networks of computers began to join the network, and the need arose for an agreed set of rules for handling data. In 1974 two American computer scientists, Bob Kahn and Vint Cerf, proposed a new method that involved sending data packets in a digital envelope or ‘datagram’. The address on the datagram can be read by any computer, but only the final host machine can open the envelope and read the message inside.
Kahn and Cerf called this method transmission-control protocol (TCP). TCP allowed computers to speak the same language, and it helped the ARPANET to grow into a global interconnected network of networks, an example of ‘internetworking’—internet for short.
IP stands for Internet Protocol and, when combined with TCP, helps internet traffic find its destination. Every device connected to the internet is given a unique IP number. Known as an IP address, the number can be used to find the location of any internet-connected device in the world.
What is DNS?
DNS stands for Domain Name System. It is the internet’s equivalent of a phone book, and converts hard-to-remember IP addresses into simple names.
In the early 1980s, cheaper technology and the appearance of desktop computers allowed the rapid development of local area networks (LANs). An increase in the amount of computers on the network made it difficult to keep track of all the different IP addresses.
This problem was solved by the introduction of the Domain Name System (DNS) in 1983. DNS was invented by Paul Mockapetris and Jon Postel at the University of Southern California. It was one of the innovations that paved the way for the World Wide Web.
The beginnings of email
Email was a rapid—but unintended—consequence of the growth of ARPANET. As the network increased in popularity and scope, users quickly realised the potential of the network as a tool for sending messages between different ARPANET computers.
Ray Tomlinson , an American computer programmer, is responsible for electronic mail as we know it today. He introduced the idea that the destination of a message should be indicated using the @ symbol, which was first used to distinguish between the individual user’s name and that of their computer (i.e. user@computer). When DNS was introduced, this was extended to [email protected] .
Early email users sent personal messages and began mailing lists on specific topics. One of the first big mailing lists was ‘SF-LOVERS’ for science fiction fans.
The development of email showed how the network had transformed. Rather than a way of accessing expensive computing power, it had started to become a place to communicate, gossip and make friends.
Early home computers
From the 1970s onwards, the home computer industry grew exponentially. The uptake of home computers was not necessarily driven by users’ needs or a computer’s functionality; early machines could actually do relatively little. The appeal to the consumer was the idea of becoming part of the ‘Information Revolution’. Computers were embedded with the rhetoric of the future and learning, but in most cases this meant learning to program so that people could actually make the technology do something, such as play games.

More information about collection object
The growth of the internet, 1985–95.
The invention of DNS, the common use of TCP/IP and the popularity of email caused an explosion of activity on the internet. Between 1986 and 1987, the network grew from 2,000 hosts to 30,000. People were now using the internet to send messages to each other, read news and swap files. However, advanced knowledge of computing was still needed to dial in to the system and use it effectively, and there was still no agreement on the way that documents on the network were formatted.
The internet needed to be easier to use. An answer to the problem appeared in 1989 when a British computer scientist named Tim Berners-Lee submitted a proposal to his employer, CERN, the international particle-research laboratory in Geneva, Switzerland. Berners-Lee proposed a new way of structuring and linking all the information available on CERN’s computer network that made it quick and easy to access. His concept for a ‘web of information’ would ultimately become the World Wide Web.
The launch of the Mosaic browser in 1993 opened up the web to a new audience of non-academics, and people started to discover how easy it was to create their own HTML web pages. Consequently, the number of websites grew from 130 in 1993 to over 100,000 at the start of 1996.
By 1995 the internet and the World Wide Web were established phenomena: Netscape Navigator, which was the most popular browser at the time, had around 10 million global users.
How is the World Wide Web different from the internet?
The terms ‘World Wide Web’ and ‘internet’ are often confused. The internet is the networking infrastructure that connects devices together, while the World Wide Web is a way of accessing information through the medium of the internet.
Tim Berners-Lee first proposed the idea of a ‘web of information’ in 1989. It relied on ‘hyperlinks’ to connect documents together. Written in Hypertext Markup Language (HTML), a hyperlink can point to any other HTML page or file that sits on top of the internet.
In 1990, Berners-Lee developed Hypertext Transfer Protocol (HTTP) and designed the Universal Resource Identifier (URI) system. HTTP is the language computers use to communicate HTML documents over the internet, and the URI, also known as a URL, provides a unique address where the pages can be easily found.
Berners-Lee also created a piece of software that could present HTML documents in an easy-to-read format. He called this ‘browser’ the ‘WorldWideWeb’.

On 6 August 1991 the code to create more web pages and the software to view them was made freely available on the internet. Computer enthusiasts around the world began setting up their own websites. Berners-Lee’s vision of a free, global and shared information space began to take shape.
The dream behind the Web is of a common information space in which we communicate by sharing information. Its universality is essential: the fact that a hypertext link can point to anything, be it personal, local or global, be it draft or highly polished. Tim Berners-Lee (1998)
The introduction of web browsers
Tim Berners-Lee was the first to create a piece of software that could present HTML documents in an easy-to-read format. He called this ‘browser’ the ‘WorldWideWeb’. However, this original application had limited use as it could only be used on advanced NeXT machines . A simplified version that could run on any computer was created by Nicola Pellow, a maths student who worked alongside Berners-Lee at CERN.
In 1993, Marc Andreessen, an American student in Illinois, launched a new browser called Mosaic. Created at the National Center for Super-computing Applications (NCSA), Mosaic was easy to download and install, worked on many different computers and provided simple point-and-click access to the World Wide Web. Mosaic was also the first browser to display images next to text, rather than in a separate window.
Mosaic’s simplicity opened the web up to a new audience, and caused an explosion of activity on the internet, with the number of websites growing from 130 in 1993 to over 100,000 at the start of 1996.
In 1994 Andreesen formed Netscape Communications with entrepreneur Jim Clark. They led the company to create Netscape Navigator, a widely used internet browser that at the time was faster and more sophisticated than any of the competition. By 1995, Navigator had around 10 million global users.
Early ecommerce and the ‘dotcom bubble’
The enormous excitement surrounding the internet led to a massive boom in new technology shares between 1998 and 2000. This became known as the ‘dotcom bubble’.
The claim was that world industry was experiencing a ‘new economic paradigm’, the likes of which had never been experienced before. Investors in the stock market began to believe the hype and threw themselves into a frenzy of activity. The internet was thought to be central to economic growth, while share prices implied that new online companies carried the seeds for expansion. This led in turn to a feverish level of investment and unrealistic expectations about rates of return.
We have entered a period of sustained growth that could eventually double the world’s economy every dozen years and bring increasing prosperity for—quite literally—billions of people on the planet. We are riding the early waves of a 25-year run of a greatly expanding economy that will do much to solve seemingly intractable problems like poverty and to ease tensions throughout the world. —Peter Schwartz and Peter Leyden, Wired , July 1997
Venture capitalists flourished and many companies were founded on dubious business plans. The most notorious of these was the high fashion online retailer Boo.com, which spent its way through $200 million, only to collapse within six months of its website going live.
However, despite their failure, such businesses helped cause a fundamental transformation and left an important legacy. Many investors lost money, but they also helped to finance the new system and lay the groundwork for future success in ecommerce.
Further reading
- Brief History of the Internet , Internet Society
- Internet History 1962 to 1992 , Computer History Museum
- Internet Pioneers , ibiblio
- Tim Berners-Lee biography , World Wide Web Consortium
- The World Wide Web: A global information space , Science Museum
- John Naughton, A Brief History of the Future: The Origins of the Internet , 1999
- Katie Hafner and Matthew Lyon, Where Wizards Stay Up Late: The Origins of the Internet , 1996
- Tim Berners-Lee, Weaving the Web , 1999
More objects and stories

The first digital photos, from Victorian technology to the internet
Read about the first experiments in digital image technology—which took place longer ago than you might think.

Investigate the development of calculating, computing and data processing technology.

Yorkshire Games Festival
A festival celebrating videogames, with special guests, workshops and fun-packed activities for gamers of all ages.
- Part of the Science Museum Group
- Terms and conditions
- Privacy and cookies
- Modern Slavery Statement
- Web accessibility
The internet: History, evolution and how it works
The Internet is a massive computer network that has revolutionized communication and changed the world forever.

What is the internet?
- Internet invention
- How it works
How do websites work?
- Speed and bandwidth
Additional resources
Bibliography.
The internet is a vast network that connects computers across the world via more than 750,000 miles (1,200,000 kilometres) of cable running under land and sea, according to the University of Colorado Boulder.
It is the world's fastest method of communication, making it possible to send data from London, U.K. to Sydney, Australia in just 250 milliseconds, for example. Constructing and maintaining the internet has been a monumental feat of ingenuity.
The internet is a giant computer network, linking billions of machines together by underground and underwater fibre-optic cables.These cables run connect continents and islands , everywhere except Antarctica
Each cable contains strands of glass that transmit data as pulses of light, according to the journal Science . Those strands are wrapped in layers of insulation and buried beneath the sea floor by ships carrying specialist ploughs. This helps to protect them from everything from corrosion to shark bites.
When you use it, your computer or device sends messages via these cables asking to access data stored on other machines. When accessing the internet, most people will be using the world wide web.

When was the internet invented?
It was originally created by the U.S. government during the Cold War . In 1958, President Eisenhower founded the Advanced Research Projects Agency ( ARPA ) to give a boost to the country’s military technology, according to the Journal of Cyber Policy . Scientists and engineers developed a network of linked computers called ARPANET.
- The Internet of Things: A seamless network of everyday objects
- What is cyberwarfare?
- Internet history timeline: ARPANET to the World Wide Web
ARPANET's original aim was to link two computers in different places, enabling them to share data. That dream became a reality in 1969, according to Historian Jeremy Norman . In the years that followed, the team linked dozens of computers together and, by the end of the 1980s, the network contained more than 30,000 machines, according to the U.K.'s Science and Media Museum .
How the onternet works
Most computers connect to the internet without the use of wires, using Wi-Fi , via a physical modem. It connects via a wire to a socket in the wall, which links to a box outside. That box connects via still more wires to a network of cables under the ground. Together, they convert radio waves to electrical signals to fibre optic pulses, and back again.
At every connection point in the underground network, there are junction boxes called routers. Their job is to work out the best way to pass data from your computer to the computer with which you’re trying to connect. According to the IEEE International Conference on Communications , they use your IP addresses to work out where the data should go. Latency is the technical word that describes how long it takes data to get from one place to another, according to Frontier .

Each router is only connected to its local network. If a message arrives for a computer that the router doesn’t recognizse, it passes it on to a router higher up in the local network. They each maintain an address book called a routing table . According to the Internet Protocol Journal , it shows the paths through the network to all the local IP addresses.
The internet sends data around the world, across land and sea, as displayed on the Submarine Cable Map . The data passes between networks until it reaches the one closest to its destination. Then, it passes through local routers until it arrives at the computer with the matching IP address.
The internet relies upon the two connecting computers speaking the same digital language. To achieve this, there is a set of rules called the Transmission Control Protocol (TCP) and Internet Protocol (IP), according to the web infrastructure and website security company Cloudflare .
TCP/IP makes the internet work a bit like a postal system. There is an address book that contains the identity of every device on the network, and a set of standard envelopes for packaging up data. The envelopes must carry the address of the sender, the address of the recipient, and details about the information packed inside. The IP, explains how the address system works, whileTCP, how to package and send the data.
Click the numbers on the following interactive image to find out what happens when you type www.livescience.com into your browser:
Internet speed and bandwidth
When it comes to internet speed how much data you can download in one second: bandwidth. According to Tom’s Guide , to surf the web, check your email, and update your social media, 25 megabits per second is enough. But, if you want to watch 4K movies, live stream video, or play online multiplayer games, you might need speeds of up to 100-200 megabits per second.
Your download speed depends on one main factor: the quality of the underground cables that link you to the rest of the world. Fibre optic cables send data much faster than their copper counterparts, according to the cable testing company BASEC , and your home internet is limited by the infrastructure available in your area.
Jersey has the highest average bandwidth in the world, according to Cable.co.uk . The little British island off the coast of France boasts average download speeds of over 274 megabits per second. Turkmenistan has the lowest, with download speeds barely reaching 0.5 megabits per second.
You can read more about the history of the internet at the Internet Society website . To discover how the Internet has changed our daily lives, read this article by Computing Australia .
- " Getting to the bottom of the internet’s carbon footprint ". University of Colorado Boulder, College of Media, Communication and Information (2021).
- " The evolution of the Internet: from military experiment to General Purpose Technology ". Journal of Cyber Policy (2016).
- " The Internet: Past, Present, and Future ". Educational Technology (1997).
- " Three-Way Handshake ". CISSP Study Guide (Second Edition) (2012).
- " Content Routers: Fetching Data on Network Path ". IEEE International Conference on Communications (2011).
- " Analyzing the Internet's BGP Routing Table ". The Internet Protocol Journal (2001).
- " The Internet of Tomorrow ". Science (1999).
Sign up for the Live Science daily newsletter now
Get the world’s most fascinating discoveries delivered straight to your inbox.
Laura Mears is a biologist who left the confines of the lab for the rigours of an office desk as a keen science writer and a full-time software engineer. Laura has previously written for the magazines How It Works and T3 . Laura's main interests include science, technology and video games.
Follow Live Science on social media
Live Science daily newsletter: Get amazing science every day
'Dragon' and 'tree of life' hydrothermal vents discovered in Arctic region scientists thought was geologically dead
Most Popular
- 2 Self-healing 'living skin' can make robots more humanlike — and it looks just as creepy as you'd expect
- 3 Milky Way's black hole 'exhaust vent' discovered in eerie X-ray observations
- 4 James Webb Space Telescope spies strange shapes above Jupiter's Great Red Spot
- 5 What defines a species? Inside the fierce debate that's rocking biology to its core
- 2 What causes you to get a 'stitch in your side'?
- 3 Tasselled wobbegong: The master of disguise that can eat a shark almost as big as itself
- 4 Self-healing 'living skin' can make robots more humanlike — and it looks just as creepy as you'd expect
- 5 This robot could leap higher than the Statue of Liberty — if we ever build it properly
Philip Emeagwali, Nigerian American Computer Pioneer
- Famous Inventors
- Famous Inventions
- Patents & Trademarks
- Invention Timelines
- Computers & The Internet
- American History
- African American History
- African History
- Ancient History and Culture
- Asian History
- European History
- Latin American History
- Medieval & Renaissance History
- Military History
- The 20th Century
- Women's History
- M.L.S, Library Science, Indiana University
Philip Emeagwali (born August 23, 1954) is a Nigerian American computer scientist. He achieved computing breakthroughs that helped lead to the development of the internet . His work with simultaneous calculations on connected microprocessors earned him a Gordon Bell Prize, considered the Nobel Prize of computing.
Fast Facts: Philip Emeagwali
- Occupation : Computer scientist
- Born : August 23, 1954 in Akure, Nigeria
- Spouse: Dale Brown
- Child: Ijeoma Emeagwali
- Key Achievement: 1989 Gordon Bell Prize from the Institute of Electronics and Electrical Engineers
- Notable Quote : "My focus is not on solving nature's deeper mysteries. It is on using nature's deeper mysteries to solve important societal problems."
Early Life in Africa
Born in Akure, a village in Nigeria, Philip Emeagwali was the oldest in a family of nine children. His family and neighbors considered him a prodigy because of his skills as a math student. His father spent a significant amount of time nurturing his son's education. By the time Emeagwali reached high school, his facility with numbers had earned him the nickname "Calculus."
Fifteen months after Emeagwali's high school education began, the Nigerian Civil War erupted, and his family, part of the Nigerian Igbo tribe, fled to the eastern part of the country. He found himself drafted into the army of the seceding state of Biafra. Emeagwali's family lived in a refugee camp until the war ended in 1970. More than half a million Biafrans died of starvation during the Nigerian Civil War.
After the war ended, Emeagwali doggedly continued to pursue his education. He attended school in Onitsha, Nigeria, and walked two hours to and from school each day. Unfortunately, he had to drop out due to financial problems. After continuing to study, he passed a high school equivalency exam administered by the University of London in 1973. The education efforts paid off when Emeagwali earned a scholarship to attend college in the U.S.
College Education
Emeagwali traveled to the U.S. in 1974 to attend Oregon State University. Upon arrival, in the course of one week, he used a telephone, visited a library, and saw a computer for the first time. He earned his degree in mathematics in 1977. Later, he attended George Washington University to earn a Master of Ocean and Marine Engineering. He also holds a second master's degree from the University of Maryland in applied mathematics.
While attending the University of Michigan on a doctoral fellowship in the 1980s, Emeagwali began work on a project to use computers to help identify untapped underground oil reservoirs . He grew up in Nigeria, an oil-rich country, and he understood computers and how to drill for oil. Conflict over control of oil production was one of the critical causes of the Nigerian Civil War.
Computing Achievements
Initially, Emeagwali worked on the oil discovery problem using a supercomputer. However, he decided it was more efficient to use thousands of widely distributed microprocessors to do his calculations instead of tying up eight expensive supercomputers. He discovered an unused computer at the Los Alamos National Laboratory formerly used to simulate nuclear explosions. It was dubbed the Connection Machine.
Emeagwali began hooking up over 60,000 microprocessors. Ultimately, the Connection Machine, programmed remotely from Emeagwali's apartment in Ann Arbor, Michigan, ran more than 3.1 billion calculations per second and correctly identified the amount of oil in a simulated reservoir. The computing speed was faster than that achieved by a Cray supercomputer.
Describing his inspiration for the breakthrough, Emeagwali said that he remembered observing bees in nature. He saw that their way of working together and communicating with each other was inherently more efficient than trying to accomplish tasks separately. He wanted to make computers emulate the construction and operation of a beehive's honeycomb.
Emeagwali's primary achievement wasn't about oil. He demonstrated a practical and inexpensive way to allow computers to speak with each other and collaborate all around the world. The key to his achievement was programming each microprocessor to talk with six neighboring microprocessors simultaneously. The discovery helped lead to the development of the internet.
Emeagwali's work earned him the Institute of Electronics and Electrical Engineers' Gordon Bell Prize in 1989, considered the "Nobel Prize" of computing. He continues to work on computing problems, including models to describe and predict the weather, and he has earned more than 100 honors for his breakthrough achievements. Emeagwali is one of the most prominent inventors of the 20th century.
- Who Invented the Microchip?
- A List of Every Nobel Prize Winner in English Literature
- Biography of John Bardeen, Nobel Prize-Winning Physicist
- Biography of Mark Dean, Computer Pioneer
- Biography of Chinua Achebe, Author of "Things Fall Apart"
- The History of Computers
- Biography of William Shockley, American Physicist and Inventor
- January Calendar of Famous Inventions and Birthdays
- The History of the Transistor
- Biography of Alfred Nobel, Inventor of Dynamite
- Biography of Alan Turing, Code-Breaking Computer Scientist
- September Calendar of Famous Inventions and Birthdays
- October Calendar of Famous Inventions and Birthdays
- August Calendar of Famous Inventions and Birthdays
- The Atanasoff-Berry Computer: The First Electronic Computer
- Jack Kilby, Father of the Microchip
Asia & Oceania
Middle east & africa.
- Middle East - English
- Middle East - Farsi
- Sub-Saharan Africa
- Sub-Saharan Africa Gold
- الشرق الأوسط - العربية
- خاور میانه - فارسی
- Česká republika
- Deutschland
- Magyarország
SHOWS BY SUBJECT
Megastructures, engineering, catch-up shows, don't miss, aussie snake wranglers too close for comfort thursday 11 july 2024 at 7:00pm, aussie snake wranglers tripe threat thursday 11 july 2024 at 7:30pm, extraordinary birder with christian cooper extraordinary birder with christian cooper: puerto rico thursday 11 july 2024 at 8:00pm, primal survivor: extreme african safari valley of giants thursday 11 july 2024 at 9:00pm, world's greatest train journeys from above australia's outback railway thursday 11 july 2024 at 10:00pm.
- America's National Parks
- JFK: One Day in America
- Wicked Tuna
- Border Protection Spain
- Growing up Animal
Science Fair: The Series
- Drug Lords: The Takedown

Aussie Snake Wranglers 00:30 Aussie Snake Wranglers following the busiest snake...

Extraordinary Birder With Christian Cooper 00:30 Life-long birder Christian Cooper takes us on a journey...

Primal Survivor: Extreme African Safari 00:30 Wilderness explorer and survival expert Hazen Audel...

Dead By Dawn 00:30 Witness the wild horror that animals have to face once...
Most viewed, fight science show: fight science, genius - scientist show: genius, naked science show: naked science, katie’s new face show: katie’s new face, europe from above show: europe from above, human weapons show: fight science, the hot zone show: the hot zone, is it real show: is it real, secrets of the octopus show: secrets of the octopus, photo of the day.
![biography of the internet The team carefully secure Liberty... [Photo of the day - 11 JULY 2024]](https://assets-natgeotv.fnghub.com/POD/15400.ThumbL.jpg)

11 JULY 2024 The team carefully secure Liberty the baby great white... National Geographic/James Blake
![biography of the internet A closer look as snake catcher Simon... [Photo of the day - 10 JULY 2024]](https://assets-natgeotv.fnghub.com/POD/15398.ThumbL.jpg)
10 JULY 2024 A closer look as snake catcher Simon Keys carefully... Earth Touch
![biography of the internet Hot Tuna First Mate Jarrett... [Photo of the day - 9 JULY 2024]](https://assets-natgeotv.fnghub.com/POD/15396.ThumbL.jpg)
9 JULY 2024 Hot Tuna First Mate Jarrett Przybyszewski. This is from... PFTV
Food factory - season 3 show: food factory, big cat week show: big cat week, rover sd1 show: car s.o.s, kim il sung show: dictators rulebook, messerschmitt kr200 show: car s.o.s, lion specials show: lion specials.
- TV LISTINGS

INSIDE THE INTERNET: 50 YEARS OF LIFE ONLINE
Exclusive videos.

Inside The Internet: 50 Years of Life Online
From its humble California origins to the dotcom bust to its transformation of the way we live,...
ABOUTTHESHOW
Inside the internet: 50 years of life online on facebook.

Follow us on Facebook
The official page for National Geographic Channel Abu Dhabi.
More On History

Europe from Above

Dictators Rulebook

Ww2: Hell Under The Sea

- WEEKLY ARTICLES
About National Geographic Abu Dhabi
- How To Watch
Site Information
Top galleries.
- Unsubscribe
Fox Channels
- Fox Networks Group Middle East
© 2024 National Geographic Abu Dhabi, All Rights Reserved

Technology to defeat Ebola
Mathematics for a sustainable world, openmind books, scientific anniversaries, what is the purpose of music, featured author, latest book, how the internet has changed everyday life, what happened.
The Internet has turned our existence upside down. It has revolutionized communications, to the extent that it is now our preferred medium of everyday communication. In almost everything we do, we use the Internet. Ordering a pizza, buying a television, sharing a moment with a friend, sending a picture over instant messaging. Before the Internet, if you wanted to keep up with the news, you had to walk down to the newsstand when it opened in the morning and buy a local edition reporting what had happened the previous day. But today a click or two is enough to read your local paper and any news source from anywhere in the world, updated up to the minute.
The Internet itself has been transformed. In its early days—which from a historical perspective are still relatively recent—it was a static network designed to shuttle a small freight of bytes or a short message between two terminals; it was a repository of information where content was published and maintained only by expert coders. Today, however, immense quantities of information are uploaded and downloaded over this electronic leviathan, and the content is very much our own, for now we are all commentators, publishers, and creators.
In the 1980s and 1990s, the Internet widened in scope to encompass the IT capabilities of universities and research centers, and, later on, public entities, institutions, and private enterprises from around the world. The Internet underwent immense growth; it was no longer a state-controlled project, but the largest computer network in the world, comprising over 50,000 sub-networks, 4 million systems, and 70 million users.
The emergence of web 2.0 in the first decade of the twenty-first century was itself a revolution in the short history of the Internet, fostering the rise of social media and other interactive, crowd-based communication tools.
The Internet was no longer concerned with information exchange alone: it was a sophisticated multidisciplinary tool enabling individuals to create content, communicate with one another, and even escape reality. Today, we can send data from one end of the world to the other in a matter of seconds, make online presentations, live in parallel “game worlds,” and use pictures, video, sound, and text to share our real lives, our genuine identity. Personal stories go public; local issues become global.
The rise of the Internet has sparked a debate about how online communication affects social relationships. The Internet frees us from geographic fetters and brings us together in topic-based communities that are not tied down to any specific place. Ours is a networked, globalized society connected by new technologies. The Internet is the tool we use to interact with one another, and accordingly poses new challenges to privacy and security.
Information technologies have wrought fundamental change throughout society, driving it forward from the industrial age to the networked era. In our world, global information networks are vital infrastructure—but in what ways has this changed human relations? The Internet has changed business, education, government, healthcare, and even the ways in which we interact with our loved ones—it has become one of the key drivers of social evolution.
The changes in social communication are of particular significance. Although analogue tools still have their place in some sectors, new technologies are continuing to gain ground every day, transforming our communication practices and possibilities—particularly among younger people. The Internet has removed all communication barriers. Online, the conventional constraints of space and time disappear and there is a dizzyingly wide range of communicative possibilities. The impact of social media applications has triggered discussion of the “new communication democracy.”
The development of the Internet today is being shaped predominantly by instant, mobile communications. The mobile Internet is a fresh revolution. Comprehensive Internet connectivity via smartphones and tablets is leading to an increasingly mobile reality: we are not tied to any single specific device, and everything is in the cloud.
People no longer spend hours gazing at a computer screen after work or class; instead, they use their mobile devices to stay online everywhere, all the time.
Anyone failing to keep abreast of this radical change is losing out on an opportunity.
Communication Opportunities Created by the Internet
The Internet has become embedded in every aspect of our day-to-day lives, changing the way we interact with others. This insight struck me when I started out in the world of social media. I created my first social network in 2005, when I was finishing college in the United States—it had a political theme. I could already see that social media were on the verge of changing our way of communicating, helping us to share information by opening up a new channel that cuts across conventional ones.
That first attempt did not work out, but I learned from the experience.I get the feeling that in many countries failure is punished too harshly—but the fact is, the only surefire way of avoiding failure is to do nothing at all. I firmly believe that mistakes help you improve; getting it wrong teaches you how to get it right. Creativity, hard work, and a positive attitude will let you achieve any goal.
In 2006, after I moved to Spain, I created Tuenti. Tuenti (which, contrary to widespread belief, has nothing to do with the number 20; it is short for “tu entidad,” the Spanish for “your entity”) is a social communication platform for genuine friends. From the outset, the idea was to keep it simple, relevant, and private. That’s the key to its success.
I think the real value of social media is that you can stay in touch from moment to moment with the people who really matter to you. Social media let you share experiences and information; they get people and ideas in touch instantly, without frontiers. Camaraderie, friendship, and solidarity—social phenomena that have been around for as long as humanity itself—have been freed from the conventional restrictions of space and time and can now thrive in a rich variety of ways.
Out of all the plethora of communication opportunities that the Internet has opened up, I would highlight the emergence of social media and the way they have intricately melded into our daily lives. Social media have changed our personal space, altering the way we interact with our loved ones, our friends, and our sexual partners; they have forced us to rethink even basic daily processes like studying and shopping; they have affected the economy by nurturing the business startup culture and electronic commerce; they have even given us new ways to form broad-based political movements.
The Internet and Education
The Internet has clearly impacted all levels of education by providing unbounded possibilities for learning. I believe the future of education is a networked future. People can use the Internet to create and share knowledge and develop new ways of teaching and learning that captivate and stimulate students’ imagination at any time, anywhere, using any device. By connecting and empowering students and educators, we can speed up economic growth and enhance the well-being of society throughout the world. We should work together, over a network, to build the global learning society.
The network of networks is an inexhaustible source of information. What’s more, the Internet has enabled users to move away from their former passive role as mere recipients of messages conveyed by conventional media to an active role, choosing what information to receive, how, and when. The information recipient even decides whether or not they want to stay informed.
We have moved on from scattergun mass communication to a pattern where the user proactively selects the information they need.
Students can work interactively with one another, unrestricted by physical or time constraints. Today, you can use the Internet to access libraries, encyclopedias, art galleries, news archives, and other information sources from anywhere in the world: I believe this is a key advantage in the education field. The web is a formidable resource for enhancing the process of building knowledge.
I also believe the Internet is a wonderful tool for learning and practicing other languages—this continues to be a critical issue in many countries, including Spain, and, in a globalized world, calls for special efforts to improve.
The Internet, in addition to its communicative purposes, has become a vital tool for exchanging knowledge and education; it is not just an information source, or a locus where results can be published, it is also a channel for cooperating with other people and groups who are working on related research topics.
The Internet and Privacy and Security
Another key issue surrounding Internet use is privacy. Internet users are becoming more sensitive to the insight that privacy is a must-have in our lives.
Privacy has risen near the top of the agenda in step with an increasing awareness of the implications of using social media. Much of the time, people started to use social media with no real idea of the dangers, and have wised up only through trial and error—sheer accident, snafus, and mistakes. Lately, inappropriate use of social media seems to hit the headlines every day. Celebrities posting inappropriate comments to their profiles, private pictures and tapes leaked to the Internet at large, companies displaying arrogance toward users, and even criminal activities involving private-data trafficking or social media exploitation.
All this shows that—contrary to what many people seem to have assumed—online security and privacy are critical, and, I believe, will become even more important going forward. And, although every user needs privacy, the issue is particularly sensitive for minors—despite attempts to raise their awareness, children still behave recklessly online.
I have always been highly concerned about privacy. On Tuenti, the default privacy setting on every user account is the highest available level of data protection. Only people the user has accepted as a “friend” can access their personal details, see their telephone number, or download their pictures. This means that, by default, user information is not accessible to third parties. In addition, users are supported by procedures for reporting abuse. Any user can report a profile or photograph that is abusive, inappropriate, or violates the terms of use: action is taken immediately. Security and privacy queries are resolved within 24 hours.
We need to be aware that different Internet platforms provide widely different privacy experiences. Some of them are entirely open and public; no steps whatsoever are taken to protect personal information, and all profiles are indexable by Internet search engines.
On the other hand, I think the debate about whether social media use should be subject to an age requirement is somewhat pointless, given that most globally active platforms operate without age restrictions. The European regulatory framework is quite different from the United States and Asian codes. Companies based in Europe are bound by rigorous policies on privacy and underage use of social media. This can become a competitive drawback when the ground rules do not apply equally to all players—our American and Japanese competitors, for instance, are not required to place any kind of age constraint on access.
Outside the scope of what the industry or regulators can do, it is vital that users themselves look after the privacy of their data. I believe the information is the user’s property, so the user is the only party entitled to control the collection, use, and disclosure of any information about him or herself. Some social networks seem to have forgotten this fact—they sell data, make it impossible to delete an account, or make it complex and difficult to manage one’s privacy settings. Everything should be a lot simpler and more transparent.
Social networks should continue to devote intense efforts to developing self-regulation mechanisms and guidelines for this new environment of online coexistence to ensure that user information is safe: the Internet should be a space for freedom, but also for trust. The main way of ensuring that social media are used appropriately is awareness. But awareness and user education will be of little use unless it becomes an absolute requirement that the privacy of the individual is treated as a universal value.
The Internet and Culture
As in the sphere of education, the development of information and communication technologies and the wide-ranging effects of globalization are changing what we are, and the meaning of cultural identity. Ours is a complex world in which cultural flows across borders are always on the rise. The concepts of space, time, and distance are losing their conventional meanings. Cultural globalization is here, and a global movement of cultural processes and initiatives is underway.
Again, in the cultural arena, vast fields of opportunity open up thanks to online tools. The possibilities are multiplied for disseminating a proposal, an item of knowledge, or a work of art. Against those doomsayers who warn that the Internet is harming culture, I am radically optimistic. The Internet is bringing culture closer to more people, making it more easily and quickly accessible; it is also nurturing the rise of new forms of expression for art and the spread of knowledge. Some would say, in fact, that the Internet is not just a technology, but a cultural artifact in its own right.
In addition to its impact on culture itself, the Internet is enormously beneficial for innovation, which brings progress in all fields of endeavor—the creation of new goods, services, and ideas, the advance of knowledge and society, and increasing well-being.
The Internet and Personal Relationships
The Internet has also changed the way we interact with our family, friends, and life partners. Now everyone is connected to everyone else in a simpler, more accessible, and more immediate way; we can conduct part of our personal relationships using our laptops, smart phones, and tablets.
The benefits of always-online immediate availability are highly significant. I would find a long-distance relationship with my life partner or my family unthinkable without the communication tools that the network of networks provides me with. I’m living in Madrid, but I can stay close to my brother in California. For me, that is the key plus of the Internet: keeping in touch with the people who really matter to me.
As we have seen, the Internet revolution is not just technological; it also operates at a personal level, and throughout the structure of society. The Internet makes it possible for an unlimited number of people to communicate with one another freely and easily, in an unrestricted way.
Just a century ago, this was unimaginable. An increasing number of couples come together, stay together, or break up with the aid—or even as a consequence—of social communication tools. There are even apps and social networks out there that are purposely designed to help people get together for sex.
Of course, when compared to face-to-face communication, online communication is severely limited in the sense impressions it can convey (an estimated 60 to 70 percent of human communication takes place nonverbally), which can lead to misunderstandings and embarrassing situations—no doubt quite a few relationships have floundered as a result. I think the key is to be genuine, honest, and real at all times, using all the social media tools and their many advantages. Let’s just remember that a liar and a cheat online is a liar and a cheat offline too.
The Internet and Social and Political Activism
Even before the emergence of social media, pioneering experiments took place in the political sphere—like Essembly , a project I was involved in. We started to create a politically themed platform to encourage debate and provide a home for social and political causes; but the social networks that have later nurtured activism in a new way were not as yet in existence.
Research has shown that young people who voice their political opinions on the Internet are more inclined to take part in public affairs. The better informed a citizen is, the more likely they will step into the polling booth, and the better they will express their political liberties. The Internet has proved to be a decisive communication tool in the latest election campaigns. It is thanks to the Internet that causes in the social, welfare, ideological, and political arenas have been spoken up for and have won the support of other citizens sharing those values—in many cases, with a real impact on government decision making.
The Internet and Consumer Trends
New technologies increase the speed of information transfer, and this opens up the possibility of “bespoke” shopping. The Internet offers an immense wealth of possibilities for buying content, news, and leisure products, and all sorts of advantages arise from e-commerce, which has become a major distribution channel for goods and services. You can book airline tickets, get a T-shirt from Australia, or buy food at an online grocery store. New applications support secure business transactions and create new commercial opportunities.
In this setting, it is the consumer who gains the upper hand, and the conventional rules and methods of distribution and marketing break down. Consumers’ access to information multiplies, and their reviews of their experience with various products and services take center stage. Access to product comparisons and rankings, user reviews and comments, and recommendations from bloggers with large followings have shaped a new scenario for consumer behavior, retail trade, and the economy in general.
The Internet and the Economy
The Internet is one of the key factors driving today’s economy. No one can afford to be left behind. Even in a tough macroeconomic framework, the Internet can foster growth, coupled with enhanced productivity and competitiveness.
The Internet provides opportunities for strengthening the economy: How should we tackle them? While Europe—and Spain specifically—are making efforts to make the best possible use of the Internet, there are areas in which their approach needs to improve. Europe faces a major challenge, and risks serious failure if it lets the United States run ahead on its own. The European Commission, in its “Startup Manifesto,” suggests that the Old World be more entrepreneur-friendly—the proposal is backed by companies like Spotify and Tuenti. Europe lacks some of the necessary know-how. We need to improve in financial services and in data privacy, moving past the obsolete regulatory framework we now have and making a bid to achieve a well-connected continent with a single market for 4G mobile connections. We need to make it easier to hire talent outside each given country.
The use of e-commerce should be encouraged among small and medium-sized enterprises so that growth opportunities can be exploited more intensely. Following the global trend of the Internet, companies should internalize their online business. And much more emphasis should be placed on new technologies training in the academic and business spheres.
Modern life is global, and Spain is competing against every other country in the world. I do not believe in defeatism or victim culture. Optimism should not translate into callousness, but I sincerely believe that if you think creatively, if you find a different angle, if you innovate with a positive attitude and without fear of failure, then you can change things for the better. Spain needs to seize the moment to reinvent itself, grasping the opportunities offered up by the online world. We need to act, take decisions, avoid “paralysis through analysis.” I sometimes feel we are too inclined to navel-gazing: Spain shuts itself off, fascinated with its own contradictions and local issues, and loses its sense of perspective. Spain should open up to the outside, use the crisis as an opportunity to do things differently, in a new way—creating value, underlining its strengths, aspiring to be something more.
In the United States, for instance, diving headfirst into a personal Internet-related startup is regarded as perfectly normal. I’m glad to see that this entrepreneurial spirit is beginning to take hold here as well. I believe in working hard, showing perseverance, keeping your goals in view, surrounding yourself with talent, and taking risks. No risk, no success. We live in an increasingly globalized world: of course you can have a Spain-based Internet startup, there are no frontiers.
We need to take risks and keep one step ahead of the future. It is precisely the most disruptive innovations that require radical changes in approach and product, which might not even find a market yet ready for them—these are the areas providing real opportunities to continue being relevant, to move forward and “earn” the future, creating value and maintaining leadership. It is the disruptive changes that enable a business, product, or service to revolutionize the market—and, particularly in the technology sector, such changes are a necessity.
The Future of Social Communications, Innovation, Mobile Technologies, and Total Connectivity in Our Lives
The future of social communications will be shaped by an always-online culture. Always online is already here and will set the trend going forward. Total connectivity, the Internet you can take with you wherever you go, is growing unstoppably. There is no turning back for global digitalization.
Innovation is the driving force of growth and progress, so we need to shake up entrenched processes, products, services, and industries, so that all of us together—including established businesses, reacting to their emerging competitors—can move forward together.
Innovation is shaping and will continue to shape the future of social communications. It is already a reality that Internet connections are increasingly mobile. A survey we conducted in early 2013 in partnership with Ipsos found that 94 percent of Tuenti users aged 16 to 35 owned cell phones, 84 percent of users connected to the Internet using their phones, and 47 percent had mobile data subscriptions for connecting to the Internet. A total of 74 percent of users reported connecting to the Internet from their phone on a daily basis, while 84 percent did so at least weekly. Only 13 percent did not use their phones to connect to the Internet, and that percentage is decreasing every day.
Mobile Internet use alters the pattern of device usage; the hitherto familiar ways of accessing the Internet are changing too. The smartphone activities taking up the most time (over three hours a day) include instant messaging (38%), social media use (35%), listening to music (24%), and web browsing (20%). The activities taking up the least time (under five minutes a day) are: SMS texting (51%), watching movies (43%), reading and writing e-mail (38%), and talking on the phone (32%). Things are still changing.
Smartphones are gaining ground in everyday life. Many of the purposes formerly served by other items now involve using our smartphones. Some 75 percent of young people reported having replaced their MP3 player with their phone, 74 percent use their phone as an alarm clock, 70 percent use it as their camera, and 67 percent use it as their watch.
We have been observing these shifts for a while, which is why we decided to reinvent ourselves by placing smartphones at the heart of our strategy. I want to use this example as a showcase of what is happening in the world of social communication and the Internet in general: mobile connectivity is bringing about a new revolution. Tuenti is no longer just a social network, and social media as a whole are becoming more than just websites. The new Tuenti provides native mobile apps for Android, iPhone, Blackberry, Windows Phone, as well as the Firefox OS app and the mobile version of the website, m.tuenti.com. Tuenti is now a cross-platform service that lets users connect with their friends and contacts from wherever they may be, using their device of choice. A user with a laptop can IM in real time with a user with a smartphone, and switch from one device to another without losing the thread of the conversation. The conversations are in the cloud, so data and contacts are preserved independently of the devices being used. This means the experience has to be made uniform across platforms, which sometimes involves paring down functionalities, given the processing and screen size limitations of mobile devices. Facebook, Twitter, Instagram, LinkedIn, and so on are all evolving to become increasingly cross-platform experiences. But Tuenti is the first social network that has also developed its own Mobile Virtual Network Operator (MVNO)—the company is an Internet service provider over the mobile network. Tuenti is an MVNO with a social media angle, and this may be the future path of telecommunications.
Social media are evolving to become something more, and innovation must be their hallmark if they are to continue being relevant. Tuenti now embraces both social communications and telecom services provision, offering value added by letting you use the mobile app free of charge and without using up your data traffic allowance, even if you have no credit on your prepaid card—this is wholly revolutionary in the telecom sector. The convergence of social media with more traditional sectors is already bringing about a new context for innovation, a new arena for the development and growth of the Internet.
Just about everything in the world of the Internet still lies ahead of us, and mobile communications as we know them must be reinvented by making them more digital. The future will be shaped by innovation converging with the impact of mobility. This applies not just to social media but to the Internet in general, particularly in the social communications field. I feel that many people do not understand what we are doing and have no idea of the potential development of companies like ours at the global level. Right now, there may be somebody out there, in some corner of the world, developing the tool that will turn the Internet upside down all over again. The tool that will alter our day-to-day life once more. Creating more opportunities, providing new benefits to individuals, bringing more individual and collective well-being. Just ten years ago, social media did not exist; in the next ten years, something else radically new will emerge. There are many areas in which products, processes, and services can be improved or created afresh. The future is brimming with opportunities, and the future of the Internet has only just begun.
Related publications
- The Impact of the Internet on Society: A Global Perspective
- Implications of the Revolution in Work and Family
- Vision 2020+: A Future to Be Built
Download Kindle
Download epub, download pdf, more publications related to this article, more about technology, artificial intelligence, digital world, visionaries, comments on this publication.
Morbi facilisis elit non mi lacinia lacinia. Nunc eleifend aliquet ipsum, nec blandit augue tincidunt nec. Donec scelerisque feugiat lectus nec congue. Quisque tristique tortor vitae turpis euismod, vitae aliquam dolor pretium. Donec luctus posuere ex sit amet scelerisque. Etiam sed neque magna. Mauris non scelerisque lectus. Ut rutrum ex porta, tristique mi vitae, volutpat urna.
Sed in semper tellus, eu efficitur ante. Quisque felis orci, fermentum quis arcu nec, elementum malesuada magna. Nulla vitae finibus ipsum. Aenean vel sapien a magna faucibus tristique ac et ligula. Sed auctor orci metus, vitae egestas libero lacinia quis. Nulla lacus sapien, efficitur mollis nisi tempor, gravida tincidunt sapien. In massa dui, varius vitae iaculis a, dignissim non felis. Ut sagittis pulvinar nisi, at tincidunt metus venenatis a. Ut aliquam scelerisque interdum. Mauris iaculis purus in nulla consequat, sed fermentum sapien condimentum. Aliquam rutrum erat lectus, nec placerat nisl mollis id. Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Nam nisl nisi, efficitur et sem in, molestie vulputate libero. Quisque quis mattis lorem. Nunc quis convallis diam, id tincidunt risus. Donec nisl odio, convallis vel porttitor sit amet, lobortis a ante. Cras dapibus porta nulla, at laoreet quam euismod vitae. Fusce sollicitudin massa magna, eu dignissim magna cursus id. Quisque vel nisl tempus, lobortis nisl a, ornare lacus. Donec ac interdum massa. Curabitur id diam luctus, mollis augue vel, interdum risus. Nam vitae tortor erat. Proin quis tincidunt lorem.
The Way of the Dodo
Do you want to stay up to date with our new publications.
Receive the OpenMind newsletter with all the latest contents published on our website
OpenMind Books
- The Search for Alternatives to Fossil Fuels
- View all books
About OpenMind
Connect with us.
- Keep up to date with our newsletter
Quote this content
- Share full article
Advertisement
Supported by
How a Patriotic Painting Became the Internet’s Soapbox
“Freedom of Speech,” the World War II-era painting by Norman Rockwell, has taken on a new life online.

By Charles W. McFarlane
So you have an opinion you want to share online — something you need to get off your chest. Maybe it’s about the current political climate. Maybe you want to have the final word on whether or not people should wear their shoes in the house.
If you know you have a spicy take on your hands, you might look to the American painter and illustrator Norman Rockwell to help you share it. Across social media, his work “Freedom of Speech” appears alongside all manner of strong opinions, from the highly serious to the absurd to the esoteric, enshrining itself into the lingua franca of the internet decades after its creator’s death.
The oil painting, which shows a man dressed in work wear standing and poised to speak amid a crowd of men in suits, is part of a series by Rockwell inspired by Franklin D. Roosevelt’s 1941 State of the Union address arguing for U.S. involvement in World War II. In his remarks, the president outlined four universal freedoms that Americans should fight to guarantee for all: freedom of speech, freedom of worship, freedom from want and freedom from fear.
According to the internet encyclopedia Know Your Meme , the painting began showing up in posts on X, then Twitter, in 2020. It wasn’t until two years later, though, that it started spreading widely, first with a post by a user who shared the image with an opinion on shrimp-fried rice (“a shrimp did not fry that rice!”).
Since then, the image has been used to take a stance on divisive personal essays , weigh in on Taylor Swift albums , proselytize the merits of hard-shell tacos and decry the state of professional football .
On the day former President Donald J. Trump was found guilty of 34 felony counts in a New York court, Mary Katharine Ham, a Fox News contributor, posted a picture of the painting with the comment, “ jailing your political opponents is bad, actually ” — to which the frequent anti-Trump poster Armand Domalewski replied with the same image and the comment, “ nobody being above the law is good, actually .”
We are having trouble retrieving the article content.
Please enable JavaScript in your browser settings.
Thank you for your patience while we verify access. If you are in Reader mode please exit and log into your Times account, or subscribe for all of The Times.
Thank you for your patience while we verify access.
Already a subscriber? Log in .
Want all of The Times? Subscribe .

- Games & Quizzes
- History & Society
- Science & Tech
- Biographies
- Animals & Nature
- Geography & Travel
- Arts & Culture
- On This Day
- One Good Fact
- New Articles
- Lifestyles & Social Issues
- Philosophy & Religion
- Politics, Law & Government
- World History
- Health & Medicine
- Browse Biographies
- Birds, Reptiles & Other Vertebrates
- Bugs, Mollusks & Other Invertebrates
- Environment
- Fossils & Geologic Time
- Entertainment & Pop Culture
- Sports & Recreation
- Visual Arts
- Demystified
- Image Galleries
- Infographics
- Top Questions
- Britannica Kids
- Saving Earth
- Space Next 50
- Student Center
- Introduction & Top Questions
Early networks
- Foundation of the Internet
- Commercial expansion
- The 21st century and future directions
- Two agendas
- Instant broadcast communication
- Social gaming and social networking
- Love and sex
- Advertising and e-commerce
- File sharing
- Electronic publishing
- Free speech
- Political campaigns and muckraking
- “Getting over it”
- Issues in new media

Who controls the Internet?
Is the internet “making us stupid”, is cancel culture (or “callout culture”) good for society.

Our editors will review what you’ve submitted and determine whether to revise the article.
- CORE - Internet and E-Mail
- Workforce LibreTexts - Reading- The Internet
- Internet Society - About the Internet
- LiveScience - Internet History Timeline: ARPANET to the World Wide Web
- Internet - Children's Encyclopedia (Ages 8-11)
- Internet - Student Encyclopedia (Ages 11 and up)
- Table Of Contents
What is the Internet?
The Internet is a vast network that connects computers all over the world. Through the Internet, people can share information and communicate from anywhere with an Internet connection.
Who invented the Internet?
The Internet consists of technologies developed by different individuals and organizations. Important figures include Robert W. Taylor, who led the development of the ARPANET (an early prototype of the Internet), and Vinton Cerf and Robert Kahn , who developed the Transmission Control Protocol/Internet Protocol (TCP/IP) technologies.
How does the Internet work?
The Internet works through a series of networks that connect devices around the world through telephone lines. Users are provided access to the Internet by Internet service providers . The widespread use of mobile broadband and Wi-Fi in the 21st century has allowed this connection to be wireless.
Is the Internet dangerous?
The advent of the Internet has brought into existence new forms of exploitation, such as spam e-mail and malware , and harmful social behaviour, such as cyberbullying and doxxing. Many companies collect extensive information from users, which some deem a violation of privacy.
What is the Dark Web?
The Dark Web refers to a series of Web sites that require special decryption and configuration tools to access. It is most commonly used for purposes that require strict anonymity, including illegal sales (e.g., of weapons and drugs), political dissent in countries with heavy censorship , and whistleblowing .
While the Internet is theoretically decentralized and thus controlled by no single entity, many argue that tech companies such as Amazon , Facebook , and Google represent a small concentration of organizations that have unprecedented influence over the information and money on the Internet. In some countries, certain parts of the Internet are blocked via censorship .
Whether the Internet is "making us stupid" is widely debated. Some argue the Internet is reprogramming our brains for the worse, as seen by diminishing IQ scores, and that new technologies and platforms like the Internet are harming attention spams, the ability to concentrate, and perform simple tasks. Others argue that virtually all new technologies throughout history have been initially feared, that the Internet gives voice to diverse populations and equal access to information for the benefit of social advancement, and that changing how the brain works and how we access and process information is not necessarily bad. For more on the debate about whether the Internet is "making us stupid," visit ProCon.org .
Whether cancel culture is good for society is widely debated. Some argue it allows the public and marginalized people to seek accountability in their leaders, gives a voice to disenfranchised or less powerful people, and is simply a new form of boycott. Others see cancel culture as a dangerous form of bullying, a suppression of free speech, and a form of intolerance that harms democratic societies by excluding and ostracizing anyone with contrary views. For more on the cancel culture debate, visit ProCon.org .
Recent News
Internet , a system architecture that has revolutionized mass communication , mass media , and commerce by allowing various computer networks around the world to interconnect. Sometimes referred to as a “network of networks,” the Internet emerged in the United States in the 1970s but did not become visible to the general public until the early 1990s. By 2020, approximately 4.5 billion people, or more than half of the world’s population, were estimated to have access to the Internet. And that number is growing, largely due to the prevalence of “smart” technology and the " Internet of Things ," where computer-like devices connect with the Internet or interact via wireless networks . These “things” include smartphones , appliances, thermostats, lighting systems, irrigation systems, security cameras. vehicles, even cities.
The Internet provides a capability so powerful and general that it can be used for almost any purpose that depends on information, and it is accessible by every individual who connects to one of its constituent networks. It supports human communication via social media , electronic mail (e-mail), “chat rooms,” newsgroups, and audio and video transmission and allows people to work collaboratively at many different locations. It supports access to digital information by many applications, including the World Wide Web . The Internet has proved to be a spawning ground for a large and growing number of “e-businesses” (including subsidiaries of traditional “brick-and-mortar” companies) that carry out most of their sales and services over the Internet. ( See electronic commerce .)
Origin and development

The first computer networks were dedicated special-purpose systems such as SABRE (an airline reservation system) and AUTODIN I (a defense command-and-control system), both designed and implemented in the late 1950s and early 1960s. By the early 1960s computer manufacturers had begun to use semiconductor technology in commercial products, and both conventional batch-processing and time-sharing systems were in place in many large, technologically advanced companies. Time-sharing systems allowed a computer’s resources to be shared in rapid succession with multiple users, cycling through the queue of users so quickly that the computer appeared dedicated to each user’s tasks despite the existence of many others accessing the system “simultaneously.” This led to the notion of sharing computer resources (called host computers or simply hosts) over an entire network. Host-to-host interactions were envisioned , along with access to specialized resources (such as supercomputers and mass storage systems) and interactive access by remote users to the computational powers of time-sharing systems located elsewhere. These ideas were first realized in ARPANET , which established the first host-to-host network connection on October 29, 1969. It was created by the Advanced Research Projects Agency (ARPA) of the U.S. Department of Defense . ARPANET was one of the first general-purpose computer networks. It connected time-sharing computers at government-supported research sites, principally universities in the United States , and it soon became a critical piece of infrastructure for the computer science research community in the United States. Tools and applications—such as the simple mail transfer protocol (SMTP, commonly referred to as e-mail), for sending short messages, and the file transfer protocol ( FTP ), for longer transmissions—quickly emerged. In order to achieve cost-effective interactive communications between computers, which typically communicate in short bursts of data, ARPANET employed the new technology of packet switching . Packet switching takes large messages (or chunks of computer data) and breaks them into smaller, manageable pieces (known as packets) that can travel independently over any available circuit to the target destination, where the pieces are reassembled. Thus, unlike traditional voice communications, packet switching does not require a single dedicated circuit between each pair of users.
Commercial packet networks were introduced in the 1970s, but these were designed principally to provide efficient access to remote computers by dedicated terminals. Briefly, they replaced long-distance modem connections by less-expensive “virtual” circuits over packet networks. In the United States, Telenet and Tymnet were two such packet networks. Neither supported host-to-host communications; in the 1970s this was still the province of the research networks, and it would remain so for many years.

DARPA (Defense Advanced Research Projects Agency; formerly ARPA) supported initiatives for ground-based and satellite-based packet networks. The ground-based packet radio system provided mobile access to computing resources, while the packet satellite network connected the United States with several European countries and enabled connections with widely dispersed and remote regions. With the introduction of packet radio, connecting a mobile terminal to a computer network became feasible . However, time-sharing systems were then still too large, unwieldy, and costly to be mobile or even to exist outside a climate-controlled computing environment . A strong motivation thus existed to connect the packet radio network to ARPANET in order to allow mobile users with simple terminals to access the time-sharing systems for which they had authorization. Similarly, the packet satellite network was used by DARPA to link the United States with satellite terminals serving the United Kingdom, Norway, Germany, and Italy. These terminals, however, had to be connected to other networks in European countries in order to reach the end users. Thus arose the need to connect the packet satellite net, as well as the packet radio net, with other networks.
- Investigates
- Houston Life
- Newsletters
WEATHER ALERT
5 warnings in effect for 7 counties in the area
Internet connectivity down across houston area due to hurricane beryl’s impact.
Brittany Taylor , Senior Digital Content Producer
HOUSTON – While many Houston area residents are at home due to Hurricane Beryl, many are having trouble connecting to internet connection or signal on their cellphones.
According to NetBlocks , real-time network data showed the growing impact of Beryl across Texas with connectivity in Houston down to 30% of ordinary levels due to heavy winds and downed powerlines, leaving over 2 million without power and telecoms.
Recommended Videos
⚠️ Update: Real-time network data show the growing impact of Hurricane Beryl across #Texas with connectivity in Houston down to 30% of ordinary levels; the incident is attributed to heavy winds and downed lines leaving over two million without power and telecoms 🌀⚡ pic.twitter.com/ICzi39t4T7 — NetBlocks (@netblocks) July 8, 2024
Internet companies such as AT&T and Xfinity have alert their customers of the power outages causing issues with service and working to fix the disruptions.
CenterPoint Energy confirmed that more than 2.1 million electric customers are without power in the Houston area.
- More than 2 million CenterPoint customers have no electricity | Here’s how you can still watch KPRC 2 News
Comcast is offering free WiFi hotspots in the region due to widespread power outages, which also affects internet service.
You can find a hotspot location map at wifi.xfinity.com or download the Xfinity app from the App Store or Google Play.
AT&T released the following statement:
We continue to monitor Beryl’s path. Strong winds, storm surge, flooding rain and tornadoes continue to impact the greater Houston area and broader Southeast Texas. As the storm clears the area, our teams will begin to safely restore service.
Currently, all of our major network facilities remain online, with some running on backup power. Some of our customers in affected areas may be experiencing service interruptions due to storm damage and commercial power outages.
Our FirstNet liaisons are in contact with federal, state and local officials on our deployment efforts to support public safety and the communities in impacted areas. The FirstNet team continues to support public safety with additional mobile communications equipment on the way to Fort Bend, Harris and Matagorda counties. The FirstNet Response Operations Group (ROG) is prepared to deploy additional dedicated FirstNet assets to further support emergency communications.
- Comcast offers free WiFi hotspots amid power outages across Houston area as Beryl moves through
Copyright 2024 by KPRC Click2Houston - All rights reserved.
About the Author
Brittany taylor.
Award-winning journalist, mother, YouTuber, social media guru, millennial, mentor, storyteller, University of Houston alumna and Houston-native.
20 Internet-Themed Horror Movies That Will Make You Want to Quit Social Media

Your changes have been saved
Email Is sent
Please verify your email address.
You’ve reached your account maximum for followed topics.
Following the success of the webcam horror movie sub-genre, several horror films depicting the dark side of social media began to flood the mainstream. In these disturbing movies, evil exists on the Internet, and characters are haunted by the World Wide Web. The question is, how does one expel an evil that has been invited through technology?
Horror has a way of turning even the most innocent or simple experiences into the most benign ones. However, since the Internet and social media have become such an integral part of modern life, it's only natural for horror filmmakers to use them as a source of terror and entertainment. To deliver the most terrifying techno-horrors, Friend Request , Host , and Selfie from Hell play on newfound fears such as venturing into the forbidden dark web, being stalked online, and the lethal consequences of social media obsession . Fortunately, there's no shortage of films that tackle the Internet and social media in particular, with several tech-related horror movies flying under the radar. These are the best horror movies that will make audiences want to quit social media, ranked by entertainment value.
20 'Assassination Nation' (2018)
Directed by sam levinson.

Directed by Euphoria 's Sam Levinson , Assassination Nation is an action crime comedy with horror elements. The story focuses on four girls who must fight to survive after a data hacker exposes the secrets of the American town of Salem. It stars Odessa Young , Abra , Suki Waterhouse , and Hari Nef .
Assassination Nation 's social satire about our contemporary society, including privacy in the age of social media , is one of its most poignant, stand-out aspects. However, the movie's visual style and engaging plot are also great. It is not as likely to scare audiences considering that its focus is mainly on the social satire aspect of things. However, Levinson's movie is still worthwhile.
*Availability in US
Not available
19 'Selfie from Hell' (2018)
Directed by erdal ceylan.
When an online vlogger from Germany, Julia ( Meelah Adams ), visits her cousin Hannah ( Alyson Walker ) in the U.S. only to become ill. Hannah scours the Internet to find the cause of the strange illness, only to discover an inaccessible site on the dark web. Her seemingly normal home transforms into a haunted house.
Viewers who love horror movies with lots of jumpscares will definitely enjoy this; like many other dark web movies, it offers a glimpse into the terrifying online world. However, the film is a little formulaic, and it is difficult for some viewers to enjoy it thoroughly. Nevertheless, Selfie from Hell does a great job of warning people to stay away from the darkest corners of the Internet , given that bad things are certainly bound to happen when they venture there.
Watch on Tubi
18 'Missing' (2023)
Directed by will merrick and nicholas d. johnson.

Directed by Nicholas D. Johnson and Will Merrick , Missing focuses on a young woman’s ( Euphoria ’s star, Storm Reid , who plays Zendaya 's younger sister in the acclaimed teen show) attempt to find her mother ( Nia Long ) who disappears while on vacation in Colombia and to bring her back home, using the latest technological tools available to her online thousands of miles away in Los Angeles.
Handling topics of family, loss, and regret, Missing is an engaging movie even if not the best in the genre. Its premise is not groundbreaking, but certainly enjoyable. Plus, the way Nicolas D. Johnson and Will Merrick's picture incorporates innovative use of modern technologies in its storytelling is also a strong aspect , becoming a must-see cyber horror/thriller watch.
17 'Profile' (2018)
Directed by timur bekmambetov.

In the mystery thriller/horror film Profile , an undercover British journalist infiltrates the online propaganda channels of the so-called Islamic State, only to be sucked in by her recruiter. The story is based on French journalist Anna Erelle 's book In the Skin of a Jihadist about her investigation into the recruitment of young women by ISIS.
Despite its mixed reviews, the lesser-known Timur Bekmambetov movie is a gripping watch that works as an effective way to keep boredom at bay, and investing enough to keep audiences interested. Although labeled as a horror film, Profile arguably falls under the mystery and thriller genres best, but certainly features some scary moments and horror elements , namely in how it highlights the dangers of the Internet.
Profile (2018)
Watch on Peacock
16 'Megan is Missing' (2011)
Directed by michael goi.

This totally disturbing and obscure film follows 14-year-old Megan ( Rachel Quinn ) and 13-year-old Amy ( Amber Perkins ), two young teens who are kidnapped and consequently tortured after talking with a stranger on the Internet that turned out to be a child predator.
If there is a scarring movie that will likely keep anyone — especially young teens — away from the net, it is probably Michael Goi' s one. Often criticized for its usage of explicit content, Megan is Missing is a horror film that features a lot of gore and unsettling scenes . Ultimately, it sends out thought-provoking messages on the dangers of the Internet world and the cyber predators that inhabit it.
Megan Is Missing
Watch on Hoopla
15 'Feardotcom' (2002)
Directed by william malone.
In this William Malone horror film, detective Mike Reilly ( Stephen Dorff ) collaborates with Department of Health associate Terry Huston ( Natasha McElhone ) in New York City and looks into strange murders that happen 48 hours after visitors register on the website feardotcom.
Although it is far from being among the best horror films out there — rather, it is on the other side of the spectrum, as it was panned by critics and, ultimately, a box-office bomb — Feardotcom is frightening because of its realistic and believable narrative . Even if not expertly executed, this 2002 horror thriller manages to disturb audiences by showcasing the crimes around a deadly website and sending out messages that certainly provide a lot of food for thought.
Watch on Pluto
14 'Friend Request' (2016)
Directed by simon verhoeven.

Friend Request revolves around a popular college student, Laura ( Alycia Debnam-Carey ), who makes the mistake of unfriending a mysterious girl named Marina ( Liesl Ahlers ) and invites a demonic presence into her life. When her friends die mysteriously, a frightened Laura has no choice but to figure out how to fight this evil.
The list of social media horror movies cannot be complete without mentioning Friend Request . The plot may become predictable at some point, since it shares some similarities with iconic and timeless slashers like Friday the 13th . However, this gripping horror movie is more than satisfying to watch. Though it may seem a bit campy with its idea of a Facebook demon, Friend Request does have a lot of fun moments and some blood too .
Friend Request
13 'ratter' (2015), directed by branden kramer.
In this 2015 film, a young graduate student living alone in New York is tormented by a hacker who stalks her through all of her technological devices. When video feeds are not enough, he goes from virtual to a physical stalker.
Ratter manages to induce real-life panic and fear by focusing solely on online prowling. Shot through the lens of a webcam, cellphone, wobble cam, and other devices, this home invasion horror movie is frighteningly realistic. This short cyber horror movie is quite different from movies of its type in that it does not rely on gore or violence to tell the story. It has enough suspense to make it terrifying
Rent on Apple TV
12 'Initiation' (2020)
Directed by john berardo.
John Berardo 's movie illustrates a party that starts innocently but quickly takes a sinister and bloody turn when a star athlete is found impaled in his dorm room. Soon, bodies start turning up on campus as a metal mask-wearing killer picks and kills frat boys and sorority girls.
Initiation crosses slasher-horror and crime thriller tropes to deliver an engaging story. It paves the way for modern-day horror slashers by incorporating new elements such as social media bullying, women's rights, and more. An indie horror flick , Initiation is more than just another horror movie for horror’s sake ; while far from being a groundbreaking horror movie, it takes time to develop characters as well as the storyline, which is what makes it so memorable.
11 'Unfriended: Dark Web' (2017)
Directed by stephen susco.
In Unfriended: Dark Web , a group of friends stumbles upon a laptop that has access to the dark web, where they watch a series of disturbing videos about people who appear to be in danger. Soon after, they receive anonymous messages informing them that they will all die if they disconnect or call the police. The fun night suddenly turns into horrifying as they die one by one while others watch in terror.
The only similarity between this video call horror movie sequel to Unfriended and the first installment of the franchise, is that they are both depicted on laptop screens. Stephen Susco succeeds in creating a cruel and unsettling movie that offers a bleak glance at how terrifying the Internet age can be.
Unfriended 2
10 'like me' (2017), directed by robert mockler.

In the entertaining Like Me , a teenage girl desperate for human connection sets out on a killing spree that she broadcasts on social media. It is safe to say that Robert Mockler is among the most unique and underappreciated horror movies, even though it is also a widely divisive one.
The color-soaked cinematography blended with an outstanding portrayal of characters by the cast and the inventiveness of the kills will surely engender many in this disturbing serial killer tale. Furthermore, Kiya's (Addison Timlin) representation of millennial isolation sheds light on the dark side of trying so hard to be relevant online . The thrilling psychedelic horror film is a must-see for fans of the subgenre.
9 'We're All Going to the World's Fair' (2021)
Directed by jane schoenbrun.

This terrifying Jane Schoenbrun picture sees a teenage girl ( Anna Cobb ) alone in her attic bedroom. When Casey becomes immersed in an online role-playing horror game and participates in a challenge rumored to have transformative effects on participants, she begins to document a series of changes that may or may not be happening to her.
We're All Going to the World's Fair blurs the lines between reality and virtual reality , exploring themes of identity and loneliness and the effects that social media and online culture overall can have on young people who grow up in front of a computer. Even if not traditionally scary, this Schoenbrun picture is indeed unsettling and thought-provoking, partly because it explores existential questions and our relationship with social media through a chilling lens.
We're All Going to the World's Fair
8 'cam' (2018), directed by daniel goldhaber.

In a true social media horror movie (a film that could easily take part in Black Mirror cinematic universe), Alice ( Madeline Brewer ), a cam girl, discovers that a doppelgänger has hijacked her followers, and she must figure out who the double is to regain access to her account.
Aside from giving viewers a glimpse into the world of cam girls, Daniel Goldhaber 's psychological horror film is expertly woven to have a great blend of sci-fi and supernatural. Many fans have compared Cam to Black Swan , but with a cyber twist and cam girls. Cam is pretty creepy and perfectly captures what it's like to be obsessed with achieving status rank online or being obsessed with numbers. Although the film was great, some viewers may find the ending unsatisfying.
7 'Tragedy Girls' (2017)
Directed by tyler macintyre.

Two small-town friends, McKayla Hooper ( Brianna Hildebrand ) and Sadie Cunningham ( Alexandra Shipp ) are obsessed with becoming social media stars and resort to murder to entertain their distraught fans. Fortunately for them, they capture a serial killer Lowell ( Kevin Durand ), and commit several brutal murders for their ominous social media page while pinning them on him.
Tyler MacIntyre presents a slasher genre with a modern twist. Tragedy Girls is as dark as slasher films can get , featuring psychopath killers, gore, killing spree, suspense, and terror. Its satire is an aspect that differs it from traditional slasher films. While some may find this comedy-horror funny, it may put others off since these villains show no remorse for their heinous actions and virtually go unpunished.
Tragedy Girls
6 'the cleansing hour' (2019), directed by damien leveck.

Directed by Damien LeVeck , The Cleansing Hour is a worth-mentioning entry in both the exorcism and Internet subgenres. The film focuses on two entrepreneurs who run a webcast that streams live exorcisms. Although this is just a well-planned money-grabbing scheme featuring staged hoaxes, the film takes a wild turn of events when an actress becomes mysteriously possessed by a real demon that holds the crew hostage.
While this Shudder original movie is hardly a masterpiece, it is a well-executed one nonetheless. The Cleansing Hour seamlessly combines social media elements with the horror genre , ultimately delivering a refreshing and unique premise. It is also fun and surprisingly frightening at times, featuring numerous twists and turns to keep viewers invested. Furthermore, it is considered one of the best Shudder originals.
The Cleansing Hour
5 'spree' (2020), directed by eugene kotlyarenko.

In 2020's Spree , a lonely rideshare driver will stop at nothing to become famous online. He devises a deadly plan to go viral and soon earns himself a reputation as the "Rideshare Killer."
No doubt, Spree is another shocking horror-comedy movie that satirizes the lengths people will go to become famous online and delivers a refreshing take on the similar digital era/reality we're living in. While not at all a scary film, it is an atmospheric only. Plus, it is unsettling to see sweet Joseph David Keery from Stranger Things as a bloodthirsty villain. Nonetheless, his presence in the film is one of the reasons why so many viewers love it.
4 'Hard Candy' (2005)
Directed by david slade.

Hard Candy provides audiences with an intriguing and twisted narrative that follows a young girl ( Elliot Page in one of their earlier roles ) who heads to meet Jeff ( Patrick Wilson ), the photographer she met on the internet, at a coffee shop. While Jeff initially thinks he is in for a real treat, Hayley plays an unexpected trick on him.
What’s so interesting about Hard Candy is the surprising turnaround on its initial sexual predator storyline, which ultimately gives Hayley the power in what could’ve been a terrible scenario. David Slade's intelligent film keeps audiences on the edge of their seats and warns them about the dangers of the Internet through its unconventional and entertaining narrative, with a memorable performance by Page.
Watch on Amazon Prime
3 'Host' (2020)
Directed by rob savage.
In 2020's lean Host — one of the scariest pandemic movies — a group of friends attempt an online séance during their weekly Zoom meeting only to invite a demonic presence into their homes. What happens next turns Host into one of the best webcam horror movies that maximizes the format.
A Zoom-based British horror movie with a well-timed jump scare, pacing that doesn't meander, and superb acting has distinguished it from many other modern horrors. Despite being conceived during the COVID-19 lockdown, Host is among the most compelling internet horror movies, juggling between genuine tension and unsettling scares while every action is played on a Zoom call. Like Unfriended and movies of the like, this desktop horror feature will indeed have many viewers hiding under their blankets — there is no helping it.
2 'Deadstream' (2022)
Directed by vanessa and joseph winter.
In an attempt to win back his followers, a problematic internet personality has a bright idea of live streaming one night alone in a haunted house named Death Manor, where several people have died. However, as audiences would probably guess, things start to go south when he annoys a vengeful spirit.
With a runtime of only 90 minutes, Vanessa Winter and Joseph Winter's low-budget, unpredictable found-footage Deadstream is entertaining and comical . Additionally, the clever way it manages to blend technology with horror elements is one of its strongest aspects, and the unpredictability in the way it scares viewers in one minute and cracks them up in the next is also worth mentioning.
Watch on Shudder
1 'Pulse' (2001)
Directed by kiyoshi kurosawa.

Pulse (translated from Japanese: Kairo ) is perhaps one of the country's most atmospheric horror movies, as well as one of the most recommended. The techno-horror film centers on two groups of people who learn that ghosts might be attempting to infiltrate the world through the Internet.
Among the best horror movies about online interactions, this sinister thriller Pulse is the best out of the bunch , and it does a very good job at depicting the digital horrors of social alienation (with some people even believing that Pulse has predicted recent years of isolation), as well as the withdrawal from relationships. No doubt, the haunting 2001 movie provides food for thought and makes for an intriguing time in front of the screen; this is, of course, especially true if audiences are into Japanese horror features.
Pulse (2001)
NEXT: Terrifying Movies About Rogue Artificial Intelligence
What is Project 2025? The Presidential Transition Project explained.
The detailed plan to dismantle and reconstruct the government laid out by conservative groups known as the 2025 Presidential Transition Project has critics up in arms over its " apocalyptic " and " authoritarian " nature.
The Heritage Foundation, a conservative think tank in Washington, D.C., led an effort to create the more than 900-page "Mandate for Leadership," published in April 2023, reimagining the executive branch and presented a plan to overhaul several federal government agencies, including the FBI, for the country's next conservative president to follow.
More: Project 2025 head says 'second American Revolution' will be 'bloodless if the left allows'
According to the Project's website, the playbook provides a governing agenda and a lineup of people ready to implement it to "rescue the country from the grip of the radical Left." It includes a domestic and foreign policy agenda, a list of personnel, training, and a 180-day playbook.
"It is not enough for conservatives to win elections," Project 2025 said on its website . "With the right conservative policy recommendations and properly vetted and trained personnel to implement them, we will take back our government."
Project 2025's Director is Paul Dans , who served as the U.S. Office of Personnel Management chief of staff in former President Donald Trump's administration. Although it mentions Trump by name, the handbook does not directly assume the Republican party's presumptive nominee will be the one to carry out its agenda.
What is in Project 2025?
The mandate attacks several policies that former President Barack Obama and President Joe Biden instituted, including student loan forgiveness and Obamacare . It simultaneously calls for expanded executive power for the commander-in-chief while criticizing what Project 2025 members perceive as overreaches by the Biden administration.
"Presidents should not issue mask or vaccine mandates, arbitrarily transfer student loan debt, or issue monarchical mandates of any sort," the plan reads. "Legislatures make the laws in a republic, not executives."
The playbook calls for the reinstatement of a Trump executive order augmenting a president's power to hire and fire federal officials by replacing civil servants with political appointees throughout government.
It also seeks to repeal aspects of the Affordable Care Act , urge the Food and Drug Administration to reverse the approval of abortion pills , and further empower Immigration and Customs Enforcement to deport undocumented immigrants .
The plan also specifically addresses LGBTQ+ issues and attacks "radical gender ideology." In addition to calling for an end to the Department of Education, it suggests legislation that would forbid educators from using transgender students' names or pronouns without written permission from their guardians. It also appears to oppose same-sex marriage and gay couples adopting children by seeking to "maintain a biblically based, social science-reinforced definition of marriage and family."
Project 2025 generates concern
Project 2025 has received substantial criticism from Democrats, including Representative Jasmine Crockett , D-Texas, who called out the controversial plan during a congressional hearing last month.
"I don't know why or how anybody can support Project 2025," Crockett said. "In the United States of America, dictatorships are never funny, and Project 2025 is giving the playbook for authoritarianism as well as the next dictator to come in."
Progressive Democrat U.S. Representative Ayanna Pressley of Massachusetts called it a "far-right manifesto" in a post on TikTok . The Biden campaign captioned a video detailing Project 2025, stating it "needs more attention."
Rachel Barber is a 2024 election fellow at USA TODAY, focusing on politics and education. Follow her on X, formerly Twitter, as @rachelbarber_
He’s 11 and makes $100,000 a year riding his bike in the suburbs. Haverford police are not pleased.
Oneway Lilman’s internet-fueled fame has added a modern twist to a classic suburban struggle.
/cloudfront-us-east-1.images.arcpublishing.com/pmn/P6EOW7YDQVHYVDXESHFRQJTWJ4.jpg)
As soon as sixth grade is out, Alex Santacroce drops his black Air Jordan backpack in the house, grabs a banana (good for hand cramps) from the kitchen, and mounts his custom-built SE Savage Flyer bike. He can appear almost solemn as he coasts down the driveway, front wheel aloft, gently shifting his body to keep the handlebars straight. Riding is absolutely mind-clearing for him. He says sometimes he’ll try a trick 1,000 times before it’s perfect.
To some residents and the Haverford police, Santacroce, 11, is the neighborhood’s primary menace. It is not only that he and his siblings zoom around Marilyn Park on bicycles and electric bikes, practicing daredevil tricks in public places and annoying the grown-ups who live nearby.
It is also that under the professional moniker Oneway Lilman, Santacroce has successfully monetized being a kid doing crazy feats on your bike and annoying your neighbors. He has 1.4 million followers on YouTube and earned roughly $100,000 last year through sponsorships and advertising, according to his parents. Often he rides around in a Louis Vuitton half-shell helmet emblazoned with his name; packages of free gear from sneaker and apparel companies pile up at home.
Lilman’s internet-fueled fame has added a modern twist to the classic suburban struggle over common space and how kids ought to behave. In private Facebook groups, some neighbors have referred to the family as “classless” and wondered whether the children riding bikes in the street are “feral.” The family has repeatedly ended up in court; Alexander Santacroce, Lilman’s father, pleaded guilty in 2021 to “allowing a child to illegally operate a bicycle.”
Haverford Township Police Chief John Viola declined to comment for this article, saying, “We would prefer not to give this family any more press coverage.”
The situation has recently been escalating. In response to the latest round of police involvement, Santacroce planted a sign in his front yard that said “My Neighbor is a Karen,” which Philadelphia Magazine first reported.
On a recent afternoon, Lilman and his siblings practiced riding electric bikes up a small ramp at the foot of the driveway. All four bike, and all, except the 5-year-old, post content online, though Lilman’s career has taken off most prominently. “Cause Dad pays the most attention to him,” 14-year-old Alexa muttered in explanation. (Her mother disagreed.)
The grass was patchy in places because of the nonstop tires.
“I tried to explain this is what my kids do. You know, this is his job,” said Michelle Santacroce, Lilman’s mother. “I’m never going to stop my kids from doing something they love.”
‘A sponsor’s dream’
Four-foot-nine with a smattering of freckles, Alex “Lilman” Santacroce is a true disciple of “bike life” — the practice of popping wheelies and performing stunts on bicycles, sometimes while weaving through traffic on crowded city streets.
“It takes pain away,” he explained. “You’re not thinking about anything except you on the bike.”
Like any aspiring kid-biker-influencer, Lilman studied bike life icons on YouTube and Instagram to learn their tricks, and with his dad’s help, he started posting his own footage online. For his 8th birthday, his parents organized a “rideout,” where local kids gathered to do stunts on their bikes at Haverford Middle School. Some older kids joined and began swerving in traffic, Michelle said, but overall it was an idyllic day. After the ride, the Santacroces served cake to friends and strangers in their backyard.
Looking back now, that was a turning point.
“I think once we did that, we were kind of labeled as a problem. As if we had bad intent doing that,” Michelle said.
At the same time, Lilman’s devotion was starting to pay off. When he was 9, the BMX company SE invited him to join an elite nationwide crew of 15 riders as an officially sponsored biker. Like the older influencers he idolized, he would now have a monthly salary, a steady stream of free, expensive SE bikes, and the opportunity to travel the world on all-expenses-paid bike trips.
In a video SE posted on their website, 9-year-old Lilman, with a buzz cut and euphoric grin, accepted the invitation to join the team, tears sliding down his cheeks.
“He’s just a really popular, nice kid and he’s good on the bike. He’s a sponsor’s dream,” Todd Lyons, director of SE Bikes, said in a phone conversation.
So Lilman was a third grader with a job: to create content on a bike.
It was a new world for his parents. Though they both grew up biking in West Philly , Alexander works as a plumber, and Michelle works as a paralegal.
They also manage their child’s booming online brand, while navigating the sometimes challenging underbelly of online fame. This year Lilman has been consistently taunted by older kids in school, Michelle said.
In Havertown , some residents became increasingly frustrated and worried about kids doing stunts in the street. The family lives in an upscale neighborhood of large houses and cul-de-sacs that abuts the Merion Golf Club.
“I was just on Garlor [Drive] and witnessed something disturbing,” one resident wrote in a neighborhood Facebook group in March 2021. “A bunch of kids (preteens/teens) doing wheelies... on their bikes AS CARS ARE SHARING THAT EXACT STRETCH OF ROAD... Someone WILL lose control of those bikes on one back wheel at some point and some poor driver is going to have that guilt upon them when one of those kids hits their car and is injured or worse.”
The Santacroces said the post was not referring to their children. Police got involved the next month, when Alexander Santacroce received a citation for “allowing a child to illegally operate a bicycle.” He said it stemmed from then-12-year-old Alexa standing up on the seat of her bike, a trick called surfing. Pennsylvania bike law states that “a person operating a bicycle shall not ride other than astride a permanent and regular seat attached thereto.”
» READ MORE: Philly’s ‘bike life’ community knows their negative reputation. They say people have it all wrong
Bike life has its roots in low-income communities of color that have few recreation facilities, according to scholars, and in Philly and across the country, it has long bedeviled police and some residents who see it as a dangerous nuisance. Philadelphia Mayor Cherelle L. Parker has made cracking down on illegal ATV and dirt bike riders a key priority, seeing it as a quality-of-life issue.
In the suburbs, Santacroce pleaded guilty, the kids kept biking, and Lilman continued to grow online.
‘This is why you wear a helmet’
For the most part, Lilman’s YouTube videos are not slickly produced or edited, instead offering meandering documentation of his life. In one of his most popular videos , he’s seat-belted in the back of the family car, next to his two younger siblings.
“What is up, YouTube?” he says. “So I’m about to ask my mom, can I go to the bank, get some money out, some YouTube money out, and buy a 150 today?”
The video then pans to his younger sister, who chatters briefly and unrelatedly about swimming in the family pool. After Michelle says yes to Lilman’s request to buy a dirt bike, “only cause it’s your birthday,” the family visits Citizens Bank and Lilman withdraws $3,800 in cash while his dad films. To fans, his life is an example of potential unlocked.
“Any thing is possible who cares if someone disagrees with your vision, keep grinding,” a commenter wrote.
View this post on Instagram A post shared by 🐐💎Lilman💎🐐 (@oneway_lilman)
The annoyance of the neighbors has only fueled Lilman’s content creation. In a recent reel posted to his Instagram account, which his dad manages, Lilman pops a wheelie on a pedal bike down a carless street during golden hour. The front wheel rolls away mid-ride, and a woman walking in the street says, “That’s dangerous when people are walking.” The post, captioned “We Found KAREN😭,” generated tens of thousands of likes and dozens of gleeful anti-Karen comments.
The appearance of danger and breaking the rules is sometimes good for the brand, Santacroce said. But of course, there is real danger as well. Alexa got in a serious accident in the fall, hitting a raised drainage sewer while zipping downhill. She flipped over her handlebars and face-planted before her bike crashed on top of her. She broke her leg and two bones in her foot, and ultimately required a bone graft and reconstructive surgery this spring to repair it.
The kids have braved smaller injuries, too. In a YouTube video titled “ Bike Life Rideout Gone Wrong. Lil Bro Gets Staples!! ,” Santacroce documents the aftermath of a crash involving Lilman’s brother, Dante, who is 9. At the end of a rideout, another biker crashed into him, and the handlebars of the bike collided with his head.
“This is why you wear a helmet, guys,” Santacroce said, zooming in on a small bloody gash on his son’s head. The family proceeded to an urgent care clinic.
“You probably don’t get many people YouTubing while you’re in here, right?” Santacroce asked from behind the camera, as a health-care worker stapled Dante’s cut closed.
To both Alexa and Lilman, such injuries are simply part of bike life, which has brought them pure joy often enough that the injuries feel worth it.
“When you’re riding a bike, the first thing you’re worried about when you fall is your bike,” Lilman said.
“Yeah, like when I crashed, it was like, ‘But what about my bike? Is my bike alright?’” Alexa said. “When can I ride my bike?”
Another citation
In April, police mailed another citation to the Santacroce home, this one for “driving an unregistered vehicle.” The police citation noted a red electric-powered bike called a Razor Dirt Rocket . The Santacroces say the vehicle in question, which they said the police examined carefully in a visit to their home, does not require registration. Afterward, Santacroce planted the “My Neighbor is a Karen” flag, and Michelle began getting calls from friends and coworkers: I heard there was a police raid on your street.
She was upset by what seemed to her an outsize, un-neighborly reaction.
“My husband does all their plumbing up there,” she said, gesturing to the part of the neighborhood where she guessed the police calls came from.
Haverford police told Philly Mag they have responded to at least six incidents involving Oneway Lilman specifically, and that while they did not mind kids riding bikes in the neighborhood, they were troubled by the safety aspect.
“What I’m actually concerned about is having to show up at somebody’s house to tell them that their kid got killed while doing stupid things on a bike,” Joe Hagan, Haverford deputy chief of police, told Philly Mag. “We take it seriously because of that. And because the people who move here do so because they want to live in a quiet neighborhood.”
For now, the Santacroce kids are largely limited to the yard and driveway — unless they are filming YouTube content, for which they go to the neighborhood roads with a parent. Alexa has half a mind to go to the police station and try to hash out the problem herself.
“We won’t ride reckless. We will listen to whatever you guys tell us,” she said. “We just want to be able to feel the freedom and enjoyment again.”
Correction: An earlier version of this story incorrectly named the school where Alex ‘Lilman’ Santacroce and his friends gathered on his 8th birthday. It was Haverford Middle School, not Havertown Middle School.
- Choose your language...
- English (English)
- Spanish (Español)
- French (Français)
- German (Deutsch)
- Italian (Italiano)
- Portuguese (Português)
- Japanese (日本語)
- Chinese (中文)
- Korean (한국어)
- Taiwan (繁體中文)
- Organization Size
- Hybrid Cloud
- Zero Trust & Least Privilege
- Developer Security & Operations
- IoT Security Solutions
- Anti-Ransomware

See how use cases come to life through Check Point's customer stories.
- Financial Services
- Federal Government
- State & Local Government
- Telco Service Provider
- Small & Medium Business
- Infinity Platform
- Secure the Network
- Secure the Cloud
- Secure the Workspace
- Security Operations and AI
- Platform Overview
- Infinity Core Services
- Infinity Portal Access Infinity Portal
- Infinity Platform Agreement Predictable cyber-security environments through a platform agreement

AI-Powered Threat Prevention
- Next Generation Firewall (NGFW) Security Gateway Industry-leading AI powered security gateways for modern enterprises
- SD-WAN Software Defined Wide Area networks converging security with networking
- Security Policy and Threat Management Manage firewall and security policy on a unified platform for on-premises and cloud networks
- Operational Technology and Internet of Things (IoT) Autonomous IoT/OT threat prevention with zero-trust profiling, virtual patching and segmentation
- Remote Access VPN Secure, seamless remote access to corporate networks
- Cloud Network Security Industry-leading threat prevention through cloud-native firewalls
- Cloud Native Application Protection Platform Cloud native prevention first security
- Code Security Developer centric code security
- Web Application and API Security Automated application and API security
- Email and Collaboration Security Email security including office & collaboration apps
- Endpoint Security Comprehensive endpoint protection to prevent attacks & data compromise
- Mobile Security Complete protection for the mobile workforce across all mobile devices
- SASE Unifying security with optimized internet and network connectivity
- Managed Prevention & Response Service SOC operations as a service with Infinty MDR/MPR
- Extended Prevention & Response AI-Powered, Cloud-Delivered Security Operations with Infinity XDR/XPR
- Secure Automation and Collaboration Automate response playbooks with Infinity Playblocks
- Unified Security Events and Logs as a Service Infinity Events cloud-based analysis, monitoring and reporting
- AI Powered Teammate Automated Security Admin & Incident Response with AI Copilot
- ThreatCloud AI The Brain behind Check Point’s threat prevention
- Cyber Security Risk Assessment Assess cyber security maturity and plan actionable goals
- Penetration Testing Evaluate security defenses against potential cyber attacks and threats
- Security Controls Gap Analysis (NIST CIST) Analyze technology gaps and plan solutions for improved security and ROI
- Threat Intelligence Analyzed data on cyber threats, aiding proactive security measures
- See All Infinity Global Services >

Learn hackers inside secrets and beat them at their own game
- Security Deployment & Optimization Strategic deployment and refinement of security for optimal protection
- Advanced Technical Account Management Proactive service delivered by highly skilled Cyber Security professionals
- Lifecycle Management Services Effectively maintain the lifecycle of security products and services
- Certifications & Accreditations Comprehensive cyber security training and certification programs
- CISO Training Globally recognized training for Chief Information Security Officers
- Security Awareness Empower employees with cyber security skills for work and home
- Cyber Range Simulated gamification environment for security training
- Mind Check Point Cyber Security and Awareness Programs training hub
- Incident Response Manage and mitigate security incidents with systematic response services
- Managed Detection and Response Prioritize prevention, delivering comprehensive SOC operations as a service
- Digital Forensics Comprehensive investigation and analysis of cyber incidents and attacks
- MXDR with Managed SIEM
- Managed Firewalls
- EDR with Agent Management
- Managed CNAPP
- Managed CSPM
- Support Programs Programs designed to help maximize security technology utilization
- Check Point PRO Proactive monitoring of infrastructure program offerings
- Contact Support
- Infinity Portal
- Infinity Platform Agreement
- Next Generation Firewall (NGFW) Security Gateway
- Security Policy and Threat Management
- Operational Technology and Internet of Things (IoT)
- Remote Access VPN
- Cloud Network Security
- Cloud Native Application Protection Platform
- Code Security
- Web Application and API Security
- Email and Collaboration Security
- Endpoint Security
- Mobile Security
- Managed Prevention & Response Service
- Extended Prevention & Response
- Secure Automation and Collaboration
- Unified Security Events and Logs as a Service
- AI Powered Teammate
- ThreatCloud AI
- Cyber Security Risk Assessment
- Penetration Testing
- Security Controls Gap Analysis (NIST CIST)
- Threat Intelligence
- Security Deployment & Optimization
- Advanced Technical Account Management
- Lifecycle Management Services
- Certifications & Accreditations
- CISO Training
- Security Awareness
- Cyber Range
- Incident Response
- Managed Detection and Response
- Digital Forensics
- Support Programs
- Check Point PRO
- Find a Partner
- Channel Partners
- Technology Partners
- MSSP Partners
- Azure Cloud
- Partner Portal

Check Point is 100% Channel. Grow Your Business with Us!
- Investor Relations
- Resource Center
- Customer Stories
- Events & Webinars
- Check Point Research
- Cyber Talk for Executives
- CheckMates Community

CPR Warns Threat Actors are Leveraging Internet Explorer in New Zero-Day Spoofing Attack (CVE-2024-38112)

Check Point Research (CPR) warns of a new spoofing attack from threat actors using Internet Explorer shortcut files to lure Windows 10/11 users for remote code execution. CPR recommends Microsoft customers patch immediately .
Key Findings
- Threat actors are luring Windows 10/11 users into enabling remote code execution and accessing their computers
- This vulnerability has been used in the wild for over one year, potentially impacting millions of users
- CPR disclosed the vulnerability to Microsoft in May 2024; Microsoft published patches on 9 July 2024
- CPR recommends users regularly patch and update all software to ensure greatest protection against cyber threats
- Check Point released the following protections on IPS and Harmony Email, IPS signature named “Internet Shortcut File Remote Code Execution” for customers months ahead of this publication, to protect against this zero-day attack.
- Harmony Email and Collaboration provides comprehensive inline protection against this zero-day attack at the highest security level.
Check Point Research recently discovered that threat actors have been using novel (or previously unknown) tricks to lure Windows users into enabling remote code execution.
Specifically, the attackers used special Windows Internet Shortcut files (.url extension name), which, when clicked, would call the retired Internet Explorer (IE) to visit the attacker-controlled URL. An additional trick on IE was used to hide the malicious “.hta” extension name. By opening the URL with IE instead of the modern and much more secure Chrome/Edge browser on Windows, the attacker gained significant advantages in exploiting the victim’s computer, although the computer is running the modern Windows 10/11 operating system.
Note, it’s not uncommon for threat actors to use .url files as an initial attack vector in their campaigns. Even using novel or zero-day url-file-related vulnerabilities has happened before— CVE-2023-36025 , which was just patched last November, is a good example.
The malicious .url samples discovered by CPR could be dated back as early as January 2023 to May 13, 2024 and beyond. This suggests that threat actors have been using the attacking techniques for quite some time.
For the full analysis of this attack, visit the CPR blog .
Defense and Mitigation
These exploitation tricks – which have been actively used in the wild for at least one year, work on the latest Windows 10/11 operating systems.
Check Point released the following protections on IPS and Harmony Email months ago to ensure customers remain protected: IPS signature named “Internet Shortcut File Remote Code Execution.” Windows users should immediately install the Microsoft patch .
Additionally, Harmony Email and Collaboration provides comprehensive inline protection against this zero-day attack at the highest security level.
Conclusion
CPR recommends Windows users remain vigilant about .url files sent from untrusted sources. This tricky attack enables attackers to leverage IE (instead of the more secure Chrome/Edge browsers). It works in two ways
- The “mhtml” trick which allows the attacker to call (or resurrect) the IE browser
- Tricks the user into opening what they think is a PDF but is actually a dangerous .hta application
Check Point Research continues to monitor the activities related to this type of attack around the globe.
You may also like

June 2024’s Most Wanted Malware: RansomHub Takes Top Spot as Most Prevalent Ransomware Group in Wake of LockBit3 Decline
Cve-2024-6387 – regresshion remote code execution vulnerability seen in openssh.

Amazon Prime Day 2024: Cyber criminals Are Ready – Are You?

DeepBrand Clustering – an Evolution in Brand Spoofing Prevention
To revisit this article, visit My Profile, then View saved stories .
Bella Hadid Wears the Naked Dress to End All Naked Dresses

Anthony Vaccarello finally figured out how to reproduce his collection of ultra-sheer pantyhose dresses. Bella Hadid hit Cannes in look seven from the Saint Laurent fall 2024 show: a halter dress featuring 10 denier hosiery cups, a knotted pantyhose bodice, and a below-the-knee skirt with a control top hemline.

Hadid, styled by Molly Dickson, leaned into the Old Hollywood glamour that has become synonymous with the Cannes Film Festival, adding a pair of mahogany peep-toe ankle strap heels and an enormous pair of drop earrings from Chopard.

This look fits into Hadid’s latest sartorial M.O. of sheer earthy tones that can only be described as “sexy nymph.” While promoting her fragrance, Orebella, in New York, the model wore a diaphanous nude Dior slip dress by John Galliano, as well as a cream-colored Rokh dress with a lace bodice. And yesterday in Cannes, she further explored brown tones in a simple tank dress . But this look—with only some extremely well-placed seams preserving her modesty—is by far her boldest to date.

When asked about how he would manufacture these ephemeral pieces from the collection, Vaccarello told Vogue, “Don’t even ask me about production—I can’t tell you.” This being the first instance the delicate outfits have been spotted on the red carpet speaks to Hadid’s risk-taking style. Even if she is the only person who ever wears one of these sheer Saint Laurent looks out in the world (let’s see if she can make it to the end of the night without any snags) the fact that Vaccarello was readily willing to make one for her speaks to Hadid’s immense power in the fashion industry.
And if this is Hadid’s wardrobe for her first official day of events in Cannes? We can only imagine what’s to come.
More Great Fashion Stories from Vogue
Lily Collins Has Found a French-Girl Alternative to the Adidas Samba
Meghan Markle’s New Look Is Taking Shape for Spring
Angelina Jolie Will Wear This Pair of Shoes Anywhere—Even a Shopping Run
Katie Holmes’s Baggy Slip Dress Is a Lazy Girl’s Shortcut to Cool
Goodbye, Manolos! Sarah Jessica Parker’s Unlikely Summer Shoe Is a Clog
Rihanna Gives a ’90s Coat a Totally 2024 Feel
Sign up for Vogue Shopping to receive the insider’s guide to what to shop and how to wear it
Listen to The Run-Through with Vogue , a weekly podcast featuring the most exciting stories and hot takes from the worlds of culture, politics, sports and–of course–fashion
Never miss a Vogue moment and get unlimited digital access for just $2 $1 per month.

Vogue Daily
By signing up you agree to our User Agreement (including the class action waiver and arbitration provisions ), our Privacy Policy & Cookie Statement and to receive marketing and account-related emails from Vogue. You can unsubscribe at any time. This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IMAGES
VIDEO
COMMENTS
t. e. The history of the Internet has its origin in the efforts of scientists and engineers to build and interconnect computer networks. The Internet Protocol Suite, the set of rules used to communicate between networks and devices on the Internet, arose from research and development in the United States and involved international collaboration ...
Berners-Lee was born in London on 8 June 1955, [24] the son of mathematicians and computer scientists Mary Lee Woods (1924-2017) and Conway Berners-Lee (1921-2019). His parents were both from Birmingham and worked on the Ferranti Mark 1, the first commercially-built computer. His paternal grandmother was a Canadian woman from Winnipeg. [25]
Tim Berners-Lee (born June 8, 1955, London, England) is a British computer scientist, generally credited as the inventor of the World Wide Web. In 2004, he was awarded a knighthood by Queen Elizabeth II of the United Kingdom and the inaugural Millennium Technology Prize (€1 million) by the Finnish Technology Award Foundation.
Before the current iteration of the Internet, long-distance networking between computers was first accomplished in a 1969 experiment by two research teams at UCLA and Stanford. Though the system crashed during the initial attempt to log in to the neighboring computer, the researchers, led by Leonard Kleinrock, succeeded in creating the first ...
1990: Tim Berners-Lee invented the World Wide Web. Hence, the Internet's roots are in the 1960s when computer scientists began exploring the potential of linking computers together to share data and resources. This period was crucial for laying the groundwork for communication networks that could span the globe.
The Internet got its start in the United States more than 50 years ago as a government weapon in the Cold War. Unlike technologies such as the light bulb or the telephone, the Internet has no ...
Father of the Internet Tim Berners-Lee. Tim Berners-Lee was the man leading the development of the World Wide Web (with help of course), the defining of HTML (hypertext markup language) used to create web pages, HTTP (HyperText Transfer Protocol), and URLs (Universal Resource Locators). All of those developments took place between 1989 and 1991.
In this paper, 3 several of us involved in the development and evolution of the Internet share our views of its origins and history. This history revolves around four distinct aspects. There is the technological evolution that began with early research on packet switching and the ARPANET (and related technologies), and where current research continues to expand the horizons of the ...
Vinton Cerf (born June 23, 1943, New Haven, Connecticut, U.S.) is an American computer scientist who is considered one of the founders, along with Robert Kahn, of the Internet.In 2004 both Cerf and Kahn won the A.M. Turing Award, the highest honour in computer science, for their "pioneering work on internetworking, including the design and implementation of the Internet's basic ...
From Wikipedia, the free encyclopedia. The history of the Internet has its origin in the efforts of scientists and engineers to build and interconnect computer networks. The Internet Protocol Suite, the set of rules used to communicate between networks and devices on the Internet, arose from research and development in the United States and ...
The history of the Internet is a story of contributions by men and women such as J.C.R. Linklider, Leonard Kleinrock, Vint Cerf, Elizabeth (Jake) Feinler, Tim Berners-Lee, Bob Kahn, and so many others. It's also the story of previously (and perhaps hereafter) unknown collaborations between government agencies, academia, and corporations.
1972: BBN's Ray Tomlinson introduces network email. The Internet Working Group (INWG) forms to address need for establishing standard protocols. 1973: Global networking becomes a reality as the ...
The terms 'World Wide Web' and 'internet' are often confused. The internet is the networking infrastructure that connects devices together, while the World Wide Web is a way of accessing information through the medium of the internet. Tim Berners-Lee first proposed the idea of a 'web of information' in 1989.
The Internet (or internet) [a] is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) [b] to communicate between networks and devices. It is a network of networks that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of ...
The internet is a giant computer network, linking billions of machines together by underground and underwater fibre-optic cables.These cables run connect continents and islands, everywhere except ...
Personal History/Biography: the Birth of the Internet. It all began with a comic book! At the age of 6, Leonard Kleinrock was reading a Superman comic at his apartment in Manhattan, when, in the centerfold, he found plans for building a crystal radio. To do so, he needed his father's used razor blade, a piece of pencil lead, an empty toilet ...
Philip Emeagwali (born August 23, 1954) is a Nigerian American computer scientist. He achieved computing breakthroughs that helped lead to the development of the internet. His work with simultaneous calculations on connected microprocessors earned him a Gordon Bell Prize, considered the Nobel Prize of computing.
From its humble California origins to the dotcom bust to its transformation of the way we live, the Internet is the world's most powerful creation. This is the definitive story of how the web connected billions of people around the globe told through those who know it best: the Internet's pioneers, tech entrepreneurs, and viral stars who have defined 50 years of life online.
The Internet has turned our existence upside down. It has revolutionized communications, to the extent that it is now our preferred medium of everyday communication. In almost everything we do, we use the Internet. Ordering a pizza, buying a television, sharing a moment with a friend, sending a picture over instant messaging.
The Internet's Soap Box: "Freedom of Speech," the World War II-era painting by Norman Rockwell, has taken on a new life online. The Delightful Delusions of Marc Jacobs: ...
Internet, a system architecture that has revolutionized mass communication, mass media, and commerce by allowing various computer networks around the world to interconnect. Sometimes referred to as a "network of networks," the Internet emerged in the United States in the 1970s but did not become visible to the general public until the early ...
⚠️ Update: Real-time network data show the growing impact of Hurricane Beryl across #Texas with connectivity in Houston down to 30% of ordinary levels; the incident is attributed to heavy ...
Vint Cerf (⫽ s ɜːr f ⫽; born 1943) is an American Internet pioneer and is recognized as one of "the fathers of the Internet", sharing this title with TCP/IP co-developer Bob Kahn.. He has received honorary degrees and awards that include the National Medal of Technology, the Turing Award, the Presidential Medal of Freedom, the Marconi Prize, and membership in the National Academy of ...
When an online vlogger from Germany, Julia (Meelah Adams), visits her cousin Hannah (Alyson Walker) in the U.S. only to become ill.Hannah scours the Internet to find the cause of the strange ...
"I don't know why or how anybody can support Project 2025," Crockett said. "In the United States of America, dictatorships are never funny, and Project 2025 is giving the playbook for ...
The MCC will serve as a connectivity resource for those who have lost power and need connection to the internet. You can charge your device or use one of the 16 computers. The MCC will be at the Deputy Almendarez Center located at 10918 Bentley Street, Houston, TX 77093 from 8:00 a.m. to 8:00 p.m. CT beginning tomorrow, July 10. ...
Oneway Lilman's Internet-fueled fame has added a modern twist to a classic suburban struggle. ... Alex "Lilman" Santacroce is a true disciple of "bike life" — the practice of popping wheelies and performing stunts on bicycles, sometimes while weaving through traffic on crowded city streets.
RENO, NV - U.S. Senator Jacky Rosen (D-NV) hosted a roundtable discussion with U.S. Secretary of Commerce Gina Raimondo and several community leaders in Reno to highlight efforts to improve and expand broadband access across Nevada.They were joined by representatives from Zayo, a company that specializes in communications infrastructure and that will build more than 800 miles of fiber ...
Specifically, the attackers used special Windows Internet Shortcut files (.url extension name), which, when clicked, would call the retired Internet Explorer (IE) to visit the attacker-controlled URL. An additional trick on IE was used to hide the malicious ".hta" extension name. By opening the URL with IE instead of the modern and much ...
The Saint Laurent dress—with only some extremely well-placed seams preserving her modesty—is by far Bella Hadid's boldest to date.