
- Games & Quizzes
- History & Society
- Science & Tech
- Biographies
- Animals & Nature
- Geography & Travel
- Arts & Culture
- On This Day
- One Good Fact
- New Articles
- Lifestyles & Social Issues
- Philosophy & Religion
- Politics, Law & Government
- World History
- Health & Medicine
- Browse Biographies
- Birds, Reptiles & Other Vertebrates
- Bugs, Mollusks & Other Invertebrates
- Environment
- Fossils & Geologic Time
- Entertainment & Pop Culture
- Sports & Recreation
- Visual Arts
- Demystified
- Image Galleries
- Infographics
- Top Questions
- Britannica Kids
- Saving Earth
- Space Next 50
- Student Center
- Introduction

Defining cybercrime
- Identity theft and invasion of privacy
- Internet fraud
- File sharing and piracy
- Counterfeiting and forgery
- Child pornography
- Computer viruses
- Denial of service attacks
- Spam, steganography, and e-mail hacking

Our editors will review what you’ve submitted and determine whether to revise the article.
- College of DuPage Digital Press - Computers and Criminal Justice - Introduction to Cybercrime
- Academia - Cyber Crimes: An Overview
- Table Of Contents
Recent News
cybercrime , the use of a computer as an instrument to further illegal ends, such as committing fraud , trafficking in child pornography and intellectual property, stealing identities , or violating privacy. Cybercrime, especially through the Internet , has grown in importance as the computer has become central to commerce, entertainment, and government.
Because of the early and widespread adoption of computers and the Internet in the United States , most of the earliest victims and villains of cybercrime were Americans. By the 21st century, though, hardly a hamlet remained anywhere in the world that had not been touched by cybercrime of one sort or another.
New technologies create new criminal opportunities but few new types of crime. What distinguishes cybercrime from traditional criminal activity? Obviously, one difference is the use of the digital computer , but technology alone is insufficient for any distinction that might exist between different realms of criminal activity. Criminals do not need a computer to commit fraud, traffic in child pornography and intellectual property, steal an identity, or violate someone’s privacy. All those activities existed before the “cyber” prefix became ubiquitous . Cybercrime, especially involving the Internet, represents an extension of existing criminal behaviour alongside some novel illegal activities.
Most cybercrime is an attack on information about individuals, corporations, or governments. Although the attacks do not take place on a physical body, they do take place on the personal or corporate virtual body, which is the set of informational attributes that define people and institutions on the Internet. In other words, in the digital age our virtual identities are essential elements of everyday life: we are a bundle of numbers and identifiers in multiple computer databases owned by governments and corporations. Cybercrime highlights the centrality of networked computers in our lives, as well as the fragility of such seemingly solid facts as individual identity.
An important aspect of cybercrime is its nonlocal character: actions can occur in jurisdictions separated by vast distances. This poses severe problems for law enforcement since previously local or even national crimes now require international cooperation. For example, if a person accesses child pornography located on a computer in a country that does not ban child pornography, is that individual committing a crime in a nation where such materials are illegal? Where exactly does cybercrime take place? Cyberspace is simply a richer version of the space where a telephone conversation takes place, somewhere between the two people having the conversation. As a planet-spanning network, the Internet offers criminals multiple hiding places in the real world as well as in the network itself. However, just as individuals walking on the ground leave marks that a skilled tracker can follow, cybercriminals leave clues as to their identity and location, despite their best efforts to cover their tracks. In order to follow such clues across national boundaries, though, international cybercrime treaties must be ratified.
In 1996 the Council of Europe , together with government representatives from the United States, Canada, and Japan, drafted a preliminary international treaty covering computer crime. Around the world, civil libertarian groups immediately protested provisions in the treaty requiring Internet service providers (ISPs) to store information on their customers’ transactions and to turn this information over on demand. Work on the treaty proceeded nevertheless, and on November 23, 2001, the Council of Europe Convention on Cybercrime was signed by 30 states. The convention came into effect in 2004. Additional protocols , covering terrorist activities and racist and xenophobic cybercrimes, were proposed in 2002 and came into effect in 2006. In addition, various national laws, such as the USA PATRIOT Act of 2001, have expanded law enforcement’s power to monitor and protect computer networks .
Types of cybercrime
Cybercrime ranges across a spectrum of activities. At one end are crimes that involve fundamental breaches of personal or corporate privacy, such as assaults on the integrity of information held in digital depositories and the use of illegally obtained digital information to harass, harm, or blackmail a firm or individual. These new cybercapabilities have caused intense debate. Pegasus spyware, for instance, according to its creator, the Israeli cyber-intelligence firm NSO Group, is sold exclusively to government security and law enforcement agencies and only for the purpose of aiding rescue operations and battling criminals, such as money launderers , sex- and drug-traffickers, and terrorists. Yet, the smartphone-attached spyware, which can steal private data without leaving an obvious trace of its activities, has been widely used covertly by governments to track politicians, government leaders, human rights activists, dissidents , and journalists. It was even used to track Saudi journalist and U.S. resident Jamal Khashoggi months before his murder and dismemberment by Saudi agents in October 2018. Also at this end of the spectrum is the growing crime of identity theft .
Midway along the spectrum lie transaction-based crimes such as fraud , trafficking in child pornography , digital piracy , money laundering , and counterfeiting . These are specific crimes with specific victims, but the criminal hides in the relative anonymity provided by the Internet . Another part of this type of crime involves individuals within corporations or government bureaucracies deliberately altering data for either profit or political objectives. At the other end of the spectrum are those crimes that involve attempts to disrupt the actual workings of the Internet. These range from spam , hacking, and denial of service attacks against specific sites to acts of cyberterrorism—that is, the use of the Internet to cause public disturbances and even death. Cyberterrorism focuses upon the use of the Internet by nonstate actors to affect a nation’s economic and technological infrastructure . Since the September 11 attacks of 2001, public awareness of the threat of cyberterrorism has grown dramatically.
- CBSE Class 10th
- CBSE Class 12th
- UP Board 10th
- UP Board 12th
- Bihar Board 10th
- Bihar Board 12th
- Top Schools in India
- Top Schools in Delhi
- Top Schools in Mumbai
- Top Schools in Chennai
- Top Schools in Hyderabad
- Top Schools in Kolkata
- Top Schools in Pune
- Top Schools in Bangalore
Products & Resources
- JEE Main Knockout April
- Free Sample Papers
- Free Ebooks
- NCERT Notes
- NCERT Syllabus
- NCERT Books
- RD Sharma Solutions
- Navodaya Vidyalaya Admission 2024-25
- NCERT Solutions
- NCERT Solutions for Class 12
- NCERT Solutions for Class 11
- NCERT solutions for Class 10
- NCERT solutions for Class 9
- NCERT solutions for Class 8
- NCERT Solutions for Class 7
- JEE Main 2024
- MHT CET 2024
- JEE Advanced 2024
- BITSAT 2024
- View All Engineering Exams
- Colleges Accepting B.Tech Applications
- Top Engineering Colleges in India
- Engineering Colleges in India
- Engineering Colleges in Tamil Nadu
- Engineering Colleges Accepting JEE Main
- Top IITs in India
- Top NITs in India
- Top IIITs in India
- JEE Main College Predictor
- JEE Main Rank Predictor
- MHT CET College Predictor
- AP EAMCET College Predictor
- GATE College Predictor
- KCET College Predictor
- JEE Advanced College Predictor
- View All College Predictors
- JEE Advanced Cutoff
- JEE Main Cutoff
- MHT CET Result 2024
- JEE Advanced Result
- Download E-Books and Sample Papers
- Compare Colleges
- B.Tech College Applications
- AP EAMCET Result 2024
- MAH MBA CET Exam
- View All Management Exams
Colleges & Courses
- MBA College Admissions
- MBA Colleges in India
- Top IIMs Colleges in India
- Top Online MBA Colleges in India
- MBA Colleges Accepting XAT Score
- BBA Colleges in India
- XAT College Predictor 2024
- SNAP College Predictor
- NMAT College Predictor
- MAT College Predictor 2024
- CMAT College Predictor 2024
- CAT Percentile Predictor 2024
- CAT 2024 College Predictor
- Top MBA Entrance Exams 2024
- AP ICET Counselling 2024
- GD Topics for MBA
- CAT Exam Date 2024
- Download Helpful Ebooks
- List of Popular Branches
- QnA - Get answers to your doubts
- IIM Fees Structure
- AIIMS Nursing
- Top Medical Colleges in India
- Top Medical Colleges in India accepting NEET Score
- Medical Colleges accepting NEET
- List of Medical Colleges in India
- List of AIIMS Colleges In India
- Medical Colleges in Maharashtra
- Medical Colleges in India Accepting NEET PG
- NEET College Predictor
- NEET PG College Predictor
- NEET MDS College Predictor
- NEET Rank Predictor
- DNB PDCET College Predictor
- NEET Result 2024
- NEET Asnwer Key 2024
- NEET Cut off
- NEET Online Preparation
- Download Helpful E-books
- Colleges Accepting Admissions
- Top Law Colleges in India
- Law College Accepting CLAT Score
- List of Law Colleges in India
- Top Law Colleges in Delhi
- Top NLUs Colleges in India
- Top Law Colleges in Chandigarh
- Top Law Collages in Lucknow
Predictors & E-Books
- CLAT College Predictor
- MHCET Law ( 5 Year L.L.B) College Predictor
- AILET College Predictor
- Sample Papers
- Compare Law Collages
- Careers360 Youtube Channel
- CLAT Syllabus 2025
- CLAT Previous Year Question Paper
- NID DAT Exam
- Pearl Academy Exam
Predictors & Articles
- NIFT College Predictor
- UCEED College Predictor
- NID DAT College Predictor
- NID DAT Syllabus 2025
- NID DAT 2025
- Design Colleges in India
- Top NIFT Colleges in India
- Fashion Design Colleges in India
- Top Interior Design Colleges in India
- Top Graphic Designing Colleges in India
- Fashion Design Colleges in Delhi
- Fashion Design Colleges in Mumbai
- Top Interior Design Colleges in Bangalore
- NIFT Result 2024
- NIFT Fees Structure
- NIFT Syllabus 2025
- Free Design E-books
- List of Branches
- Careers360 Youtube channel
- IPU CET BJMC
- JMI Mass Communication Entrance Exam
- IIMC Entrance Exam
- Media & Journalism colleges in Delhi
- Media & Journalism colleges in Bangalore
- Media & Journalism colleges in Mumbai
- List of Media & Journalism Colleges in India
- CA Intermediate
- CA Foundation
- CS Executive
- CS Professional
- Difference between CA and CS
- Difference between CA and CMA
- CA Full form
- CMA Full form
- CS Full form
- CA Salary In India
Top Courses & Careers
- Bachelor of Commerce (B.Com)
- Master of Commerce (M.Com)
- Company Secretary
- Cost Accountant
- Charted Accountant
- Credit Manager
- Financial Advisor
- Top Commerce Colleges in India
- Top Government Commerce Colleges in India
- Top Private Commerce Colleges in India
- Top M.Com Colleges in Mumbai
- Top B.Com Colleges in India
- IT Colleges in Tamil Nadu
- IT Colleges in Uttar Pradesh
- MCA Colleges in India
- BCA Colleges in India
Quick Links
- Information Technology Courses
- Programming Courses
- Web Development Courses
- Data Analytics Courses
- Big Data Analytics Courses
- RUHS Pharmacy Admission Test
- Top Pharmacy Colleges in India
- Pharmacy Colleges in Pune
- Pharmacy Colleges in Mumbai
- Colleges Accepting GPAT Score
- Pharmacy Colleges in Lucknow
- List of Pharmacy Colleges in Nagpur
- GPAT Result
- GPAT 2024 Admit Card
- GPAT Question Papers
- NCHMCT JEE 2024
- Mah BHMCT CET
- Top Hotel Management Colleges in Delhi
- Top Hotel Management Colleges in Hyderabad
- Top Hotel Management Colleges in Mumbai
- Top Hotel Management Colleges in Tamil Nadu
- Top Hotel Management Colleges in Maharashtra
- B.Sc Hotel Management
- Hotel Management
- Diploma in Hotel Management and Catering Technology
Diploma Colleges
- Top Diploma Colleges in Maharashtra
- UPSC IAS 2024
- SSC CGL 2024
- IBPS RRB 2024
- Previous Year Sample Papers
- Free Competition E-books
- Sarkari Result
- QnA- Get your doubts answered
- UPSC Previous Year Sample Papers
- CTET Previous Year Sample Papers
- SBI Clerk Previous Year Sample Papers
- NDA Previous Year Sample Papers
Upcoming Events
- NDA Application Form 2024
- UPSC IAS Application Form 2024
- CDS Application Form 2024
- CTET Admit card 2024
- HP TET Result 2023
- SSC GD Constable Admit Card 2024
- UPTET Notification 2024
- SBI Clerk Result 2024
Other Exams
- SSC CHSL 2024
- UP PCS 2024
- UGC NET 2024
- RRB NTPC 2024
- IBPS PO 2024
- IBPS Clerk 2024
- IBPS SO 2024
- Top University in USA
- Top University in Canada
- Top University in Ireland
- Top Universities in UK
- Top Universities in Australia
- Best MBA Colleges in Abroad
- Business Management Studies Colleges
Top Countries
- Study in USA
- Study in UK
- Study in Canada
- Study in Australia
- Study in Ireland
- Study in Germany
- Study in China
- Study in Europe
Student Visas
- Student Visa Canada
- Student Visa UK
- Student Visa USA
- Student Visa Australia
- Student Visa Germany
- Student Visa New Zealand
- Student Visa Ireland
- CUET PG 2024
- IGNOU B.Ed Admission 2024
- DU Admission 2024
- UP B.Ed JEE 2024
- LPU NEST 2024
- IIT JAM 2024
- IGNOU Online Admission 2024
- Universities in India
- Top Universities in India 2024
- Top Colleges in India
- Top Universities in Uttar Pradesh 2024
- Top Universities in Bihar
- Top Universities in Madhya Pradesh 2024
- Top Universities in Tamil Nadu 2024
- Central Universities in India
- CUET DU Cut off 2024
- IGNOU Date Sheet
- CUET DU CSAS Portal 2024
- CUET Response Sheet 2024
- CUET Result 2024
- CUET Participating Universities 2024
- CUET Previous Year Question Paper
- CUET Syllabus 2024 for Science Students
- E-Books and Sample Papers
- CUET Exam Pattern 2024
- CUET Exam Date 2024
- CUET Cut Off 2024
- CUET Exam Analysis 2024
- IGNOU Exam Form 2024
- CUET PG Counselling 2024
- CUET Answer Key 2024
Engineering Preparation
- Knockout JEE Main 2024
- Test Series JEE Main 2024
- JEE Main 2024 Rank Booster
Medical Preparation
- Knockout NEET 2024
- Test Series NEET 2024
- Rank Booster NEET 2024
Online Courses
- JEE Main One Month Course
- NEET One Month Course
- IBSAT Free Mock Tests
- IIT JEE Foundation Course
- Knockout BITSAT 2024
- Career Guidance Tool
Top Streams
- IT & Software Certification Courses
- Engineering and Architecture Certification Courses
- Programming And Development Certification Courses
- Business and Management Certification Courses
- Marketing Certification Courses
- Health and Fitness Certification Courses
- Design Certification Courses
Specializations
- Digital Marketing Certification Courses
- Cyber Security Certification Courses
- Artificial Intelligence Certification Courses
- Business Analytics Certification Courses
- Data Science Certification Courses
- Cloud Computing Certification Courses
- Machine Learning Certification Courses
- View All Certification Courses
- UG Degree Courses
- PG Degree Courses
- Short Term Courses
- Free Courses
- Online Degrees and Diplomas
- Compare Courses
Top Providers
- Coursera Courses
- Udemy Courses
- Edx Courses
- Swayam Courses
- upGrad Courses
- Simplilearn Courses
- Great Learning Courses
Cyber Crime Essay
The unlawful act of gaining unauthorised access to computer systems or digital devices is known as cybercrime. A detailed grasp of how to stop or recover from cyberattacks is provided by cyber security. Online courses offer guidance on how to avoid, safeguard against, and recover from cybercrime risks. Here are a few sample essays on the topic ‘Cyber Crime’.
100 Words Essay on Cyber Crime
200 words essay on cyber crime, 500 words essay on cyber crime.

Cybercrime is the most discussed problem in the twenty-first century. The usage of cellphones and the internet is increasing dramatically over the world, which is generating questions about consumers' security and privacy. Because of this, it is crucial for all users to understand cybercrime and security. Cybercrime is defined as organised criminal conduct carried out by attackers online. Cybercrime comes in numerous forms, such as fraud, computer viruses, cyberstalking, and others. Due to these, businesses and government organisations are spending more on maintaining and employing professionals in cybercrime.
There are millions and billions of users and websites in the vast community known as cyberspace. People utilise it for a variety of activities including e-commerce, transactions, shopping, movies, music, and video games. Anyone can simply access anything online in the current technological era owing to accessible internet connection. As a result, crime in general and cybercrime in particular have surged dramatically. Additionally, the faster internet connection has greatly boosted the rate of data circulation. All of these problems are responsible as to why cyber security has grown to be a significant issue for society.
The government has created a number of cybercrime-related laws in an effort to curb the spread of the crime and to protect people's interests. These laws also provide defence against cybercrime. Aside from that, the government has established cyber cells in police stations to combat cybercrime as quickly as possible.
Cybercrime is an attack that can be harmful to both an individual and a business. There have been several instances where a cyber attack led to a data leak that caused a significant loss for a business or a person. These cyber-attacks could have negative effects on the country and the business. The countless instances of cyberattacks that have taken place in India and other nations have necessitated increased security measures. There are four main categories of cybercrime, according to a popular definition—hacking, money, privacy, and cyber terrorism.
Cybercrime is a type of crime in which illegal activities are carried out online or using computers. Cybercrime comes in a variety of forms which involves harassing online users. Cybercrime is the most serious and rapidly expanding type of crime in this day and age. Any person's life may be negatively impacted for a very long time by becoming a cyber victim. Cybercrimes have a wide range of repercussions on financial and investment activity in digital organisations.
One typical tactic used by criminals is to lure online users in by creating attractive websites and sending phoney emails purporting to be from banks or other organisations and asking for personal information. It makes it easier for criminals to access a person's bank account and personal data. Due to viruses, mail fraud, account hacking, and software piracy, people have been victims of cybercrimes. They also run into problems with unauthorised access mailing, threats from pornographic emails, and video transmission.
Types of Cyber Crime
Cyberstalking | It is the use of electronic communication to track down a person or to make repeated attempts to get in touch with them in order to foster personal interaction despite their blatant lack of interest. Anyone who monitors the internet, email, or any other form of electronic communication is guilty of stalking.
Phishing | It is a sort of fraud that includes collecting personal data from recipients of emails that seem to be coming from a reliable source, including Customer ID, IPIN, Credit/Debit Card number, Card expiration date, CVV number, etc.
Vishing | It is an attempt when criminals attempt to obtain personal information over the phone, such as Customer ID, Net Banking password, ATM PIN, OTP, Card expiration date, CVV, etc.
Smishing | It is a sort of fraud that employs text messages sent to mobile devices to entice victims into dialling a fake phone number, going to a fake website, or downloading harmful software.
Impersonation And Identity Theft | This includes the dishonest or fraudulent use of another person's electronic signature, password, or other distinctive identification trait.
Virus, Worms, Trojan | A computer virus is a programme designed to infiltrate your computer, corrupt your files and data, and spread itself. Worms are malicious software applications that repeatedly duplicate themselves on local drives, network shares, etc. Trojan is a malicious programme that mimics a legitimate application. Trojans offer unauthorised people and applications access to your computer through a backdoor entry, allowing them to steal sensitive data.
How to Prevent Cyber Crime
Backup every piece of information—data, systems, and considerations—to make it easier for businesses to recover from unforeseen events with the help of prior data.
Pick a firewall that offers protection from viruses, malware, and dishonest hackers.
Never divulge private information to a stranger since they might exploit it for fraud.
To avoid cybercrime, check your security settings—in order to determine if someone has logged into your computer, a cyber firewall analyses your network settings.
Antivirus software aids in identifying potential threats and malware before they infect a computer system. Never use software that has been cracked since it poses a serious risk of data loss or malware attack.
Keep your information protected when accessing untrusted websites—information can readily bypass the data through phishing websites.
Applications for Admissions are open.

Aakash iACST Scholarship Test 2024
Get up to 90% scholarship on NEET, JEE & Foundation courses

JEE Main Important Physics formulas
As per latest 2024 syllabus. Physics formulas, equations, & laws of class 11 & 12th chapters

PW JEE Coaching
Enrol in PW Vidyapeeth center for JEE coaching

JEE Main Important Chemistry formulas
As per latest 2024 syllabus. Chemistry formulas, equations, & laws of class 11 & 12th chapters

TOEFL ® Registrations 2024
Accepted by more than 11,000 universities in over 150 countries worldwide

PTE Exam 2024 Registrations
Register now for PTE & Save 5% on English Proficiency Tests with ApplyShop Gift Cards
Download Careers360 App's
Regular exam updates, QnA, Predictors, College Applications & E-books now on your Mobile
Certifications
We Appeared in
Talk to our experts
1800-120-456-456
- Cyber Crime Essay

Essay on Cyber Crime
Cyber crime is the most discussed issue of the 21st century. The technology sector world wide is witnessing a boom in the consumer of smartphones and the internet which is raising concerns with regard to the privacy and security of the users. Owing to this reason, it is highly essential for all the users to know about cyber crime & security. As a result, thi topic has become the most favorite topic of the examiner and can often be seen asked in the exams. In this view, students must have information on cyber crime and stay prepared to tackle such topics in the essay question in the English paper.
Introduction
Cybercrime is a dangerous attack a company or an individual may face. There are many cases where the cyber attack has brought massive loss to the company and individuals due to the data hack. We live in a technology-driven era, and every piece of information is now fed on computers. Cybercrime involves an attack on computers and digital devices. These cyber-attacks can prove hazardous not just for the organization, but also for the nation. To date, there are many digital attack cases in India and global, pushing for more security measures. These attacks are also affecting the economy of the country if not controlled in the initial stage.
What is Cybercrime?
Cybercrime or attack is defined as the systematic criminal activity occurring digitally
and done by attackers. There are many examples of cybercrime, including fraud,
malware viruses, cyberstalking and others. Due to these, government agencies and
companies are investing more in the maintenance and hiring of cybercrime experts.
Earlier, cybercrime was committed only by individuals or by small groups. However, now a highly complex cybercriminals network work on attacking the system for data
collection.
Three groups of cybercrimes-
This is the form of cyberstalking, trafficking, and grooming. Over the years, this
This type of cybercrime has been taken seriously by law enforcement agencies. It is
now keeping a track over every such attack on an individual.
Similar to the real world where criminals steal the property, in the cyber world,
attackers steal data. Here, the attacker steals a person's bank details and
misuse the credit card for online purchase. By using malicious software, the
attacker attacks the property to disrupt the system of the organization.
These types of crimes are denoted as cyber terrorism. This can be a terror because
the attacker can get hold of essential documents related to government
projects. An enemy nation or terrorist usually makes such attacks. There are
many cases globally where a terrorist hacks government data.
Apart from these, there is a financial crime where the hacker steals the money of the
user account holder. Moreover, they steal company data and finance.
In this type, the computer system of the person is hacked to get personal
information. In many countries, including India, hacking is a punishable act.
It is quite different from ethical hacking. In normal hacking, illegal use
different types of software to enter the system of the target person. Hacker is
then able to monitor every activity done by the person.
This Cybercrime is about violating copyright and downloading music or movies. In
India, many movies before their releases are leaked on the movie download
sites. In other words , theft is also called privacy, which can bring a huge
loss to the organization.
Cyber Stalking
It is online harassment by an individual or a group of people. Normally, these
stalkers target an individual and harass online. There are many cases of
cyberstalking in India, resulting in the target person ending up taking
Malicious Software
These are computer-based cybercrimes where virus-based software is installed in the
target people or organization computers. This is to damage the system and
corrupt the data of the target.
Laws Related to Cybercrime
In India, there are many cybercrime laws enacted to stop this threat. Be it for
the individual or the organization; these laws help to either bring down the
number of cases or eliminate these digital crimes.
Apart from these laws, as an individual, you also need to take steps to stop these
crimes. Like, not providing your login details, installing trust anti-virus
software and keeping your online profile private can help to act against such
Cybercrime is a significant threat that can bring huge loss to the individual and the
organization. It is essential to follow basic online rules to ensure the safety
of self and the organization.
Benefits of Cyber Crime Essay in English provided by Vedantu
The essay on cybercrime provided by Vedantu is prepared by highly qualified teachers which makes it a reliable source of information. This information could be utilized for a variety of reasons. Being a reliable piece of information the essay will benefit everyone curious to know about the topic.
Following are the highlights of its benefits:
Reliable information
Adaptive to the context
Precise language
Fulfills the requirements of the students for english exam questions
Comprehensive and analytical. The article digs in the depth of the issue and analyzes it through a 360 degree perspective.
The essay could also be used by the students for preparing themselves for the essay question in the English paper. This essay is an excellent guide to understand what the examiner is looking for in the exam. Moreover, the topic of cybercrime is quite a recurrent one in the exam. So the students use this essay to deal with the same topic.
The Essay on Cyber Crime is an excellent guide on averting any possibilities of a cyber attack. On today's date, one is mostly on the internet for a variety of reasons. It becomes essential for one to know important tips that can keep one safe from cyberbullies, thieves, or blackmailers. It is also important for one to understand the right course of actions to be taken in an eventuality of such an incident.
Download the cybercrime essay for students in English on the Vedantu website.

FAQs on Cyber Crime Essay
1. How Does Cybercrime Work?
Group of people or an individual commits most of these cyber-crimes. These criminals use a systematic process to hack and commit these acts. These criminal communities share strategies and tools to launch attacks. Some of the cybercrime techniques
Fast Flux - In this method, the hacker moves data quickly among computers in a botnet, making it challenging to find the right source.
Social Engineering - This method includes using lies and manipulation to trick people into revealing their personal information.
Skimmers - This involves installing a skimming tool in an ATM and stealing the information. You may find such skimming devices in ATMs.
There are some digital criminals targeting organizations to steal personal information.
2. How Cybercrime Affects Society?
Cybercrime can hugely affect society. In 2018, the US faced a loss of $600 billion. As consumers are increasingly allowing technologies to get into their lives, cyber attackers are getting better access. Some of the essential information available are-
Personal health data, sleep schedules, and geo-locations Shopping history, account information, and passive conversations noticed voice-controlled devices, Private conversations on social media accounts.
Your entire life is now available on social media, making it vulnerable to hack or cyber-attack. Attackers use different techniques including- installing malware, virus, phishing, cyberstalking, etc. These can certainly bring loss of lives and data for individuals and organizations. For society, this is a significant loss in the long run. One needs to be very careful when presenting himself socially.
3. How to stay secure in times of cybercrime?
Cybercrime is a real threat posing to society. It is the 21st-century version of theft and blackmailing. There are certain ways one should adopt to prevent any possibilities of cybercrime. Do not disclose the banking details to random people or fill the CVV of your debit or credit cards on an unknown and unverified website. Keep your passwords always discrete. The camera of the laptop should always be covered.
4. Where can I get a cybercrime essay?
One can find a good quality cyber crime essay on Vedantu's website. The essay which is prepared by the expert teachers describes everything that one needs to know about cybercrime. It is the one-stop solution for all your requirements on the topic. Their essay is available in PDF format on the website and could be downloaded on any device. One downloaded essay could be used in offline mode too. If one finds it feasible, the printout of the PDF could also be taken out.

45,000+ students realised their study abroad dream with us. Take the first step today
Meet top uk universities from the comfort of your home, here’s your new year gift, one app for all your, study abroad needs, start your journey, track your progress, grow with the community and so much more.

Verification Code
An OTP has been sent to your registered mobile no. Please verify

Thanks for your comment !
Our team will review it before it's shown to our readers.

- School Education /
✍️Essay on Cybercrime: Free Samples in 100, 200, 300 Words

- Updated on
- Apr 26, 2024

The 21st century is a digital age, where any and every task is done on the internet. All thanks to the developments in technology which have been the main factor to ease human life on earth and maybe on other plants in future. But with the benefits of technology, there are several harmful effects, one of them which has recently gained popularity; Cyber Crime.

Cybercrime has emerged as pervasive and evolved as one of the most dangerous threats to humans. There are several users on the internet who indulge in illegal and criminal activities, using computers and networks. To guide you through this hot debate topic, below we have discussed essays on cybercrime.
Table of Contents
- 1 Essay on Cybercrime in 100 Words
- 2 Essay on Cybercrime in 200 Words
- 3 Essay on Cybercrime in 300 Words
- 4 Short Essay on Cybercrime
Also Read: Essay on Student Life
Essay on Cybercrime in 100 Words
Cybercrime involves illegal activities like hacking, ransomware, cyberbullying, online fraud, etc. People who are involved in cybercrime or any similar activities are called hackers, scammers or fraudsters. Cybercrime leads to financial loss for individuals who have fallen victim to one. Cybercrime often invades a person’s privacy by stealing their personal details, including sensitive data, photos, and communication records, which can be used for blackmailing or any malicious purpose.
There are several governmental and non-government organizations which are working
To tackle cybercrime by raising awareness among the masses, cyber security training, implementing robust security protocols, and enacting comprehensive cybercrime laws.
Also Read: I Love My India Essay: 100 and 500+ Words in English for School Students
Essay on Cybercrime in 200 Words
Cybercrime is a criminal activity done online using a computer, network and internet. With the increasing use of the internet and mobile phones, the number of criminal activities has also gained pace. These criminal-minded people steal the personal details of a person, which leads to financial losses and damages the reputation of the victims. Various scams and fraudulent schemes are offered on the internet like online auctions, advance fees, or any investment scam, which are all aimed at deceiving individuals into parting with their money.
Cybercrime is not limited to financial losses or reputational damage, a more discrete term has emerged; cyberbullying. In cyberbullying, a person is harassed, humiliated, or threatened online. This can have severe psychological and emotional consequences. Ethical hackers or white hat hackers can help organizations identify vulnerabilities in their systems before malicious hackers exploit them.
Cybercrime doesn’t have any boundaries and is an international issue and international cooperation is crucial for tracking and prosecuting cybercriminals who operate across borders. To combat cybercrime effectively, a multi-faceted approach is required, involving education, technology, legislation, and international cooperation. As technology continues to advance, our efforts to combat cybercrime must keep pace to protect our increasingly interconnected world.
Also Read : Essay on Winter Season
Essay on Cybercrime in 300 Words
Economists have termed cybercrime as ‘ A Hidden Threat to the Digital World.’ Modern humans are relying on the internet for their day-to-day activities and every macro and micro activity. In this sense, the term cybercrime comes to the front. Cybercrime refers to criminal activities conducted through the use of computers, networks, and the Internet.
Cybercrime consists of various malicious activities like hacking, phishing, ransomware attacks, identity theft, online fraud, and cyberbullying. Hackers, fraudsters, scammers, criminals, and even state-sponsored actors exploit vulnerabilities in digital systems to steal sensitive information, disrupt operations, and cause financial and emotional harm to victims.
The consequences of cybercrime are far-reaching. Financial losses run into 10 digits annually, affecting individuals and organizations alike. Personal privacy is invaded as cybercriminals steal sensitive data, photos, and communication records. In cases of cyberbullying and harassment, victims suffer reputational damages, psychological distress, and emotional trauma, particularly in cases of cyberbullying and harassment.
It’s necessary to look for a multifaceted approach to deal with cybercrime, some of which are.
- Raising public awareness through campaigns where people are informed about the risks of cybercrime and educate them on best practices for online safety.
- Individuals and organizations should implement robust security protocols, regularly update software, and use multi-factor authentication to protect their digital assets.
- Governments should enact and enforce cybercrime laws, providing law enforcement agencies with the resources and expertise needed to prosecute cybercriminals effectively.
- Looking at the global nature of cybercrime, international collaboration is vital. Countries should work together to share threat intelligence and cooperate in the investigation and prosecution of cybercriminals.
- Ethical hackers can help organizations identify and rectify vulnerabilities in their systems before malicious actors exploit them.
Tackling cybercrime requires proactive measures, including education, strong cybersecurity practices, legislation, international cooperation, and the active involvement of ethical hackers.
Also Read: Essay on Green Energy PDF: 150 and 250 Words
Short Essay on Cybercrime
Find the short essay on cyber crime from below:
Cybercrime is an illegal and unethical activity which is done by hackers and fraudsters to gain financial or any other benefits for themselves.
To tackle cybercrime, several measures can be taken. Some of these measures are education and public awareness, research and innovation, ethical hacking, etc.
To write an essay on cybercrime, you need to give details on how it works and the level of danger it poses to humans. Cybercrime consists of various malicious activities like hacking, phishing, ransomware attacks, identity theft, online fraud, and cyberbullying. Hackers, fraudsters, scammers, criminals, and even state-sponsored actors exploit vulnerabilities in digital systems to steal sensitive information, disrupt operations, and cause financial and emotional harm to victims.
Related Articles
For more information about such informative articles, visit our essay writing page and make sure to follow Leverage Edu .
Shiva Tyagi
With an experience of over a year, I've developed a passion for writing blogs on wide range of topics. I am mostly inspired from topics related to social and environmental fields, where you come up with a positive outcome.
Leave a Reply Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Contact no. *

Connect With Us
45,000+ students realised their study abroad dream with us. take the first step today..

Resend OTP in

Need help with?
Study abroad.
UK, Canada, US & More
IELTS, GRE, GMAT & More
Scholarship, Loans & Forex
Country Preference
New Zealand
Which English test are you planning to take?
Which academic test are you planning to take.
Not Sure yet
When are you planning to take the exam?
Already booked my exam slot
Within 2 Months
Want to learn about the test
Which Degree do you wish to pursue?
When do you want to start studying abroad.
January 2024
September 2024
What is your budget to study abroad?

How would you describe this article ?
Please rate this article
We would like to hear more.
Have something on your mind?

Make your study abroad dream a reality in January 2022 with
India's Biggest Virtual University Fair

Essex Direct Admission Day
Why attend .

Don't Miss Out
- Threats and vulnerabilities
- Michael Cobb
What is cybercrime?
Cybercrime is any criminal activity that involves a computer, network or networked device.
While most cybercriminals use cybercrimes to generate a profit, some cybercrimes are carried out against computers or devices to directly damage or disable them. Others use computers or networks to spread malware , illegal information, images or other materials. Some cybercrimes do both -- i.e., target computers to infect them with a computer virus, which is then spread to other machines and, sometimes, entire networks.
A primary effect of cybercrime is financial. Cybercrime can include many different types of profit-driven criminal activity, including ransomware attacks, email and internet fraud, and identity fraud, as well as attempts to steal financial account, credit card or other payment card information.
As cybercriminals might target an individual's private information or corporate data for theft and resale, it's especially important to protect backup data .
The U.S. Department of Justice (DOJ) divides cybercrime into the following three categories:
- Crimes in which the computing device is the target -- for example, to gain network access.
- Crimes in which the computer is used as a weapon -- for example, to launch a denial-of-service ( DoS ) attack.
- Crimes in which the computer is used as an accessory to a crime -- for example, using a computer to store illegally obtained data.
The Council of Europe Convention on Cybercrime, to which the U.S. is a signatory, defines cybercrime as a wide range of malicious activities, including the illegal interception of data, system interferences that compromise network integrity, and availability and copyright infringements.
The necessity of internet connectivity has enabled an increase in the volume and pace of cybercrime activities because criminals no longer need to be physically present when committing a crime. The internet's speed, convenience, anonymity and lack of borders make computer-based variations of financial crimes -- such as ransomware, fraud and money laundering, as well as crimes such as stalking and bullying -- easier to carry out.
Cybercriminal activity can be carried out by individuals or groups with relatively little technical skill or by highly organized global criminal groups that could include skilled developers and others with relevant expertise. To further reduce the chances of detection and prosecution, cybercriminals often choose to operate in countries with weak or nonexistent cybercrime laws.
How cybercrime works
Cybercrime attacks can begin wherever there is digital data, opportunity and motive. Cybercriminals include everyone from the lone user engaged in cyberbullying to state-sponsored actors, such as China's intelligence services.
Cybercrimes generally do not occur in a vacuum; they are, in many ways, distributed in nature. That is, cybercriminals typically rely on other actors to complete the crime. This is whether it's the creator of malware using the dark web to sell code, the distributor of illegal pharmaceuticals using cryptocurrency brokers to hold virtual money in escrow or state threat actors relying on technology subcontractors to steal intellectual property.
Cybercriminals use various attack vectors to carry out cyberattacks and are constantly seeking new methods and techniques to achieve their goals, while avoiding detection and arrest.
Cybercriminals often conduct activities using malware and other types of software, but social engineering is usually an important component of executing most types of cybercrime. Phishing emails are another important component to many types of cybercrime but especially for targeted attacks, such as business email compromise , in which an attacker attempts to impersonate, via email, a business owner to convince employees to pay out bogus invoices.
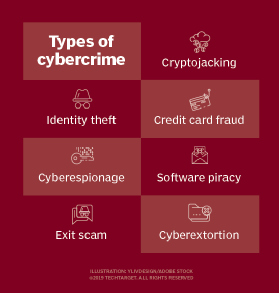
Types of cybercrime
Cybercriminals have a plethora of cybercrime types to conduct malicious attacks. Most attackers carry out cybercrimes with the expectation of financial gain, though the ways cybercriminals get paid can vary. Specific types of cybercrimes include the following:
- Cyberextortion . This crime involves an attack or threat of an attack coupled with a demand for money to stop the attack. One form of cyberextortion is a ransomware attack. Here, the attacker gains access to an organization's systems and encrypts its documents and files -- anything of potential value -- making the data inaccessible until a ransom is paid. Usually, payment is in some form of cryptocurrency, such as bitcoin.
- Cryptojacking . This attack uses scripts to mine cryptocurrencies within browsers without the user's consent. Cryptojacking attacks can involve loading cryptocurrency mining software to the victim's system. Many attacks depend on JavaScript code that does in-browser mining if the user's browser has a tab or window open on the malicious site. No malware needs to be installed as loading the affected page executes the in-browser mining code.
- Identity theft . This type of attack occurs when an individual accesses a computer to steal a user's personal information, which is then used to steal that person's identity or access their valuable accounts, such as banking and credit cards. Cybercriminals buy and sell identity information on darknet markets, offering financial accounts and other types of accounts, such as video streaming services, webmail, video and audio streaming, online auctions and more. Personal health information is another frequent target for identity thieves.
- Credit card fraud. This is an attack that occurs when malicious hackers infiltrate retailers' systems to get their customers' credit card or banking information. Stolen payment cards can be bought and sold in bulk on darknet markets, where hacking groups that have stolen mass quantities of credit cards profit by selling to lower-level cybercriminals who profit through credit card fraud against individual accounts.
- Cyberespionage . This crime involves cybercriminals hacking into systems or networks to gain access to confidential information held by a government or other organization. Attacks are motivated by profit or ideology. Cyberespionage activities include cyberattacks that gather, modify or destroy data, as well as using network-connected devices, such as webcams or closed-circuit TV cameras, to spy on a targeted individual or groups and monitoring communications, including emails, text messages and instant messages.
- Software piracy . This attack involves the unlawful copying, distribution and use of software programs with the intention of commercial or personal use. Trademark violations, copyright infringements and patent violations are often associated with software piracy.
- Exit scam. The dark web has given rise to the digital version of an old crime known as the exit scam . In today's form, dark web administrators divert virtual currency held in marketplace escrow accounts to their own accounts -- essentially, criminals stealing from other criminals.
Common examples of cybercrime
Commonly seen cybercrime attacks include distributed DoS ( DDoS ) attacks, which use a network's own communications protocol against it by overwhelming its ability to respond to connection requests. DDoS attacks are sometimes carried out for malicious reasons or as part of a cyberextortion scheme , but they can also be used to distract the victim organization from some other attack or exploit carried out at the same time.
Malware is another common cybercrime that can damage systems, software or data stored on a system. Ransomware attacks are a type of malware that encrypts or shuts down victim systems until a ransom is paid.
Phishing campaigns help attackers infiltrate corporate networks. Phishing includes sending fraudulent emails to users in an organization, enticing them to download malicious attachments or click on malicious links that then spread the malware across the network.
In credential attacks, a cybercriminal aims to steal or guess victims' usernames and passwords. These attacks can use of brute-force -- for example, by installing keylogger software -- or by exploiting software or hardware vulnerabilities that expose the victim's credentials.
Cybercriminals can also hijack websites to change or delete content or to access or modify databases without authorization. For example, attackers use Structured Query Language injection exploits to insert malicious code into a website, which can then be used to exploit vulnerabilities in the website's database, enabling a malicious hacker to access and tamper with records or gain unauthorized access to sensitive information and data, such as customer passwords, credit card numbers, personally identifiable information, trade secrets and intellectual property.
Other common examples of cybercrime include illegal gambling, the sale of illegal items -- such as weapons, drugs or counterfeit goods -- and the solicitation, production, possession or distribution of child pornography.
Effects of cybercrime on businesses
The true cost of cybercrime is difficult to assess accurately. Cybersecurity Ventures reported that global cybercrime grows by 15% annually, with it expected to reach $10.5 trillion by 2025.
While the financial losses due to cybercrime can be significant, businesses can also suffer other disastrous consequences as a result of criminal cyberattacks, including the following:
- Damage to investor perception after a security breach can cause a drop in the value of a company.
- Businesses could face increased costs for borrowing and greater difficulty in raising more capital as a result of a cyberattack.
- Loss of sensitive customer data can result in fines and penalties for companies that have failed to protect their customers' data. Businesses might also be sued over the data breach.
- Damaged brand identity and loss of reputation after a cyberattack undermine customers' trust in a company and that company's ability to keep their financial data safe. Following a cyberattack, firms could lose current customers and lose the ability to gain new customers.
- Businesses might incur direct costs from a criminal cyberattack, including increased insurance premium costs and the cost of hiring cybersecurity companies for incident response and remediation, as well as public relations and other services related to an attack.
Effects of cybercrime on national defense
Cybercrimes can have public health and national security implications, making computer crime one of DOJ's top priorities. In the U.S., at the federal level, the Federal Bureau of Investigation's (FBI) Cyber Division is the agency within DOJ charged with combating cybercrime. The Department of Homeland Security (DHS) sees strengthening the security and resilience of cyberspace as an important homeland security mission. Cybersecurity and Infrastructure Security Agency ( CISA ), a division of DHS, aims to improve the resilience and security of cyber and physical infrastructure. Other agencies, such as the U.S. Secret Service (USSS) and U.S. Immigration and Customs Enforcement (ICE), have special divisions dedicated to combating cybercrime.
USSS' Electronic Crimes Task Force, for example, investigates cases that involve electronic crimes, particularly attacks on the nation's financial and critical infrastructures. USSS also runs the National Computer Forensics Institute, which provides state and local law enforcement, judges and prosecutors with computer forensics training.
The Internet Crime Complaint Center, a partnership among the FBI, National White Collar Crime Center and Bureau of Justice Assistance, accepts online complaints from victims of internet crimes or interested third parties.
How to prevent cybercrime
While it isn't possible to completely eradicate cybercrime and ensure complete internet security, businesses can reduce their exposure to it by maintaining an effective cybersecurity strategy using a defense-in-depth approach to securing systems, networks and data.
Organizations can reduce cybercrime risks with the following:
- Develop clear policies and procedures for the business and employees.
- Create cybersecurity incident response plans to support these policies and procedures.
- Outline the security measures in place about how to protect systems and corporate data.
- Use multifactor authentication ( MFA ) apps or physical security keys.
- Activate MFA on every online account when possible.
- Verbally verify the authenticity of requests to send money by talking to a financial manager.
- Create intrusion detection system rules that flag emails with extensions similar to company emails.
- Scrutinize all email requests for transfer of funds to determine if the requests are out of the ordinary.
- Train employees on cybersecurity policies and procedures and what to do in the event of a security breach.
- Keep websites, endpoint devices and systems current with all software release updates or patches .
- Back up data and information regularly to reduce the damage in case of a ransomware attack or data breach.
Information security and resistance to cybercrime attacks can also be built by encrypting local hard disks and email platforms, using a virtual private network and using a private, secure domain name system server.
Cybercrime legislation and agencies
Various U.S. government agencies have been established to deal specifically with the monitoring and management of cybercrime attacks. The FBI's Cyber Division is the lead federal agency for dealing with attacks by cybercriminals, terrorists or overseas adversaries. Within DHS, CISA coordinates between private sector and government organizations to protect critical infrastructure.
The Cyber Crimes Center (C3) within ICE provides computer-based technical services that support domestic and international investigations included in the Homeland Security Investigations (HSI) portfolio of immigration and customs authorities. C3 focuses on cybercrimes that involve transborder illegal activities. It is responsible for finding and targeting all cybercrimes within HSI jurisdiction. C3 includes the Cyber Crimes Unit, Child Exploitation Investigations Unit and Computer Forensics Unit.
Various laws and legislation have also been enacted. In 2015, the United Nations Office on Drugs and Crime released a cybercrime repository, a central database that includes legislation, previous findings and case law on cybercrime and electronic evidence. The intention of the cybercrime repository is to assist countries and governments in their attempts to prosecute and stop cybercriminals.
Cybercrime legislation dealing can be applicable to the general public or sector-specific, extending only to certain types of companies. For example, the Gramm-Leach-Bliley Act focuses on financial institutions and regulates the implementation of written policies and procedures to improve the security and confidentiality of customer records, while also protecting private information from threats and unauthorized access and use.
Other legislation has been established to deal with specific cybercrimes, such as cyberbullying and online harassment. A little over half of U.S. states have implemented laws dealing directly with these crimes. For example, Massachusetts law cites that cyber-stalking is a crime punishable with a fine of up to $1,000, a maximum of five years in jail or both. In Tennessee, online harassment and stalking is considered a Class A misdemeanor, and a convicted cybercriminal can face a jail sentence of, at most, 11 months and 29 days, a fine of up to $2,500 or both.
The definition was written by Kate Brush and Michael Cobb in 2021. TechTarget editors revised it in 2024 to improve the reader experience.
Continue Reading About cybercrime
- Standardized data collection methods can help fight cybercrime
- Cyber Crime -- FBI
- Common types of cyberattacks and how to prevent them
- Types of insider threats and how to prevent them
- Benefits of sustainable cybersecurity in the enterprise
Related Terms
Dig deeper on threats and vulnerabilities.

What role does an initial access broker play in the RaaS model?

35 cybersecurity statistics to lose sleep over in 2024

A who's who of cybercrime investigators

Microsoft, Fortra get court order to disrupt Cobalt Strike

This introduction explores eight network devices that are commonly used within enterprise network infrastructures, including ...
Organizations should create comprehensive work-from-home reimbursement plans that drive better network and internet connectivity ...
Experts at the Cisco Live 2024 conference discussed the future of AI in networks and how its use can help simplify network and ...
Businesses of the future will rely on workers with IT skills even more than they do today. Find out which jobs might be most in ...
Get guidance on how relevant cloud compliance standards are developed and tips on evaluating third-party providers' cloud ...
The Biden administration's regulatory efforts have defined the U.S. approach to climate over the last four years. That could ...
As Microsoft prods its customers toward Windows 11, organizations should be asking what their approach to the new OS will be and ...
These 12 tools approach patching from different perspectives. Understanding their various approaches can help you find the right ...
Windows 10 end of support is a critical date for administrators to know about. While the simplest option is to move to Windows 11...
CIOs are taking a hard look at the VMware portfolio, weighing the potential benefits of Broadcom's changes and deciding whether ...
Building AI apps in the cloud requires you to pay more attention to your cloud workload management because of how AI impacts ...
While cloud-first gained popularity for its scalability and cost efficiency, the hybrid-first approach acknowledges that not all ...
Survey reveals lack of reliable mobile connectivity in the office is affecting seven in 10 hybrid workers, forcing a majority of ...
A former Fujitsu engineer made an ‘unbelievable’ claim about evidence he gave in witness statements when acting as an expert ...
The Gulf Energy subsidiary will offer Google’s sovereign cloud service in Thailand with a focus on air-gapped configurations

Essay on Cyber Crime
Students are often asked to write an essay on Cyber Crime in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Cyber Crime
Introduction to cyber crime.
Cybercrime refers to illegal activities conducted through the internet. It’s a fast-growing area of crime, with more criminals exploiting the speed, convenience, and anonymity of the internet.
Types of Cyber Crime
Preventing cyber crime.
Preventing cybercrime is crucial. This can be achieved by using strong, unique passwords, keeping software and systems updated, and being cautious of suspicious emails or websites.
Cybercrime is a significant issue in today’s digital age. Awareness and proper precautions can help in preventing these crimes.
250 Words Essay on Cyber Crime
Introduction.
Cybercrime, an umbrella term encompassing a variety of offenses committed using digital technology, poses a significant threat to the modern world. As our reliance on technology increases, so does the potential for misuse, leading to a surge in cybercrimes.
The Nature of Cybercrime
Cybercrimes can range from financial theft, identity theft, cyberstalking, to more complex forms like cyber terrorism and cyber warfare. They exploit the anonymity provided by the internet, making them difficult to trace, investigate, and prosecute.
Impact of Cybercrime
The impact of cybercrime extends beyond financial loss. It can cause significant psychological harm to victims, damage reputations, and even pose threats to national security. In a digital world, the effects of cybercrime are far-reaching and potentially devastating.
Preventing Cybercrime
Preventing cybercrime requires a multi-faceted approach. It involves not only technological solutions but also legal and educational measures. A robust cybersecurity infrastructure, stringent laws, and increased public awareness are crucial to mitigating the risk of cybercrime.
In conclusion, as technology advances, so too does the sophistication of cybercrimes. Combating this growing threat requires a comprehensive approach that combines technology, legislation, and education. The fight against cybercrime is a shared responsibility, requiring collective effort from individuals, organizations, and governments alike.
500 Words Essay on Cyber Crime
In the digital age, our reliance on technology has given rise to a new form of criminal activity known as cyber crime. This term encapsulates any illegal activity that utilizes a computer as its primary means of commission. Cyber crime has become a critical concern due to its widespread impact, affecting individuals, businesses, and even nations.
The Different Forms of Cyber Crime
Cyber crime manifests in various forms, each carrying its unique implications. Identity theft, for instance, involves unauthorized access and use of personal information for fraudulent purposes. Another common type, cyberstalking, uses digital tools to harass or threaten individuals. More complex forms of cyber crime include cyberterrorism and cyber warfare, which target national security and infrastructure.
The Impact of Cyber Crime
The impact of cyber crime is far-reaching and multifaceted. On an individual level, victims may face financial loss, emotional distress, and privacy invasion. For businesses, the implications can be devastating, leading to significant financial losses, reputational damage, and loss of customer trust. On a national level, cyber crime can threaten a country’s security, economy, and infrastructure.
Legal and Ethical Considerations
The legal landscape surrounding cyber crime is complex and continually evolving. Jurisdictional issues often arise, given the borderless nature of the internet. Ethically, the debate around privacy and security is pertinent. While law enforcement agencies advocate for backdoors into encrypted systems to combat cyber crime, this raises concerns about potential misuse and invasion of privacy.
The Future of Cyber Crime
As technology advances, so does the sophistication of cyber crimes. Future threats could involve artificial intelligence and machine learning, making detection and prevention even more challenging. Therefore, continuous research, development of advanced cybersecurity measures, and international cooperation are imperative to stay a step ahead of cyber criminals.
If you’re looking for more, here are essays on other interesting topics:
Apart from these, you can look at all the essays by clicking here .
Leave a Reply Cancel reply

- Skip to main content
- Skip to secondary menu
- Skip to primary sidebar
- Skip to footer
A Plus Topper
Improve your Grades
Cyber Crime Essay | Essay on Cyber Crime for Students and Children in English
February 14, 2024 by Prasanna
Cyber Crime Essay: A crime that involves a network and a computer is known as computer-oriented crime or cybercrime. Such a crime affects the security of everything, might be a person, institution or even a nation. The computer is either used to commit a crime or is usually a target. Things that are hacked include information, privacy, data and it is often released out in the open to bring someone or some people down. Cybercriminals can be anyone, even your next-door neighbour or a high functional, advanced organization. Like any other form of criminal activity, cybercrime is committed to gain excess money and finish the lives of people without murder.
You can also find more Essay Writing articles on events, persons, sports, technology and many more.
Long and Short Essays on Cyber Crime for Students and Kids in English
We are providing students with essay samples on an extended essay of 500 words and a short piece of 150 words on the topic Cyber Crime for reference.
Long Essay on Cyber Crime 500 Words in English
Long Essay on Cyber Crime is usually given to classes 7, 8, 9, and 10.
There are various forms and types of Cyber Crime all over the world. Cybercrimes are committed by hackers not only for profit but for personal gains and with aims to damage a person, institution or nation. Internationally, both governmental and non-state institutions engage in cybercrime. Cybercrime is known as cyber warfare as soon as it crosses international borders.
Most cybercrimes fall under two broad categories, namely, Criminal Activity that Targets and Criminal Activities that Uses.
Other categories of cybercrime include, cyberterrorism which is is terrorism committed through a network or a computer, Financial Fraud Crimes, Cyber extortion which is when individuals ask for money in return of stopping malicious attacks on a system, Cybersex Trafficking, Online Harassment, Drug Trafficking, etc. Phishing, Malware Attacks, Denial of services and distributed DoS attacks are few of the most common examples of cybercrime.
Online Harassment is something that is not considered as a form of cybercrime by most people, but it, in reality, is what happens in bulk. Under the category of online Harassment also falls the sub-category of cyber crimes against women, which is defined as ‘crimes targeted against women with a motive to intentionally harm them either physically or psychologically, using modern communication networks’.
Tracing a cybercrime delinquent isn’t the most straightforward task to do because of their use of virtual spaces and attacks from various parts. It has been recorded that in 2018 The Internet Crime Complaint Sector received 351,937 complaints alone.
Sine, everything you do on a computer or a network is recorded one way or the other, getting hold of the criminals isn’t impossible.
Since many developing countries like the Philippines have underdeveloped laws regarding cybercrime and cybersecurity, it becomes easy for cybercriminals to use the underdeveloped laws of the developing countries to remain undetectable and anonymous.
With the rise of the increase of technology, cybercrime has become a critical part of the society, and majors like that of Cyber Security have been established in many universities, hence, becoming an integral part of the academic system.
You can now access more Essay Writing on Cyber Crime topic and many more topics.
Since the age of computers and technology is rising every day, our lifestyles are becoming computer-dependent, and everything is stored on there. As the main aim of cybercriminals is the breach of privacy, things become simpler for them.
One major step towards prevention of cybercrime is the spread of Awareness. There are many individuals who aren’t comfortable using a computer, and hence they are more prone to cybercrimes. People don’t know how much and to what extent things can be done with the help of technology and computers; once, people are made aware of all these factors, a little wall of prevention can be created. Updated software and use of reliable anti-virus software are critical practices in preventing cybercrimes.
The phrase, ‘prevention is better than cure might be old but has been relevant since forever and is relevant in today’s technology-dependent world full of all sorts of crime.
Short Essay on Cyber Crime 150 Words in English
Short Essay on Cyber Crime is usually given to classes 1, 2, 3, 4, 5, and 6.
Crime synonymous with the use of computers and network as means or targets is known as computer crime or cybercrime. Cybercrime is not a new word for anyone living in the 21st century, but not many know in how many forms they are present.
Some of the most relevant forms of cybercrime are online Harassment, even though some might not give too much attention to it, it is part of the heinous umbrella term. Drug Trafficking, Cyber Warfare, Cyber Extortions, etc. are a few other famous forms of cybercrime.
The cybercriminal can either use a computer to commit the crime or have another computer as his aim. Most of these criminals commit cybercrimes for money, no matter the reason, their primary objective is to a breach of privacy. Since most people have their lives saved on computers, they need to be extra cautious, which will only be possible through education and Awareness.
10 Lines on Cyber Crime Essay in English
1. Crimes committed by using a network or computer is known as cybercrime. 2. Cybercriminals either use the computer as a tool to commit the crime or aim the computer to commit the crime. 3. Online Harassment, no matter what anyone says, is a significant and ubiquitous form of cybercrime. 4. Most cybercriminals resided in America since America’s development with the computer was faster than that of any other country, but now, no place is devoid of cybercriminals. 5. Cyber-crimes can bring down a person, an institution or even a whole nation with the breach of privacy. 6. Cyber Criminals use underdeveloped laws of the developing countries to manipulate records and remain anonymous; hence laws need to be made stricter. 7. Education and Awareness are the initials steps taken to prevent cybercrimes from taking place. 8. One needs to have a reliable anti-virus service and have all their software updated if they want to prevent cybercrimes. 9. Cyber Security has become an integral part of the curriculum in developed countries in the past few years. 10. Anyone can be a cyber-criminal. They can be a well-structured organization or a novice hacker.
FAQ’s on Cyber Crime Essay
Question 1. How to prevent cyber crimes?
Answer: The best way of prevention is by keeping everything updated and secure with a reliable anti-virus service.
Question 2. How to file cybercrime reports?
Answer: Almost all countries have a cybersecurity cell, and their contact information is available online easily.
Question 3. Is Online Harassment Cyber Crime?
Answer: Yes, it is; please report the individual as soon as possible.
Question 4. Is it very hard to catch cybercriminals?
Answer: Yes, it is hard to catch cybercriminals but not impossible.
- Picture Dictionary
- English Speech
- English Slogans
- English Letter Writing
- English Essay Writing
- English Textbook Answers
- Types of Certificates
- ICSE Solutions
- Selina ICSE Solutions
- ML Aggarwal Solutions
- HSSLive Plus One
- HSSLive Plus Two
- Kerala SSLC
- Distance Education
- Trending Blogs
- Geeksforgeeks NEWS
- Geeksforgeeks Blogs
- Tips & Tricks
- Website & Apps
- ChatGPT Blogs
- ChatGPT News
- ChatGPT Tutorial
What is Cybercrime? (Types and Legal Remedies)
- What is Cyber Law? (Importance, Types and Purpose)
- What is Cyberbullying and its impact?
- What is a Cyber Security Audit?
- What is the Importance of Cyber Law?
- What is Cyber Security Awareness?
- What are Digital Rights? (It's Importance and Types)
- What is Spyware in Cyber Security?
- What is a Cyber Security Strategy?
- What is Cyber Bullying? Definition, Types, Effects, Laws
- What is Cyber Resilience?
- What is Cyber Terrorism?
- What is Spoofing in Cyber Security?
- What is Spillage in Cybersecurity?
- What is Copyright Act in Cyber Security?
- Cybercrime Causes And Measures To Prevent It
- Cyber Security, Types and Importance
- Cyber Criminals and its types
- What is Cyber Threat Intelligence?
- Malware and its types
Cybercrime refers to illegal activities carried out using computers and the Internet. These crimes can range from stealing personal information and financial fraud to hacking and spreading malicious software. Cybercrime poses significant risks to individuals, businesses, and governments worldwide.

Most of the time, people who do cybercrime, called cybercriminals or hackers, are trying to make money. But sometimes, they do it to damage computers or networks for other reasons, like political or personal motives.
Cybercrime can be done by just one person or a whole group. Some cybercriminals are very organized and good with technology. They use complicated methods to commit crimes. Others might just be starting out and not have much skill yet.
This article explores different types of cybercrime, their impact, and ways to prevent becoming a victim. Understanding cybercrime is essential for staying safe online and protecting against digital threats
Table of Content
What is Cybercrime?
What are the types of cybercrime, examples of cybercrime, impacts of cybercrimes.
- What are the Legal Remedies for Cybercrimes?
Importance of Legal Remedies for Cybercrimes
What is cybercrime .
Cybercrime is illegal activities related to a computer or internet. It includes activities like Hacking , phishing, selling identity, disseminating malware, and bringing abuse to the fore are but a few of the malicious things that come under this act.
The exploitation of the internet and another digital platforms by offenders in recent times has led to an increase in the efficiency and appearance of new tactics by cyber criminals who are constantly upgrading their way to acquire different sorts of data and money by carrying out various Cybercrimes. Along with the world, hacking is spiraling down as per the recent surveys. Every year, these bad things complicate or prevent them from doing their work with billions of people and businesses.
There are several types of cybercrime, each involving different methods and objectives. Here are some common types of cybercrime:
- Hacking : Unauthorized access to computer systems or networks to steal data, disrupt operations, or cause damage.
- Phishing : Phishing includes fraudulent attempts to obtain sensitive information such as usernames, passwords, and credit card details by posing as a trustworthy entity in electronic communications.
- Ransomware : Malicious software that encrypts data on a victim’s computer, demanding payment (usually in cryptocurrency) to decrypt it.
- Identity Theft : Stealing personal information (such as Social Security numbers or bank account details) to impersonate someone else for financial gain.
- Online Scams : Various fraudulent schemes conducted via the Internet, including fake websites, online auctions, and investment frauds.
- Malware : Malicious software designed to damage or gain unauthorized access to computer systems, including viruses, worms, trojans, and spyware.
- Denial-of-Service (DoS) Attacks : DoS attacks focuses on flooding a network or server with traffic to overwhelm it and prevent legitimate users from accessing services.
- Cyberbullying : Harassment, threats, or humiliation of individuals through digital platforms, often through social media, messaging apps, or email.
- Data Breaches : Unauthorized access to sensitive data stored electronically, resulting in exposure or theft of personal or corporate information.
- Child Exploitation : Using digital platforms to exploit children for sexual purposes, such as producing or distributing child pornography.
- Financial Fraud : Illegally acquiring money or goods through deception, including online banking fraud, credit card fraud, and investment scams.
- Cyber Espionage : Stealing classified, sensitive, or proprietary information from governments, corporations, or individuals using digital means.
How Cybercrime Works
Cybercrime works through various methods and techniques that exploit vulnerabilities in computer systems, networks, and human behavior. Here’s a simplified overview of how cybercrime typically operates:
- Identifying Vulnerabilities : Cybercriminals look for weaknesses in software, networks, or devices that can be exploited. These vulnerabilities can include outdated software, weak passwords, unprotected networks, or human error.
- Planning the Attack : Once a vulnerability is identified, cybercriminals plan their attack. This can involve writing malicious code, creating fake websites or emails, or developing a strategy to deceive victims.
- Phishing : Sending deceptive emails or messages to trick individuals into revealing sensitive information.
- Malware : Distributing malicious software that can infiltrate and control systems.
- Hacking : Exploiting software vulnerabilities to gain unauthorized access to systems.
- Social Engineering : Manipulating people into divulging confidential information.
- Data Theft : Stealing personal, financial, or corporate data.
- Ransomware : Encrypting data and demanding payment for its release.
- Fraud : Conducting fraudulent transactions or impersonating individuals for financial gain.
- Service Disruption : Launching attacks like Denial-of-Service (DoS) to disrupt services.
- Covering Tracks : After executing the attack, cybercriminals often take steps to cover their tracks and avoid detection. This can involve deleting logs, using encryption, or routing their activities through multiple locations to hide their identity.
Cybercrime often include both, using viruses to attack computers and then using those computers to spread harmful software further. Some places also think about crimes where computers help other crimes, like storing stolen data, as a type of cybercrime.
Here are some well-known types of cybercrime that criminals use:
| Cyber Attack | Description |
|---|---|
| Phishing | Phishing involves tricking individuals into providing sensitive information, such as passwords or financial details, by posing as a legitimate entity through emails, messages, or websites. |
| Ransomware | R if the ransom is not paid. |
| Malware | Malware is malicious software designed to disrupt, damage, or gain unauthorized access to computer systems, often spread through infected files, downloads, or compromised websites. |
| DDoS (Distributed Denial of Service) | disrupting services, and potentially leading to financial losses. |
| Insider Threat | Insider threats involve malicious actions or data breaches perpetrated by individuals within an organization, such as employees or contractors, who exploit their access for personal gain or sabotage. |
| Social Engineering | Social engineering manipulates individuals into divulging confidential information or performing actions through psychological manipulation, often exploiting trust or authority. |
| Man-in-the-Middle (MitM) | without their knowledge, allowing attackers to eavesdrop, steal information, or inject malicious content. |
| SQL Injection | to execute unauthorized SQL commands, potentially granting attackers access to sensitive data or compromising the system. |
| Zero-Day Exploits | Zero-day exploits target previously unknown vulnerabilities in software or hardware, leveraging the element of surprise to launch attacks before developers can develop and deploy patches or fixes. |
Below are some of the major impacts of cybercrime:
- Financial Losses: Cybercrimes result in substantial financial losses for individuals and businesses, including stolen funds, fraudulent transactions, and extortion payments.
- Reputational Damage: Victims of cybercrimes often experience reputational harm, affecting their credibility, trustworthiness, and brand image.
- Data Breaches: Cyberattacks can lead to data breaches, exposing sensitive information such as personal data, financial records, and intellectual property.
- Legal Consequences: Cybercrimes may result in legal repercussions, including regulatory fines, lawsuits, and criminal charges.
- Psychological Effects: Victims of cyberbullying and online harassment may suffer from psychological distress, anxiety, and depression.
- Disruption of Services: Cyberattacks can disrupt essential services, such as healthcare, transportation, and utilities, causing inconvenience and potential safety risks.
- Societal Impact: Cybercrimes pose significant societal challenges, undermining trust in digital technologies, eroding privacy rights, and threatening national security.
What are the Legal Remedies for Cybercrimes ?
Here are some of the top legal remedies for cybercrimes :
- Cybercrime Laws: Governments make rules to make cybercrimes illegal and punish people who do them. These laws help stop bad activities online and make sure that people who break the rules face consequences.
- Law Enforcement Agencies: Special police groups, called cybercrime units, are formed to look into cybercrimes and catch the people who do them. They work to find the people behind cybercrimes and bring them to justice.
- International Cooperation: Different countries work together to fight cybercrimes that happen across borders. They share information and make agreements to help catch cybercriminals no matter where they are in the world.
- Regulatory Compliance: Organizations need to follow rules about cybersecurity to keep themselves and their customers safe. They have to put measures in place to protect against cyber threats like hackers and data leaks.
- Victim Support Services: If someone becomes a victim of a cybercrime, they can get help from support services. These services offer counseling and help victims recover from the harm caused by cybercrimes .
Hacking should be stopped at all costs by law to make sure people, businesses, and institutions are safe from online threats. These kinds of activities make it easy to place hackers, end up with new crime events, and provide training for responsible people.
A legal system, that aids digital asset safety, and its members can take justice into fulfillment and build trust in the digital world, exists via making laws clearer, giving police clear ways to apply them, and offering victim services.
Obeying the regulations and being team players while forming country groups is the most effective way of building global cybersecurity as it brings the countries together and makes threatening attacks a dream.
Cybercrime poses a significant and growing threat in our increasingly digital world . It affects individuals, businesses, and governments, causing substantial financial losses, privacy breaches, and operational disruptions. As technology advances, so do the tactics of cybercriminals, making it crucial for everyone to stay informed and vigilant. Implementing robust cybersecurity measures, promoting awareness, and fostering collaboration between law enforcement and technology experts are essential steps in combating cybercrime.
We can protect the cyber world from abuse by cybercriminals and create an excellent cyberspace where all can thrive if we implement stringent cyber security, cooperate internationally, and firmly adhere to cybercrime laws.
What is Cybercrime? (Types and Legal Remedies) – FAQs
Cybercrime is an incident related to a computer or network online precisely and undoubtedly is known as an electronic device having an illegal element.
What is cybersecurity?
Cybersecurity refers to the practice of protecting computer systems, networks, and data from digital attacks.
What are the common types of cyberattacks?
Common cyberattacks include malware infections, phishing scams, ransomware attacks, DDoS (Distributed Denial of Service) attacks, and insider threats.
How can individuals enhance their cybersecurity?
Individuals can enhance their cybersecurity by using strong, unique passwords, enabling two-factor authentication, keeping software up to date, being cautious of suspicious emails and links, and regularly backing up their data.
What is the role of encryption in cybersecurity?
Encryption plays a crucial role in cybersecurity by encoding data in a way that only authorized parties can access it, thus protecting it from unauthorized access and interception.
How do businesses benefit from cybersecurity measures?
Businesses benefit from cybersecurity measures by safeguarding their sensitive data, maintaining customer trust, avoiding financial losses due to cyberattacks, and ensuring continuity of operations.
What legal frameworks govern cybersecurity?
Legal frameworks governing cybersecurity include regulations such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and industry-specific standards like the Payment Card Industry Data Security Standard (PCI DSS).
What should I do if I become a victim of a cyberattack?
If you become a victim of a cyberattack, you should immediately report the incident to the relevant authorities or your organization’s IT security team, change your passwords, and take steps to mitigate further damage, such as restoring from backups and updating security measures.
Please Login to comment...
Similar reads.
- tech-updates
Improve your Coding Skills with Practice
What kind of Experience do you want to share?

116 CyberCrime Topics & Essay Samples
If you are writing a cybercrime essay, our team prepared this article just for you. Here, you will find 115 unique topics for any type of paper.
Solutions By Industry
- Support Log-in
- Digital Risk Portal
- Email Fraud Defense
- ET Intelligence
- Proofpoint Essentials
- Sendmail Support Log-in
- English (Americas)
- English (Europe, Middle East, Africa)
- English (Asia-Pacific)
What Is Cyber Crime?
Table of contents, cyber crime types and examples, the impact of cyber crime, cyber crime prevention, how proofpoint can help.
Cyber crime has become alarmingly prevalent in a world where most transactions are conducted online using digital platforms. Based on current cyber crime trends , the cost of such attacks could reach upwards of $20 trillion worldwide by 2026.
Cyber crime is a general term describing the myriad of criminal activities carried out using a computer, network, or another set of digital devices. Consider cyber crime the umbrella over the vast range of illegal activities that cyber criminals commit. These include hacking, phishing, identity theft , ransomware, and malware attacks, among many others.
The reach of cyber crime knows no physical boundaries. Criminals, victims, and technical infrastructure span worldwide. With the use of technology to exploit security vulnerabilities on both a personal and enterprise level, cyber crime takes many shapes and continuously evolves. In turn, the ability to effectively investigate, prosecute, and prevent cyber crimes is an ongoing fight with many dynamic challenges.
Cyber crime poses a serious threat to individuals, businesses, and government entities and can result in significant financial loss, damaged reputation, and compromised records. As technology advances and more people rely on digital devices and networks for standard operations, the threat of cyber crime continues to increase, making it more critical than ever to take steps to protect against it.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:.
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we'll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
Cyber crime covers a broad spectrum of criminal activities that involve various digital platforms and technologies. Many types of cyber crimes are worth discussing, from fraudulent emails and social media activity to phishing scams and ransomware attacks. While some of these overlap with how they are committed, the most common include:
Email Scams
Misleading schemes that take many forms. Fake emails mislead recipients, while social engineering techniques deceive people into divulging information, such as credit card numbers, or transferring money to the attacker. Phishing schemes, whereby scammers mimic legitimate brands, are a common form of email scams .
Social Media Fraud
Scams that use social media platforms like Facebook, Twitter, Instagram, and TikTok to deceive and defraud victims. Examples include fictitious online stores, catfishing , social engineering attacks, or impersonation scams. Social media frauds often exploit user trust, naivety, and a tendency to overshare personal information online.
Banking Fraud
Fraudulent activities that target financial institutions or their customers and stakeholders. Banking frauds most commonly result in significant financial loss or identity theft, and attacker strategies often involve sophisticated hacking and social engineering tactics. Examples include credit card fraud, ATM skimming, and online banking scams.
eCommerce Fraud
Elaborate consumer scams that exploit weaknesses and pitfalls of online shopping technologies, like artificial or fabricated online stores, fake seller accounts, or credit card information theft. Cases of eCommerce fraud typically result in financial losses on behalf of both consumers and online retailers.
A highly-prevalent software attack programmed to damage and manipulate computer systems by introducing viruses, trojans, or spyware into the system. Malware is a frequent problem across many cases because it targets both individual PCs and enterprise-level computer networks. It's most commonly used for disrupting networks and stealing data from users.
A type of malware attack that encrypts victims' critical data and declares a ransom payment in exchange for a decryption key to recover access. Financially crippling for individuals and organizations alike, ransomware attacks often lead to data and asset loss, fiscal devastation, and disrupted productivity. One of the most talked about ransomware cases involved Costa Rica’s government and erupted into a national emergency.
Cyber Espionage
The use of hacking, malware attacks, or other cyber activity in which an unauthorized user attempts to access sensitive data or intellectual property to gain a competitive advantage over a company or government entity. Cases of cyber espionage often involve state-sponsored groups or individual hackers and can have major political or economic implications. One of the most significant cases of cyber espionage was the five Chinese military hackers indicted for computer hacking, economic espionage, and other offenses directed at U.S. entities.
Data Breaches
Unauthorized access or leaks of sensitive data, such as confidential information, critical records, or financial access. Data breaches can be attributed to a wide array of risk factors, such as weak passwords and cybersecurity protocols, software system vulnerabilities, or insider threats. The consequences can result in compromised data, financial damages, or tarnished reputations. Verizon's data breach investigations report highlighted that 82% of breaches involved a human element.
Computer Viruses
Perhaps the most common type of malicious software that can self-replicate and spread to other systems, often causing damage to computer files or programs. Examples of computer viruses include the Melissa, ILOVEYOU, and Nimda viruses - all spread fast to infect files and damage computer systems.
DDoS Attacks
Distributed Denial of Service attacks, or DDoS attacks , are programmed to overwhelm a network or website with traffic, causing it to slow down or crash entirely. DDoS attacks were one of many of Russia’s destructive cyber activities against Ukraine, along with other attacks designed to delete computer data belonging to governmental and private entities.
Software Piracy
A digital form of intellectual property theft involving unauthorized use or distribution of copyrighted material, such as software, music, or movies. Examples of software piracy include using key generators or crack software to activate paid software without a license.
Phishing Scams
Email fraud that involves techniques like deceptive emails, website scams, or misleading communications to con victims into sharing their personal information and sensitive data or clicking links to malicious downloads and websites. Examples of phishing scams involve emails that appear to be from household brands, financial institutions, government agencies, or social media sites.
Identity Theft
In a digital context, identity theft refers to acquiring someone's private data for fraudulent or malicious purposes. Target assets of identity theft include social security numbers, date of birth, credit card details, or online accounts. Specific types include financial, medical, and tax identity theft; social media impersonation; and identity cloning, when a person uses another's identity to conceal their own.
Online Harassment
Involves cyberbullying, cyberstalking, and repeated acts intended to scare, harm, anger, or shame a particular individual. Today, online harassment is most prevalent on social media sites, dating apps, and forums/message boards. Examples of online harassment include sending inappropriate and unsolicited messages, making clear and intentional threats, or distributing sensitive photos or videos of a victim.
Cyber Terrorism
Generally grander acts of destruction online by using the Internet or computer technology to carry out acts of terror, such as causing infrastructure damage and catastrophic malfunctions, stealing confidential information, or spreading propaganda with political or cultural implications. Cases of cyber terrorism are becoming increasingly sophisticated, placing higher demands on cybersecurity and protection.
As the types of cyber crime become increasingly sophisticated, so does the sheer volume of associated threats and financial losses. According to FBI reports, Secretary Mayorkas of the Department of Homeland Security highlighted losses related to cyber crime exceeding $4.1 billion in 2020.
More recent reports by the FBI's Internet Crime Complaint Center (IC3) division show losses surpassing $6.9 billion in 2021. Based on the IC3's report , the FBI attributes this steep rise in cyber crime losses to more ransomware attacks, business email compromise scams, and cryptocurrency-related crimes. The report also highlights the evolving landscape of cyber-attacks becoming increasingly interconnected with international relations and foreign intelligence threats.
On a more granular level, cyber crime runs rampant in many peoples' homes and personal computers. According to stats reported by the Cyber & Infrastructure Security Agency (CISA), 47% of Americans exposed their personal information to criminals online, and malicious software infected one-third of home computers.
The future impact of cyber crime looks to be a pivotal economic driver and a massive call to action for cybersecurity companies and countries that host them. Cybersecurity Ventures predicts the global costs of cyber crime will continue to grow by 15% a year over the next five years, reaching $10.5 trillion in annual damages by 2025.
As the overall cost and risks associated with cyber crimes continue to increase, so does the need to continuously implement, monitor, and upgrade prevention systems and technologies. Between foreign adversaries, terrorists, and everyday scammers, cyber-attacks are becoming smarter and more sophisticated.
Individuals, businesses, and governmental entities must take proactive measures to prevent cyber crime from penetrating security systems and infiltrating sensitive data. While some cyber crime prevention strategies remain steadfast in warding off attackers, there's also been a new wave of modern technologies to help support these initiatives.
Advanced Cybersecurity Systems
One of the key strategies in preventing cyber crime is utilizing advanced cybersecurity protection. This includes fundamental technologies like firewalls, antivirus software, and intrusion detection systems, but more advanced cybersecurity systems are evolving with artificial intelligence (AI) and machine learning (ML). Implementing the right cybersecurity tools should be a top priority for any organization or individual aiming to protect itself from cyber-attacks and digital threats.
Multifactor Authentication
Multifactor authentication (MFA), commonly used as two-factor authentication, is a common security protocol that prevents data breaches, hacks, and other direct cyber-attacks. In simple terms, this process requires users to provide two or more forms of identification to authenticate access to their accounts, such as needing a password and an access code sent to a device. Now a best practice protocol for organizations, MFA adds extra layers of cybersecurity to online accounts, making it much more challenging for attackers to access your data.
Virtual Private Networks
A Virtual Private Network (VPN) is a service that enables users to browse the Internet with reinforced security and anonymity. VPNs are engineered to encrypt online activity, making it far more difficult for cyber-attackers to intercept and steal your data. VPNs act as intermediaries between your device and the targeted server, adding their own encryption layer and routing communication via their own servers. VPNs are especially effective in helping protect against email frauds like phishing scams by masking your IP address and location.
Email Security Solutions
Email accounts are one of the most frequently exploited channels for cyber-attackers to breach access to sensitive data and private information. Specialized email security technologies can be leveraged to prevent this activity, which includes solutions like email encryption, spam filters, and antivirus software. Encryption is a powerful technology that protects email content from interception. Spam filters detect and prevent unwarranted and malicious emails from reaching your inbox, while antivirus software detects and removes malicious attachments from emails.
Password Managers
Cyber criminals frequently attack password credentials. In addition to creating secure, difficult-to-hack passwords, password managers are software applications that securely store multiple login credentials in an encrypted database, all of which are locked behind a master password. Password managers are commonly used by organizations, remote teams, and individuals to provide extra security protection when surfing the web while safely maintaining passwords in a safe space. The most common password managers include 1Password, KeePass, LastPass, and Apple's iCloud Keychain. However, some password managers come with risks.
Security Awareness Training
Many cyber-attacks result from human error, such as clicking on malicious links or downloading virus-containing files. Security awareness training is intended to help educate users on how to better identify, avoid, and mitigate the threat of cyber-attacks. The most common forms of training are computer-based awareness training and phishing simulated exercises where employees receive fake phishing emails to test how they react. Security awareness training helps organizations establish a security-conscious culture, creating a more resilient network to protect against cyber-attackers.
Data Backup and Recovery
Many forms of cyber-attacks can result in critical data loss, which can have severe financial and operational repercussions for both individuals and organizations. Data backup and recovery solutions can help mitigate the damages from data loss by creating backup copies of data and ensuring a faster recovery in the event of a ransomware attack, data breach, or another form of cyber-attack. Regularly archiving data is an essential security protocol to ensure that you can recover your data in the event of an attack.
AI and ML Cyber Crime Protection
More advanced cyber crime prevention technologies now utilize machine learning and artificial intelligence to gather and analyze data, track and trace threats, pinpoint vulnerabilities, and respond to breaches. For example, ML algorithms can detect and prevent fraud in financial transactions by identifying patterns that indicate fraudulent activity and flagging them for review. Similarly, AI technologies can detect and prevent cyber-attacks on networks and systems by analyzing network traffic, identifying abnormal patterns, and responding to threats in real-time.
As an organization, it can be challenging to anticipate the seemingly endless forms of cyber crime and the sophisticated strategies used by attackers. Proofpoint provides the most effective, enterprise-level cybersecurity solutions to protect your critical assets and data from advanced cyber threats.
Related Cyber Crime Resources
Awareness material, 3 weeks of cybersecurity best practices for ‘23, protecting healthcare’s greatest cyber security risk, cybersecurity platform to protect people and defend data, crime finds a way: the evolution and experimentation of the cybercrime ecosystem, subscribe to the proofpoint blog, ready to give proofpoint a try.
Start with a free Proofpoint trial.
- Skip to primary navigation
- Skip to main content
- Skip to primary sidebar
UPSC Coaching, Study Materials, and Mock Exams
Enroll in ClearIAS UPSC Coaching Join Now Log In
Call us: +91-9605741000
Cybercrime – Definition, Types, and Reporting
Last updated on June 19, 2024 by Alex Andrews George

Computers, mobile phones, and the internet have changed modern life. They provide us with many benefits.
However, information technology also makes us vulnerable to a wide range of threats. These threats may result in financial loss or damage to our reputation.
A minor lapse in managing our digital lives can open the door to cybercriminals. So it is extremely important to know how to prevent us from cybercrimes.
Table of Contents
What is cybercrime?
A Cybercrime is a crime involving computers and networks.
The computer may have been used in the execution of a crime or it may be the target.
Definition of Cyber Crime
Cybercrime may be defined as “Any unlawful act where computer or communication device or computer network is used to commit or facilitate the commission of a crime”.
Your Favourite Programs to Clear UPSC CSE: Download Timetable and Study Plan ⇓
(1) ⇒ UPSC Mains Test Series 2024
(2) ⇒ UPSC Prelims Test Series 2025
(3) ⇒ UPSC Fight Back 2025
(4) ⇒ UPSC Prelims cum Mains 2025
Two Main Types of Cybercrimes
Most cybercrime falls under two main categories:
- Criminal activity that targets computers.
- Criminal activity that uses computers.
Cybercrime that targets computers often involves malware like viruses.
Cybercrime that uses computers to commit other crimes may involve using computers to spread malware, illegal information or illegal images.
List of Cybercrimes: Examples
Cybercrimes include monetary crimes as well as non-monetary offences. The crimes result in damage to persons, computers, or governments.
1. Child Pornography OR Child sexually abusive material (CSAM)
Child sexually abusive material (CSAM) refers to a material containing sexual images in any form, of a child who is abused or sexually exploited. Section 67 (B) of the IT Act states that “it is punishable for publishing or transmitting of material depicting children in the sexually explicit act, etc. in electronic form.
2. Cyber Bullying
A form of harassment or bullying inflicted through the use of electronic or communication devices such as computers, mobile phones, laptops, etc.
3. Cyber Stalking
Cyberstalking is the use of electronic communication by a person to follow a person, or attempts to contact a person to foster personal interaction repeatedly despite a clear indication of disinterest by such person; or monitors the internet, email or any other form of electronic communication commits the offence of stalking.
4. Cyber Grooming
Cyber Grooming is when a person builds an online relationship with a young person and tricks or pressures him/ her into doing a sexual act.
5. Online Job Fraud
Online Job Fraud is an attempt to defraud people who are in need of employment by giving them false hope/ promise of better employment with higher wages.
6. Online Sextortion
Online Sextortion occurs when someone threatens to distribute private and sensitive material using an electronic medium if he/ she doesn’t provide images of a sexual nature, sexual favours, or money.
7. Phishing
Phishing is a type of fraud that involves stealing personal information such as Customer ID, IPIN, Credit/Debit Card number, Card expiry date, CVV number, etc. through emails that appear to be from a legitimate source.
Vishing is an attempt where fraudsters try to seek personal information like Customer ID, Net Banking password, ATM PIN, OTP, Card expiry date, CVV etc. through a phone call.
9. Smishing
Smishing is a type of fraud that uses mobile phone text messages to lure victims into calling back on a fraudulent phone number, visiting fraudulent websites or downloading malicious content via phone or web.
10. Sexting
Sexting is an act of sending sexually explicit digital images, videos, text messages, or emails, usually by cell phone.
11. SIM Swap Scam
SIM Swap Scam occurs when fraudsters manage to get a new SIM card issued against a registered mobile number fraudulently through the mobile service provider. With the help of this new SIM card, they get One Time Password (OTP) and alerts, required for making financial transactions through the victim’s bank account. Getting a new SIM card against a registered mobile number fraudulently is known as SIM Swap.
12. Credit Card Fraud or Debit Card Fraud
Credit card (or debit card) fraud involves the unauthorized use of another’s credit or debit card information for the purpose of purchases or withdrawing funds from it.
13. Impersonation and identity theft
Impersonation and identity theft is an act of fraudulently or dishonestly making use of the electronic signature, password or any other unique identification feature of any other person.
14. Spamming
Spamming occurs when someone receives an unsolicited commercial message sent via email, SMS, MMS and any other similar electronic messaging media. They may try to persuade the recipient to buy a product or service, or visit a website where he can make purchases, or they may attempt to trick him/ her into divulging bank account or credit card details.
15. Ransomware
Ransomware is a type of computer malware that encrypts the files, storage media on communication devices like desktops, Laptops, Mobile phones etc., holding data/information as a hostage. The victim is asked to pay the demanded ransom to get his device decrypts
16. Viruses, Worms, and Trojans
A computer virus is a program written to enter your computer and damage/alter your files/data and replicate itself.
Worms are malicious programs that make copies of themselves again and again on the local drive, network shares, etc.
A Trojan horse is not a virus. It is a destructive program that looks like a genuine application. Unlike viruses, Trojan horses do not replicate themselves but they can be just as destructive. Trojans open a backdoor entry to your computer which gives malicious users/programs access to your system, allowing confidential and personal information to be theft.
17. Data Breach
A data breach is an incident in which information is accessed without authorization.
18. Denial of Services (DoS) attack
A denial of Services (DoS) attack is an attack intended for denying access to computer resources without the permission of the owner or any other person who is in charge of a computer, computer system or computer network.
A Distributed Denial of Service (DDoS) attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources.
19. Website Defacement
Website Defacement is an attack intended to change the visual appearance of a website and/ or make it dysfunctional. The attacker may post indecent, hostile and obscene images, messages, videos, etc.
20. Cyber-Squatting
Cyber-Squatting is an act of registering, trafficking in or using a domain name with an intent to profit from the goodwill of a trademark belonging to someone else.
21. Pharming
Pharming is a cyber-attack aiming to redirect a website’s traffic to another, bogus website.
22. Cryptojacking
Cryptojacking is the unauthorized use of computing resources to mine cryptocurrencies.
23. Online Drug Trafficking
Online Drug Trafficking is a crime of selling, transporting, or illegally importing unlawful controlled substances, such as heroin, cocaine, marijuana, or other illegal drugs using electronic means.
24. Espionage
Espionage is the act or practice of obtaining data and information without the permission and knowledge of the owner.
How to file a Cybercrime complaint online in India?
A cybercrime complaint can be filed using the National Crime Reporting Portal of India .
Website link is – https://cybercrime.gov.in/
National Cyber Crime Reporting Portal of India
This portal is an initiative of the Government of India to facilitate victims/ complainants to report cybercrime complaints online.
This portal caters for all types of cybercrime complaints including complaints pertaining to
- online Child Pornography (CP),
- Child Sexual Abuse Material (CSAM),
- sexually explicit content such as Rape/Gang Rape (CP/RGR) content and
- other cybercrimes such as mobile crimes, online and social media crimes, online financial frauds, ransomware, hacking, cryptocurrency crimes and online cyber trafficking.
The portal also provides an option of reporting an anonymous complaint about reporting online Child Pornography (CP) or sexually explicit content such as Rape/Gang Rape (RGR) content.
Cybercrime Helpline Number
The Cyber Crime Helpline Number is 155260.
Indian Computer Emergency Response Team (CERT-IN or ICERT)
The Indian Computer Emergency Response Team ( CERT-IN or ICERT ) is an office within the Ministry of Electronics and Information Technology of the Government of India.
CERT-In is the national nodal agency for responding to computer security incidents as and when they occur. CERT-In is operational since January 2004.
CERT-In has been designated to serve as the national agency to perform the following functions in the area of cyber security:
- Collection, analysis and dissemination of information on cyber incidents.
- Forecast and alerts of cyber security incidents.
- Emergency measures for handling cyber security incidents.
- Coordination of cyber incident response activities.
- Issue guidelines, advisories, vulnerability notes and whitepapers relating to information security practices, procedures, prevention, response and reporting of cyber incidents.
- Such other functions relating to cyber security may be prescribed.
CERT-IN has overlapping responsibilities with other agencies such as National Critical Information Infrastructure Protection Centre (NCIIPC) .
Cyber Laws in India
Information Technology Act 2000 (IT Act 2000) is the main law connected with cyber security in India.
Indian Penal Code, 1860 is also used to book criminals connected with cybercrimes.
India also has a cyber security policy .
- eSIM: All you need to know
- Cyberwarfare

Top 10 Best-Selling ClearIAS Courses
Upsc prelims cum mains (pcm) gs course: unbeatable batch 2025 (online), rs.75000 rs.29000, upsc prelims test series (pts) 2025 (online), rs.9999 rs.4999, upsc mains test series (mts) (online), rs.19999 rs.9999, csat course 2025 (online), current affairs course 2025: important news & analysis (online), ncert foundation course (online), essay writing course for upsc cse (online), ethics course for upsc cse (online), fight back: repeaters program with daily tests (online or offline), rs.55000 rs.25000.
About Alex Andrews George
Alex Andrews George is a mentor, author, and social entrepreneur. Alex is the founder of ClearIAS and one of the expert Civil Service Exam Trainers in India.
He is the author of many best-seller books like 'Important Judgments that transformed India' and 'Important Acts that transformed India'.
A trusted mentor and pioneer in online training , Alex's guidance, strategies, study-materials, and mock-exams have helped many aspirants to become IAS, IPS, and IFS officers.
Reader Interactions
December 4, 2021 at 12:15 pm
How can one enroll for the mains course
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Don’t lose out without playing the right game!
Follow the ClearIAS Prelims cum Mains (PCM) Integrated Approach.
Join ClearIAS PCM Course Now
UPSC Online Preparation
- Union Public Service Commission (UPSC)
- Indian Administrative Service (IAS)
- Indian Police Service (IPS)
- IAS Exam Eligibility
- UPSC Free Study Materials
- UPSC Exam Guidance
- UPSC Prelims Test Series
- UPSC Syllabus
- UPSC Online
- UPSC Prelims
- UPSC Interview
- UPSC Toppers
- UPSC Previous Year Qns
- UPSC Age Calculator
- UPSC Calendar 2024
- About ClearIAS
- ClearIAS Programs
- ClearIAS Fee Structure
- IAS Coaching
- UPSC Coaching
- UPSC Online Coaching
- ClearIAS Blog
- Important Updates
- Announcements
- Book Review
- ClearIAS App
- Work with us
- Advertise with us
- Privacy Policy
- Terms and Conditions
- Talk to Your Mentor
Featured on

and many more...
ClearIAS Programs: Admissions Open
Thank You 🙌
UPSC CSE 2025: Study Plan
Subscribe ClearIAS YouTube Channel

Get free study materials. Don’t miss ClearIAS updates.
Subscribe Now
Download Self-Study Plan

Analyse Your Performance and Track Your Progress
Download Study Plan
IAS/IPS/IFS Online Coaching: Target CSE 2025
Cover the entire syllabus of UPSC CSE Prelims and Mains systematically.
Cyber Security Essay for Students and Children
Cyber security essay.
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today’s world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data. Cybersecurity is important because not only it helps to secure information but also our system from virus attack. After the U.S.A. and China, India has the highest number of internet users.

Cyber Threats
It can be further classified into 2 types. Cybercrime – against individuals, corporates, etc.and Cyberwarfare – against a state.
Cyber Crime
Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime. They exploit the weaknesses in the software and hardware design through the use of malware. Hacking is a common way of piercing the defenses of protected computer systems and interfering with their functioning. Identity theft is also common.
Cybercrimes may occur directly i.e, targeting the computers directly by spreading computer viruses. Other forms include DoS attack. It is an attempt to make a machine or network resource unavailable to its intended users. It suspends services of a host connected to the internet which may be temporary or permanent.
Malware is a software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It usually appears in the form of code, scripts, active content, and other software. ‘Malware’ refers to a variety of forms of hostile or intrusive software, for example, Trojan Horses, rootkits, worms, adware, etc.
Another way of committing cybercrime is independent of the Computer Network or Device. It includes Economic frauds. It is done to destabilize the economy of a country, attack on banking security and transaction system, extract money through fraud, acquisition of credit/debit card data, financial theft, etc.
Hinder the operations of a website or service through data alteration, data destruction. Others include using obscene content to humiliate girls and harm their reputation, Spreading pornography, threatening e-mail, assuming a fake identity, virtual impersonation. Nowadays misuse of social media in creating intolerance, instigating communal violence and inciting riots is happening a lot.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Warfare
Snowden revelations have shown that Cyberspace could become the theatre of warfare in the 21st century. Future wars will not be like traditional wars which are fought on land, water or air. when any state initiates the use of internet-based invisible force as an instrument of state policy to fight against another nation, it is called cyberwar’.
It includes hacking of vital information, important webpages, strategic controls, and intelligence. In December 2014 the cyberattack a six-month-long cyberattack on the German parliament for which the Sofacy Group is suspected. Another example 2008 cyberattack on US Military computers. Since these cyber-attacks, the issue of cyber warfare has assumed urgency in the global media.
Inexpensive Cybersecurity Measures
- The simplest thing you can do to up your security and rest easy at night knowing your data is safe is to change your passwords.
- You should use a password manager tool like LastPass, Dashlane, or Sticky Password to keep track of everything for you. These applications help you to use unique, secure passwords for every site you need while also keeping track of all of them for you.
- An easy way for an attacker to gain access to your network is to use old credentials that have fallen by the wayside. Hence delete unused accounts.
- Enabling two-factor authentication to add some extra security to your logins. An extra layer of security that makes it harder for an attacker to get into your accounts.
- Keep your Softwares up to date.
Today due to high internet penetration, cybersecurity is one of the biggest need of the world as cybersecurity threats are very dangerous to the country’s security. Not only the government but also the citizens should spread awareness among the people to always update your system and network security settings and to the use proper anti-virus so that your system and network security settings stay virus and malware-free.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

- IAS Preparation
- UPSC Preparation Strategy
- Cyber Crime
Cybercrime: Notes for UPSC GS-III
Cybercrime is a crime that involves a computer and a network. The computer may have been used to commit the crime and in many cases, it is also the target. Cybercrime may threaten a person or a nation’s security and financial health.
Cybercrime is a topic featured in the GS-III section of the IAS Exam . Candidates attempting the exam will find the details given in the article to be of immense use.
|
|
Definition of Cybercrime
Any offenses committed against individuals or groups of individuals to harm the reputation or cause physical or mental trauma through electronic means can be defined as Cybercrime. Electronic means can include but are not limited to, the use of modern telecommunication networks such as the Internet (networks including chat rooms, emails, notice boards and groups) and mobile phones (Bluetooth/SMS/MMS).
To know more about India’s national cybersecurity policy , visit the linked article.
Why is Cybercrime considered a grave offense?
There are many privacy concerns surrounding cybercrime when sensitive information is intercepted and leaked to the public, legally or otherwise. Some of that information may include data about military deployments, internal government communications, and even private data about high-value individuals. Cybercrime is not confined to individuals alone. Internationally, both governmental and non-state actors engage in cybercrimes, including espionage, financial theft, and other cross-border crimes. Cybercrimes crossing international borders and involving the actions of at least one nation-state is sometimes referred to as cyberwarfare.
In 2018, a study by Center for Strategic and International Studies (CSIS), in partnership with McAfee, a leading cybersecurity firm concludes that close to $600 billion, nearly one percent of global GDP, is lost to cybercrime each year.
Candidates can check out the relevant links given below to prepare for the upcoming exams even better-
Laws against Cybercrime in India
Ever since the introduction of cyber laws in India, the Information Technology Act (IT Act) 2000 covers different types of crimes under cyber law in India. The following types of cybercrimes are covered under the IT Act 2000.
- Identity theft – Identity theft is defined as theft of personnel information of an individual to avail financial services or steal the financial assets themselves.
- Cyberterrorism – Cyberterrorism is committed with the purpose of causing grievous harm or extortion of any kind subjected towards a person, groups of individuals, or governments.
- Cyberbullying – Cyberbullying is the act of intimidating, harassment, defaming, or any other form of mental degradation through the use of electronic means or modes such as social media.
- Hacking – Access of information through fraudulent or unethical means is known as hacking. This is the most common form of cybercrime know to the general public.
- Defamation – While every individual has his or her right to speech on internet platforms as well, but if their statements cross a line and harm the reputation of any individual or organization, then they can be charged with the Defamation Law.
- Trade Secrets – Internet organization spends a lot of their time and money in developing software, applications, and tools and rely on Cyber Laws to protect their data and trade secrets against theft; doing which is a punishable offense.
- Freedom of Speech – When it comes to the internet, there is a very thin line between freedom of speech and being a cyber-offender. As freedom of speech enables individuals to speak their mind, cyber law refrains obscenity and crassness over the web.
- Harassment and Stalking – Harassment and stalking are prohibited over internet platforms as well. Cyber laws protect the victims and prosecute the offender against this offense.
IT Act, 2000 went through amendments under the Indian Penal Code in the year 2008. These were made in light of the laws on cybercrime – IT Act, 2000 by way of the IT Act, 2008. They were enforced at the beginning of 2009 to strengthen the cybersecurity laws.
Cybercrime – UPSC Notes:- Download PDF Here
Frequently Asked Questions about Cybercrime
What are examples of cyber crimes, what are types of cybercrime.
For more UPSC- related preparation articles visit the links given in the table below. Candidates can visit the UPSC Syllabus page to get a general idea of the UPSC exams.
Related Links

| IAS General Studies Notes Links | |
Leave a Comment Cancel reply
Your Mobile number and Email id will not be published. Required fields are marked *
Request OTP on Voice Call
Post My Comment
IAS 2024 - Your dream can come true!
Download the ultimate guide to upsc cse preparation, register with byju's & download free pdfs, register with byju's & watch live videos.
Home — Essay Samples — Law, Crime & Punishment — Cyber Crimes — Cyber Crimes and Cyber Security in Modern World
Cyber Crimes and Cyber Security in Modern World
- Categories: Cyber Crimes Cyber Security
About this sample

Words: 1481 |
Published: Aug 14, 2018
Words: 1481 | Pages: 3 | 8 min read
Table of contents
Disaster recovery, network security, cyber attacks, website defacement.
- Identification, authentication & authorization of the user.
- Cryptography.
Flooding Services

Cite this Essay
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Prof Ernest (PhD)
Verified writer
- Expert in: Law, Crime & Punishment Information Science and Technology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
3 pages / 1254 words
2 pages / 947 words
3 pages / 1529 words
1 pages / 1357 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online

Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Cyber Crimes
Lee, S. (2017). Encrypted Messaging: Keeping Your Conversations Secure. Security Boulevard.Smirnoff, V., & Turner, S. (2019). Symmetric Encryption: Definition, Types, and Examples. SecurityTrails.Almeida, R. (2019). Asymmetric [...]
In our increasingly interconnected world, where technology is deeply woven into the fabric of our daily lives, the specter of computer threats looms large. From malware attacks to hacking and data breaches, the digital landscape [...]
Cybersecurity has become a very familiar term that has drawn increasing awareness of the danger of leaving cybercrimes unpunished. Because the world is moving more toward online trading and e-commerce, and basically living [...]
There are myriad ways for the bad guys to get your information and use it for all sorts of nefarious purposes — mainly, stealing your money, althoughoccasionally for other kinds of fraud or to cover their tracks when committing [...]
The problem of preventing cybercrime on an international scale has received considerable attention from many different countries. This essay analyzes cybercrime law. It aims to review past legislation and how it affected the [...]
A popular controversial issue today is whether children who are at risk for abuse remain with their families or not. Many people feel differently about this issue. Some people feel that it would be best for the children to [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free

- Classroom Programme
- Interview Guidance
- Online Programme
- Drishti Store
- My Bookmarks
- My Progress
- Change Password
- From The Editor's Desk
- How To Use The New Website
- Help Centre
Achievers Corner
- Topper's Interview
- About Civil Services
- UPSC Prelims Syllabus
- GS Prelims Strategy
- Prelims Analysis
- GS Paper-I (Year Wise)
- GS Paper-I (Subject Wise)
- CSAT Strategy
- Previous Years Papers
- Practice Quiz
- Weekly Revision MCQs
- 60 Steps To Prelims
- Prelims Refresher Programme 2020
Mains & Interview
- Mains GS Syllabus
- Mains GS Strategy
- Mains Answer Writing Practice
- Essay Strategy
- Fodder For Essay
- Model Essays
- Drishti Essay Competition
- Ethics Strategy
- Ethics Case Studies
- Ethics Discussion
- Ethics Previous Years Q&As
- Papers By Years
- Papers By Subject
- Be MAINS Ready
- Awake Mains Examination 2020
- Interview Strategy
- Interview Guidance Programme
Current Affairs
- Daily News & Editorial
- Daily CA MCQs
- Sansad TV Discussions
- Monthly CA Consolidation
- Monthly Editorial Consolidation
- Monthly MCQ Consolidation
Drishti Specials
- To The Point
- Important Institutions
- Learning Through Maps
- PRS Capsule
- Summary Of Reports
- Gist Of Economic Survey
Study Material
- NCERT Books
- NIOS Study Material
- IGNOU Study Material
- Yojana & Kurukshetra
- Chhatisgarh
- Uttar Pradesh
- Madhya Pradesh
Test Series
- UPSC Prelims Test Series
- UPSC Mains Test Series
- UPPCS Prelims Test Series
- UPPCS Mains Test Series
- BPSC Prelims Test Series
- RAS/RTS Prelims Test Series
- Daily Editorial Analysis
- YouTube PDF Downloads
- Strategy By Toppers
- Ethics - Definition & Concepts
- Mastering Mains Answer Writing
- Places in News
- UPSC Mock Interview
- PCS Mock Interview
- Interview Insights
- Prelims 2019
- Product Promos
- Daily Updates
Make Your Note
Cyber Crime
- 28 Jul 2023
- GS Paper - 2
- Government Policies & Interventions
- GS Paper - 3
- Cyber Security
- Cyber Warfare
- Challenges to Internal Security Through Communication Networks
For Prelims: Cyber Crime , Seventh Schedule of the Constitution , Internet of Things , Crypto-Currency, Massive Open Online Courses.
For Mains: Cyber Crime, Related Challenges and Measures to Deal with it.
Source: PIB
Why in News?
The Indian government has taken significant steps to strengthen the mechanism for dealing with Cybercrimes in a comprehensive and coordinated manner.
What is Cyber Crime?
- Cybercrimes fall under State subjects as per the Seventh Schedule of the Constitution of India.
- It involves illegal or unauthorized activities that exploit technology to commit various forms of crimes.
- Cybercrime covers a wide range of offenses and can affect individuals, organizations, and even governments.
- Distributed Denial-of-Service (DDoS) Attacks: These are used to make an online service unavailable and take the network down by overwhelming the site with traffic from a variety of sources.
- Botnets: Botnets are networks from compromised computers that are controlled externally by remote hackers. The remote hackers then send spam or attack other computers through these botnets.
- Identity Theft: This cybercrime occurs when a criminal gains access to a user’s personal information or confidential information and then tries to tarnish reputation or seek a ransom.
- Cyberstalking: This kind of cybercrime involves online harassment where the user is subjected to a plethora of online messages and emails. Typically, cyberstalks use social media, websites, and search engines to intimidate a user and instill fear.
- Phishing: It is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message.
What are the Challenges Related to Cyber Security in India?
- Post liberalisation, the Information Technology (IT), electricity and telecom sector have witnessed large investments by the private sector.
- Operators are not investing in protective infrastructure , rather they are focused on the profitable infrastructure only, because they think investment on cyber-attack preparedness may not generate good profits.
- All operators are focused on profits, and do not want to invest in infrastructure that will not generate profits (i.e. protective infrastructure).
- There is no separate procedural code for the investigation of cyber or computer-related offences.
- Most cybercrimes are trans-national in nature. The collection of evidence from foreign territories is not only a difficult but also a tardy process.
- In the last couple of years, India has traversed on the path of digitalizing its various economic factors and has carved a niche for itself successfully.
- The latest technologies like 5G and Internet of Things (IoT) will increase the coverage of the internet-connected ecosystem.
- With the advent of digitalisation, paramount consumer and citizen data will be stored in digital format and transactions are likely to be carried out online which makes India a breeding ground for potential hackers and cyber-criminals.
- Offenses related to crypto-currency remain under-reported as the capacity to solve such crimes remains limited.
- Although most State cyber labs are capable of analysing hard disks and mobile phones, they are yet to be recognized as 'Examiners of Electronic Evidence' (by the central government). Until then, they cannot provide expert opinions on electronic data.
What Measures Can be Taken to Tackle Cyber Crimes in India?
- The governments at various levels need to conduct massive cybersecurity awareness campaigns, regarding Cyber frauds , use strong, unique passwords, being careful using public wi-fi, etc.
- Cyber insurance provides financial coverage against losses resulting from cyber incidents and by mitigating the financial impact of these incidents, organizations can recover more quickly and continue their operations.
- In this context, the European Union's General Data Protection Regulation and India’s Personal Data Protection Bill, 2019 are steps in the right direction.
- This mechanism would bind all parties and enable law enforcers to act quickly and safeguard citizens and businesses from a fast-growing menace.
- In this context, the Indian Cyber Crime Coordination Centre will assist in centralizing cybersecurity investigations , prioritize the development of response tools and bring together private companies to contain the menace.
What are the Government Initiatives to Cope with Cyber Crimes in India?
- Indian Cyber Crime Coordination Centre (I4C): This center coordinates efforts to tackle all types of cyber-crimes across the country.
- National Cyber Forensic Laboratory : It provides early-stage cyber forensic assistance to Investigating Officers of all State/UT Police through both online and offline modes.
- CyTrain Portal: A Massive Open Online Courses (MOOC) platform for capacity building of police officers, judicial officers, and prosecutors through online courses on critical aspects of cyber-crime investigation, forensics, and prosecution.
- National Cyber Crime Reporting Portal: A platform where the public can report incidents of cyber-crimes, with a special focus on crimes against women and children.
- Citizen Financial Cyber Fraud Reporting and Management System: It is a system for immediate reporting of financial frauds and assistance in lodging online cyber complaints through a toll-free helpline.
- Cybercrime Prevention against Women and Children (CCPWC) Scheme: Financial assistance provided to States/UTs for developing capabilities of Law Enforcement Agencies in investigating cyber-crimes.
- Joint Cyber Coordination Teams: Constituted to enhance coordination among Law Enforcement Agencies of States/UTs, particularly in areas with multi-jurisdictional issues related to cyber-crimes.
- Central Assistance for Modernization of Police: Providing financial support to States/UTs for acquiring modern weaponry, advanced communication/forensic equipment, and cyber policing equipment.
- It is of critical importance to ensure global cooperation through information sharing and strengthening joint efforts in cybersecurity research and development as most cyberattacks originate from beyond the borders.
- It is important for the corporates or the respective government departments to find the gaps in their organisations and address those gaps and create a layered security system, wherein security threat intelligence sharing is happening between different layers.


IMAGES
VIDEO
COMMENTS
500+ Words Essay on Cyber Crime. Cyber Crime Essay- Everybody thinks that only stealing someone's private data is Cyber Crime.But in defining terms we can say that 'Cyber Crime refers to the use of an electronic device (computer, laptop, etc.) for stealing someone's data or trying to harm them using a computer.
cybercrime, the use of a computer as an instrument to further illegal ends, such as committing fraud, trafficking in child pornography and intellectual property, stealing identities, or violating privacy. Cybercrime, especially through the Internet, has grown in importance as the computer has become central to commerce, entertainment, and ...
There are four main categories of cybercrime, according to a popular definition—hacking, money, privacy, and cyber terrorism. 500 Words Essay on Cyber Crime. Cybercrime is a type of crime in which illegal activities are carried out online or using computers. Cybercrime comes in a variety of forms which involves harassing online users.
Cybercrime encompasses a wide range of criminal activities that are carried out using digital devices and/or networks. These crimes involve the use of technology to commit fraud, identity theft, data breaches, computer viruses, scams, and expanded upon in other malicious acts. Cybercriminals exploit vulnerabilities in computer systems and ...
Essay on Cyber Crime. Cyber crime is the most discussed issue of the 21st century. The technology sector world wide is witnessing a boom in the consumer of smartphones and the internet which is raising concerns with regard to the privacy and security of the users. Owing to this reason, it is highly essential for all the users to know about ...
Essay on Cybercrime in 100 Words. Cybercrime involves illegal activities like hacking, ransomware, cyberbullying, online fraud, etc. People who are involved in cybercrime or any similar activities are called hackers, scammers or fraudsters. Cybercrime leads to financial loss for individuals who have fallen victim to one.
Cybercrime, also called computer crime, is any illegal activity that involves a computer or network-connected device, such as a mobile phone. The Department of Justice divides cybercrime into three categories: crimes in which the computing device is the target, for example, to gain network access; crimes in which the computer is used as a ...
Introduction to Cyber Crime. In the digital age, our reliance on technology has given rise to a new form of criminal activity known as cyber crime. This term encapsulates any illegal activity that utilizes a computer as its primary means of commission. Cyber crime has become a critical concern due to its widespread impact, affecting individuals ...
Cyber Crime Essay: A crime that involves a network and a computer is known as computer-oriented crime or cybercrime. Such a crime affects the security of everything, might be a person, institution or even a nation. The computer is either used to commit a crime or is usually a target. Things that are hacked include information, […]
Cyber crime evolved since 1990 when computers and networks came in to being. The types of attacks gradually grew from "Morris code worm" in 1997 to "Torjan" in 2004 and to "Ransom ware " attack in 2013. When computers and networks came into being in the 1990s, hacking was done basically to get more information about the systems.
Effects of Cyber Crime on Social Media. 2 pages / 933 words. The issue of cyber Crime has risen rapidly as a result of increased access to computers in the recent years compared to the past. Cyber Crime refers to criminal activities, which are carried out by the use of computers or the internet.
Cybercrime is defined as crimes committed on the internet using the computer as either a tool or a targeted victim by hacker or cracker. while we growth on fast data manipulating system in this technology era, Unfortunately, some of the skilled professionals use this ability in a bad way by harming society, by finding the vulnerabilities in the ...
Cybercrime refers to illegal activities carried out using computers and the Internet. These crimes can range from stealing personal information and financial fraud to hacking and spreading malicious software. Cybercrime poses significant risks to individuals, businesses, and governments worldwide. Most of the time, people who do cybercrime ...
116 CyberCrime Topics & Essay Samples. Updated: Mar 2nd, 2024. 9 min. If you are writing a cybercrime essay, our team prepared this article just for you. Here, you will find 115 unique topics for any type of paper. Table of Contents. These days, people are asking more and more questions about cybercrime. The most straightforward definition is ...
Cyber crime is a general term describing the myriad of criminal activities carried out using a computer, network, or another set of digital devices. Consider cyber crime the umbrella over the vast range of illegal activities that cyber criminals commit. These include hacking, phishing, identity theft, ransomware, and malware attacks, among many ...
Abstract. Cyber Crime is a common phenomenon in the world. Cyber Crime is that group of activities made by the people by creating disturbance in network, stealing others important and private data ...
Definition of Cyber Crime. Cybercrime may be defined as "Any unlawful act where computer or communication device or computer network is used to commit or facilitate the commission of a crime". Don't miss: UPSC Prelims Test Series 2025. ⇒ Download Timetable.
Cyber Security Essay. Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today's world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software.
Speer (2000) defines cybercrime as activities in which computers, telephones, cellular equipment and other technological devices are used for illicit purposes. Most often cybercrime is done for personal information or financial gain. As a result, business organization, government agencies, online users and individuals become victims of ...
Cyber Crime Is a Serious. PAGES 8 WORDS 2431. These "stepping stone" computes can be located anywhee in the physical wold because eal-space is ielevant to activity in cybespace (Benne, 379)." The use of stepping stones can make it difficult fo law enfocement to find whee an attack actually oiginated.
Cybercrime: Notes for UPSC GS-III. Cybercrime is a crime that involves a computer and a network. The computer may have been used to commit the crime and in many cases, it is also the target. Cybercrime may threaten a person or a nation's security and financial health. Cybercrime is a topic featured in the GS-III section of the IAS Exam.
Cybersecurity is a process to save the networks, computer programs, and data from the illegal access or users that aim to access users data for personal uses and benefits. For the protection of data, many organizations develop a software. This software help to protect the data and information. Cybersecurity playing a big role in developing a ...
What is Cyber Crime? About: Cybercrime is defined as a crime where a computer is the object of the crime or is used as a tool to commit an offense. Cybercrimes fall under State subjects as per the Seventh Schedule of the Constitution of India.