You are using an outdated browser. Please upgrade your browser to improve your experience.
Your browser does not support JavaScript. Please turn it on for the best experience.

Configuration Guide on Dynamic VLAN with the VLAN Assignment function of RADIUS
OC200 , OC300 , Omada Software Controller , Omada Cloud-Based Controller
Recent updates may have expanded access to feature(s) discussed in this FAQ. Visit your product's support page, select the correct hardware version for your device and check either the Datasheet or the firmware section for the latest improvements added to your product.
With the VLAN Assignment feature of RADIUS, the Omada SDN solution can put clients authenticated by different accounts to the corresponding VLANs. In this way, clients will obtain IP addresses from different VLANs, and you don't have to create many SSIDs bound with different VLANs for wireless networks, or bind the PVIDs of the switch ports to specific VLANs for wired networks.
To achieve the above features, you will need the Omada SDN Controller, EAP for wireless assignment, JetStream Switch for wired assignment, and an external RADIUS server. In this article, we will share the configuration guide for below network topology.
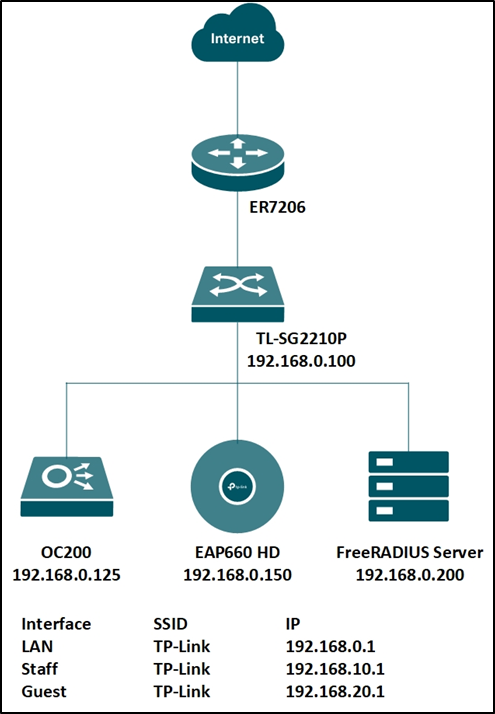
Step 1. Set up the RADIUS server.
Here we run a FreeRADIUS ® server on a Linux server. For more information on installation and configuration, please refer to the official website: https://freeradius.org/
First, edit the “ clients.conf ” file, set the client IP address as “192.168.0.0/24” and the password as “tplink”.
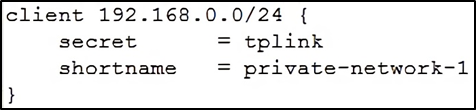
Next, edit the “ users ” file, create two accounts “test10” and “test20” in VLAN10 and VLAN20, respectively.
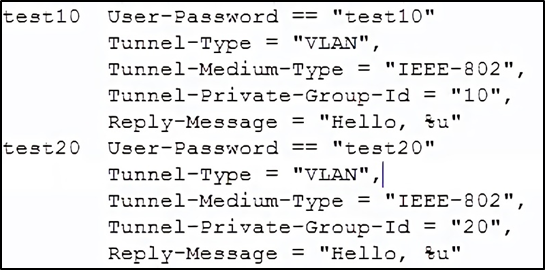
You may also edit the “ eap.conf ” to modify the EAP type for WPA-Enterprise. After configuration, run the RADIUS server to listen for access requests.
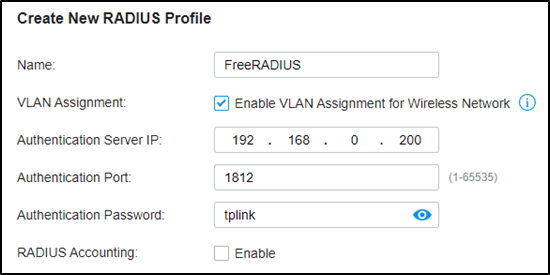
Step 2. Create the RADIUS profile.
Go to Authentication --- RADIUS Profile, create a new profile bound with the RADIUS server, and check “Enable VLAN Assignment for Wireless Network” to assign VLANs for wireless clients.
Step 3. Create more VLAN for VLAN assignments.
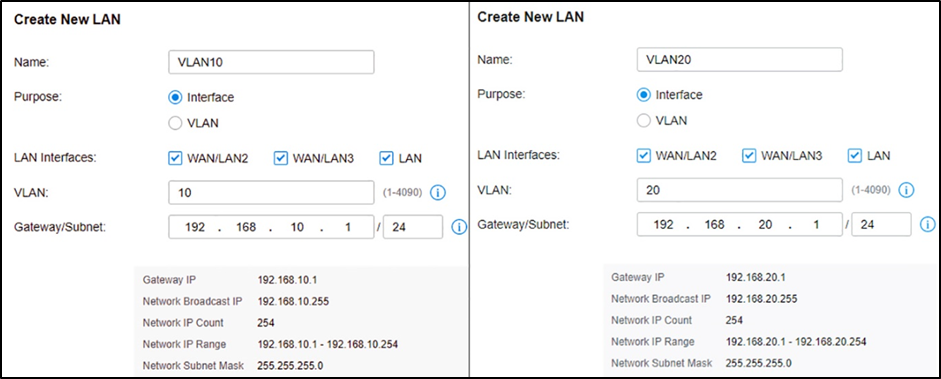
Assuming all Omada devices have been adopted by the controller, go to Settings --- Wired Networks --- LAN, and create two interfaces with VLAN10 and VLAN20.
Step 4. VLAN assignment for wireless networks.
Go to Settings – Wireless Networks, and create a new SSID with WPA-Enterprise as below. For differences between WPA-Personal and WPA-Enterprise, please refer to FAQ500 .
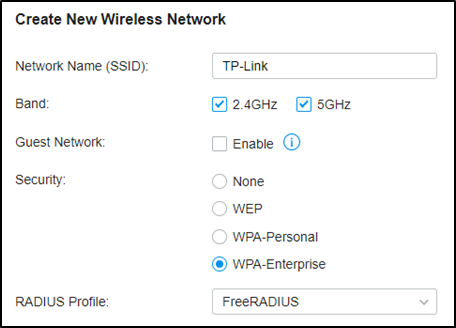
When connecting your client to the SSID, you will be asked to choose the authentication type of WPA-Enterprise, and enter the account username and password. After successfully authenticating with account “test10”, the client will obtain an IP address from VLAN10, while with account “test20”, it will get that from VLAN20.
Step 5. VLAN assignment for wired networks.
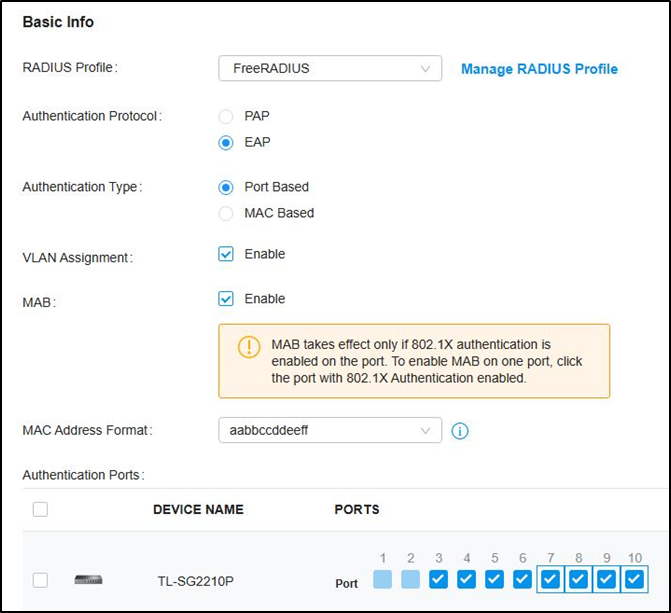
Go to Authentication --- 802.1X and enable the feature, select Authentication Type as “Port Based”, enable “VLAN Assignment” and check the Ports to be authenticated according to your requirements.
Not to click the ports twice to enable MAB for them.
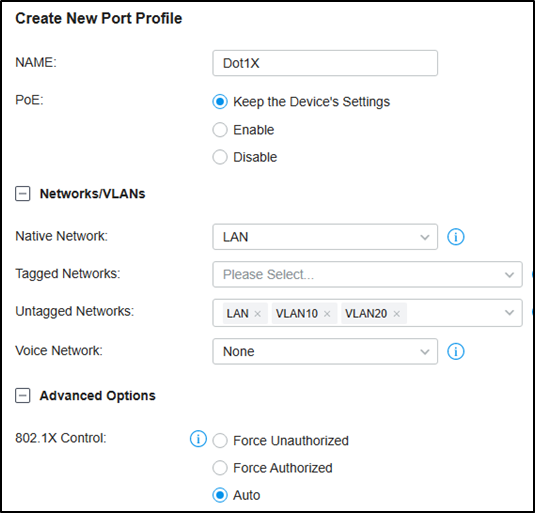
Then go to Wired Networks --- LAN --- Profile, create a new port profile, add VLAN10 and VLAN20 to untagged networks, and make sure the 802.1X Control mode is Auto.
Then Go to Devices, click your switch, go to Ports, check the authentication ports, and batch edit to change the port profile to the one created just now.
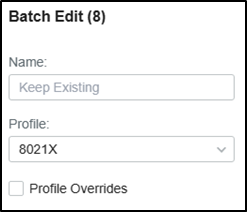
For 802.1X authentication, you may need to run TP-Link 802.1X Client Software (click here to download) for authentication. Please refer to FAQ787 and Step 3. For detailed guidance.
Is this faq useful?
Your feedback helps improve this site.
What’s your concern with this article?
- Dissatisfied with product
- Too Complicated
- Confusing Title
- Does not apply to me
We'd love to get your feedback, please let us know how we can improve this content.
We appreciate your feedback. Click here to contact TP-Link technical support.
Recommend Products
Omada Cloud-Based Controller
Omada Software Controller

Omada Hardware Controller
TP-Link Community
Still need help? Search for answers, ask questions, and get help from TP-Link experts and other users around the world.
Visit the Community >
We have updated our Policies. Read Privacy Policy and Terms of Use here. This website uses cookies to improve website navigation, analyze online activities and have the best possible user experience on our website. You can object to the use of cookies at any time. You can find more information in our privacy policy .
Basic Cookies
These cookies are necessary for the website to function and cannot be deactivated in your systems.
accepted_local_switcher, tp_privacy_base, tp_privacy_marketing, tp_smb-select-product_scence, tp_smb-select-product_scenceSimple, tp_smb-select-product_userChoice, tp_smb-select-product_userChoiceSimple, tp_smb-select-product_userInfo, tp_smb-select-product_userInfoSimple, tp_top-banner, tp_popup-bottom, tp_popup-center, tp_popup-right-middle, tp_popup-right-bottom, tp_productCategoryType
__livechat, __lc2_cid, __lc2_cst, __lc_cid, __lc_cst, CASID
id, VISITOR_INFO1_LIVE, LOGIN_INFO, SIDCC, SAPISID, APISID, SSID, SID, YSC, __Secure-1PSID, __Secure-1PAPISID, __Secure-1PSIDCC, __Secure-3PSID, __Secure-3PAPISID, __Secure-3PSIDCC, 1P_JAR, AEC, NID, OTZ
Analysis and Marketing Cookies
Analysis cookies enable us to analyze your activities on our website in order to improve and adapt the functionality of our website.
The marketing cookies can be set through our website by our advertising partners in order to create a profile of your interests and to show you relevant advertisements on other websites.
Google Analytics & Google Tag Manager
_gid, _ga_<container-id>, _ga, _gat_gtag_<container-id>
Google Ads & DoubleClick
test_cookie, _gcl_au
cebsp_, _ce.s, _ce.clock_data, _ce.clock_event, cebs
OptanonConsent, _sctr, _cs_s, _hjFirstSeen, _hjAbsoluteSessionInProgress, _hjSessionUser_14, _fbp, ajs_anonymous_id, _hjSessionUser_<hotjar-id>, _uetsid, _schn, _uetvid, NEXT_LOCALE, _hjSession_14, _hjid, _cs_c, _scid, _hjAbsoluteSessionInProgress, _cs_id, _gcl_au, _ga, _gid, _hjIncludedInPageviewSample, _hjSession_<hotjar-id>, _hjIncludedInSessionSample_<hotjar-id>
lidc, AnalyticsSyncHistory, UserMatchHistory, bcookie, li_sugr, ln_or
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Regarding Dot1X dynamic VLAN assignment
I am trying to get 802.1X working for me. I want RADIUS server to dynamically assign VLANs to ports based on RADIUS reply attribute for particular user. I have an HP E2620 switch and a FreeRADIUS server. The supplicant is a Windows 8.1 machine
I referred to this document on freeradius website.
What I've done so far:
On FreeRADIUS I created a user with such parameters:
I also tried Tunnel-Pvt-Group-ID instead, but it doesn't work on FreeRADIUS, just barks at me (I saw this on resources for configuring on Microsoft NPS, one of these ) . Also I tried values "802", 802, 6 for tunnel medium type.
Also I tried to use actual VLAN name instead of VLAN-ID as Group ID value. Anyway its datatype is string.
I configured the HP switch to use this RADIUS server for AAA and set this up for port 10:
Port 10 also has untagged VLAN 150 assigned to it: vlan 150 untagged 10 . And I can't get rid of the static assignment
All VLANs listed above are present in switch's VLAN database.
Whenever I plug into this port it asks me for credentials; after I succeed with authentication it just sends me to VLAN150 and if I try to fail I get to VLAN200.
I enabled 802.1X authentication on Windows connection just like described here .
I tried enabling GVRP - it doesn't change anything
Diagnostic/show command output:
Static VLAN assignment for Port 10. VLAN 150 untagged
In show logging I see this:
show port-access authenticator output:
RADIUS user test:
This is what I saw in TCPdump on the RADIUS server. I was capturing outgoing UDP traffic with source port 1812. It's what my switch gets (if it does actually, not sure how to check that...)
After that I unplugged and plugged in the cable and did show debug buffer and here is the copy-paste of it . It's weird, nothing is said about any attributed related to VLAN.
What am I doing wrong?
I've read in a bunch of resources that if the RADIUS assigns a VLAN ID switch uses that in the first place. Then it falls back to Authorized VLAN configured for Port-Access Authenticator if authentication succeeds. If that is not present it assigns Untagged VLAN configured on the port. Why don't I get that behavior?
I kind of start to think the attribute Tunnel-Private-Group-Id is not supported on these switches. It seems every resource refers to Tunnel-Pvt-Group-Id instead (configuring on Microsoft). Too bad I don't have Windows Server to check.
Maybe it's firmware related? Didn't try to upgrade yet, I use RA_15_06_0009.swi and there's RA_15_14_0007.swi out there already
Just tried on a 3500yl-24G-PWR model and still doesn't work. So.. I'd guess, switches just don't get the config from the RADIUS server (or did I use incorrect attributes or operators?). How can I troubleshoot that?
- ieee-802.1x
- Do you have the port on vlan100 as tagged? – some_guy_long_gone Commented Sep 5, 2014 at 13:47
- Been a while since I played on HP switches, but it seems to me there should be a aaa port-access authenticator 10 auth-vid 150 statement as well. IIRC, this would tell the switch to use 150 for authenticated devices unless it gets a different value from RADIUS. Without this, I suspect it will just use the configured port value. Not posting as an answer because I am working off memory and it often fails nowadays. If it works, let me know and I will post as answer. – YLearn Commented Sep 5, 2014 at 15:21
- *legioxi, no the port is set to Untagged VLAN 150. *YLearn, I don't need it to assign a specific VLAN. I want it to assign a VLAN depending on what user authenticates. Auth-vid comes second in priority after RADIUS (which doesn't work). If no Auth-vid is set, then it does indeed choose configured untagged VLAN. – Alex Commented Sep 9, 2014 at 4:14
Your Answer
Sign up or log in, post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged switch vlan radius ieee-802.1x or ask your own question .
- Featured on Meta
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network...
- We spent a sprint addressing your requests — here’s how it went
Hot Network Questions
- Can a MicroSD card help speed up my Mini PC?
- Implementation of Euler-Maruyama numerical solver
- Histogram manipulation
- Table overflow with tabular
- Looking for title of old Star Trek TOS book where Spock is captured and gets earring
- Keyboard Ping Pong
- I am trying to calculate Albumin-Creatinine ratios for research, why is the result so high?
- Is it possible to replace the flat-top pins on flat pedals with ones that have a dome top?
- Does the damage from Thunderwave occur before or after the target is moved
- USB Data communication issue on a panelized pcba hardware test platform
- Any philosophical works that explicitly address the heat death of the Universe and its philosophical implications?
- Is a spirit summoned with the Find Greater Steed spell affected by the Divine Word spell?
- How to turn a sum into an integral?
- Does there exist a nontrivial "good" set?
- The meaning of "tarmac ticket"
- Why does Macbeth well deserve his name?
- Are there countries where only voters affected by a given policy get to vote on it?
- Does the proverb "having your cake and eating it too" imply hypocrisy?
- Confusion regarding "since" vs "for"
- o y u (or and or)
- Are there any reasons I shouldn't remove this odd nook from a basement room?
- Does physical reality exist without an observer?
- Accommodating whiteboard glare for low-vision student
- How should I deal with curves in new deck boards during installation?

Microsoft NPS as a RADIUS Server for WiFi Networks: Dynamic VLAN Assignment
Configuration Example Here’s an example of how to configure NPS to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the WLC or AP) by the authentication server (i.e.NPS) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to. The other elements that need to be returned by NPS are:
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
- Tunnel-PVT-Group-ID: <VLAN Number>
We’ll have a look at how we specify each of these attributes in an NPS policy. For our example, we’ll assign all ‘staff’ users to VLAN 10 and all ‘student’ users to VLAN 20. Here is an overview of what the network might look like (this is obviously very simplified, but gives an overview of the type of thing that might be achieved):
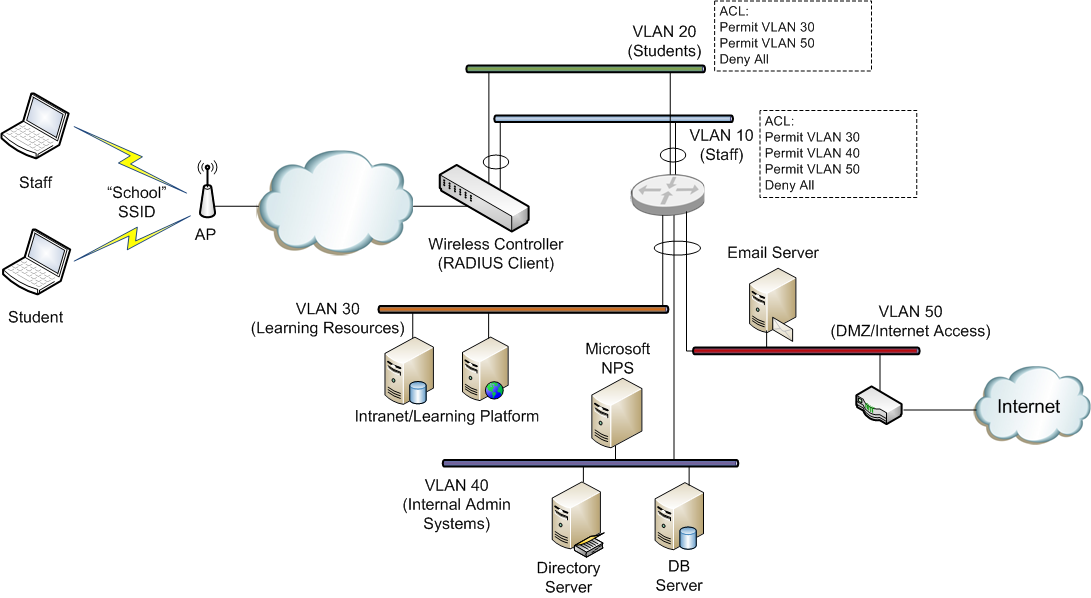
VLAN 10 has an ACL (access control list) that allows users on this VLAN to access all systems across the school network. The ACL would generally be configured on the layer 3 switch or router that interconnects the school VLANs) VLAN 20 has an ACL which only allow access to the learning system VLAN and the Internet related services. By studying the example above, you can see that if we can control a users VLAN assignment, based on their AD group membership, we can ensure that they only receive the network access to which they are entitled (purely via their AD group membership). Also, note that this is all being done on a single SSID (“School” in this case). Now we’ll take a look at how we achieve this using NPS. NPS Configuration To configure NPS to provide the VLAN assignments outlined above, we will create 2 policies within NPS:
- School Wireless – Staff (to assigned members of the staff AD group to VLAN 10)
- School Wireless – Students (to assign members of the students AD group to VLAN 20)
The screen-shots below outline the configuration required. Here is the policy summary screen within NPS. Note that when configuring multiple policies, the order of the policies is important. Policies are assessed top-down, so make sure the policies that need to be hit are enabled and above any disabled polices.
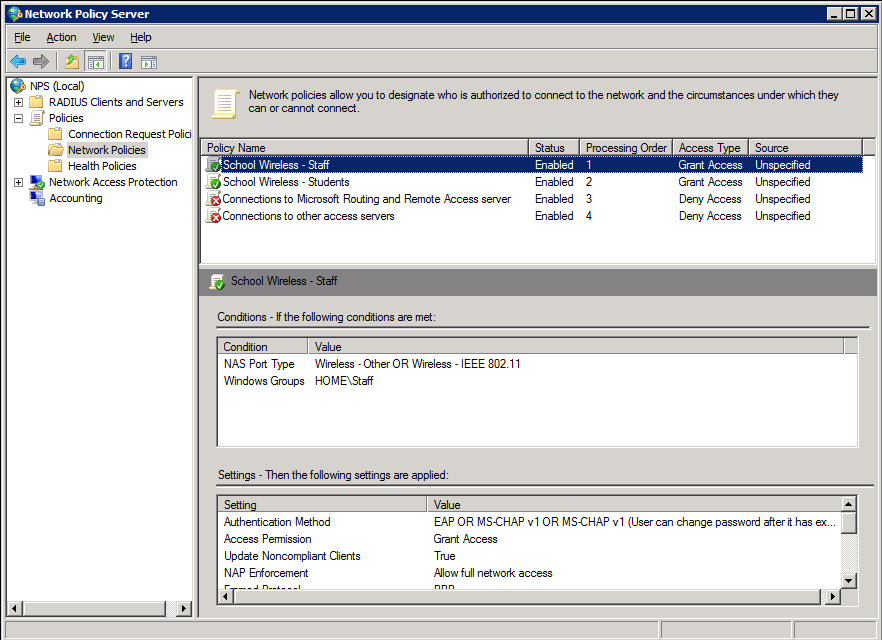
Staff Policy 1. Create the policy and enable it:
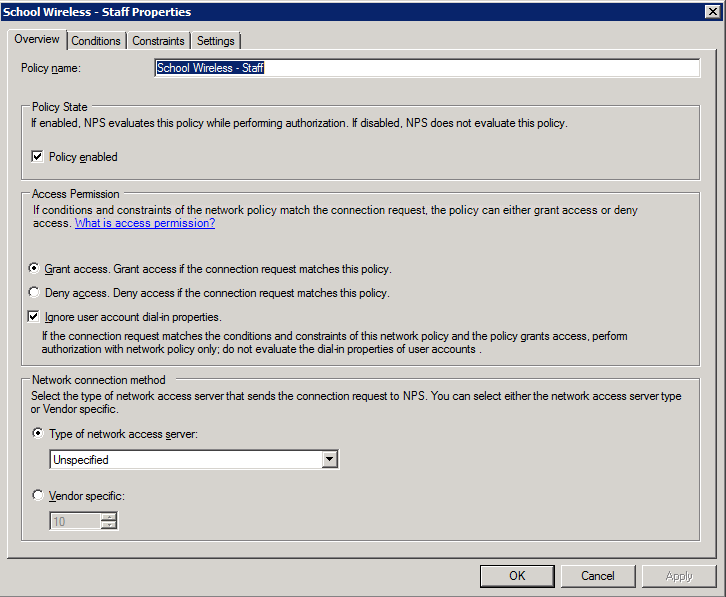
2. Add the NAS type and AD group membership conditions (must be members of the staff group):
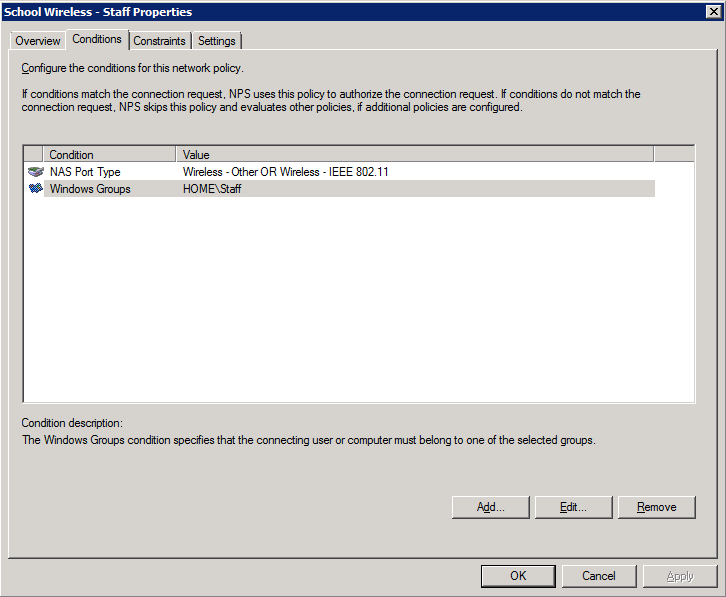
3. Select and configure an EAP type (note this may be PEAP or EAP-TLS – we’ve shown PEAP just as an example)
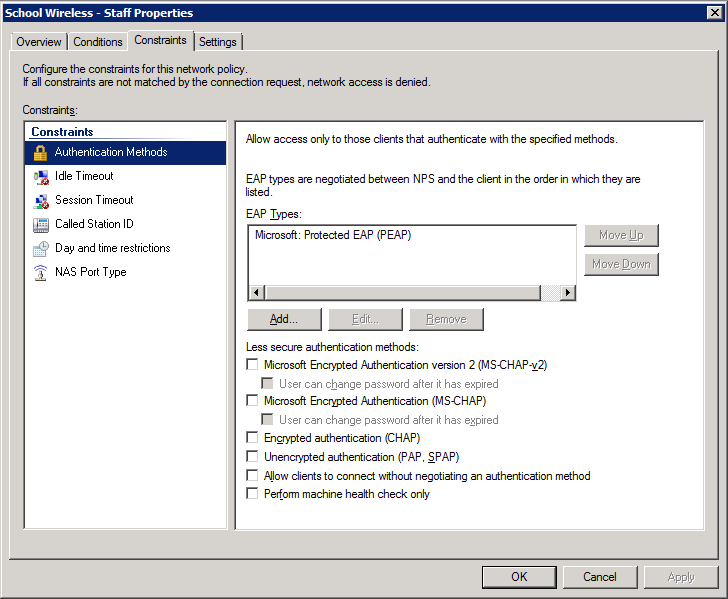
4. Configure the settings for this policy to assign any users which match this policy to VLAN 10:
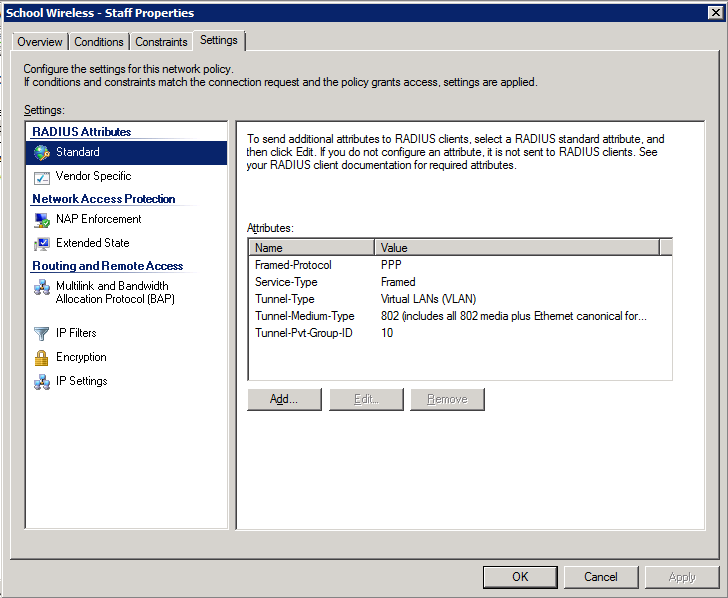
Students Policy 1. Create the policy and enable it:
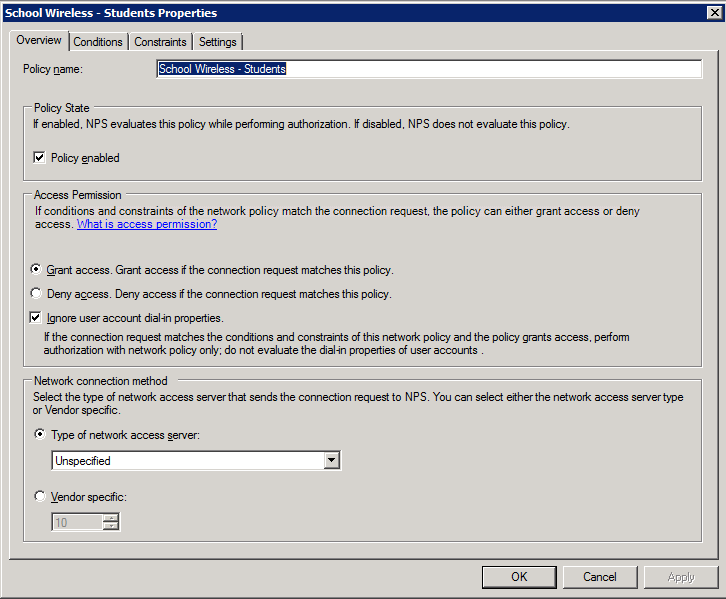
2. Add the NAS type and AD group membership conditions: (must be members of the students group to match this policy)
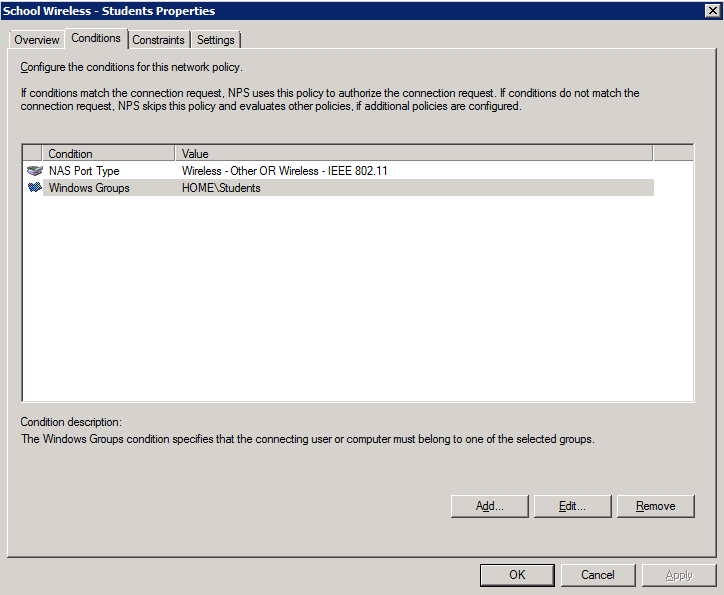
4. Configure the settings for this policy to assign any users which match this policy to VLAN 20:
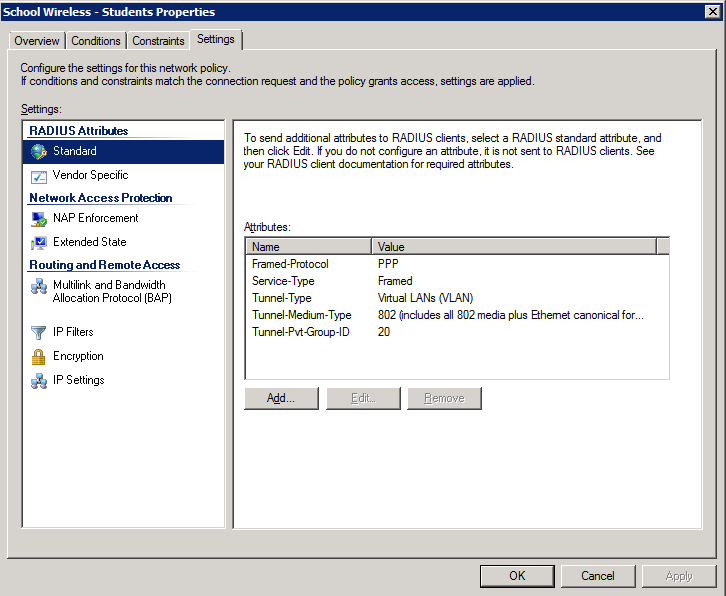
Once NPS has been configured with policies similar to those shown above, users can be dynamically assigned to an appropriate VLAN based on their AD group membership. As we’ve already discussed, this provides great benefits in reducing additional overheads associated with multiple SSIDs on a WiFi network. In addition, it simplifies user wireless management by allowing all users to be configured with a single wireless client profile, with their access being configured via Microsoft AD. One caveat to note when trying to use this technique is that all users must be using the same security mechanisms to join the SSID. For instance, all users must be using 802.1x (EAP) – you can’t have a mix of PSK & 802.1x authenticated devices on the same SSID. Generally, they should also be using the same WPA version (i.e. WPA or WPA2).
Related Articles
How to use openpath mobile pass (avigilon alta), integrate your existing network policy server (nps) infrastructure with azure ad multi-factor authentication, how to find out who the user profile disk belongs to terminal server rds, how to sign up and use chatgpt, sage 50 payroll – change database path, generate a report of all passwords for all cameras on your milestone xprotect vms., leave a reply cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Power by IT Capture
- Cisco Community
- Technology and Support
- Network Access Control
Dynamic Vlan Assignment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Report Inappropriate Content
Solved! Go to Solution.
- All forum topics
- Previous Topic

01-27-2013 05:01 AM
View solution in original post
01-17-2013 11:09 PM
01-27-2013 11:33 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
Log in to Community
Meraki Community
- Community Platform Help
- Contact Community Team
- Meraki Documentation
- Meraki DevNet Developer Hub
- Meraki System Status
- Technical Forums
802.1X /w Dynamic VLAN Assignment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Report Inappropriate Content
- All forum topics
- Previous Topic

- New July 8: Points Contest: Week 1 Roundup
- July 1: Recognizing the June 2024 Members of the Month
- July 1: The annual points contest is BACK and better than ever!
- Interfaces 232
- Layer 2 250
- Layer 3 181
- Community guidelines
- Cisco privacy
- Khoros privacy
- Terms of service
Log in to ask questions, share your expertise, or stay connected to content. Don’t have a login? Join now.

- Community Home
- Topic Thread
Wireless Access

- Discussion 121K
- Library 3.2K

Dynamic vlan Assignment using Radius attribute& filter ID
1. dynamic vlan assignment using radius attribute& filter id.
Hello Every one
i have one customer that require spacific business needs to achive it he want to make Dynamic vlan assinment in aruba controller after users Authenticated using dot1x via AD radius server ,and By using spacific Radius attribute like filter id returned to controller he want make dynamic vlan assignment based on this attribute and AD user group , is there any configuration guide ,step by step to achive this , i already do basic intgeration Aruba controller with AD and users can authenticated and have internet access , but i dont know how to achive this busness requirment
Best regards
2. RE: Dynamic vlan Assignment using Radius attribute& filter ID
You would need a policy engine like ClearPass to do that. Windows NPS server can authenticate and return radius attributes, but cannot combine AD group logic with another attribute to send back a third attribute.
3. RE: Dynamic vlan Assignment using Radius attribute& filter ID
But it already done in another palces
so dont care about AD groups
does it applicable with Filter ID only
4. RE: Dynamic vlan Assignment using Radius attribute& filter ID
Please see "configuring server derivation rules" on the page here: https://www.arubanetworks.com/techdocs/ArubaOS_6_5_4_X_Web_Help/Web_Help_Index.htm#ArubaFrameStyles/AAA_Servers/Server_Groups.htm%3FTocPath%3DArubaOS%2520User%2520Guide%2520Topics%7CAuthentication%2520Servers%7C_____5
New Best Answer

- Environmental Citizenship
- Support Services
- Contact Support
- Training & Certification
- Software Downloads
- Licensing Login
- Find a Partner
- Become a Partner
- Partner Ready for Networking
- Technology Partner Programs
- Privacy policy
- Terms of service
© Copyright 2024 Hewlett Packard Enterprise Development LP All Rights Reserved.
How To Configure NPS and Active Directory For Dynamic Radius based Vlan assignment
How Configure NPS and Active Directory For Dynamic Radius based Vlan assignment
==================================================================
This document is to describe the steps to configure NPS(network policy servicer)server with below use case
- Vlans need to be assigned based on different Radius group i.e Sales group to Vlan 10
Account group to Vlan 20.

3. Like these create as many groups required.
5. Give Username as xyz and click on OK

Click on properties of the created user xyz and click on Dial In tab.
Select Allow access and then press OK.

Click on Member Of tab.
Add domain users and the radius group by clicking on Add button

Adding group

Adding domain users

8.Press Ok . Now the user is part of the domain user and group .
Configuring NPS server
==================================
9.Click on Network Policy and click on New

10. Give policy name such as Vlan10_policy.Click on Next

11. Click on Add button.

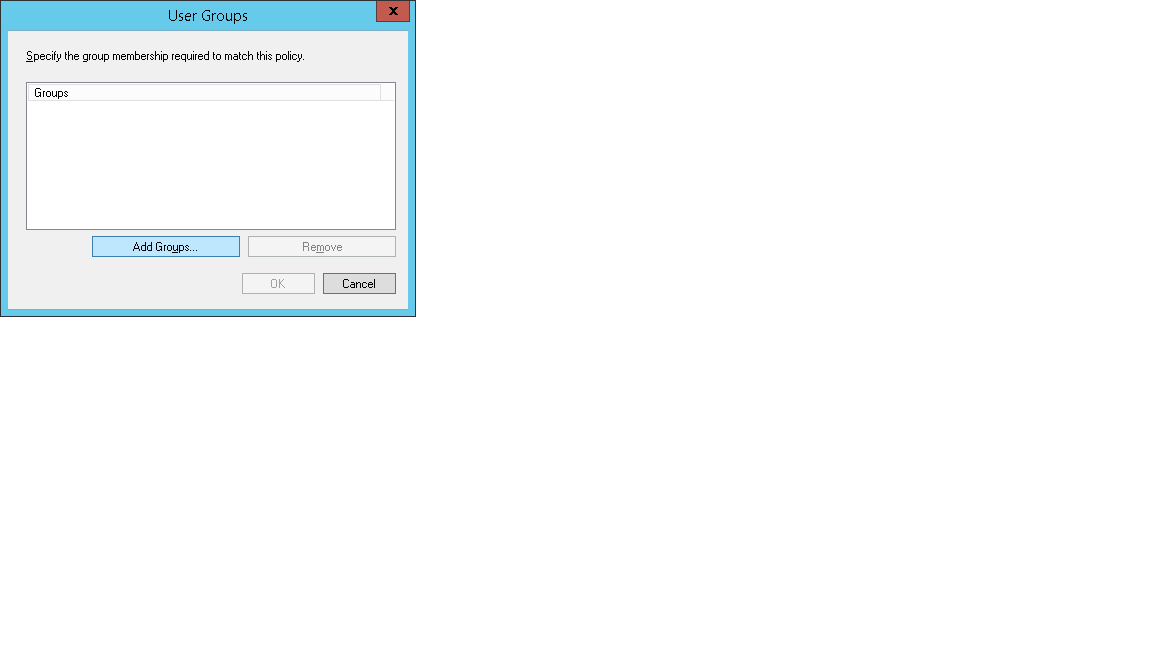
12. Select User Groups and click on Add.

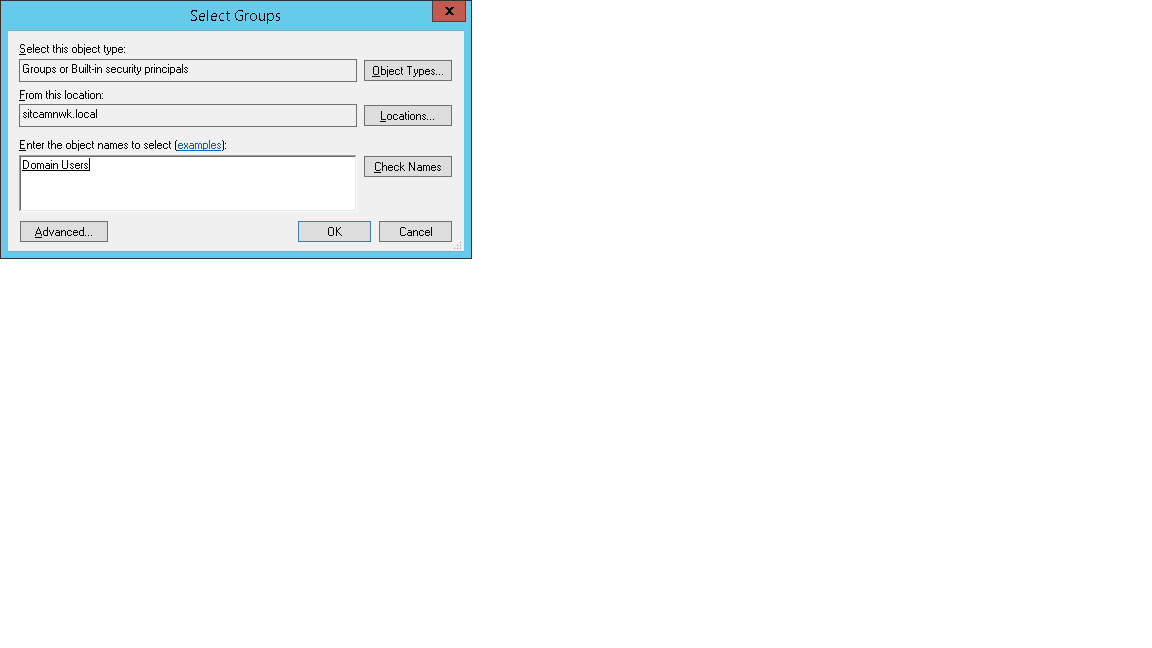
13. Adding user group .Click on Add Groups
Click on Add Groups and add the configured AD group , in this example Vlan10.Click on OK

Add another condition in Network policy that is Nas port type

16. Select Nas port type and then add. Select Wireless –IEEE 802.11

17. Now Both the conditions are added.

19. Click on constraints and select EAP methods that you want to be supported.

20. Now click on Settings tab

20. Click on Add button.Add three attributes
Select Tunnel-Pvt-Group-ID,Tunnel-Medium-Type,Tunnel-Type
Select Tunnel-Pvt-Group-ID

Click on Add . Then click on Add
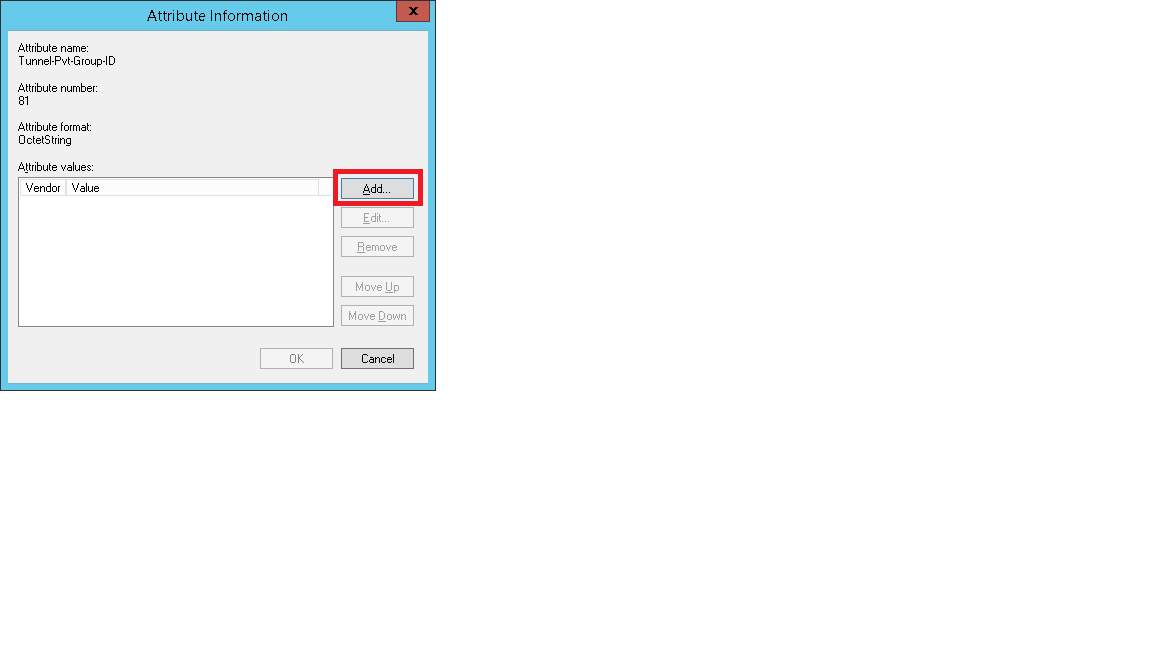
22. Select String radio button under “Enter the attribute value in ”.Configure the vlan ID that you want to configure and click OK.

23. This way add Tunnel-Medium-Type and Tunnel-Type attributes
as 802(includes all 802 media plus Ethernet Calonical Format) and Tunnel-Type as Vlan

- Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers
- Advertising & Talent Reach devs & technologists worldwide about your product, service or employer brand
- OverflowAI GenAI features for Teams
- OverflowAPI Train & fine-tune LLMs
- Labs The future of collective knowledge sharing
- About the company Visit the blog
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.
Can FreeRADIUS be used for dynamic VLAN assignment based on a certificate attribute in EAP-TLS?
I would like to use FreeRADIUS to dynamically assign VLAN tags using the Tunnel Private Group ID field.
I would like to do this via EAP-TLS and have the freeRADIUS server assign the VLAN id based on a given certificate attribute i.e the name value in the subject field.
Is this possible?
I have looked at freeRADIUS dynamic VLAN assignment but cannot see where this could be done , I have seen others create users and have the VLAN id based on the user, but I would like to base it on the EAP-TLS device certificate.
- x509certificate2
2 Answers 2
yes it is possible. In sites-enabled/default edit post_auth section after
- Can you point to some documentation on the specific syntax of this? Can I use a regex? what about the colons that @tfb alluded to below? The canonical documentation is unclear as to if/when a colon is required. – CaNerdIan Commented Apr 15 at 18:54
- The configuration is correct as I indicated. You can also look at this guide to Aruba arubanetworks.com/techdocs/Instant_83_WebHelp/Content/… What do you want to use the regex for? – Francesco Commented Apr 17 at 20:51
- I'm trying to assign a VLAN based on the DC listed in the cert subject. the EAP config is validating the certificate, but I can't seem to get it to actually send anything in the reply, like it's not running that section of the default site config (unless it is and watching it in debug mode isn't actually showing it (which it should be showing) – CaNerdIan Commented Apr 22 at 15:11
- update { &reply: += &session-state: } if (TLS-Client-Cert-Subject =~ /\/DC=Foo\/CN=[ex]\d{4,6}/) { update reply { Tunnel-Type := 13, Tunnel-Medium-Type = 6, Tunnel-Private-Group-Id = "111" } } – CaNerdIan Commented Apr 22 at 15:15
include a colon to make it work:
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged dynamic x509certificate2 freeradius radius vlan or ask your own question .
- Featured on Meta
- We spent a sprint addressing your requests — here’s how it went
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network...
- What makes a homepage useful for logged-in users
Hot Network Questions
- Pattern on a PCB
- Is infinity a number?
- French Election 2024 - seat share based on first round only
- Where do we go if we gain knowledge of the absolute truth?
- The meaning of "tarmac ticket"
- Using grout that had hardened in the bag
- Why does King Aegon speak to his dragon in the Common Tongue (English)?
- How does light beyond the visible spectrum relate to color theory?
- I am trying to calculate Albumin-Creatinine ratios for research, why is the result so high?
- Questions about writing a Linear Algebra textbook, with Earth Science applications
- What scientifically plausible apocalypse scenario, if any, meets my criteria?
- Confusion regarding "since" vs "for"
- Are there other proposed translations of "aelfheres" in Beowulf than a name?
- Distorted square wave
- Dual of slope semistable vector bundle on higher dimensional variety
- Reviewer "rejected" my submission, and then submitted one by their own. What did they do wrong?
- Can a festival or a celebration like Halloween be "invented"?
- Error concerning projectile motion in respected textbook?
- Can IBM Quantum hardware handle any CSWAP at all?
- Does physical reality exist without an observer?
- Are there countries where only voters affected by a given policy get to vote on it?
- o y u (or and or)
- Car stalls when coming to a stop except when in neutral
- Is this definitive conclusion of a blown head gasket?

IMAGES
VIDEO
COMMENTS
This document introduces the concept of dynamic VLAN assignment. The document describes how to configure the wireless LAN controller (WLC) and a RADIUS server to assign wireless LAN (WLAN) clients into a specific VLAN dynamically.
Complete these steps: From the ISE GUI, navigate to Administration > Identity Management > Identities and select Add. Complete the configuration with the username, password, and user group as shown in the image: Step 3. Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment.
This document describes the concept of dynamic VLAN assignment. It also describes how to configure the wireless LAN controller (WLC) and a RADIUS server in order to assign wireless LAN (WLAN) clients to a specific VLAN dynamically. In this document, the RADIUS server is an Access Control Server (ACS) that runs Cisco Secure Access Control System Version 5.2.
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate ...
To be able to assign VLANs dynamically from the RADIUS server you can use one of the following standard attributes to deliver the VLAN attribute (RFC2865, RFC2866, and RFC3576 define standard RADIUS attributes, which are supported by all mainstream vendors): Attribute No. Attribute Name Description 64 Tunnel-Type Protocol type of the tunnel. The value is fixed as 13, indicating VLAN. 65 Tunnel ...
Cisco documentation states that dynamic vlan assignment via RADIUS should provide the following IETF values: The RADIUS user attributes used for the VLAN ID assignment are: IETF 64 (Tunnel Type)—Set this to VLAN.
To be able to assign VLANs dynamically from the RADIUS server you can use one of the following standard attributes to deliver the VLAN attribute (RFC2865, RFC2866, and RFC3576 define standard RADIUS attributes, which are supported by all mainstream vendors): Attribute No. Attribute Name Description 64 Tunnel-Type Protocol type of the tunnel. The value is fixed as 13, indicating VLAN. 65 Tunnel ...
After configuration, run the RADIUS server to listen for access requests. Step 2. Create the RADIUS profile. Go to Authentication --- RADIUS Profile, create a new profile bound with the RADIUS server, and check "Enable VLAN Assignment for Wireless Network" to assign VLANs for wireless clients. Step 3.
I would like to configure and understand how to dynamically assign vlan on one ssid by radius attribute? With other vendor this is more easy.
Dynamic VLAN assignment, as described in RFC 2868, allows a RADIUS server to steer an authenticated user to a VLAN specified by the "Tunnel-Private-Group-ID" attribute.
I want RADIUS server to dynamically assign VLANs to ports based on RADIUS reply attribute for particular user. I have an HP E2620 switch and a FreeRADIUS server.
The VLAN RADIUS Attributes in Access Requests feature enhances the security for access switches with the use of VLAN RADIUS attributes (VLAN name and ID) in the access requests and with an extended VLAN name length of 128 characters. This module describes how to create an attribute filter-list and how to bind an attribute filter-list with ...
Here's an example of how to configure NPS to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. The key to getting this to work is the use of a RADIUS element called: 'Tunnel-PVT-Group-ID'.
All, I'm looking for a means to secure interfaces configured in an admin vlan. In an ideal world the interface would be configured with the admin vlan if the device is somehow identified (not necessarily authenticated). In the event that the device isn't identified it fails back to a standard devic...
In lieu of CoA, MS switches can still dynamically assign a VLAN to a device by assigned the VLAN passed in the Tunnel-Pvt-Group-ID attribute. It may be necessary to perform dynamic VLAN assignment on a per computer or per user basis. This can be done on your wired network via 802.1x authentication (RADIUS).
2. RE: Dynamic vlan Assignment using Radius attribute& filter ID. You would need a policy engine like ClearPass to do that. Windows NPS server can authenticate and return radius attributes, but cannot combine AD group logic with another attribute to send back a third attribute. 3.
The VLAN RADIUS Attributes in Access Requests feature enhances the security for access switches with the use of VLAN RADIUS attributes (VLAN name and ID) in the access requests and with an extended VLAN name length of 128 characters.
Hello, I am implementing WP2 Enterprise for my office network also included dynamic vlan assignment. I am using FreeRADIUS as my radius server and I am currently facing some issues when I configure dynamic vlan for cnPilot. I have already configured some options at cloud controller and added Radius attribute for cambium at DaloRADIUS and applied this to user account. When I login with this ...
Vlans need to be assigned based on different Radius group i.e Sales group to Vlan 10
I would like to do this via EAP-TLS and have the freeRADIUS server assign the VLAN id based on a given certificate attribute i.e the name value in the subject field.