- Open access
- Published: 04 September 2015

A systematic review of RFID applications and diffusion: key areas and public policy issues
- Kwangho Jung 1 &
- Sabinne Lee 2
Journal of Open Innovation: Technology, Market, and Complexity volume 1 , Article number: 9 ( 2015 ) Cite this article
35k Accesses
11 Altmetric
Metrics details
RFID applicants called as e-ID, smart tag, and contactless smart card are being applied to numerous areas in our daily life, including tracking manufactured goods, currency, and patients to payments systems. To review these various applications of RFID is important to exploring not only ongoing e-governance issues such as digital identification, delivery process, and governance but also business oriented application areas like supply chain. Through a systematic review methodology from 111 previous studies about RFID technology for public sector, we found six key areas of RFID applications: defense and security, identification, environmental applications, transportation, healthcare and welfare, and agriculture-livestock. We also suggest that the diffusion and applications of RFID can involve unexpected disadvantages including technological deficiency, uncertain benefits, dubious transparency, uncomfortable privacy issue, and unequal distribution of digital power and literacy. Further research on RFID impact includes not only various theoretical issues of but also legal and managerial problems. Rigorous research is required to explore what factors are critical to adopt and implement new RFID applications in terms of technology governance and digital literacy. Massive data driven research is also expected to identify RFID performance in government agencies and various industry sectors.
RFID technology has been widely implemented all over the world and its impact on our daily life is very diverse and massive (Li et al., 2006 ; Wyld, 2005 ). Those diverse areas of RFID application include logistical tracking, monitoring and maintenance of products, product safety and information, and payment process. Today many governments around the world in both developed Footnote 1 and developing Footnote 2 countries are trying to apply it for various areas from tracking manufactured goods, currency, and patients to securing sagety of payments systems. Massive RFID applications around all the industry sectors and countries are expected to generate a huge potential benefits for sustainable efficient energy infrastructure, transportation safety, and health care. Over the past 50 years, RFID technology went through innovations and progressions to become a more efficient and effective gadget for human beings as well as effective solutions of technical and organizational problems in various industry sectors. However, key issues of appropriate ICT technology, governing networks among RFID domains, standardization requirement, and privacy still remain unsolved Footnote 3 .
We review previous literature about RFID technology used in public sectors in order to identify what has been done and found to suggest policy implications and further research agenda. More specifically, we discuss four aspects regarding RFID research issues and policy implications. First, we examine various competing concepts of RFID use by governments all over the world. Second, we categorize numerous applications of RFID technology through analyzing previous literature. Third, we try to figure out technological issues and governance problems that RFID technology faces today. Last, we draw key public issues and suggest future research agenda.
Methodology of the RFID literature review
A brief history of rfid technology.
RFID technology was emerged as Frederick Hertz found existence of radio frequency during his experiment in 1886 (Wyld, 2005 ) and developed for the purpose of defense during the Second World War Footnote 4 . During 1970s and 1980s, the RFID system attracted plenty of scholars and innovators, so efforts to register patents progressed (Takahashi, 2004 ). Researchers like Charles Walton had registered a patent to use RFID. In the 1980s, many US and European companies recognized the importance of developing RFID technology and started to manufacture RFID tags. Soon scholars at MIT University opened an Auto-ID center to promote the use and implementation of RFID technology. But most of the scholars report that the first commercialization of RFID technology was done by Wal-Mart as they launched RFID based material identifying system in 2005 (Shahram and Manish 2005 ). Wal-Mart is now tracking merchandise including food, apparels, and electronic items with RFID technology in their supply chain. Footnote 5 . RFID technology is a brand new policy tool that can ensure high transparency, efficiency and effectiveness not only in industrial areas but also in government service delivery. Table 1 describes a brief history of how RFID technology was developed and diffused.
Research design for a systematic review
We searched online data base and expert based information to identify RFID publications between 2003 and 2015. We categorized RFID applications and analyzed issues and concerns that RFID faces today by systematically reviewing published literature. We have collected literature we use for systematic review from two different resources. First, most of the studies are found by searching the e-database. We could access electronic databases, such as Google Scholar, World Web of Science (WWS), Proquest Central, and Science Direct through Seoul National University’s main library homepage. We had set ‘RFID technology’, ‘RFID government,’ ‘RFID application, and ‘RFID issue’ as keywords for searching literature. We found most of the research through this method of searching. The second method we used for collecting data was having discussions with experts. To do this, we first made a list of experts who specialize in IT technology, Science technology, and public administration. Five experts agreed to help us and recommended some research papers that were known for their fluent flow of logic and plentiful contents. We chose relevant research papers from among experts’ recommendations. In sum we had used previous literature collected from two methods we discussed above, searching e-database and asking experts, as our resource of searching.
[Figure 1 ] shows analytical frame that we use for this study. We have determined the literature for systematic review according to three stages shown on the flow chart. First, the original total number of studies we have found from the e-database was 4260. Also 185 research papers were found from experts’ recommendations and previous public papers. A total of 4,445 studies were chosen through the first stage. Second, we excluded 4,121 following general eligibility criteria by screening title and abstract. More specifically, we excluded RFID studies only with one of the following criteria: 1) studies focusing on private sector; 2) studies without considering how public sector implemented RFID technology; 3) studies that did not discuss any social scientific implications; and 4) studies that only deal with RFID technology from pure scientific and engineering points of view. In sum, we included only 324 papers that discussed RFID issues and their implications in public sector. Third, we removed further 213 studies too much focusing on private sector or RFID technology itself, rather on its applications in our society and social scientific implications. Finally, 111 articles were chosen for our systematic review.
Analytical Frame
[Figure 2 ] below showed descriptive statistics of collected literatures by published year. It shows 22 studies were published in 2007 among 111 literatures. As we already described above in history of RFID section, the popularization and commercialization of RFID technology was started in 2005 with Wal-Mart’s adoption. It seems that after Wal-Mart’s innovative footsteps hit the world, many scholars were started to recognize the potential of new technology and tried to understand and develop RFID technology. Besides some governments from all over the world implemented new way of public service delivery using RFID technology. Consequently, 49 literatures were publishedbetween 2006 and 2008 and it forms almost 45 % of our collected studies
Descriptive Statistics of Literatures by year
For this study, we categorized governments’ way of using RFID technology in 6 areas; Agriculture and Livestock, Defense and Security, Environmental Applications, Healthcare and Welfare, Identification, and Transportation. [Figure 3 ] shows descriptive statistics of collected literatures categorized by applications. We categorized studies that did not focus on specific sector and analyze and introduce RFID technology from the general perspectives as ‘RFID general’. ‘RFID general’ studies usually deal with various ways of using RFID technology in diverse sectors simultaneously. As we can see from [Fig. 3 ], RFID general area had 42 papers. That means still lots of RFID studies could not be fully specialized and remained in status of generally introducing RFID technology. Identification sector scores secondly highest number of published literatures among areas. This result seems natural because e-ID card or e-Passport have most powerful force that can hurt privacy, one of the most serious and notorious issues that RFID technology face today
Descriptive Statistics of Literatures by applications
Key applied areas of RFID
Defense and security.
As we show in [Table 1 ], the history of RFID technology was started from the need for ensuring national security. Almost 60 years have passed since US army developed RFID based identification system to identify allies and enemies, RFID technology is still used for protecting people. For instance, Weinstein ( 2005 ) and Konsysnki & Smith ( 2003 ) reported how the US Army and Navy implement RFID technology in cargo containers to identify materials. The US Army and Navy implement RFID not only to identify US troops’ own weapons and containers but also to identify enemies in battle (Tien 2004 ) Footnote 6 . RFID systems are also important in terms of airport and port security. After the 9/11 terror attack on the United States, President George W. Bush let all the airport and port in US adopt identification systems based on RFID technology to protect its nation from additional terrorist attacks (Werb and Sereiko 2002 ) Footnote 7 . In 2012, the Taiwanese government decided to implement an RFID based e-Seal system to increase security and efficiency (Tsai and Huang 2012 ). In addition, RFID technology can be used effectively in prison management Footnote 8 and child protection. In some countries like Japan and Republic of Korea, the RFID tag is implemented in child protection monitoring (Table 2 ). Footnote 9
Identification
Electronic passports like ‘e-passports’ were adopted electrically after the 9/11 attack. After the terrible tragedy broke heart of United States, the American government became aware of the importance of checking VISAs and passports correctly. The US Department of State soon let people who wanted to enter US to use RFID tag embedded electronic passports instead of traditional barcode based passports Footnote 10 . The European Union also endorsed the inclusion of biological information in e-passports. The EU Justice and Home Affairs Council decided to include fingerprints as a second mandatory identifier on passports in 2004. Footnote 11 In addition, RFID can be used in e-ID cards in various countries. For example, in the United Kingdom, Prime Minister Tony Blair and his Labor Party convinced the nation to adopt biometrically-enhanced national identification cards (Ezovski and Watkins 2007 ). Tony Blair’s administration announced its will to implement RFID tag embedded national identification card in late 2004. China is another case where the e-ID card is used today. As a matter of fact, China is the country where e-ID card is widely and largely adopted today. The Beijing Olympics held in 2008 lit the fuse of adoption. The largest smart card project was implemented as a part of preparing the most prominent international sports event. In 2008, the Chinese government supplied 1.2 billion dollars of RFID readers and 2.25 billion dollars of RFID embedded smart cards to citizens. This made China the world’s largest market for RFID (Kovavisaruch and Suntharasaj 2007 ) (Table 3 ).
Environmental applications
RFID technology can be widely applied in environmental applications. Adopting an RFID system in waste management is the most prominent way of using RFID to ensure efficient, eco-friendly waste management among lots of countries in the world. PAYT (Pay-As-You-Throw) program done by European Union (EU) is the pioneer of this field. PAYT is an RFID based waste pricing model that allows each individuals or each household to pay for the tag along with the total amount of waste they throw. Since each household and individual has a waste box in which RFID tags are embedded, the exact volume of waste can be calculated. In Europe this incentive based system has been proven to be a powerful policy tool for reducing the total amount of waste and for encouraging recycling (Schindler et al. 2012 ). Similar systems are broadly implemented in US (Ransford et al. 2012 ). In South Korea, the ministry of environment introduced it to industry and urged them to use an RFID based waste management system, especially in medical waste management. RFID technology is implemented in waste management in developed and developing countries, but the purpose of adoption is somewhat different from Europe to the US. India, the second-most populated country in the world, has adopted RFID technology to cope with the rapid increase of volume and types of waste (Infotech 2013 ). Similarly in 2010, what China faced were the World Expo and huge amounts of construction waste that comprised 30 % to 40 % of the total urban waste. Shanghai was chosen for a pilot project using an RFID based waste management system. All the waste dumping trucks had an embed RFID tag and volume of waste they carry was checked by the local government (Ruan and Hu 2011 ). Another interesting case of environmental application emerges from South Korea. The South Korean government operates U-Street Trees Systems through which the exact location and status of street trees can be monitored. Information about location and status of street trees are collected by an RFID tag that is attached to each tree is saved in a web information system, so trees can be managed effectively. Kim et al. ( 2006 ) claim that this web based information system could manage information remotely with an interactive system (Table 4 ).
Transportation
Public transportation is another popular sector for RFID technology applications. RFID based electronic toll collection technology is one of the oldest and widespread RFID implementation (Ulatowski 2007 ). As soon as an RFID tag embedded car arrives at a toll booth, the RFID reader scans and reads the information that the RFID tag contains. The driver will pay debits according to the price that electronic reader suggests. In the US, electronic toll collection is thought as efficient and effective method that eliminates long lines of traffic at toll booth (Ulatowski 2007 ). RFID based toll collection is also adopted in criminal cases because it enables prosecutors to identify the exact location of the criminal’s car (Smith 2006 ). In South Korea, the Korean government has set credit card-linked electronic toll collection system called ‘Hypass’ especially for collecting transportation tolls on express ways. If an RFID tag is embedded on their cars, drivers can pass the tollbooth without stopping the car because RFID reader scan the data immediately and handle the whole payment process in about 5 s (Kim 2008 ). Hong Kong launched similar public transportation toll collection system in 1997 and the ‘Octopus Card’ is now internationally famous for its convenience. This system is able to handle 10 million transactions per day and includes all modes of public transport (Kovavisaruch and Suntharasaj 2007 ). South Korea has set credit card-linked electronic toll collection system called ‘Hypass’ especially for collecting transportation tolls on express ways. RFID technology is also implemented in railroad toll collection in India, where railroads are the most widely used form of public transportation. If an RFID tag is embedded on their cars, drivers can pass the tollbooth without stopping the car because RFID reader scan the data immediately and handle the whole payment process in about 5 s (Kim, 2008 ). In addition, RFID has been used as a critical technology to promote efficiency and transparency for public transportation system in developing countries. For instance, the Mexican government runs “Creating Traffic Knowledge in Mexico: Applying RFID to prevent vandalism” and one of the purposes of this innovative project is to develop a transportation information system to acquire more subtle data necessary for government decision making ( Prado et al. 2010 ). Analogous to Mexican case, in Bangladesh where BRTA (Bangladesh Road Transport Authority) was started in 2003, the technology is operated mainly for control and supervision of the road transport systems (Hossain et al. 2009 ). RFID technology is also implemented in railroad toll collection in India, where railroads are the most widely used form of public transportation (Table 5 ).
Healthcare and welfare
RFID enables hospitals to manage their equipment more easily and save expenses in public health areas Footnote 12 . The US government agencies like FDA have also already used RFID tag in monitoring drug industry Footnote 13 . Since American hospitals handle almost 4,000 medicines per day, medication errors can be easily occurred. With strong government support, public hospitals in Taiwan have actively adopted innovation of RFID (Kuo and Chen 2008 ) Footnote 14 . Even though it is not yet commercialized, an RFID identification system Footnote 15 for the visually impaired people is being developed by engineers in Pakistan with the support of the Pakistani government (Murad et al. 2011 ) (Table 6 ).
Agriculture and livestock
RFID technology can be an effective tool for securing food safety and managing agriculture and livestock. Another major advantage to this system is that animal disease tracking can be realized through innovative technology like RFID (Hossain and Quaddus 2009 ). With the government support, researchers have developed the Navigation System for Appropriate Pesticide Use as a basic system for risk management in agriculture (Nanseki et al. 2005 ). RFID technology in agriculture was first introduced by the European Union (EU) in the late 1990s and shortly thereafter many countries, such as Australia, Japan and South Korea, adopted the innovation. Among those countries, the Australian government was the most passionate in implementing RFID Footnote 16 . For instance, all the livestock in Australia have RFID embedded tags on their bodies immediately after they are born; information that enables farmers to identify each entity and its health status is registered in National Livestock Identification System (NLIS). RFID technology in Japan has been also adopted in agriculture especially to secure food safety and agricultural risk management that can occur by abusing pesticides (Nanseki et al. 2005 , Sugahara 2009 ). The Japanese government planned to make a food traceability system by 2010 as a part of the “e-Japan” plan (Chen et al. 2008 ). The United States is another case that applies mandatory RFID based identification system in managing livestock. According to RFID Gazette ( 2006 ), the USDA is pushing for RFID tagging of cattle to make tracing of disease patterns easier. With the formation of National Institute for Animal Agriculture (NIAA) in 2002, the plan for setting the National Animal Identification System was started. What the US government fulfilled through this program was “to be able to identify all animals and premises that have had contact with a foreign or domestic animal disease of concern within 48 h” (Wyld, 2005 ) because “the sooner animal health officials can identify infected and exposed animals and premises, the sooner they can contain the disease and stop its spread (USDA-APHIS 2005 )” (Table 7 ).
Public policy issues from RFID diffusion
RFID applications and diffusion generate complex policy and governance problems. We address public policy issues such as technological gap and uncertainty of expecting potential benefits and costs from a rapid and massive RFID diffusion. Uneasy governing issues in transparency, digital identification and power distribution are arising from inappropriate RFID applications. We discuss governance issues such as corruption, privacy problem, and digital monopoly and literacy in the following.
Technological concerns
Technology is not still enough to satisfy all the elements that RFID is trying to perform various operational mechanisms. RFID technology deficiencies inevitably occur with the application of technology because there is niche space still left. For instance, RFID technology does not have a unified frequency standard yet. Since there are no internationally agreed upon frequencies for RFID operations, permitted scanner/reader powers also differ between countries. There are still significant differences between the frequencies from the EU and the USA (Hossain et al., 2009 ). In addition, Reichenhach (2008) pointed out the lack of storage capacity. In the EU, where RFID based waste management is common, there are technological barriers like a shortage of storage capacity Footnote 17 . Ema and Fujigaki ( 2011 ) draw implications from a child monitoring case done in Japan that being informed of children’s exact location cannot guarantee their actual safety, but RFID tags often lead to that cherished illusion. Vining ( 2005 ) warned about another possibility of niche space. According to his study about port security in the US, stealing goods without damaging RFID tag is possible because at ports, the container can be drilled into and contents can be removed. The RFID tag does not have to endure any damage through this whole process. In the US, as a response to continued pressure from various stakeholders, the US government even adopted the ‘Faraday cage’ for privacy protection Footnote 18 (Table 8 ).
Uncertain cost-benefit effectiveness
RFID defenders emphasize that RFID technology can guarantee effectiveness and efficiency at a very cheap price. There is, however, substantial evidence to show RFID can generate unexpected costs Footnote 19 . In reality, the RFID tag is much more expensive than a barcode, which was very popular in identifying materials before the rise of RFID technology (Becker 2004 ). Purchasing RFID devices, hardware, and tags is not sufficient to drive system relevantly. To guarantee a better quality of service, the RFID system needs more additional things such as “circular process mechanism, the richness of consultant, project manager, programmers and plentiful project labors” (Kuo and Chen 2008 ). These elements for a better RFID performance may involve considerable costs. Kuo and Chen ( 2008 ) reported that RFID technology consumers and government should pay the extra hidden cost in the healthcare industry (Table 9 ).
Dubious transparency and corruption
RFID technology is expected to increase transparency and monitor corruption. However, RFID technology cannot ensure a high level of transparency than expected. As a matter of fact, RFID tags can be cloned and manipulated quite easily, and this kind of tag corruption can occur at every stage of RFID implementation. There are various examples to show an inappropriate use of RFID technology. For instance, Armknecht et al. ( 2010a , b ) warned the possibility of tag corruption. Lee et al. ( 2012 ) pointed out reader corruption of the RFID technology. An existing security model mainly focuses on the possibility of tag corruption, but reader corruption can hurt consumers’ privacy as seriously as tag corruption can. Jules ( 2006 ) reported one of the tag corruption cases that observed in United States. One of the staff members who worked in a Dupyu store, an unscrupulous retailer, attached a cloned tag to counterfeit drugs. Avoine et al. ( 2010 ) argued that internet based databases can also be directly attacked and emphasized the possibility of reader corruption. There are also unethical behaviors to avoid RFID monitoring process. In the EU where an RFID based waste management system is aggressively implemented, some people disposed waste that came from their house at work places in order to avoid exact calculation through the RFID system. Not only this, Bilitewski ( 2008 ) reported that some conscienceless people are burning or transferring waste outside instead of throwing it into their RFID tag attached garbage can (Table 10 ).
Privacy issues
One of the most serious issues that RFID technology faces today is whether RFID technology is secure enough to protect privacy. Privacy is the most important concern RFID users have to deal with (Perakslis and Wolk 2005 ). RFID tag embedded chips often contain important personal information and usually this kind of private information can hurt one’s privacy seriously if leaked. To prevent leakage of private information, engineers developed cryptography, but there remains criticism Footnote 20 . The reason why these sorts of privacy concerns arise is because of the lack of security protection capacity of modern RFID technology. As we discussed above in the technological issues section, RFID technology today is not developed to secure perfect privacy. The technology itself has lots of deficiencies and people are smart enough to find niche spaces that can destroy the RFID security process. RFID itself can involve not only various hidden costs Footnote 21 but also induces a serious privacy problem Footnote 22 . However, despite these possibilities of attacks on privacy, there are lots of stakeholders and scholars who advocate the potential benefits of RFID. They claim that tracking and profiling consumers is solely for implementing RFID chips more effectively. Eaward Rerisi, one of the producers of early implementation of RFID technology argued that, “An RFID reader can read the number on a tag, but without knowing what the number means, there is no way to access personal information. The idea that the tags can be read by just anybody—that’s pretty impossible” (Murray 2003 ) (Table 11 ).
Unequal power and digital literacy
Unequal distribution of RFID technology can generate unequal distribution of various resources such as information and digital literacy. Especially in developing countries, the combination of unbalanced power distribution between stakeholders and a low level of digital literacy can cause serious problems. Ketprom et al. ( 2007 ) emphasized that in developing countries like Thailand Footnote 23 , governments should provide education and training on how to use brand new technology to poor farmers whose digital literacy remains relatively low. But poor farmers in Thailand are not the only stakeholders who are suffering from a lack of digital literacy. In Bangladesh, where RFID toll collection is common, traffic policies have no interest in using RFID technology for managing public transportation systems. Rather, they prefer traditional ways of toll collecting to information based technology (Hossain et al., 2009 ). Prasanth et al. ( 2009 ) found that the lack of digital literacy among the Indian people hampered an effective process of railroad toll collection in India. Another problem developing countries face is an unbalanced power distribution due to lack of democratic value embedded governance. Chen et al. ( 2008 ) criticized the Taiwanese government because it monopolizes most of the information collected by RFID technology. As we already discussed above, when RFID tag scanned, information saved in RFID tag is scanned by reader and then transmitted to an internet based database. If that data were available to the public, individuals and industry could make more reasonable decisions by analyzing them. We find another unbalanced power distribution case in China’s waste management system. According to Ruan and Hu ( 2011 ), the Chinese government benefits most from the RFID system Footnote 24 (Table 12 ).
Discussion and Conclusion
We found, relying on a systematic review from 111 RFID studies, six key areas of RFID applications. Specifically in the defense and security section, we addressed how military and airports/ports manage RFID systems to ensure security. We also found that RFID is effectively implemented in prison management and child protection programs. Numerous governments have introduced RFID identification tools such as e-passport and e-ID. RFID systems for waste management and street tree management are widely used from rich to poor countries. In healthcare and welfare delivery, RFID based smart cards have turned out to be very efficient. RFID is now being used to monitor counterfeit drugs. RFID has been applied to delivering service for the impaired and to trace infection. However, despite potential benefits from RFID applications, various unexpected problems arise. RFID can still involve technological deficiencies, especially in securing cryptography techniques, international standards of frequency, and storage capacity. RFID technology is not still enough to be efficient and effective in some areas (Becker 2004 , Jensen et al. 2007 ). Tag and reader corruption can hurt transparency and security. Privacy issues are still the most serious issues that RFID faces today (Naumann and Hogben 2008 ). RFID itself can generate new unequal digital literacy and power distribution, especially in developing countries such as Thailand and Bangladesh. Even the most latest innovative technologies, like RFID, do not have perfect answers to securing efficiency, effectiveness, convenience, and transparency. Rather, RFID technology itself creates unexpected problems. It should be noted that democratic governance and trust is still important to technological innovation and policy issues arising from a rapid RFID diffusion.
Our systematic review is incomplete to discuss all of the RFID issues from technology, market and management, e-government, and legal aspects. Further research on RFID diffusion and impact include not only various theoretical issues of but also legal and managerial problems. For instance, both qualitative and quantitative research is required to explore what factors are critical to adopt and implement new RFID technology in terms of governance and digital literacy. Both micro and macro approaches with massive data are also required to identify how RFID improve not only organizational performance in government agencies and various industry sectors but also quality of our life.
For example, after serious attack by Osama Bin Laden on 9/11, the American government decided to implement an RFID tag embedded e-passport and VISA waiver program. The US government asked their member countries to implement e-passport by late 2005 and soon US member countries like ROK and EU started to use e-passports. Currently, no one can enter to United States without an RFID tag based e-passport.
Especially in developing countries, governments usually adopt brand new IT technologies, but their low level of socio-economic infrastructures may prohibit the efficient operation of technology.
For instance, RFID applications may lack social virtues like trust, ethics, and democracy. It is essential to understanding how a rapid diffusion and massive applications of RFID generate conflict or harmony among human behaviors, digital literacy, institutional rules, and technology.
US Army and its allies could not only manage weapons and soldiers but also identify who was the enemy or not (Castro and Wamba, 2007 ). This whole project of developing an RFID based identifying system was known as IFF (Identify Friend of Foe).
See more various examples of RFID applications at the website ( https://epic.org/privacy/rfid/ )
In 2004, the US Army adopted RFID during the Iraq war to track Iraq troops. Not only these, the US Army piloted 4 projects using RFID; identifying material locations, weapons deteriorations, hazardous material tracking, and asset tracking (Anon 2002).
The New York City government also started an RFID e-seal pilot project in the New Jersey Port. Once RFID read and scan the tag, it can identify the contents of the container box. Also, the port of Tacoma and Seattle planned to adopt E-Seals, made of metal bolts with embedded RFID devices to ensure its security (Konsynski and Smith 2003 ).
Calpatria prison, located in Los Angeles, adopted a prisoner monitoring system using RFID chips in 2000 as the very first pilot using RFID in prison management in United States (Kim 2008 ). According to regulations of Calpatria prison, all the prison inmates were issued bracelets in which RFID chips were embedded. Since the pilot project at the Calpatria prison was successful, the local government let other prisons in Los Angeles adopt the innovative bracelet. The LA County prison started to use a brand new bracelet in response to the state government’s order; it is reported that through its adoption the prison could increase efficiency and effectiveness and decrease crimes occurred between inmates simultaneously (Nicholas 2008).
For instance, city governments in the Gifu and Osaka prefecture provided RFID tags that can be attached in students’ schoolbags to public elementary schools (Ema and Fujigaki, 2011 ). Similarly, in Haewoondae beach, one of the most famous vacation spots in South Korea, Busan Metropolitan City provides for parents RFID embedded bracelet that enables tracking exact location of their child by a smart phone ( http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=102&oid=001&aid=0003353674 ).
This project began in 2002, but it took 3 years to fully implement for all 16 US passports (Meingast et al. 2007 ). The appearance of the e-passport is very similar to old passports, but woven into the paper of the passport, there is RFID tag that information about owner of the passport is included. Information about nationality, sex, age, and so on is scanned, as airport staff members scan the passport through RFID reader (Lorenc 2007 ). The US government did not stop at this point and adopted VISA Waiver Program. By 2005, the US member countries had to adopt RFID based e-passports and VISA Waiver Programs in order for their citizens to enter the United States because without e-passports, passengers could not be accepted at American points of entry. Today, the e-passport includes not only individual data but biological data, such as fingerprints (ICAO TAG MRTD/TWF 2004).
E-Government News, “EU Asks US for Time to Issue Biometric Passports”. iDABC European e-Government Services, 1 April, 2005.
For instance, Wicks et al. ( 2006 ) reported that this RFID based hospital management system is very effective in reducing management costs because embedded RFID tags can track lost or hidden expensive equipment. Miller (1999) pointed out that the potential of RFID technology can be expanded in tracking the location of patients and controlling the drugs. Also, Chowdhury and Khosla ( 2007 ) argued that RFID technology can be effectively used not only in hospital equipment management but also in patient management.
According to statistics published by the Institute of Medicine (IOM), about 44,000 to 98,000 people die in the USA per year because of improper drug administration (Kohn et al. 2000). To rectify this phenomenon, in 2004 the US government and US FDA recommended pharmaceutical industries to implement RFID tags to prevent the production of counterfeit drugs (Wyld, 2005 ). The Florida state government added legal regulations to this recommendation in 2006. If a pharmaceutical industry located in Florida does not attach RFID embedded tags on its products, it has to face substantial financial penalties (Skinar 2005).
For instance, RFID technology saved Singapore and Taiwan from SARS attack around 2003. Two public hospitals in Singapore in 2003 adopted RFID technology to track staff, patients, and visitors in order to trace people who carried the SARS virus. The RFID information database saved all the data collected from each individual’s RFID tag for 21 days, which was thought to be long enough for expression of SARS virus (Nicholas 2008). A similar process was done in Taiwan too. During the SARS period, five hospitals, including Taipei Veteran’s General Hospital, implemented RFID tags to track patients who had possibility contracted the SARS virus (Kuo et al. 2004 ) with strong government support.
One peculiar characteristic of this system as compared to other systems is that visually impaired people are both the reader carrier and the service beneficiaries, simultaneously. Generally in government service delivery using RFID technology, the service provider usually carries RFID tag readers and service beneficiaries usually act more passive roles by attaching RFID tags. But in this Pakistani case, the service beneficiaries can identify objects around them by operating RFID tag reader they have.
The Australian government passed legislation on mandatory use of RFID tags in the livestock industry, so Hossain and Quaddus ( 2014 ) categorized Australian case as a very rare and special adoption case. According to Trevarthen and Michael ( 2007 )’s case study, one of the Australian farms where the RFID tag is implemented, farmers not only track the exact location of the cows but also check the condition, identify cows and even feed the new born cows automatically by using an RFID system.
Usually people throw waste in various places. They may throw it away at their houses or at work places, like an office. Since the RFID tag is only attached to a garbage can in house, it is impossible to track all types of waste throwing behaviors. Inevitably, this shortage of storage capacity leads to selective waste collection monitoring.
The faraday cage is an object in metal; proponents of this device argue that faraday cage can prevent hacker’s attack because electronic devices are prevented from passing through the object (Ezovski et al. 2007). But speculation about stability of this technology still remains. Lorenc ( 2007 ) reported that if there is no additional technology, the faraday cage cannot preserve sensitive security.
As a matter of fact, there are two kinds of RFID tags, the passive tag and the active tag. These two tags provide owners with different benefits and liabilities. Active tags are implemented by a power source, such as small battery. Active tags are more efficient and safe in protecting privacy than passive tags, so sensitive organizations like military prefer active tags to passive tags. But ordinary consumers have less accessibility to active tags because active tags are much more expensive than passive ones (Jensen et al. 2007 ).
According to Laurie ( 2007 ), even without physically losing an RFID tag, private information can be stolen because what’s inside RFID tags can be skimmed quite easily. If we can build a device that enables us to transmit an arbitrary number, invading the internet based database is theoretically possible.
For instance, Wal-Mart Stores Inc. and Procter & Gamble Co. in autumn 2003 planned a very interesting experiment to check the potential deficiencies of RFID technology. Customers of a Wal-Mart store in Broken Arrow, Oklahoma were secretly tracked through RFID tags while purchasing lipstick that Procter & Gamble Co. made (Barut et al. 2006 ).
For instance, Hwang et al. ( 2009 ) and Numann & Hogben (2009) categorized various kinds of privacy attack cases that can possibly occur. According Hwang et al. ( 2009 ), technological deficiency enables hackers to engage in cloning, eavesdropping, replay attack, denial of service, forward security, tag tracing, individual data privacy, and data forging. Specifically, the hacker can read the tag and then clone the tag (cloning), surreptitiously listen to all the communications between and the tag (eavesdropping), repeat or delay the message (replay attack), send large amount of message to break down RFID system (denial of service), compromise a tag (forward security), trace the exact location of the tag (tag tracing), find out shopping trend of the consumer (individual data privacy), and modify information saved on an RFID tag (Data forging). In addition, Numann and Hogben (2008) categorized the privacy attacking cases more briefly. According to their research, the hacker can attack RFID tag in some ways. First, the attacker can open a connection to the chip and can steal the data inside (skimming). Second, the attacker can intercept the communication between tag and reader (eavesdropping). Last, the attacker can track the exact location of the tag or the person.
In Thailand, most of the farms are trying to adopt an RFID system in farm management, but RFID technology is widening the gap between poor and rich farmers. Poor farmers are usually less educated people who have hardly had any experience using digital technology like RFID. On the other hand, well-educated wealthy farmers face low entry barriers and easily adopt the technology. Rich farmers armed with innovative technology not only make enormous fortunes by increasing efficiency but also by replacing poor labors with RFID embedded devices. According to the Thailand Ministry of Labor (2006), most farm labors are afraid of being replaced. Unfortunately, this phenomenon eventually correlates to a serious gap between rich and poor.
The government has invested a huge amount of money to buy necessary devices such as readers, tags, hardware, and so on, but in the long run cost of management will decrease. On the other hand, the waste industry could carry a very heavy debt. The waste contractors have to deal with expensive RFID tag rental and as well as the cost of construction simultaneously. Although this situation is totally unfavorable for them, the waste management industry cannot resist to this policy because the Chinese government is the entity which has made the use of RFID policy and set prices. The industry has no other choice but consent.
Armknecht F, Chen L, Sadeghi AR, Wachsmann C. Anonymous authentication for RFID systems. In: Radio Frequency Identification: Security and Privacy Issues. Berlin Heidelberg: Springer; 2010a. p. 158–75.
Chapter Google Scholar
Armknecht F, Sadeghi AR, Visconti I, Wachsmann C. On RFID privacy with mutual authentication and tag corruption. In: Applied Cryptography and Network Security. Berlin Heidelberg: Springer; 2010b. p. 493–510.
Avoine G, Coisel I, Martin T. Time measurement threatens privacy-friendly RFID authentication protocols. In: Radio Frequency Identification: Security and Privacy Issues. Berlin Heidelberg: Springer; 2010. p. 138–57.
Barut M, Brown R, Freund N, May J, Reinhart E. RFID and corporate responsibility: hidden costs in RFID implementation. Bus Soc Rev. 2006;111:287–303.
Article Google Scholar
Becker C. A new game of leapfrog? RFID is rapidly changing the product-tracking process. Some say the technology--once costs drop--could displace bar-coding. Modern Healthcare. 2004;34:38–40.
Google Scholar
Bilitewski B. From traditional to modern fee systems. Waste Management. 2008;28(12):2760–6.
Castro L, Wamba SF. An inside look at RFID technology. J Technol Manag Innov. 2007;2:128–41.
Chen RS, Chen CC, Yeh KC, Chen YC, Kuo CW. Using RFID technology in food produce traceability. WSEAS Transac Inform Sci Appli. 2008;5:1551–60.
Chowdhury B, Khosla R. RFID-based hospital real-time patient management system. In: Computer and Information Science, 2007. ICIS 2007. 6th IEEE/ACIS International Conference on. 2007. p. 363–8. IEEE.
Ema A, Fujigaki Y. How far can child surveillance go?: Assessing the parental perceptions of an RFID child monitoring system in Japan. Surveillance Soc. 2011;9:132–48.
Ezovski GM, Watkins SE. The electronic passport and the future of government-issued RFID-based identification. In: RFID, 2007. IEEE International Conference on. Grapevine, TX: IEEE; 2007. p. 15–22.
Hossain MA. Exploring the Perceived Measures of Privacy: RFID in Public Applications. Aus J Inform Systems. 2014;18(2):133–48.
Hossain MA, Quaddus M. An adoption-diffusion model for RFID applications in Bangladesh. In: Computers and Information Technology, 2009. ICCIT'09. 12th International Conference on. 2009. p. 127–32. IEEE.
Hossain MF, Sohel MK, Arefin AS. Designing and implementing RFID technology for vehicle tracking in Bangladesh. Dhaka, Bangladesh: National Conference on Communication and Information Security; 2009.
Hossain MA, Quaddus M. Developing and validating a hierarchical model of external responsiveness: A study on RFID technology. Inform Systems Frontiers. 2014;17(1):109–25.
Hwang MS, Wei CH, Lee CY. Privacy and security requirements for RFID applications. J Comput. 2009;20:55–60.
Jensen A, Cazier J, Dave D. The impact of government trust perception on privacy risk perceptions and consumer acceptance of residual RFID technologies. AMCIS 2007 Proceedings, 146. (2007).
Jensen AS, Cazier JA, Dave DS. Mitigating consumer perceptions of privacy and security risks with the use of residual RFID technologies through governmental trust. J Inform Syst Security. 2008;4:41–66.
Jules A. RFID security and privacy: A research survey. Selected Areas Commun IEEE J. 2006;24:381–94.
Infotech. RFID based Waste Management System. 2013. http://www.slideshare.net/iaitoinfotech/rfid-in-waste-management-slide-share.
Ketprom U, Mitrpant C, Lowjun P. Closing digital gap on RFID usage for better farm management. In: Management of Engineering and Technology, Portland International Center for. Portland, OR: IEEE; 2007. p. 1748–55.
Kim JG. A divide-and-conquer technique for throughput enhancement of RFID anti-collision protocol. Communications Letters, IEEE. 2008;12:474–6.
Kim EM, Pyeon MW, Kang MS, Park JS. A management system of street trees by using RFID. In: Web and Wireless Geographical Information Systems. Berlin Heidelberg: Springer; 2006. p. 66–75.
Konsynski B, Smith HA. Developments in practice x: Radio frequency identification (rfid)-an internet for physical objects. Commun Assoc Inform Systems. 2003;12:19.
Kovavisaruch L, Suntharasaj P. Converging technology in society: opportunity for radio frequency identification (RFID) in Thailand's transportation system. In: Management of Engineering and Technology, Portland International Center for. Portland, OR: IEEE; 2007. p. 300–4.
Kuo CH, Chen HG. The critical issues about deploying RFID in healthcare industry by service perspective. In: Hawaii International Conference on System Sciences, Proceedings of the 41st Annual. Waikoloa, HI: IEEE; 2008. p. 111–1.
Kuo F, Lee Y, Tang CY. The Development of RFID in Healthcare in Taiwan. Bejing: ICEB; 2004. p. 340–5.
Laurie A. Practical attacks against RFID. Network Security. 2007;2007:4–7.
Lee K, Nieto JG, Boyd C. A state-aware RFID privacy model with reader corruption. In: Cyberspace Safety and Security. Berlin Heidelberg: Springer; 2012. p. 324–38.
Li S, Visich JK, Khumawala BM, Zhang C. Radio frequency identification technology: applications, technical challenges and strategies. Sensor Review. 2006;26:193–202.
Lorenc ML. Mark of the Beast: US Government Use of RFID in Government-Issued Documents. The Alb LJ Sci Tech. 2007;17:583.
Meingast M, King J, Mulligan DK. Embedded RFID and everyday things: A case study of the security and privacy risks of the US e-passport. In: RFID, 2007. IEEE International Conference on. Grapevine, TX: IEEE; 2007. p. 7–14.
Murad M, Rehman A, Shah AA, Ullah S, Fahad M, Yahya KM. RFAIDE—An RFID based navigation and object recognition assistant for visually impaired people. In: Emerging Technologies (ICET), 2011 7th International Conference on. Islamabad: IEEE; 2011. p. 1–4.
Murray C. Privacy concerns mount over retail use of RFID technology. EE Times. 2003;2:4–5.
Nanseki. A navigation system for appropriate pesticide use: design and implementation. Agricultural Information Research. 2005;14:207–26.
Naumann I, Hogben G. Privacy features of European eID card specifications. Network Security. 2008;8:9–13.
Perakslis C, Wolk R. Social acceptance of RFID as a biometric security method. In Technology and Society, 2005. Weapons and Wires: Prevention and Safety in a Time of Fear. ISTAS 2005. Proceedings. 2005 International Symposium on (pp. 79-87). IEEE. New York, New York; 2005.
Prado JAD, Monterrey IC, Prado FED. Creating Traffic Knowledge System in Mexico: Applying RFID to Prevent the Vandalism. The 15th International Business Information Management Association Conference. 2010. p. 2042–50.
Prasanth V, Hari PR, Soman KP. Ticketing Solutions for Indian Railways Using RFID Technology. In: Advances in Computing, Control, & Telecommunication Technologies, 2009. ACT'09. Trivandrum, Kerala: International Conference on. 2009. p. 217–9. IEEE.
Ransford B, Sorber J, Fu K. Mementos: system support for long-running computation on RFID-scale devices. Acm Sigplan Notices. 2012;47:159–70.
Reichenbach J. Status and prospects of pay-as-you-throw in Europe–A review of pilot research and implementation studies. Waste Management. 2008;28:2809–14.
Romero A, Lefebvre E. Gaining Deeper Insights into RFID Adoption in Hospital Pharmacies. World. 2013;3:164–75.
Ruan T, Hu H. Application of an RFID-based system for construction waste transport: a case in Shanghai. In: Computational Logistics. Berlin Heidelberg: Springer; 2011. p. 114–26.
RFID Gazette. RFID hybrid tech: Combining GPS for location tracking. Retrieved December 5, 2006, from tec.html http://www.rfidgazette.org/2006/12/index.html .
Schindler R, Schmalbein N, Steltenkamp V, Cave J, Wens B, Anhalt A, et al. SMART TRASH – study on RFID tags and the recycling industry, technical report. TR-1283-EC. Santa Monica, CA: RAND Europe Corporation; 2012.
Shahram M, Manish B. RFID Field Guide: Deploying radio frequency identification systems. New York: Prentice Hall; 2005.
Smith JE. You Can Run, But You Can’t Hide: Protecting Privacy from Radio Frequency Identification Technology. NCJL Tech. 2006;8:249.
Sugahara K. Traceability system for agricultural productsbased on RFID and mobile technology. In: Computer and Computing Technologies in Agriculture II, vol. 3. US: Springer; 2009. p. 2293–301.
Tien L. RFID tags should track inventory, not people. RCR Wireless News, 2004. http://www.rcrwireless.com/20040705/archived-articles/rfid-tags-should-track-inventory-not-people .
Takahashi. “The Father of RFID,” Mercury News, www.siliconvalley.com (June 7, 2004).
Trevarthen A, Michael K. Beyond mere compliance of RFID regulations by the farming community: a case study of the Cochrane dairy farm. In: Management of Mobile Business, 2007. ICMB 2007. International Conference on the. Toronto, Canada: IEEE; 2007. p. 8–8.
Tsai FMC, Huang CM. Cost-Benefit Analysis of Implementing RFID System in Port of Kaohsiung. Procedia-Social Behav Sci. 2012;57:40–6.
Ulatowski LM. Recent developments in RFID technology: weighing utility against potential privacy concerns. ISJLP. 2007;3:623.
USDA APHIS. National Animal Identification System: Animal Identification Number(AIN). Retrieved from the web on June 8, 2005. Available at https://www.aphis.usda.gov/traceability/downloads/NAIS_overview_report.pdf.
Vining J. RFID Alone Can’t Resolve Cargo Container Security Issues. 2005.
Weinstein R. RFID: a technical overview and its application to the enterprise. IT professional. 2005;7:27–33.
Werb J, Sereiko P. More than just tracking. Frontline Solutions. 2002;3:11–42.
Wicks AM, Visich JK, Li S. Radio frequency identification applications in hospital environments. Hosp Top. 2006;84:3–9.
Wyld DC. Delta airlines Tags Baggage with RFID. Re:ID Magazine. 2005;1:63–34.
Wyld DC. RFID: The right frequency for government. Washington DC: IBM Center for the Business of Government. IBM Center; 2005.
Wyld DC. Death sticks and taxes: RFID tagging of cigarettes. Int J Retail Distribution Manag. 2008;36:571–82.
Yonhap news. 2013. http://news.naver.com/main/read.nhn?.mode=LSD&mid=sec&sid1=102&oid=001&aid=0003353674 .
Zhang R. A transportation security system applying RFID and GPS. J Ind Engr Manag. 2013;6(1):163–74.
Download references
Acknowledgments
This paper was supported by the research grant of Seoul National University Foundation (Korea Institute of Public Affairs) in 2015.
Author information
Authors and affiliations.
Korea Institute of Public Affairs, Graduate School of Public Administration of Seoul National University, Seoul, Republic of Korea
Kwangho Jung
Graduate School of Public Administration of Seoul National University, Seoul, Republic of Korea
Sabinne Lee
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Kwangho Jung .
Additional information
Competing interests.
The authors declare that they have no competing interests.
Authors’ contributions
KJ and SL carried out a systematic literature review not only from not only technological point of view but also from social scientific point of view. Both authors read and approved the final manuscript.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
Reprints and permissions
About this article
Cite this article.
Jung, K., Lee, S. A systematic review of RFID applications and diffusion: key areas and public policy issues. J. open innov. 1 , 9 (2015). https://doi.org/10.1186/s40852-015-0010-z
Download citation
Received : 07 July 2015
Accepted : 11 August 2015
Published : 04 September 2015
DOI : https://doi.org/10.1186/s40852-015-0010-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Digital identification
- Digital delivery
- Contactless smart card
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Journal Proposal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu
- Subscribe SciFeed
- Recommended Articles
- PubMed/Medline
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
A review of iot sensing applications and challenges using rfid and wireless sensor networks.

1. Introduction
2. rfid sensing technology.
- Analog RFID sensing : These systems perform an analog processing of the physical signals related to the communication between the reader and the tag, with no dedicated sensing electronics. The reader is able to obtain much more information about the target, more than just identification, without the need for additional electronics. Analog RFID sensing relies on the knowledge that the performance of an RFID tag is affected by the hosting object, and hence it is possible to retrieve sensing data simply by evaluating the variation of the signals backscattered from the tags. Sensitive coating materials or lumped components displaced over the antenna are also used to achieve a more specific response of the device [ 12 ].
- Digital RFID sensing : Tags are integrated with electronic components, such as sensory material, analog-to-digital converters, and a microcrontroller, to make an integrated sensor module [ 13 ]. These systems are referred to as Computational RFID (CRFID). CRFID systems permit running programs on embedded computers using only scavenged Radio Frequency (RF) energy. Battery free, “invisible” sensing and computation is key to truly ubiquitous computing applications for the IoT. The CRFID tag is used as a communication interface for transmitting data. Passive RFID sensors harvest the RF energy from RF radiation to power the circuit, perform the sensing task, and save the data in the RFID chip to be accessed by RFID readers.
2.1. Challenges
- Limited energy harvester and read range : These are considered to be two of the most important limitations because both sensor nodes and RFID tags are made of scarce resources [ 14 , 15 ]. Existing RFID platforms implemented in the IoT are mostly passive, that is, they cannot operate or sense data without being placed inside the reader’s reading zone. The integrated circuit (IC), the microcontroller unit, and the sensing module on a passive tag are powered by harvesting the RF energy transmitted by the reader, and communicate by backscattering the incident signal. This implementation reduces the manufacturing cost by keeping IC costs low. However, the long-range communication and power hungry sensing capabilities will be limited by the power available at the tag. Furthermore, the maximum power transmitted by the reader is constrained by the Federal Communications Commission (FCC) (or similar regional organization) at 1 W (30 dBm), assuming an antenna with a maximum gain of 6 dBi. Only a fraction of this transmitted RF power is received at the IC after path losses and polarization mismatches. Although all the components are typically designed to be power efficient, the operation of the logic of the sensors is more complex and time consuming. Therefore, it is still a challenge to power all the components and cover the operations of the logic with only harvested RF energy. This challenge is more notable when the sensors are implanted in the materials under test, because the RF signal is attenuated by the surrounding materials and the received RF energy can hardly power all the operations, which seriously affects the read/write range of the RFID sensor.
- Sensor responses collisions : An RFID sensing application is composed of at least one reader and several RFID sensors, which include at least one sensor. The tag collision problem acquires the main focus when interrogating these tags. The communication channel is shared among them and, therefore, their responses need to be arbitrated in order to avoid simultaneous responses that will lead to collisions. This problem is one of the main causes of energy wastage, increases in identification time, and decreases in the read rate [ 16 ]. Due to the current increasing number of sensor tags in a shared reader interrogation area, this problem is the subject of increasing concern. Efficient anti-collision protocols for streaming sensor data are needed to minimize the impact of collisions.
- Lack of flexibility : Current sensor RFID tags usually come with a single sensor or, in some cases, with multiple built-in sensors. But once they are manufactured, they cannot be replaced or reconfigured without a costly redesign and reproduction. Since the IoT is an open, dynamic, and versatile global networking and sensing system, the generality, modularity, and reconfigurability of the sensing nodes/platform are essential for the their adoption in the future IoT architecture. Furthermore, commercial RFID readers are generally black box systems that only allow limited configuration [ 16 ] and are only capable of implementing the current UHF RFID communication standard named EPCglobal Class 1 Generation 2 (EPC C1G2) (ISO/IEC 18000-63). Thus, it is not possible to implement new communication protocols beyond the EPC C1G2 that meet the demands of novel and emerging RFID-based sensors. Although there are some publications in the literature that propose a flexible RFID reader based on a software-defined radio, there is a lot of room for improvement in this regard [ 17 ]. Another limitation is related to the current lack of an UHF RFID mobile sensing platform. Currently are portable commercial RFID readers, which do not need to be plugged in to operate, but there is a lack of a smartphone-based platform that enables the use of unmodified smartphones to read data from UHF RFID sensors. It would be very beneficial and practical to be able to read RFID sensor tags by using a common smartphone with some additional hardware components (such as an UHF antenna).
- Cost : The cost of commercial RFID readers is relatively high compared to the cost of sensors and tags.
2.2. Applications
3. wireless sensor networks, 3.1. challenges.
- Reliability : Nodes must be available at any time to monitor critical areas, but this can lead to unnecessary communications or computations, which can cause the batteries of the nodes to run out of charge. Also, time synchronization between the nodes and spectrum sharing techniques are of the utmost importance to ensure the integrity of the data or avoid uncertainty in the sensed data, without consuming all the radio resources [ 37 ].
- Energy consumption , including harvesting, conservation and usage. Nodes must be power efficient and must be capable of low power communication with low cost on-node processing. Whether the nodes use a battery or harvest energy from the surroundings, their power consumption must be low in order to maximize their efficiency. The optimal node would be able to harvest energy from its surroundings and not waste any of that energy in its operations [ 38 ].
- Scalability : IoT solutions will involve thousands of smart devices, and this number will be dramatically increased in the coming years. Hence, a WSN must be sufficiently scalable so as to be able to integrate new nodes and provide (Quality of Service) QoS services involving heterogeneous devices, working for long periods [ 39 ].
- Communication mechanisms and protocols : There are 4 types of MAC communication strategies: Fixed, On-demand, Random, and Hybrid assignment [ 36 ]. Fixed assignment protocols divide the resources between the nodes in predefined time slots; On-demand protocols provide resources to each node on demand; Random Assignment protocols randomly divide the resources; and Hybrid Assignment protocols combine the previous three strategies. The Fixed assignment strategy adds determinism at the expense of an inefficient use of time; whilst the On-demand assignment lacks determinism and is not suitable for industrial real-time applications. In between these strategies are the Hybrid assignment strategies, combining fixed and random assignments. Moreover, the WSNs used in the IoT need to implement Internet functionalities. The most used one is the Internet Protocol (IP), to allow the routing of the messages among the wireless network.

3.2. Applications
4. iot promising technologies, 4.1. rfid and wsn integration.
- The category of RFID tags with WSN nodes involves the possibility that the end node can be an RFID tag or a WSN node (see Figure 4 a), and thus, there are two cases: integrated sensors with limited communication capabilities for the first case, and integrated sensors with extended communication capabilities for the second [ 58 ].
- For the category of RFID readers with WSN nodes (see Figure 4 b), the integration is at the reader level. This increases the capabilities of the integrated system, allowing the identification of a tag, through the WSN node, at a very long distance, at the expense of an increase in the WSN node’s power consumption [ 8 ].
- The last category, hybrid integration, is a mixture of the previous two (see Figure 4 c). An RFID reader is attached to a WSN gateway and thus, RFID tags coexist with WSN nodes as sensors. This Reader/Gateway collects data from either RFID sensors or sensor nodes and forwards the data to the coordinator of the network. Figure 4 shows a diagram of an example of hybrid integration.
4.2. Wearable Sensors
- Public Land Mobile Networks: These range from 2G to future 5G communication systems, which support machine to machine communications (M2M) or purpose specific systems for sensor integration, such as NB-IoT or Cat. Mobile terminals can be used as opportunistic sensor platforms or to provide access gateways in tethered operation to WBAN/WPAN networks.
- WPAN/WBAN: These are wireless communication systems which are intended to support short to medium range communications, have network topologies that are reconfigurable in the face of adverse network conditions (i.e., ad-hoc network configurations), and large scalability. The majority of communication systems have been developed under the scope of IEEE 802.15 standards, such as Bluetooth, ZigBee, RFID/NFC liaison or Ultrawideband (UWB), while there are other alternatives, such as ANT, Zarlink, Sensium, Z-Wave, RuBee, Dash7 and EnOcean, among others.
- WLAN: Wireless local area networks provide multiple functionalities, such as communication gateway capabilities or support for guiding and location systems.
- Small form factor and ergonomics: Typically, the circuit footprint is on the order of several mm 2 in order to enable their integration with wearable platforms, such as wristbands, watches, earrings, necklaces, or in different types of textiles. Novel approaches have been followed to increase the integration, employing additive manufacturing techniques (ergonomic casings and enclosures, conductive screen printing of electrodes, sensors and antennas), embroidering conductive wires within textiles, or flexible/stretchable electronics.
- Reduced energy consumption: Wearable applications usually have the use of only limited energy sources. Moreover, an extended lifetime of the energy source is a desirable requirement, to increase the user’s comfort in terms of device downtime owing to the need to recharge the device. Energy reduction is provided by hardware (e.g., the use of ultra-low power electronics, optimized circuit routing, etc.) and communication protocol/software (optimized device states and modified MAC protocols, energy efficient routing protocols, cooperative and heterogeneous network schemes). Other aspects, such as restrictions on the antenna size, non-optimal antenna matching conditions, and the influence of the human body on the antenna radiation diagram, also limit the performance and hence affect the available energy. New approaches have been proposed, such as the use of artificial electromagnetic bandgap embedded antennas in order to enhance antenna performance in contact with the human body. Extended device operation can be provided by using energy harvesting schemes (with different options, such as solar energy, thermo-electric conversion such as Peltier cells, piezo-electric transducers or RF/electromagnetic harvesting by using rectennas).
- Seamless communication capabilities: Wearable devices require communication systems which can efficiently transmit and receive the required information, providing optimal coverage/capacity response, with straightforward connection capabilities in order to ease their operation by the users. WBAN/WPAN communication systems, such as Bluetooth (BT)/Bluetooth Low Energy (BLE), RFID or Near Field Communications (NFC) provide simple association procedures, requiring little or no configuration by the user under conventional operating conditions. Moreover, coverage/capacity restrictions must also be taken into consideration, in aspects such as the transceiver density, which can increase the overall interference levels and hence reduce the quality of service parameters. Moreover, user interaction and adoption levels will also be biased by normalization in the use of the technology, in terms of accepting information exchange and ensuring adequate privacy and security levels.
| Technology | Challenges | Solutions |
|---|---|---|
| RFID | Energy harvesting Inflexibility Platform Cost Communication protocols Coverage/Read range | [ , , , ] [ , , ] [ , , , ] [ , ] [ , , , ] [ , ] |
| WSN | Latency Reliability Data rate Energy consumption Scalability Communication protocols Security & privacy | [ , , ] [ , , , , ] [ , ] [ , , ] [ , , ] [ , ] [ , , , ] |
| RFID-WSN | Coordination Communication protocols Energy management & Accuracy of sensors | [ , , ] [ , ] [ , , ] |
5. Conclusions
Author contributions, conflicts of interest.
- Chopra, K.; Gupta, K.; Lambora, A. Future Internet: The Internet of Things—A Literature Review. In Proceedings of the International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon), Faridabad, India, 14–16 Feburary 2019; pp. 135–139. [ Google Scholar ]
- Nagakannan, M.; Inbaraj, C.J.; Kannan, K.M.; Ramkumar, S. A Recent Review on Iot Based Techniques and Applications. In Proceedings of the 2nd International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), Palladam, India, 30–31 August 2018; pp. 70–75. [ Google Scholar ]
- Ji, W.; Li, L.; Zhou, W. Design and Implementation of a RFID Reader/Router in RFID-WSN Hybrid System. Future Internet 2018 , 10 , 106. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Finkenzeller, K. RFID Handbook: Radio-Frequency Identification Fundamentals and Applications ; Wiley: Hoboken, NJ, USA, 1999. [ Google Scholar ]
- Souto, G.; Muralter, F.; Arjona, L.; Landaluce, H.; Perallos, A. Protocol for Streaming Data from an RFID Sensor Network. Sensors 2019 , 19 , 3148. [ Google Scholar ] [ CrossRef ] [ PubMed ] [ Green Version ]
- Mitrokotsa, A.; Douligeris, C. Integrated RFID and Sensor Networks: Architectures and Applications. RFID Sens. Netw. 2009 , 5 , 11–535. [ Google Scholar ]
- Torres, B.; Pang, Q.; Skelton, G.W.; Bridges, S.; Meghanathan, N. Integration of an RFID reader to a wireless sensor network and using it to identify an individual carrying RFID tags. Int. J. Ad Hoc Sens. Ubiquitous Comput. 2010 , 1 , 1–15. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Adame, T.; Bel, A.; Carreras, A.; Melià-Seguí, J.; Oliver, M.; Pous, R. CUIDATS: An RFID-WSN hybrid monitoring system for smart health care environments. Futur. Gener. Comput. Syst. 2016 , 78 , 602–615. [ Google Scholar ] [ CrossRef ]
- Al-Turjman, F.M.; Al-Fagih, A.E.; Hassanein, H.S. A novel cost-effective architecture and deployment strategy for integrated RFID and WSN systems. In Proceedings of the International Conference on Computing, Networking and Communications, San Diego, CA, USA, 28–31 January 2013; pp. 835–839. [ Google Scholar ]
- Yang, L.; Xu, M. The hardware design of frequency identification system based on Zigbee technology. J. Harbin Inst. Tech. Yanghnol. Univ. 2012 , 17 , 65–68. [ Google Scholar ]
- Wang, L.; Xu, L.; Bi, Z.; Xu, Y. Data cleaning for RFID and WSN integration. IEEE Trans. Ind. Inform. 2013 , 10 , 408–418. [ Google Scholar ] [ CrossRef ]
- Cchiuzzi, C.; Caizzone, S.; Marrocco, G. Passive UHF RFID antennas for sensing applications: Principles, methods, and classifications. IEEE Antennas Propag. Mag. 2013 , 55 , 14–34. [ Google Scholar ] [ CrossRef ]
- EVAL01-Spectre-RM. Available online: http://www.farsens.com/en/products/eval01-spectre-rm/ (accessed on 10 February 2020).
- Kantareddy, S.N.R.; Mathews, I.; Bhattacharyya, R.; Peters, I.M.; Buonassisi, T.; Sarma, S.E. Long Range Battery-Less PV-Powered RFID Tag Sensors. IEEE Internet Things J. 2019 , 6 , 6989–6996. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Sample, A.P.; Braun, J.; Parks, A.; Smith, J.R. Photovoltaic enhanced UHF RFID tag antennas for dual purpose energy harvesting. In Proceedings of the IEEE International Conference on RFID, Orlando, FL, USA, 12–14 April 2011; pp. 146–153. [ Google Scholar ]
- Arjona, L.; Landaluce, H.; Perallos, A.; Parks, A. Survey and analysis of RFID DFSA anti-collision protocols and their physical implementation capabilities. In NOVA Chapter: RFID Technology: Design Principles, Applications and Controversies ; NOVA Science Pub.: Hauppauge, NY, USA, 2018; ISBN 978-1-53613-250-2. [ Google Scholar ]
- Arjona, L.; Landaluce, H.; Perallos, A.; Souto, G. Protocol for Streaming Data from an RFID Sensor Network. In Proceedings of the International Conference on Ubiquitous Computing and Ambient Intelligence (UCAmI 2018), Punta Cana, Dominican Republic, 4–7 December 2018. [ Google Scholar ]
- Rashee, A.; Iranmanes, E.; Li, W.; Fen, X.; Andrenk, A.S.; Wan, K. Experimental study of human body effect on temperature sensor integrated RFID tag. In Proceedings of the IEEE International Conference on RFID Technology & Application, Warsaw, Poland, 20–22 September 2017; pp. 243–247. [ Google Scholar ]
- Yang, S.; Crisp, M.; Penty, R.V.; White, I.H. RFID Enabled Health Monitoring System for Aircraft Landing Gear. IEEE J. Radio Freq. Identif. 2018 , 2 , 159–169. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Fuhrer, P.; Guinard, D. Building a Smart Hospital Using RFID Technologies: Use Cases and Implementation ; Department of Informatics, University of Fribourg: Fribourg, Switzerland, 2006. [ Google Scholar ]
- Bothe, A.; Bauer, J.; Aschenbruck, N. RFID-assisted Continuous User Authentication for IoT-based Smart Farming. In Proceedings of the IEEE International Conference on RFID Technology and Applications, Pisa, Italy, 25–27 September 2019; pp. 505–510. [ Google Scholar ]
- Saggin, B.; Belaizi, Y.; Vena, A.; Sorli, B.; Guillard, V.; Dedieu, I. A Flexible Biopolymer based UHF RFID-Sensor for food quality monitoring. In Proceedings of the IEEE International Conference on RFID Technology and Applications, Pisa, Italy, 25–27 September 2019; pp. 484–487. [ Google Scholar ]
- Liu, M.; Wang, H.; Yang, Y.; Zhang, Y.; Ma, L.; Wang, N. RFID 3-D Indoor Localization for Tag and Tag-Free Target Based on Interference. IEEE Trans. Instrum. Meas. 2019 , 68 , 718–3732. [ Google Scholar ] [ CrossRef ]
- Zhang, Y.; Ma, Y.; Liu, K.; Wang, J.; Li, S. RFID based Vehicular Localization for Intelligent Transportation Systems. In Proceedings of the IEEE International Conference on RFID Technology and Applications, Pisa, Italy, 25–27 September 2019; pp. 267–272. [ Google Scholar ]
- Belenguer, F.M.; Martínez-Millana, A.; Salcedo, A.M.; Núñez, J.H.A. Vehicle Identification by Means of Radio-Frequency-Identification Cards and Magnetic Loops. IEEE Trans. Intell. Transp. Syst. 2019 , 1–9. [ Google Scholar ] [ CrossRef ]
- Farhat, H.; Iliev, P.; Marriage, P.; Rolland, N. An Added Value Alternative to RAIN RFID Items Characterization in Retail. IEEE Access 2018 , 6 , 32430–32439. [ Google Scholar ] [ CrossRef ]
- Anssens, C.; Rolland, N.; Rolland, P. A sensor network based on RFID inventory for retail application. In Proceedings of the IEEE International Conference on RFID-Technologies and Applications, Sitges, Spain, 15–16 September 2011; pp. 64–67. [ Google Scholar ]
- Xu, H.; Wu, M.; Li, P.; Zhu, F.; Wang, R. An RFID Indoor Positioning Algorithm Based on Support Vector Regression. Sensors 2018 , 18 , 1504. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Zhou, J.; Zhang, H.; Mo, L. Two-dimension localization of passive RFID tags using AOA estimation. In Proceedings of the Instrumentation and Measurement Technology Conference, Beijing, China, 10–12 May 2011; pp. 1–5. [ Google Scholar ]
- Shao, S.; Burkholder, R.J. Item-Level RFID Tag Location Sensing Utilizing Reader Antenna Spatial Diversity. IEEE Sens. J. 2013 , 13 , 3767–3774. [ Google Scholar ] [ CrossRef ]
- Alvarez-Narciandi, G.; Motroni, A.; Pino, M.R.; Buffi, A.; Nepa, P. A UHF-RFID gate control system based on a Convolutional Neural Network. In Proceedings of the IEEE International Conference on RFID Technology and Applications, Pisa, Italy, 25–27 September 2019; pp. 353–356. [ Google Scholar ]
- Melià-Seguí, J.; Vilajosana, X. Ubiquitous moisture sensing in automaker industry based on standard UHF RFID tags. In Proceedings of the IEEE International Conference on RFID (RFID), Phoenix, AZ, USA, 2–4 April 2019; pp. 1–8. [ Google Scholar ]
- Ranganathan, V.; Nakahara, J.; Samejima, S.; Tolley, N.; Khorasani, A.; Moritz, C.T.; Smith, J.R. NeuralCLIP: A Modular FPGA-Based Neural Interface for Closed-Loop Operation. In Proceedings of the 9th International IEEE/EMBS Conference on Neural Engineering (NER), San Francisco, CA, USA, 20–23 March 2019; pp. 791–794. [ Google Scholar ]
- Arjona, L.; Rosenthal, J.; Smith, J.R.; Moritz, C.T. High Performance Flexible Protocol for Backscattered-Based Neural Implants. In Proceedings of the IEEE-APS Topical Conference on Antennas and Propagation in Wireless Communications (APWC), Granada, Spain, 9–13 September 2019; pp. 276–280. [ Google Scholar ]
- Rashvand, H.F.; Abedi, A.; Alcaraz-Calero, J.M.; Mitchell, P.D.; Mukhopadhyay, S.C. Wireless Sensor Systems for Space and Extreme Environments: A Review. IEEE Sens. J. 2014 , 14 , 3955–3970. [ Google Scholar ] [ CrossRef ]
- Seferagić, A.; Famaey, J.; Poortera, E.D.; Hoebeke, J. Survey on Wireless Technology Trade-Offs for the Industrial Internet of Things. Sensors 2020 , 20 , 488. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Yıldırım, K.S.; Aantjes, H.; Pawełczak, P.; Majid, A.Y. On the Synchronization of Computational RFIDs. IEEE Trans. Mob. Comput. 2019 , 18 , 2147–2159. [ Google Scholar ] [ CrossRef ]
- Kranenburg, V.; Bassi, A. IoT Challenges. Commun. Mob. Comput. 2012 , 1 , 1–5. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Saelens, M.; Hoebeke, J.; Shahid, A.; Poorter, E.D. Impact of EU duty cycle and transmission power limitations for sub-GHz LPWAN SRDs: An overview and future challenges. EURASIP J. Wirel. Commun. Netw. 2019 , 2019 , 219. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Hu, Y.C.; Perrig, A.; Johnson, D.B. Packet leashes: A defense against wormhole attacks in wireless networks. In Proceedings of the IEEE INFOCOM 2003. Twenty-Second Annual Joint Conference of the IEEE Computer and Communications Societies, San Francisco, CA, USA, 30 March–3 April 2003; Volume 3, pp. 1976–1986. [ Google Scholar ]
- Farooq, M.U.; Waseem, M.; Mazhar, S.; Khairi, A.; Kamal, T. A review on Internet of Things (IoT). Int. J. Comput. Appl. 2015 , 113 , 1–7. [ Google Scholar ]
- Cankar, M.; Stanovnik, S.; Landaluce, H. Transportation ecosystem framework in Fog to Cloud environment. In Proceedings of the 2018 IEEE/ACM International Conference on Utility and Cloud Computing Companion (UCC Companion), Zurich, Switzerland, 17–20 December 2018; pp. 266–271. [ Google Scholar ]
- Sharma, R.; Shiva, P. Latest Trends and Future Directions of Localization Algorithms in Wireless Sensor Networks. In Proceedings of the 2019 6th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 13–15 March 2019. [ Google Scholar ]
- Xu, J.; Liu, W.; Lang, F.; Zhang, Y.; Wang, C. Distance measurement model-based on RSSI in WSN. Wirel. Sens. Netw. 2010 , 2 , 606. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Rong, P.; Sichitiu, M.L. Angle of arrival localization for wireless sensor networks. In Proceedings of the 3rd Annual IEEE Communications Society onSensor and Ad Hoc Communications and Networks (SECON), Reston, VA, USA, 28 September 2006; Volume 1, pp. 374–382. [ Google Scholar ]
- Catovic, A.; Sahinoglu, Z. The Cramer-Rao bounds of hybrid TOA/RSS and TDOA/RSS location estimation schemes. IEEE Commun. Lett. 2004 , 8 , 626–628. [ Google Scholar ] [ CrossRef ]
- Niculescu, D.; Nath, B. DV-based positioning in ad hoc networks. Telecommun. Syst. 2003 , 22 , 267–280. [ Google Scholar ] [ CrossRef ]
- Yang, S.; Yi, J.; Cha, H. HCRL: A hop-count-ratio-based localization in wireless sensor networks. In Proceedings of the 4th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON), San Diego, CA, USA, 18–21 June 2007. [ Google Scholar ]
- Chen, H.; Huang, P.; Martins, M.; So, H.C.; Sezaki, K. Novel centroid localization algorithm for three-dimensional wireless sensor networks. In Proceedings of the IEEE 4th International Conference on Wireless Communications, Networking and Mobile Computing (WiCOM), Dalian, China, 12–14 October 2008; pp. 1–4. [ Google Scholar ]
- Wang, J.Z.; Jin, H. Improvement on APIT localization algorithms for wireless sensor networks. In Proceedings of the IEEE International Conference on Networks Security, Wireless Communications and Trusted Computing (NSWCTC), Wuhan, China, 25–26 April 2009; Volume 1, pp. 719–723. [ Google Scholar ]
- Deshpande, N.; Grant, E.; Henderson, T.C. Target localization and autonomous navigation using wireless sensor networks—A pseudogradient algorithm approach. IEEE Syst. J. 2013 , 8 , 93–103. [ Google Scholar ] [ CrossRef ]
- Diez, L.E.; Bahillo, A.; Otegui, J.; Otim, T. Step length estimation methods based on inertial sensors: A review. IEEE Sens. J. 2018 , 18 , 6908–6926. [ Google Scholar ] [ CrossRef ]
- Shubhangiborkar, T. A Review on WSN for Detection of Natural Disaster Using Data Mining. Int. J. Eng. Sci. 2018 , 8 , 17500–17503. [ Google Scholar ]
- Boubrima, A.; Bechkit, W.; Rivano, H. Optimal WSN Deployment Models for Air Pollution Monitoring. IEEE Trans. Wirel. Commun. 2017 , 16 , 2723–2735. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Teixeira, E.; Pedreiras, P.; Mota, A. Low Power WSN Protocol for Smart Green Homes. In Proceedings of the 24th IEEE International Conference on Emerging Technologies and Factory Automation, Zaragoza, Spain, 10–13 September 2019; pp. 1411–1414. [ Google Scholar ]
- Ouyang, F.; Cheng, H.; Lan, Y.; Zhang, Y.; Yin, X.; Hu, J.; Peng, X.; Wang, G.; Chen, S. Automatic Delivery and Recovery System of Wireless Sensor Networks (WSN) Nodes Based on UAV for Agricultural Applications. Comput. Electron. Agric. 2019 , 162 , 31–43. [ Google Scholar ] [ CrossRef ]
- Salim, C.; Mitton, N. Machine Learning Based Data Reduction in WSN for Smart Agriculture. In Proceedings of the 34th International Conference on Advanced Information Networking and Applications (AINA), Caserta, Italy, 15–17 April 2020. [ Google Scholar ]
- Anjum, S.S.; Noor, R.M.; Anisi, M.H.; Ahmedy, I.B.; Othman, F.; Alam, M.; Khan, M.K. Energy Management in RFID-Sensor Networks: Taxonomy and Challenges. IEEE Internet Things J. 2019 , 6 , 250–266. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Zhang, Y.; Yang, L.T.; Chen, J. RFID and Sensor Networks: Architectures, Protocols, Security, and Integrations ; CRC Press: Boca Raton, FL, USA, 2017. [ Google Scholar ]
- Liu, H.; Bolic, M.; Nayak, A.; Stojmenovic, I. Taxonomy and challenges of the integration of RFID and wireless sensor networks. IEEE Netw. 2008 , 22 , 26–35. [ Google Scholar ] [ CrossRef ]
- Onieva, E.; Osaba, E.; Angulo, I.; Moreno, A.; Bahillo, A.; Perallos, A. Improvement of Drug Delivery Routes Through the Adoption of Multi-Operator Evolutionary Algorithms and Intelligent Vans Capable of Reporting Real-Time Incidents. IEEE Trans. Autom. Sci. Eng. 2017 , 14 , 1009–1019. [ Google Scholar ] [ CrossRef ]
- Selinis, I.; Katsaros, K.; Allayioti, M.; Vahid, S.; Tafazolli, R. The Race to 5G Era, LTE and Wi-Fi. IEEE Access 2018 , 6 , 56598–56636. [ Google Scholar ] [ CrossRef ]
- Ghamari, M.; Janko, B.; Sherratt, R.S.; Harwin, W.; Piechockic, R.; Soltanpur, C. A Survey on Wireless Body Area Networks for eHealthcare Systems in Residential Environments. Sensors 2016 , 16 , 831. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Hall, P.S.; Hao, Y. Antennas and Propagation for Body-Centric Wireless Communications , 2nd ed.; Artech House: Norwood, MA, USA, 2012. [ Google Scholar ]
- Ashyap, A.Y.I.; Dahlan, S.H.B.; Abidin, Z.Z.; Abbasi, M.I.; Kamarudin, M.R.; Majid, H.A.; Dahri, M.H.; Jamaluddin, M.H.; Alomainy, A. An Overview of Electromagnetic Band-Gap Integrated Wearable Antennas. IEEE Access 2020 , 8 , 7641–7658. [ Google Scholar ] [ CrossRef ]
- Hong, S.; Lee, S.; Kim, D.-H. Materials and Design Strategies of Stretchable Electrodes for Electronic Skin and Its Applications. Proc. IEEE 2019 , 107 , 2185–2197. [ Google Scholar ] [ CrossRef ]
- Picallo, I.; Klaina, H.; Lopez-Iturri, P.; Sánchez, A.; Méndez-Giménez, L.; Falcone, F. Implementation of Radiating Elements for Radiofrequency Front-Ends by Screen-Printing Techniques for Internet of Things Applications. Sensors 2019 , 19 , 3626. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Celaya-Echarri, M.; Azpilicueta, L.; López-Iturri, P.; Aguirre, E.; Falcone, F. Performance Evaluation and Interference Characterization of Wireless Sensor Networks for Complex High-Node Density Scenario. Sensors 2019 , 19 , 3516. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Hoof, C.V. Frictionless wearable technology: The key to unleashing the power of wearable sensors for health and lifestyle. In Proceedings of the 10th International Conference on Design & Technology of Integrated Systems in Nanoscale Era (DTIS), Naples, Italy, 21–23 April 2015. [ Google Scholar ]
- Altawy, R.; Youssef, A.M. Security Tradeoffs in Cyber Physical Systems: A Case Study Survey on Implantable Medical Devices. IEEE Access 2016 , 4 , 959–979. [ Google Scholar ] [ CrossRef ]
- Andreu-Perez, J.; Leff, D.R.; Ip, H.M.D.; Yang, G.Z. From Wearable Sensors to Smart Implants—Toward Pervasive and Personalized Healthcare. IEEE Trans. Biomed. Eng. 2015 , 62 , 2750–2762. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Tobón, D.P.; Falk, T.H.; Maier, M. Context Awareness in WBANs: A Survey on Medical and Non-Medical Applications. IEEE Wirel. Commun. 2013 , 20 , 30–37. [ Google Scholar ] [ CrossRef ]
- Iqbal, M.H.; Aydin, A.; Brunckhorst, O.; Dasgupta, P.; Ahmed, K. A review of wearable technology in medicine. J. R. Soc. Med. 2016 , 109 , 372–380. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Epps, J.; Chen, S. Automatic Task Analysis. Toward Wearable Behaviometrics. IEEE Syst. Man Cybern. Mag. 2018 , 4 , 15–20. [ Google Scholar ] [ CrossRef ]
- Wang, L.; Jones, D.; Chapman, G.J.; Siddle, H.J.; Russell, D.A.; Alazmani, A.; Culmer, P. A Review of Wearable Sensor Systems to Monitor Plantar Loading in the Assessment of Diabetic Foot Ulcers. IEEE Trans. Biomed. Eng. (Early Access) 2019 . [ Google Scholar ] [ CrossRef ]
- Fallmann, S.; Chen, L. Computational Sleep Behavior Analysis: A Survey. IEEE Access 2019 , 7 , 142421–142440. [ Google Scholar ] [ CrossRef ]
- Aguirre, E.; Led, S.; Lopez-Iturri, P.; Azpilicueta, L.; Serrano, L.; Falcone, F. Implementation of Context Aware e-Health Environments Based on Social Sensor Networks. Sensors 2016 , 16 , 310. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Aroganam, G.; Manivannan, N.; Harrison, D. Review on Wearable Technology Sensors Used in Consumer Sport Applications. Sensors 2019 , 19 , 1983. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Lopez-Iturri, P.; Aguirre, E.; Azpilicueta, L.; Astrain, J.J.; Villadangos, J.; Falcone, F. Radio Characterization for ISM 2.4 GHz Wireless Sensor Networks for Judo Monitoring Applications. Sensors 2014 , 14 , 24004–24028. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Lopez-Iturri, P.; Aguirre, E.; Azpilicueta, L.; Astrain, J.J.; Villadangos, J.; Falcone, F. Implementation and Analysis of ISM 2.4 GHz Wireless Sensor Network Systems in Judo Training Venues. Sensors 2016 , 16 , 1247. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Mardonova, M.; Choi, Y. Review of Wearable Device Technology and Its Applications to the Mining Industry. Energies 2018 , 11 , 547. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Aguirre, E.; Lopez-Iturri, P.; Azpilicueta, L.; Astrain, J.J.; Villadangos, J.; Santesteban, D.; Falcone, F. Implementation and Analysis of a Wireless Sensor Network-Based Pet Location Monitoring System for Domestic Scenarios. Sensors 2016 , 16 , 1384. [ Google Scholar ] [ CrossRef ] [ PubMed ] [ Green Version ]
- Barriuso, A.L.; Villarrubia González, G.; De Paz, J.F.; Lozano, Á.; Bajo, J. Combination of Multi-Agent Systems and Wireless Sensor Networks for the Monitoring of Cattle. Sensors 2018 , 18 , 108. [ Google Scholar ] [ CrossRef ] [ PubMed ] [ Green Version ]
Click here to enlarge figure
| continuous patient monitoring inter-departmental communications patients’ mobility Efficient emergency dispatching [ , , ] | sensor innovations smart irrigation smart tractors monitoring key parameters [ , ] | smart roads environment-connected vehicles people-centric integrated transportation [ , , ] |
| security process automation real-time stock control product quality control [ , ] | smart maintenance environment-aware objects real-time monitoring real-time monitoring of the platforms [ , , ] | biomedical device communications low-power communications backscatter communications [ , ] |
| Technology | Description and Main Applications |
|---|---|
| RFID | Radio Frequency Identification Very low power identification, tracking, sensing, indoor positioning |
| NFC | Near Field Communications Very short range identification, tracking, sensing |
| BT/BLE | Low Energy Support short to medium range communications. Indoor positioning |
| 2G and 5G | Mobile communications network. Support M2M communications, sensor integration |
| ZigBee | Communication protocol for WPAN Short distance, low complexity, power, and rate sensor data transmission |
| UWB | Ultra Wide Band radio techonology Short-range indoor applications. Real-time positioning systems |
| Requirements | Enabling Technologies | Application Domains |
|---|---|---|
| Small form factor-ergonomics | Additive manufacturing techniques | Sports-Leisure (training, injury monitoring, competition assistance) |
| Reduced energy consumption | Energy harvesting supercapacitor/batteries-ultra low power consumption | Healthcare (body signal monitoring, ambient assisted living, telemedicine) |
| Small/moderate coverage-transmission rate | WBAN/WPAN-PLMN-WLAN communication systems | Location and tracking (infants, industrial security, livestock/domestic pet tracking and monitoring) |
Share and Cite
Landaluce, H.; Arjona, L.; Perallos, A.; Falcone, F.; Angulo, I.; Muralter, F. A Review of IoT Sensing Applications and Challenges Using RFID and Wireless Sensor Networks. Sensors 2020 , 20 , 2495. https://doi.org/10.3390/s20092495
Landaluce H, Arjona L, Perallos A, Falcone F, Angulo I, Muralter F. A Review of IoT Sensing Applications and Challenges Using RFID and Wireless Sensor Networks. Sensors . 2020; 20(9):2495. https://doi.org/10.3390/s20092495
Landaluce, Hugo, Laura Arjona, Asier Perallos, Francisco Falcone, Ignacio Angulo, and Florian Muralter. 2020. "A Review of IoT Sensing Applications and Challenges Using RFID and Wireless Sensor Networks" Sensors 20, no. 9: 2495. https://doi.org/10.3390/s20092495
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
Advertisement
A Review of RFID in Supply Chain Management: 2000–2015
- Original Article
- Published: 03 June 2016
- Volume 17 , pages 189–228, ( 2016 )
Cite this article

- Ahmed Musa 1 &
- Al-Amin Abba Dabo 1
5101 Accesses
43 Citations
1 Altmetric
Explore all metrics
This paper presents a systematic literature review of papers that were published in academic journals on the applications of radio frequency identification (RFID) in supply chain management between the years 2000 and 2015. As the literature on RFID is not confined to specific disciplines or repositories, this paper proposes a discipline-based framework for classifying RFID literature. Five main classification categories are used in this paper: technology, supply chain management, research methodology, application industries, and social aspects. The paper then focuses on the category of supply chain management and reviews 1187 articles that were published between 2000 and 2015 in rated journals. All the papers reviewed are further classified into eight subclasses under this category of supply chain management. The review yields useful insights into the anatomy of RFID literature in supply chain management, enhances evidence-based knowledge, and contributes to informing practice, policymaking and future research. The review reveals that even presently, despite technical and cost challenges, enormous potential exists for the application of RFID in several areas of supply chain management and the prospects are likely to grow into the future. Since RFID solutions have emerged primarily over only the past 20 years, significant research opportunities exist and would need to be addressed to continue to support the technology’s maturation, evaluation, adoption, implementation, and diffusion.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or eBook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Radio Frequency Identification (RFID) and Supply Chain Management

RFID in Retail Supply Chains: Current Developments and Future Potential
Abbreviations.
Business process reengineering
Enterprise resources planning
Fast-moving consumer goods
Information and communications technology
Information system
Information technology
Internet of things
Net present value
Product lifecycle information management
Radio frequency identification
Return on investment
Real-time location system
Supervisory control and data acquisition
- Supply chain management
Unified modeling language
Ahn, H., & Kim, K. (2014). A policy-driven RFID event management framework. Telecommunication Systems, 55 (1), 5–15.
Article Google Scholar
Alomair, B., Lazos, L., & Poovendran, R. (2011). Securing low-cost RFID systems: An unconditionally secure approach. Journal of Computer Security, 19 (2), 229–257. doi: 10.3233/JCS-2010-0406 .
Amini, M., Otondo, R. F., Janz, B. D., & Pitts, M. G. (2007). Simulation modeling and analysis: A collateral application and exposition of RFID technology. Production and Operations Management, 16 (5), 586–598. doi: 10.1111/j.1937-5956.2007.tb00282.x .
Anand, A., & Wamba, S. F. (2013). Business value of RFID-enabled healthcare transformation projects. Business Process Management Journal, 19 (1), 111–145. doi: 10.1108/14637151311294895 .
Angeles, R. (2005). RFID technologies: Supply-chain applications and implementation issues. Information Systems Management, 22 (1), 51–65. doi: 10.1201/1078/44912.22.1.20051201/85739.7 .
Angeles, R. (2013). The structurational model of technology: The case of Dow chemical’s RFID tracking system for hazardous materials. Human Systems Management, 32 (4), 267–282. doi: 10.3233/HSM-130797 .
Google Scholar
Arun, N. (2009). RFID technology: A review of its applications. Engineering and Computer Science, 4 (1), 1253.
Asif, Z., & Mandviwalla, M. (2005). Integrating the supply chain with RFID. Communications of the Association for Information Systems, 15 (24), 393–426.
Attaran, M. (2007). RFID: An enabler of supply chain operations. Supply Chain Management: An International Journal, 12 (4), 249–257. doi: 10.1108/13598540710759763 .
Azevedo, S. G., & Carvalho, H. (2012). Contribution of RFID technology to better management of fashion supply chains. International Journal of Retail and Distribution Management, 40 (2), 128–156. doi: 10.1108/09590551211201874 .
Azevedo, S. G., & Ferreira, J. (2009). RFID technology in retailing: An exploratory study on fashion apparels. The IUP Journal of Managerial Economics, 7 (1), 7–22.
Baars, H., Gille, D., & Strüker, J. (2009). Evaluation of RFID applications for logistics: A framework for identifying, forecasting and assessing benefits. European Journal of Information Systems, 18 (6), 578–591. doi: 10.1057/ejis.2009.32 .
Baldini, G., Oliveri, F., Braun, M., Seuschek, H., & Hess, E. (2012). Securing disaster supply chains with cryptography enhanced RFID. Disaster Prevention and Management, 21 (1), 51–70. doi: 10.1108/09653561211202700 .
Balocco, R., Miragliotta, G., Perego, A., & Tumino, A. (2011). RFID adoption in the FMCG supply chain: An interpretative framework. Supply Chain Management: An International Journal, 16 (5), 299–315. doi: 10.1108/13598541111155820 .
Barut, M., Brown, R., Freund, N., May, J., & Reinhart, E. (2006). RFID and corporate responsibility: Hidden costs in RFID implementation. Business and Society Review, 111 (3), 287–303. doi: 10.1111/j.1467-8594.2006.00273.x .
Bendavid, Y., & Boeck, H. (2011). Using RFID to improve hospital supply chain management for high value and consignment items. Procedia Computer Science, 5 , 849–856. doi: 10.1016/j.procs.2011.07.117 .
Bendavid, Y., Boeck, H., & Philippe, R. (2010). Redesigning the replenishment process of medical supplies in hospitals with RFID. Business Process Management Journal, 16 (6), 991–1013. doi: 10.1108/14637151011093035 .
Bendavid, Y., Boeck, H., & Philippe, R. (2012). RFID-enabled traceability system for consignment and high value products: A case study in the healthcare sector. Journal of Medical Systems, 36 (6), 3473–3489. doi: 10.1007/s10916-011-9804-0 .
Bendavid, Y., & Cassivi, L. (2010). Bridging the gap between RFID/EPC concepts, technological requirements and supply chain e-business processes. Journal of Theoretical and Applied Electronic Commerce Research, 5 (3), 1–16. doi: 10.4067/S0718-18762010000300002 .
Bendavid, Y., Lefebvre, É., Lefebvre, L. A., & Wamba, S. (2009). Key performance indicators for the evaluation of RFID-enabled B-to-B e-commerce applications: The case of a five-layer supply chain. Information Systems and e-Business Management, 7 (1), 1–20. doi: 10.1007/s10257-008-0092-2 .
Benssalah, M., Djeddou, M., & Drouiche, K. (2014). Security enhancement of the authenticated RFID security mechanism based on chaotic maps. Security and Communication Networks, 7 (12), 2356–2372.
Bertolini, M., Botanni, E., Rizzi, A., Volpi, A., & Renzi, P. (2013). Shrinkage reduction in perishable food supply chain by means of an RFID-based FIFO management policy. International Journal of RF Technologies: Research and Applications, 5 (3–4), 123–136. doi: 10.3233/RFT-130052 .
Bertolini, M., Bottani, E., Ferretti, G., Rizzi, A., & Volpi, A. (2012). Experimental evaluation of business impacts of RFID in apparel and retail supply chain. International Journal of RF Technologies: Research and Applications, 3 (4), 257–282. doi: 10.3233/RFT-2012-028 .
Bhakoo, V., & Chan, C. (2011). Collaborative implementation of e-business processes within the health-care supply chain: The Monash Pharmacy Project. Supply Chain Management: An International Journal, 16 (3), 184–193. doi: 10.1108/13598541111127173 .
Bhattacharya, M. (2012). Impact of RFID on the retail value chain: An exploratory study using a mixed method approach. Journal of Technology Management and Innovation, 7 (4), 36–49. doi: 10.4067/S0718-27242012000400003 .
Bhattacharya, M. (2015). A conceptual framework of RFID adoption in retail using Rogers stage model. Business Process Management Journal, 21 (3), 517–540.
Bhattacharyya, R., Floerkemeier, C., Sarma, S., & Deavours, D. (2011). RFID tag antenna based temperature sensing in the frequency domain. Paper presented at the IEEE international conference on RFID (pp 70–77), 12–14 April 2011, Orlando, FL.
Biji, K., Mohan, C., Srinivasa Gopal, T., & Ravishankar, C. (2015). Smart packaging systems for food applications: A review. Journal of Food Science and Technology, 11 (2), 11. doi: 10.1007/s13197-015-1766-7 .
Björk, A., Erlandsson, M., Häkli, J., Jaakkola, K., Nilsson, Å., Nummila, K., & Puntanen, V. (2011). Monitoring environmental performance of the forestry supply chain using RFID. Computers in Industry, 62 (8–9), 830–841. doi: 10.1016/j.compind.2011.08.001 .
Bose, I., Ngai, E. T., Teo, T. H., & Spiekermann, S. (2009). Managing RFID projects in organizations. European Journal of Information Systems, 18 (6), 534–540. doi: 10.1057/ejis.2009.43 .
Bosona, T., & Gebresenbet, G. (2013). Food traceability as an integral part of logistics management in food and agricultural supply chain. Food Control, 33 , 32–48. doi: 10.1016/j.foodcont.2013.02.004 .
Bottani, E., Ferretti, G., Montanari, R., & Rizzi, A. (2009a). The impact of RFID technology on logistics processes of the fashion industry supply chain. International Journal of RF Technologies: Research and Applications, 1 (4), 225–252. doi: 10.1080/17545730903321675 .
Bottani, E., Hardgrave, B., & Volpi, A. (2009b). A methodological approach to the development of RFID supply chain projects. International Journal of RF Technologies: Research and Applications, 1 (2), 131–150. doi: 10.1080/17545730802065043 .
Bottani, E., Manfredi, M., Vignali, G., & Volpi, A. (2014). Lifecycle assessment of RFID implementation in the fresh food supply chain. International Journal of RF Technologies: Research and Applications, 6 (1), 51–71. doi: 10.3233/RFT-140060 .
Bottani, E., Montanari, R., & Volpi, A. (2010). The impact of RFID and EPC network on the bullwhip effect in the Italian FMCG supply chain. International Journal of Production Economics, 124 (2), 426–432. doi: 10.1016/j.ijpe.2009.12.005 .
Bottani, E., & Rizzi, A. (2008). Economical assessment of the impact of RFID technology and EPC system on the fast-moving consumer goods supply chain. International Journal of Production Economics, 112 (2), 548–569. doi: 10.1016/j.ijpe.2007.05.007 .
Brintrup, A., Ranasinghe, D., & McFarlane, D. (2010). RFID opportunity analysis for leaner manufacturing. International Journal of Production Research, 48 (9), 2745–2764. doi: 10.1080/00207540903156517 .
Brusey, J., & McFarlane, D. C. (2009). Effective RFID-based object tracking for manufacturing. International Journal of Computer Integrated Manufacturing, 22 (7), 638–647. doi: 10.1080/09511920701805519 .
Bureau, S., Meiller, Y., Zhou, W., & Piramuthu, S. (2011). Performance drivers for RFID-generated item-level information in the oil industry. Journal of Organizational Computing and Electronic Commerce, 21 (4), 295–314. doi: 10.1080/10919392.2011.614191 .
Çakıcı, Ö. E., Groenevelt, H., & Seidmann, A. (2011). Using RFID for the management of pharmaceutical inventory—System optimization and shrinkage control. Decision Support Systems, 51 (4), 842–852. doi: 10.1016/j.dss.2011.02.003 .
Camdereli, A. Z., & Swaminathan, J. M. (2010). Misplaced inventory and radio-frequency identification (RFID) technology: Information and coordination. Production and Operations Management, 19 (1), 1–18. doi: 10.1111/j.1937-5956.2009.01057.x .
Cannon, A. R., Reyes, P. M., Frazier, G. V., & Prater, E. L. (2008). RFID in the contemporary supply chain: Multiple perspectives on its benefits and risks. International Journal of Operations and Production Management, 28 (5), 433–454. doi: 10.1108/01443570810867196 .
Cao, H., Folan, P., Mascolo, J., & Browne, J. (2009). RFID in product lifecycle management: A case in the automotive industry. International Journal of Computer Integrated Manufacturing, 22 (7), 616–637. doi: 10.1080/09511920701522981 .
Caridi, M., Perego, A., & Tumino, A. (2013). Measuring supply chain visibility in the apparel industry. Benchmarking: An International Journal, 20 (1), 25–44. doi: 10.1108/14635771311299470 .
Castro, L., Lefebvre, E., & Lefebvre, L. A. (2013). Adding Intelligence to mobile asset management in hospitals: The true value of RFID. Journal of Medical Systems, 37 (5), 1–17. doi: 10.1007/s10916-013-9963-2 .
Catarinucci, L., Colella, R., De Blasi, M., Patrono, L., & Tarricone, L. (2012). Enhanced UHF RFID tags for drug tracing. Journal of Medical Systems, 36 (6), 3451–3462. doi: 10.1007/s10916-011-9790-2 .
Chan, H., Choi, T., & Hui, C. (2012). RFID versus bar-coding systems: Transactions errors in health care apparel inventory control. Decision Support Systems, 54 (1), 803–811. doi: 10.1016/j.dss.2012.08.004 .
Chan, H.-L., Choi, T.-M., Hui, C.-L., & Ng, S.-F. (2015). Quick response healthcare apparel supply chains: Value of RFID and coordination. IEEE Transactions on Systems, Man, and Cybernetics (Systems), 45 (6), 887–900.
Chao, C.-C., Yang, J.-M., & Jen, W.-Y. (2007). Determining technology trends and forecasts of RFID by a historical review and bibliometric analysis from 1991 to 2005. Technovation, 27 (5), 268–279. doi: 10.1016/j.technovation.2006.09.003 .
Chatziantoniou, D., Pramatari, K., & Sotiropoulos, Y. (2011). Supporting real-time supply chain decisions based on RFID data streams. Journal of Systems and Software, 84 (4), 700–710. doi: 10.1016/j.jss.2010.12.011 .
Chen, S., Chang, C., Liu, K., & Kao, C. (2014). The prototype and application of RFID implementation: A case study of automobiles assembly industries. International Journal of Electronic Business Management, 12 (2), 145–156.
Chen, C.-L., Chen, Y.-Y., Kuo, T.-M., Chiou, K.-C., & Deng, Y.-Y. (2012a). Design of an RFID on-line authentication and anti-counterfeit transaction protocol. International Journal of RF Technologies: Research and Applications, 4 (1), 37–53. doi: 10.3233/RFT-2012-0034 .
Chen, J. C., Cheng, C. H., & Huang, P. B. (2012b). Supply chain management with lean production and RFID application: A case study. Expert Systems and Applications, 40 (9), 3389–3397. doi: 10.1016/j.eswa.2012.12.047 .
Chen, J. C., Cheng, C.-H., Huang, P. B., Wang, K.-J., Huang, C.-J., & Ting, T.-C. (2013a). Warehouse management with lean and RFID application: A case study. The International Journal of Advanced Manufacturing Technology, 69 (1–4), 531–542. doi: 10.1007/s00170-013-5016-8 .
Chen, F., Drezner, Z., Ryan, J. K., & Simchi-Levi, D. (2000). Quantifying the bullwhip effect in a simple supply chain: The impact of forecasting, lead time, and information. Management Science, 46 (3), 436–443. doi: 10.1287/mnsc.46.3.436.12069 .
Chen, C.-L., Huang, Y.-C., & Jiang, J.-R. (2013b). A secure ownership transfer protocol using EPCglobal Gen-2 RFID. Telecommunication Systems, 53 (4), 387–399.
Chen, X., Zhu, Y., Li, J., Wen, Y., & Gong, Z. (2015). Efficiency and privacy enhancement for a track and trace system of RFID-based supply chains. Information, 6 (2), 258–274.
Cheon-pyo, L., & Shim, J. P. (2007). An exploratory study of radio frequency identification (RFID) adoption in the healthcare industry. European Journal of Information Systems, 16 (6), 712–724. doi: 10.1057/palgrave.ejis.3000716 .
Chew, E. P., Lee, L. H., & Sim, C.-K. (2013). The impact of supply chain visibility when lead time is random. OR Spectrum, 35 (1), 163–190. doi: 10.1007/s00291-011-0254-3 .
Choi, T.-M. (2011). Coordination and risk analysis of VMI supply chains with RFID technology. IEEE Transactions on Industrial Informatics, 7 (3), 497–504. doi: 10.1109/TII.2011.2158830 .
Choi, S. H., Yang, Y. X., Yang, B., & Cheung, H. H. (2015). Item-level RFID for enhancement of customer shopping experience in apparel retail. Computers in Industry, 71 , 10–23. doi: 10.1016/j.compind.2015.03.003 .
Chong, A. Y.-L., & Chan, F. T. S. (2012). Structural equation modeling for multi-stage analysis on Radio Frequency Identification (RFID) diffusion in the health care industry. Expert Systems with Applications, 39 (10), 8645–8654. doi: 10.1016/j.eswa.2012.01.201 .
Chong, A. Y.-L., Liu, M. J., Jun Luo, J., & Keng-Boon, O. (2015). Predicting RFID adoption in healthcare supply chain from the perspectives of users. International Journal of Production Economics, 159 , 66–75.
Chongwatpol, J., & Sharda, R. (2013). RFID-enabled track and traceability in job-shop scheduling environment. European Journal of Operational Research, 227 (3), 453–463. doi: 10.1016/j.ejor.2013.01.009 .
Chow, H. K. H., Choy, K. L., Lee, W. B., & Chan, F. T. S. (2007). Integration of web-based and RFID technology in visualizing logistics operations—A case study. Supply Chain Management: An International Journal, 12 (3), 221–234. doi: 10.1108/13598540710742536 .
Cinicioglu, E., & Shenoy, P. (2012). A new heuristic for learning Bayesian networks from limited datasets: A real-time recommendation system application with RFID systems in grocery stores. Annals of Operations Research, . doi: 10.1007/s10479-012-1171-9 .
Condea, C., Thiesse, F., & Fleisch, E. (2012). RFID-enabled shelf replenishment with backroom monitoring in retail stores. Decision Support Systems, 52 (4), 839–849. doi: 10.1016/j.dss.2011.11.018 .
Costa, C., Antonucci, F., Pallottino, F., Aguzzi, J., Sarriá, D., & Menesatti, P. (2013). A review on agri-food supply chain traceability by means of RFID technology. Food and Bioprocess Technology, 6 (2), 353–366. doi: 10.1007/s11947-012-0958-7 .
Coustasse, A., Arvidson, C., & Rutsohn, P. (2010). Pharmaceutical counterfeiting and the RFID technology intervention. Journal of Hospital Marketing and Public Relations, 20 (2), 100–115. doi: 10.1080/15390942.2010.493369 .
Coustasse, A., Tomblin, S., & Slack, C. (2013). Impact of radio-frequency identification (RFID) technologies on the hospital supply chain: A literature review. Perspectives in Health Information Management, 10 , 1–17.
Cui, L., Wang, L., & Deng, J. (2014). RFID technology investment evaluation model for the stochastic joint replenishment and delivery problem. Expert Systems with Applications, 41 (4), 1792–1805. doi: 10.1016/j.eswa.2013.08.078 .
Curran, K., & Porter, M. (2007). A primer on radio frequency identification for libraries. Library Hi Tech, 25 (4), 595–611. doi: 10.1108/07378830710840536 .
Dai, H., & Tseng, M. M. (2012). The impacts of RFID implementation on reducing inventory inaccuracy in a multi-stage supply chain. International Journal of Production Economics, 139 (2), 634–641. doi: 10.2139/ssrn.1387024 .
Dash, D. P. (2011). Supply chain management: The RFID advantage. IUP Journal of Supply Chain Management, 8 (4), 42–57.
de Donno, D., Catarinucci, L., Di Serio, A., & Tarricone, L. (2013). A long-range computational RFID tag for temperature and acceleration sensing applications. Progress in Electromagnetics Research, Part C, 45 (4), 223–235. doi: 10.2528/PIERC13101904 .
DeHoratius, N., & Raman, A. (2008). Inventory record inaccuracy: An empirical analysis. Management Science, 54 (4), 627–641. doi: 10.1287/mnsc.1070.0789 .
del Castillo, E. (2007). Process optimization: A statistical approach . New York: Springer.
Book Google Scholar
Delen, D., Hardgrave, B. C., & Sharda, R. (2007). RFID for better supply-chain management through enhanced information visibility. Production and Operations Management, 16 (5), 613–624. doi: 10.1111/j.1937-5956.2007.tb00284.x .
Dimakopoulou, A. G., Pramatari, K. C., & Tsekrekos, A. E. (2014). Applying real options to IT investment evaluation: The case of radio frequency identification (RFID) technology in the supply chain. International Journal of Production Economics, 156 , 191–207. doi: 10.1016/j.ijpe.2014.06.005 .
Dimitropoulos, P., & Soldatos, J. (2010). RFID enabled fully automated warehouse management: Adding the business context. International Journal of Manufacturing Technology and Management, 21 (3–4), 269–288. doi: 10.1504/IJMTM.2010.035436 .
Dong, Q., Ding, W., & Wei, L. (2014). Improvement and optimized implementation of cryptoGPS protocol for low-cost radio frequency identification authentication. Security and Communication Networks, 8 , 1474–1484. doi: 10.1002/sec.1096 .
Duan, Q., & Liao, T. W. (2013). A new age-based replenishment policy for supply chain inventory optimization of highly perishable products. International Journal of Production Economics, 145 (2), 658–671. doi: 10.1016/j.ijpe.2013.05.020 .
Erguler, I. (2015). A potential weakness in RFID-based Internet-of-things systems. Pervasive and Mobile Computing, 20 , 115–126.
Fan, T. J., Chang, X. Y., Gu, C. H., Yi, J. J., & Deng, S. (2014). Benefits of RFID technology for reducing inventory shrinkage. International Journal of Production Economics, 147 (PART C), 659–665. doi: 10.1016/j.ijpe.2013.05.007 .
Fan, T., Tao, F., Deng, S., & Li, S. (2015). Impact of RFID technology on supply chain decisions with inventory inaccuracies. International Journal of Production Economics, 159 , 117–125. doi: 10.1016/j.ijpe.2014.10.004 .
Fan, H., Wu, Q., Lin, Y., & Zhang, J. (2013a). A split-path schema-based RFID data storage model in supply chain management. Sensors, 13 (5), 5757–5776. doi: 10.3390/s130505757 .
Fan, H., Wu, Q., & Zhang, J. (2013). Efficient RFID data cleaning in supply chain management. IEICE Transactions on Information and Systems, E96-D (7), 1557–1560.
Fangtsou, C.-T. (2014). Optimizing recommendations with an RFID-based approach for the Taiwan Trainquali Document Management System. International Journal of Electronic Commerce Studies, 5 (1), 1–26. doi: 10.7903/ijecs.1148 .
Farris, I., Iera, A., & Spinella, S. C. (2013). Introducing a novel ‘virtual communication channel’ into RFID ecosystems for IoT. IEEE Communications Letters, 17 (8), 1532–1535. doi: 10.1109/LCOMM.2013.070913.130392 .
Fauska, P., Kryvinska, N., & Strauss, C. (2014). Agile management of complex goods & services bundles for B2B E-commerce by global narrow-specialized companies. Global Journal of Flexible Systems Management, 15 (1), 5–23. doi: 10.1007/s40171-013-0054-5 .
Ferrer, G., Heath, S. K., & Dew, N. (2011). An RFID application in large job shop remanufacturing operations. International Journal of Production Economics, 133 (2), 612–621. doi: 10.1016/j.ijpe.2011.05.006 .
Fleisch, E., & Tellkamp, C. (2005). Inventory inaccuracy and supply chain performance: A simulation study of a retail supply chain. International Journal of Production Economics, 95 (3), 373–385. doi: 10.1016/j.ijpe.2004.02.003 .
Fu, L., Shen, X., Zhu, L., & Wang, J. (2014). A low-cost UHF RFID tag chip with AES cryptography engine. Security and Communication Networks, 7 (2), 365–375.
Gangwar, H., Hema Date, H., & Ramaswamy, R. (2015). Understanding determinants of cloud computing adoption using an integrated TAM-TOE model. Journal of Enterprise Information Management, 28 (1), 107–130.
Gao, H. D., Guo, Y. J., Cui, J. Q., Hao, H. G., & Shi, H. (2012). A communication protocol of RFID systems in Internet of Things. International Journal of Security and Its Applications, 6 (2), 91–101.
Garcia, A., Chang, Y., Abarca, A., & Oh, C. (2007). RFID enhanced MAS for warehouse management. International Journal of Logistics: Research and Applications, 10 (2), 97–107. doi: 10.1080/13675560701427379 .
Gastaldi, L., Mangiaracina, R., Miragliotta, G., Perego, A., & Tumino, A. (2015). Measuring the benefits of tracking medical treatment through RFID. International Journal of Productivity and Performance Management, 64 (2), 175–193. doi: 10.1108/IJPPM-10-2013-0171 .
Gaukler, G. M. (2010). Preventing avoidable stock-outs: The impact of item-level RFID in retail. Journal of Business and Industrial Marketing, 25 (8), 572–581. doi: 10.1108/08858621011088301 .
Gaukler, G. M. (2011). Item-level RFID in a retail supply chain with stock-out-based substitution. IEEE Transactions on Industrial Informatics, 7 (2), 362–370. doi: 10.1109/TII.2010.2068305 .
Gaukler, G. M., & Hausman, W. H. (2008). RFID in mixed-model automotive assembly operations: Process and quality cost savings. IIE Transactions, 40 (11), 1083–1096. doi: 10.1080/07408170802167654 .
Gaukler, G. M., Seifert, R. W., & Hausman, W. H. (2007). Item-level RFID in the retail supply chain. Production and Operations Management, 16 (1), 65–76. doi: 10.1111/j.1937-5956.2007.tb00166.x .
Geary, S., Disney, S. M., & Towill, D. R. (2006). On bullwhip in supply chains—Historical review, present practice and expected future impact. International Journal of Production Economics, 101 (1), 2–18. doi: 10.1016/j.ijpe.2005.05.009 .
Geerts, G. L., & O’Leary, D. E. (2014). A supply chain of things: The EAGLET ontology for highly visible supply chains. Decision Support Systems, 63 (1), 3–22. doi: 10.1016/j.dss.2013.09.007 .
Goel, R. (2007). Managing RFID consumer privacy and implementation barriers. Information Systems Security, 16 , 217–223. doi: 10.1080/10658980701576396 .
Grunow, M., & Piramuthu, S. (2013). RFID in highly perishable food supply chains: Remaining shelf life to supplant expiry date? International Journal of Production Economics, 146 (2), 717–727. doi: 10.1016/j.ijpe.2013.08.028 .
Gulcharan, N. I., Daud, H., Nor, N. M., Ibrahim, T., & Nyamasvisva, E. T. (2013). Limitation and solution for healthcare network using RFID technology: A review. Procedia Technology, 11 , 565–571. doi: 10.1016/j.protcy.2013.12.229 .
Gunasekaran, A., & Ngai, E. W. T. (2004). Information systems in supply chain integration and management. European Journal of Operational Research, 159 (2), 269–295. doi: 10.1016/j.ejor.2003.08.016 .
Gunasekaran, A., Ngai, E. W. T., & McGaughey, R. E. (2006). Information technology and systems justification: A review for research and applications. European Journal of Operational Research, 173 (3), 957–983. doi: 10.1016/j.ejor.2005.06.002 .
Hammer, M., & Champy, J. A. (1993). Reengineering the corporation: A manifesto for business revolution . Harper Business Books, New York. doi: 10.1002/qre.4680100613 .
Hardgrave, B. C., Aloysius, J., & Goyal, S. (2009). Does RFID improve inventory accuracy? A preliminary analysis. International Journal of RF Technologies: Research and Applications, 1 (1), 44–56. doi: 10.1080/17545730802338333 .
Hardgrave, B. C., Aloysius, J. A., & Goyal, S. (2013). RFID-enabled visibility and retail inventory record inaccuracy: Experiments in the field. Production and Operations Management, 22 (4), 843–856. doi: 10.1111/poms.12010 .
He, C., Zheng, Y., Wang, L., & Ma, D. (2014). RFID application research for discrete manufacturing. Computer Integrated Manufacturing Systems, 20 (5), 1160–1170. doi: 10.13196/j.cims.2014.05.hechangpeng.1160.11.20140519 .
Heese, H. S. (2007). Inventory record inaccuracy, double marginalization, and RFID adoption. Production and Operations Management, 16 (5), 542–553. doi: 10.1111/j.1937-5956.2007.tb00279.x .
Hellström, D., & Wiberg, M. (2010). Improving inventory accuracy using RFID technology: A case study. Assembly Automation, 30 (4), 345–351. doi: 10.1108/01445151011075807 .
Herrmann, S., Rogers, H., Gebhard, M., & Hartmann, E. (2015). Co-creating value in the automotive supply chain: An RFID application for processing finished vehicles. Production Planning and Control, 26 (12), 981–993. doi: 10.1080/09537287.2014.1002023 .
Higgins, L. N., & Cairney, T. (2006). RFID opportunities and risks. Journal of Corporate Accounting and Finance, 17 (5), 51–57. doi: 10.1002/jcaf.20231 .
Hinkka, V. (2012). Challenges for building RFID tracking systems across the whole supply chain. International Journal of RF Technologies: Research and Applications, 3 (3), 201–218. doi: 10.3233/RFT-2012-025 .
Hinkka, V., Främling, K., & Häkkinen, M. (2015). Typology of configurable RFID tracking in fashion logistics. International Journal of RF Technologies: Research and Applications, 6 (2–3), 77–97. doi: 10.3233/RFT-130061 .
Holweg, M., Disney, S., Holmstrom, J., & Smaros, J. (2005). Supply chain collaboration: Making sense of the strategy continuum. European Management Journal, 23 (2), 170–181. doi: 10.1016/j.emj.2005.02.008 .
Hong, I.-H., Dang, J.-F., Tsai, Y.-H., Liu, C.-S., Lee, W.-T., Wang, M.-L., & Chen, P.-C. (2011). An RFID application in the food supply chain: A case study of convenience stores in Taiwan. Journal of Food Engineering, 106 (2), 119–126. doi: 10.1016/j.jfoodeng.2011.04.014 .
Hong, S. R., Kim, S. T., & Kim, C. O. (2010). Neural network controller with on-line inventory feedback data in RFID-enabled supply chain. International Journal of Production Research, 48 (9), 2613–2632. doi: 10.1080/00207540903564967 .
Hou, J.-L., & Huang, C.-H. (2006). Quantitative performance evaluation of RFID applications in the supply chain of the printing industry. Industrial Management and Data Systems, 106 (1), 96–120. doi: 10.1108/02635570610641013 .
Hozak, K., & Collier, D. A. (2008). RFID as an enabler of improved manufacturing performance. Decision Sciences, 39 (4), 859–881. doi: 10.1111/j.1540-5915.2008.00214.x .
Hribernik, K. A., Rabe, L., Thoben, K.-D., & Schumacher, J. (2006). The product avatar as a product-instance-centric information management concept. International Journal of Product Lifecycle Management, 1 (4), 367–379. doi: 10.1504/IJPLM.2006.011055 .
Hsiaoping, Y. (2013). Effects of RFID in retailing on customer trust. Journal of Service Science and Management, 6 (2), 143–150.
Hu, J., Lewis, F. L., Gan, O. P., Phua, G. H., & Aw, L. L. (2014). Discrete-event shop-floor monitoring system in RFID-enabled manufacturing. IEEE Transactions on Industrial Electronics, 61 (12), 7083–7091.
Huang, G., Jin, H. L., Yuan, X. D., Goa, L., & Rao, Y. (2012). RFID-enabled real-time PBS monitoring for automobile assembly factory. International Journal of Computer Integrated Manufacturing, 25 (1), 66–85. doi: 10.1080/0951192X.2010.528034 .
Huang, G. Q., Wright, P. K., & Newman, S. T. (2008). Wireless manufacturing: A literature review, recent developments, and case studies. International Journal of Computer Integrated Manufacturing, 22 (7), 1–16.
Irani, Z., Gunasekaran, A., & Dwivedi, Y. K. (2010). Radio frequency identification (RFID): Research trends and framework. International Journal of Production Research, 48 (9), 2485–2511. doi: 10.1080/00207540903564900 .
Jaggi, A. S., Sawhney, R. S., Balestrassi, P. P., Simonton, J., & Upreti, G. (2014). An experimental approach for developing radio frequency identification (RFID) ready packaging. Journal of Cleaner Production, 85 , 371–381. doi: 10.1016/j.jclepro.2014.08.105 .
Jain, V., & Raj, T. (2013). Ranking of flexibility in flexible manufacturing system by using a combined multiple attribute decision making method. Global Journal of Flexible Systems Management, 14 (3), 125–141. doi: 10.1007/s40171-013-0038-5 .
Jakhar, S. (2014). Designing the green supply chain performance optimisation model. Global Journal of Flexible Systems Management, 15 (3), 235. doi: 10.1007/s40171-014-0069-6 .
Jaselskis, E. J., Asce, A. M., & El-Misalami, T. (2003). Implementing radio frequency identification in the construction process. Journal of Construction Engineering and Management, 129 (6), 680–689. doi: 10.1061/(ASCE)0733-9364(2003)129:6(680) .
Jedermanna, R., Ruiz-Garciab, L., & Langa, W. (2009). Spatial temperature profiling by semi-passive RFID loggers for perishable food transportation. Computers and Electronics in Agriculture, 65 (2), 145–154. doi: 10.1016/j.compag.2008.08.006 .
Jeong, B.-K., & Lu, Y. (2008). The impact of radio frequency identification (RFID) investment announcements on the market value of the firm. Journal of Theoretical and Applied Electronic Commerce Research, 3 (1), 41–54.
Jimenez, C., Dauzère-Pérès, S., Feuillebois, C., & Pauly, E. (2013). Optimizing the positioning and technological choices of RFID elements for aircraft part identification. European Journal of Operational Research, 227 (2), 350–357. doi: 10.1016/j.ejor.2012.10.034 .
Jones, P., Clarke-Hill, C., Comfort, D., Hillier, D., & Shears, P. (2005). Radio frequency identification and food retailing in the UK. British Food Journal, 107 (6), 356–360. doi: 10.1108/00070700510602156 .
Jones, E. C., Riley, M. W., Franca, R., & Reigle, S. (2007). Case study: The engineering economics of RFID in specialized manufacturing. The Engineering Economist, 52 (3), 285–303. doi: 10.1080/00137910701503951 .
Juels, A. (2006). RFID security and privacy: A research survey. IEEE Journal on Selected Areas in Communications, 24 (2), 381–394. doi: 10.1109/JSAC.2005.861395 .
Jun, H.-B., Shin, J.-H., Kim, Y.-S., Kiritsis, D., & Xirouchakis, P. (2009). A framework for RFID applications in product lifecycle management. International Journal of Computer Integrated Manufacturing, 22 (7), 595–615. doi: 10.1080/09511920701501753 .
Kang, Y., & Gershwin, S. B. (2004). Information inaccuracy in inventory systems—Stock loss and stockout. IEEE Transactions, 37 (9), 1–29. doi: 10.1080/07408170590969861 .
Kapoor, K., Dwivedi, Y., Piercy, N. C., Lal, B., & Weerakkody, V. (2014). RFID integrated systems in libraries: Extending TAM model for empirically examining the use. Journal of Enterprise Information Management, 27 (6), 731–758. doi: 10.1108/JEIM-10-2013-0079 .
Kapoor, G., Wei, Z., & Piramuthu, S. (2009). Challenges associated with RFID tag implementations in supply chains. European Journal of Information Systems, 18 (6), 526–533. doi: 10.1057/ejis.2009.41 .
Kapoor, G., Zhou, W., & Piramuthu, S. (2011). Multi-tag and multi-owner RFID ownership transfer in supply chains. Decision Support Systems, 52 (1), 258–270. doi: 10.1016/j.dss.2011.08.002 .
Karaer, Ö., & Lee, H. L. (2007). Managing the reverse channel with RFID-enabled negative demand information. Production and Operations Management, 16 (5), 625–645. doi: 10.1111/j.1937-5956.2007.tb00285.x .
Kärkkäinen, M. (2003). Increasing efficiency in the supply chain for short shelf-life goods using RFID tagging. International Journal of Retail and Distribution Management, 31 (10), 529–536. doi: 10.1108/09590550310497058 .
Kasiri, N., Sharda, R., & Hardgrave, B. (2012). A balanced scorecard for item-level RFID in the retail sector: A Delphi study. European Journal of Information Systems, 21 (3), 255–267. doi: 10.1057/ejis.2011.33 .
Keller, T., Fleisch, E., & Thiesse, F. (2014). Classification models for RFID-based real-time detection of process events in the supply chain: An empirical study. ACM Transactions on Management Information Systems, 5 (4), 1–30. doi: 10.1145/2629449 .
Kim, I., Back, M.-K., Yim, H.-J., & Lee, K.-C. (2015). RFID adaptor for detecting and handling data/events in Internet of things. Indian Journal of Science and Technology, 8 , 140–148.
Kim, T., & Glock, C. H. (2014). On the use of RFID in the management of reusable containers in closed-loop supply chains under stochastic container return quantities. Transportation Research Part E: Logistics and Transportation Review, 64 (4), 12–27. doi: 10.1016/j.tre.2014.01.011 .
Kim, H., & Sohn, S. (2009). Cost of ownership model for the RFID logistics system applicable to u-city. European Journal of Operational Research, 194 (2), 406–417. doi: 10.1016/j.ejor.2007.12.015 .
Kiritsis, D. (2011). Closed-loop PLM for intelligent products in the era of the Internet of things. Computer-Aided Design, 43 (5), 479–501.
Klundert, J., Muls, P., & Schadd, M. (2008). Optimizing sterilization logistics in hospitals. Health Care Management Science, 11 (1), 23–33. doi: 10.1007/s10729-007-9037-4 .
Ko, J. M., Kwak, C., Cho, Y., & Kim, C. O. (2011). Adaptive product tracking in RFID-enabled large-scale supply chain. Expert Systems with Applications, 38 (3), 1583–1590. doi: 10.1016/j.eswa.2010.07.077 .
Kochar, B., & Chhillar, R. S. (2011). A novel RFID data mining system: Integration of effective sequential pattern mining and fuzzy rules generation techniques. International Journal of Wireless Information Networks, 18 , 309–318. doi: 10.1007/s10776-011-0151-3 .
Kok, A. G. D., Donselaar, K. H. V., & Woensel, T. V. (2008). A break-even analysis of RFID technology for inventory sensitive to shrinkage. International Journal of Production Economics, 112 (2), 521–531. doi: 10.1016/j.ijpe.2007.05.005 .
Kök, A., & Shang, K. (2014). Evaluation of cycle-count policies for supply chains with inventory inaccuracy and implications on RFID investments. European Journal of Operational Research, 237 (1), 91–105. doi: 10.1016/j.ejor.2014.01.052 .
Kolokathi, A., & Rallis, P. (2013). Radio frequency identification (RFID) in healthcare: A literature review. Studies in Health Technology and Informatics, 190 , 157–159.
Kumar, S., Anselmo, M., & Berndt, K. (2009). Transforming the retail industry: Potential and challenges with RFID technology. Transportation Journal, 48 (4), 61–71.
Kumar, P., & Deshmukh, S. G. (2006). A model for flexible supply chain through flexible manufacturing. Global Journal of Flexible Systems Management, 7 (3/4), 17–24.
Kumar, A., & Rahman, S. (2014). RFID-enabled process reengineering of closed-loop supply chains in the healthcare industry of Singapore. Journal of Cleaner Production, 85 , 382–394. doi: 10.1016/j.jclepro.2014.04.037 .
Kumar, R., Singh, R. K., & Shankar, R. (2013). Study on coordination issues for flexibility in supply chain of SMEs: A case study. Global Journal of Flexible Systems Management, 14 (2), 81–92.
Kvarnstrom, B., Bergquist, B., & Vannman, K. (2011). RFID to improve traceability in continuous granular flows—An experimental case study. Quality Engineering, 23 (4), 343–357. doi: 10.1080/08982112.2011.602278 .
Kvarnström, B., & Vanhatalo, E. (2010). Using RFID to improve traceability in process industry: Experiments in a distribution chain for iron ore pellets. Journal of Manufacturing Technology Management, 21 (1), 139–154. doi: 10.1108/17410381011011524 .
Kwok, S. K., Ting, S. L., Tsang, A. H. C., & Cheung, C. F. (2010a). A counterfeit network analyzer based on RFID and EPC. Industrial Management and Data Systems, 110 (7), 1018–1037. doi: 10.1108/02635571011069086 .
Kwok, S. K., Ting, J. S. L., Tsang, A. H. C., Lee, W. B., & Cheung, B. C. F. (2010b). Design and development of a mobile EPC-RFID-based self-validation system (MESS) for product authentication. Computers in Industry, 61 (7), 624–635. doi: 10.1016/j.compind.2010.02.001 .
Kwon, K., Kang, D., Yoon, Y., Sohn, J.-S., & Chung, I.-J. (2014). A real time process management system using RFID data mining. Computers in Industry, 65 (4), 721–732. doi: 10.1016/j.compind.2014.02.007 .
Lai, F., Hutchinson, J., & Zhang, G. (2005). Radio frequency identification (RFID) in China: Opportunities and challenges. International Journal of Retail and Distribution Management, 33 (12), 905–916. doi: 10.1108/09590550510634639 .
Langer, N., Forman, C., Kekre, S., & Scheller-Wolf, A. (2007). Assessing the impact of RFID on return center logistics. Interfaces, 37 (6), 501–514. doi: 10.1287/inte.1070.0308 .
Lao, S. I., Choy, K. L., Ho, G. T. S., Tsim, Y. C., & Lee, C. K. H. (2011). Real-time inbound decision support system for enhancing the performance of a food warehouse. Journal of Manufacturing Technology Management, 22 (8), 1014–1031. doi: 10.1108/17410381111177467 .
Lee, C.-F., Chien, H.-Y., & Laih, C.-S. (2012). Server-less RFID authentication and searching protocol with enhanced security. International Journal of Communication Systems, 25 (3), 376–385. doi: 10.1002/dac.1246 .
Lee, C. K. H., Ho, G. T. S., Choy, K. L., & Pang, G. K. H. (2014). A RFID-based recursive process mining system for quality assurance in the garment industry. International Journal of Production Research, 52 (14), 4216–4238.
Lee, C. K. M., Ho, W., Ho, G. T. S., & Lau, H. C. W. (2011). Design and development of logistics workflow systems for demand management with RFID. Expert Systems with Applications, 38 (5), 5428–5437. doi: 10.1016/j.eswa.2010.10.012 .
Lee, I., & Lee, B.-C. (2012). Measuring the value of RFID investment: Focusing on RFID budget allocation. IEEE Transactions on Engineering Management, 59 (4), 551–559. doi: 10.1109/TEM.2011.2163072 .
Lee, H., & Özer, Ö. (2007). Unlocking the value of RFID. Production and Operations Management, 16 (1), 40–64. doi: 10.1111/j.1937-5956.2007.tb00165.x .
Lee, D., & Park, J. (2008). RFID-based traceability in the supply chain. Industrial Management and Data Systems, 108 (6), 713–725. doi: 10.1108/02635570810883978 .
Leung, J., Cheung, W., & Chu, S. C. (2014). Aligning RFID applications with supply chain strategies. Information and Management, 51 (2), 260–269. doi: 10.1016/j.im.2013.11.010 .
Li, L. (2013). Technology designed to combat fakes in the global supply chain. Business Horizons, 56 (2), 167–177. doi: 10.1016/j.bushor.2012.11.010 .
Li, S., Visich, J. K., Khumawala, B. M., & Zhang, C. (2006). Radio frequency identification technology: Applications, technical challenges and strategies. Sensor Review, 26 (3), 193–202. doi: 10.1108/02602280610675474 .
Liao, W.-P., Lin, T. M. Y., & Liao, S.-H. (2011). Contributions to radio frequency identification (RFID) research: An assessment of SCI-, SSCI-indexed papers from 2004 to 2008. Decision Support, 50 (2), 548–556. doi: 10.1016/j.dss.2010.11.013 .
Lim, M. K., Bahr, W., & Leung, S. C. H. (2013). RFID in the warehouse: A literature analysis (1995–2010) of its applications, benefits, challenges and future trends. International Journal of Production Economics, 145 (1), 409–430. doi: 10.1016/j.ijpe.2013.05.006 .
Lin, C. (2009). An empirical study on organizational determinants of RFID adoption in the logistics industry. Journal of Technology Management and Innovation, 4 (1), 1–8. doi: 10.4067/S0718-27242009000100001 .
Liu, C. M., & Chen, L. S. (2009). Applications of RFID technology for improving production efficiency in an integrated-circuit packaging house. International Journal of Production Research, 47 (8), 2203–2216. doi: 10.1080/00207540802380556 .
Liu, X., Tang, O., & Huang, P. (2008). Dynamic pricing and ordering decision for the perishable food of the supermarket using RFID technology. Asia Pacific Journal of Marketing and Logistics, 20 (1), 7–22. doi: 10.1080/12297119.2006.9707377 .
Love, J. (2007). Process automation handbook: A guide to theory and practice . London: Springer. doi: 10.1007/978-1-84628-282-9 .
Luttropp, C., & Johansson, J. (2010). Improved recycling with lifecycle information tagged to the product. Journal of Cleaner Production, 18 (4), 346–354. doi: 10.1016/j.jclepro.2009.10.023 .
Ma, D., & Saxena, N. (2014). A context-aware approach to defend against unauthorized reading and relay attacks in RFID systems. Security and Communication Networks, 7 , 2684–2695. doi: 10.1002/sec.404 .
Madaan, J., & Choudhary, D. (2015). A flexible decision model for risk analysis in product recovery systems. Global Journal of Flexible Systems Management, 16 (4), 313–329. doi: 10.1007/s40171-015-0102-4 .
Maffia, M., Mainetti, L., Patrono, L., & Urso, E. (2012). Evaluation of potential effects of RFID-based item-level tracing systems on the integrity of biological pharmaceutical products. International Journal of RF Technologies: Research and Applications, 3 (2), 101–118. doi: 10.3233/RFT-2012-022 .
Maleki, R. A., & Meiser, G. (2011). Managing returnable containers logistics—A case study: Part II—Improving visibility through using automatic identification technologies. International Journal of Engineering Business Management, 3 (2), 45–54. doi: 10.5772/50936 .
Mangla, S., Kumar, P., & Barua, M. (2015). Flexible decision modeling for evaluating the risks in green supply chain using fuzzy AHP and IRP methodologies. Global Journal of Flexible Systems Management, 16 (1), 19. doi: 10.1007/s40171-014-0081-x .
McCarthy, U., Ayalew, G., Butler, F., McDonnell, K., & Ward, S. (2011). The case for UHF RFID application in the meat supply chain in the Irish context: A review perspective. Agricultural Engineering International: CIGR Journal, 13 (3), 1125–1131.
McFarlane, D., Sarma, S., Chirn, J., Wong, C., & Ashton, K. (2003). Auto ID systems and intelligent manufacturing control. Engineering Applications of Artificial Intelligence, 16 (4), 365–376. doi: 10.1016/S0952-1976(03)00077-0 .
Mehrjerdi, Y. Z. (2010). RFID-enabled healthcare systems: Risk–benefit analysis. International Journal of Pharmaceutical and Healthcare Marketing, 4 (3), 282–300. doi: 10.1108/17506121011076192 .
Mehrjerdi, Y. Z. (2013). A framework for Six-Sigma driven RFID-enabled supply chain systems. International Journal of Quality and Reliability Management, 30 (2), 142–160. doi: 10.1108/02656711311293562 .
Meiller, Y., Bureau, S., Zhou, W., & Piramuthu, S. (2011). Adaptive knowledge-based system for health care applications with RFID-generated information. Decision Support Systems, 51 (1), 198–207. doi: 10.1016/j.dss.2010.12.008 .
Mejjaouli, S., & Babiceanu, R. F. (2015). RFID-wireless sensor networks integration: Decision models and optimization of logistics systems operations. Journal of Manufacturing Systems, 35 , 234–245. doi: 10.1016/j.jmsy.2015.02.005 .
Memon, Q. A., & Khoja, S. A. (2012). RFID-based patient tracking for regional collaborative healthcare. International Journal of Computer Applications in Technology, 45 (4), 231–244. doi: 10.1504/IJCAT.2012.051123 .
Metters, R. (1997). Quantifying the bullwhip effect in supply chains. Journal of Operations Management, 15 (2), 89–100. doi: 10.1016/S0272-6963(96)00098-8 .
Meyer, H., Fuchs, F., & Thiel, K. (2009). Manufacturing execution systems (MES): Optimal design, planning, and deployment . New York: McGraw-Hill Companies Inc.
Meyer-Larsen, N., Müller, R., Lyridis, D., & Zacharioudakis, P. (2012). Improving intermodal container logistics and security by RFID. International Journal of RF Technologies: Research and Applications, 3 (1), 15–38. doi: 10.3233/RFT-2011-015 .
Miragliotta, G., Perego, A., & Tumino, A. (2009). A quantitative model for the introduction of RFID in the fast moving consumer goods supply chain: Are there any profits? International Journal of Operations and Production Management, 29 (10), 1049–1082. doi: 10.1108/01443570910993483 .
Mirza, Z., & Brohi, M. N. (2013). An in-depth analysis on integrating campus radio frequency identification system on clouds for enhancing security. Journal of Computer Science, 9 (12), 1710–1714. doi: 10.3844/jcssp.2013.1710.1714 .
Mishra, A., & Mishra, D. (2010). Application of RFID in aviation industry: An exploratory review. Promet-Traffic-Traffico, 22 (5), 363–372.
Muir, S. (2007). RFID security concerns. Library Hi Tech, 25 (1), 95–107. doi: 10.1108/07378830710735885 .
Musa, A., Gunasekaran, A., & Yusuf, Y. (2014a). Supply chain product visibility: Methods, systems and impacts. Expert Systems with Applications, 41 (1), 176–194. doi: 10.1016/j.eswa.2013.07.020 .
Musa, A., Gunasekaran, A., Yusuf, Y., & Abdelazim, A. (2014b). Embedded devices for supply chain applications: Towards hardware integration of disparate technologies. Expert Systems with Applications, 41 (1), 137–155. doi: 10.1016/j.eswa.2013.07.017 .
Nativi, J. J., & Lee, S. (2012). Impact of RFID information-sharing strategies on a decentralized supply chain with reverse logistics operations. International Journal of Production Economics, 136 (2), 366–377. doi: 10.1016/j.ijpe.2011.12.024 .
Ngai, E., Cheng, T., Au, S., & Lai, K. (2007). Mobile commerce integrated with RFID technology in a container depot. Decision Support Systems, 43 (1), 62–76. doi: 10.1016/j.dss.2005.05.006 .
Ngai, E. W. T., Cheng, T. C. E., Lai, K., Chai, P. Y. F., Choi, Y. S., & Sin, R. K. Y. (2007). Development of an RFID-based traceability system: experiences and lessons learned from an aircraft engineering company. Production and Operations Management, 16 (5), 554-568. doi: 10.1111/j.1937-5956.2007.tb00280.x .
Ngai, E. W. T., Cheung, B. K. S., Lam, S. S., & Ng, C. T. (2014). RFID value in aircraft parts supply chains: A case study. International Journal of Production Economics, 147 (PART B), 330–339. doi: 10.1016/j.ijpe.2012.09.017 .
Ngai, E. T., Leung, T. P., Wong, Y. H., Lee, M. M., Chai, P. F., & Choi, Y. S. (2012). Design and development of a context-aware decision support system for real-time accident handling in logistics. Decision Support Systems, 52 (4), 816–827. doi: 10.1016/j.dss.2011.11.016 .
Ngai, E. W. T., Li, C.-L., Cheng, T. C. E., Lun, Y. H. V., Lai, K.-H., Cao, J., & Lee, M. C. M. (2011). Design and development of an intelligent context-aware decision support system for real-time monitoring of container terminal operations. International Journal of Production Research, 49 (12), 3501–3526. doi: 10.1080/00207541003801291 .
Ngai, E. W. T., Moon, K. K. L., Liu, J. N. K., Tsang, K. F., Law, R., & Wong, I. C. L. (2008). Extending CRM in the retail industry: An RFID-based personal shopping assistant system. Communications of the Association for Information Systems, 23 (1), 277–294.
Ngai, E. W. T., Moon, K. K. L., Riggins, F. J., & Yi, C. Y. (2008). RFID research: An academic literature review (1995–2005) and future research. International Journal of Production Economics, 112 (2), 510–520. doi: 10.1016/j.ijpe.2007.05.004 .
Nguyen, S. D., Pham, T. T., Blanc, F. F., Le, N. N., Dang, C. M., & Tedjini, S. (2013). Approach for quality detection of food by RFID-based wireless sensor tag. Electronics Letters, 49 (25), 1588–1589. doi: 10.1049/el.2013.3328 .
Nummela, J., Lehto, A., Ukkonen, L., & Sydänheimo, L. (2009). Automatic reel identification by RFID technology in paper reel supply chains: Examples from paper mill and sea port environments. International Journal of RF Technologies: Research and Applications, 1 (3), 194–213. doi: 10.1080/17545730903140851 .
Ondemir, O., & Gupta, S. (2014). A multi-criteria decision making model for advanced repair-to-order and disassembly-to-order system. European Journal of Operational Research, 233 (2), 408–419. doi: 10.1016/j.ejor.2013.09.003 .
Ondemir, O., Ilgin, M. A., & Gupta, S. M. (2012). Optimal end-of-life management in closed-loop supply chains using RFID and sensors. IEEE Transactions on Industrial Informatics, 8 (3), 719–728. doi: 10.1108/S0276-8976(2012)0000015009 .
Oztekin, A., Pajouh, F. M., Delen, D., & Swim, L. K. (2010). An RFID network design methodology for asset tracking in healthcare. Decision Support Systems, 49 (1), 100–109. doi: 10.1016/j.dss.2010.01.007 .
Page, D. (2000). The case for smart luggage. Science Spectra, 21 , 12–15.
Peppa, V., & Moschuris, S. (2013). RFID technology in supply chain management: A review of the literature and prospective adoption to the Greek market. Global Journal of Engineering Education, 15 (1), 61–68.
Piramuthu, S., Farahani, P., & Grunow, M. (2013). RFID-generated traceability for contaminated product recall in perishable food supply networks. European Journal of Operational Research, 225 (2), 253–262. doi: 10.1016/j.ejor.2012.09.024 .
Poon, T. C., Choy, K. L., Chan, F. T. S., Ho, G. T. S., Gunasekaran, A., & Lau, H. C. W. (2011). A real-time warehouse operations planning system for small batch replenishment problems in production environment. Expert Systems with Applications, 38 (7), 8524–8537. doi: 10.1016/j.eswa.2011.01.053 .
Poon, T. C., Choy, K. L., Chow, H. K. H., Lau, H. C. W., Chan, F. T. S., & Ho, K. C. (2009). A RFID case-based logistics resource management system for managing order picking operations in warehouses. Expert Systems with Applications, 36 (4), 8277–8301. doi: 10.1016/j.eswa.2008.10.011 .
Rahman, F., & Ahamed, S. I. (2012). Efficient detection of counterfeit products in large-scale RFID systems using batch authentication protocols. Personal and Ubiquitous Computing, 18 (1), 177–188. doi: 10.1007/s00779-012-0629-8 .
Raman, A. (2000). Retail data quality: Evidence, causes, costs, and fixes. Technology in Society, 22 (1), 97–109. doi: 10.1016/S0160-791X(99)00037-8 .
Ranasinghe, D. C., Harrison, M., Främling, K., & McFarlane, D. (2011). Enabling through life product-instance management: Solutions and challenges. Journal of Network and Computer Applications, 34 (3), 1015–1031.
Rantasila, K., Hinkka, V., Pilli-Sihvola, E., & Permala, A. (2014). Unveiling the RFID business: A survey of the Finnish RFID sector. International Journal of Radio Frequency Identification Technology and Applications, 4 (3), 244–259. doi: 10.1504/IJRFITA.2014.063917 .
Ravi, V. (2014). Reverse logistics operations in automobile industry: A case study using SAP-LAP approach. Global Journal of Flexible Systems Management, 15 (4), 295–303.
Ray, B. R., Abawajy, J., & Chowdhury, M. (2014). Scalable RFID security framework and protocol supporting Internet of things. Computer Networks, 67 , 89–103. doi: 10.1016/j.comnet.2014.03.023 .
Rekik, Y. (2011). Inventory inaccuracies in the wholesale supply chain. International Journal of Production Economics, 133 (1), 172–181. doi: 10.1016/j.ijpe.2010.02.012 .
Rekik, Y., Jemai, Z., Sahin, E., & Dallery, Y. (2007). Improving the performance of retail stores subject to execution errors: Coordination versus RFID technology. OR Spectrum, 29 (4), 597–626.
Rekleitis, E., Rizomiliotis, P., & Gritzalis, S. (2014). How to protect security and privacy in the IoT: A policy-based RFID tag management protocol. Security and Communication Networks, 7 (12), 2669–2683.
Revere, L., Black, K., & Zalila, F. (2010). RFIDs can improve the patient care supply chain. Hospital Topics, 88 (1), 26–31.
Rinaldi, R., & Bandinelli, R. (2015). A model to evaluate logistics RFID-based investments economic effectiveness in the apparel field. International Journal of RF Technologies: Research and Applications, 6 (2&3), 121–150. doi: 10.3233/RFT-140063 .
Roper, K. O., Sedehi, A., & Ashuri, B. (2014). A cost-benefit case for RFID implementation in hospitals: Adapting to industry reform. Facilities, 33 (5/6), 367–388. doi: 10.1108/F-05-2013-0041 .
Ross, D. F. (2015). Distribution Planning and Control: Managing in the Era of Supply Chain Management . New York: Springer.
Ross, A. D., Twede, D., Clarke, R. H., & Ryan, M. (2009). A framework for developing implementation strategies for a radio frequency identification (RFID) system in a distribution center environment. Journal of Business Logistics, 30 (1), 157–183.
Safari, A., Fesharaki, H. M., & Fesharaki, H. H. (2013). Examining the role of RFID technology on SCM effectiveness, case: Food industry of Iran. International Journal of Information Science and Management, 11 , 97–110.
Sahin, E., Buzacott, J., & Dallery, Y. (2008). Analysis of a newsvendor which has errors in inventory data records. European Journal of Operational Research, 188 (2), 370–389. doi: 10.1016/j.ejor.2007.04.021 .
Sandhya, M., & Rangaswamy, T. R. (2011). A secure and efficient authentication protocol for mobile RFID systems. Journal of Digital Information Management, 9 (3), 99–105.
Sarac, A., Absi, N., & Dauzère-Pérès, S. (2010). A literature review on the impact of RFID technologies on supply chain management. International Journal of Production Economics, 128 (1), 77–95. doi: 10.1016/j.ijpe.2010.07.039 .
Sari, K. (2008). Inventory inaccuracy and performance of collaborative supply chain practices. Industrial Management and Data Systems, 108 (4), 495–509. doi: 10.1108/02635570810868353 .
Sari, K. (2010). Exploring the impacts of radio frequency identification (RFID) technology on supply chain performance. European Journal of Operational Research, 207 (1), 174–183. doi: 10.1016/j.ejor.2010.04.003 .
Saygin, C. (2007). Adaptive inventory management using RFID data. International Journal of Advanced Manufacturing Technology, 32 (9), 1045–1051. doi: 10.1007/s00170-006-0616-1 .
Schapranow, M.-P., Müller, J., Zeier, A., & Plattner, H. (2011). Costs of authentic pharmaceuticals: Research on qualitative and quantitative aspects of enabling anti-counterfeiting in RFID-aided supply chains. Personal and Ubiquitous Computing, 16 (3), 271–289. doi: 10.1007/s00779-011-0390-4 .
Schmidt, M., Thoroe, L., & Schumann, M. (2013). RFID and barcode in manufacturing logistics: Interface concept for concurrent operation. Information Systems Management, 30 (2), 100–115. doi: 10.1080/10580530.2013.773801 .
Sheng, Q. Z., Zeadally, S., Mitrokotsa, A., & Maamar, Z. (2011). RFID technology, systems, and applications. Journal of Network and Computer Applications, 34 (3), 797–798. doi: 10.1016/j.jnca.2010.07.008 .
Shi, J., Li, Y., He, W. & Sim, D. (2012). SecTTS: A secure track and trace system for RFID-enabled supply chains. Computers in Industry, 63 (6), 574–585. doi: 10.1016/j.compind.2012.03.006 .
Shi, J., Zhang, J., & Qu, X. (2010). Optimizing distribution strategy for perishable foods using RFID and sensor technologies. Journal of Business and Industrial Marketing, 25 (8), 596–606. doi: 10.1108/08858621011088338 .
Shin, T. H., Chin, S., Yoon, S. W., & Kwon, S. W. (2011). A service-oriented integrated information framework for RFID/WSN-based intelligent construction supply chain management. Automation in Construction, 20 (6), 706–715. doi: 10.1016/j.autcon.2010.12.002 .
Shin, S., & Eksioglu, B. (2015). An empirical study of RFID productivity in the U.S. retail supply chain. International Journal of Production Economics, 163 , 89–96. doi: 10.1016/j.ijpe.2015.02.016 .
Singh, N. K., & Mahajan, P. (2014). RFID and its use in libraries: A literature review. International Journal of Information Dissemination and Technology, 4 (2), 117–123.
Singh, S. P., McCartney, M., Singh, J., & Clarke, R. (2008). RFID research and testing for packages of apparel, consumer goods and fresh produce in the retail distribution environment. Packaging Technology and Science, 21 (2), 91–102. doi: 10.1002/pts.782 .
Singh, G., & Midha, M. (2008). RFID: A new technology in library management systems. Journal of Interlibrary Loan, Document Delivery and Electronic Reserve, 18 (4), 439–447. doi: 10.1080/10723030802181778 .
Smart, A. U., Bunduchi, R., & Gerst, M. (2010). The costs of adoption of RFID technologies in supply networks. International Journal of Operations and Production Management, 30 (4), 423–447. doi: 10.1108/01443571011029994 .
Sooksaksun, N., & Sudsertsin, S. (2014). The application of RFID in warehouse process: Case study of consumer product manufacturer in Thailand. Scientific Journal of Logistics, 10 (4), 423–431.
Srivastava, B. (2004). Radio frequency ID technology: The next revolution in supply chain management. Business Horizons, 47 (6), 60–68. doi: 10.1016/j.bushor.2004.09.009 .
Stadtler, H., & Kilger, C. (2008). Supply chain management and advanced planning: Concepts, models, software and case studies . Berlin: Springer.
Stankovski, S., Lazarevic, M., Ostojic, G., Cosic, I., & Puric, R. (2009). RFID technology in product/part tracking during the whole lifecycle. Assembly Automation, 29 (4), 364–370. doi: 10.1108/01445150910987781 .
Su, C.-Y., & Roan, J. (2013). Using Hurst exponent to investigate the impact of RFID implementation on supply chain dynamics. International Journal of Business and Management, 8 (10), 52–66. doi: 10.5539/ijbm.v8n10p52 .
Subramanian, S., & Hariharan, R. (2015). Automated trolley for library book arrangement and shelf management. International Journal of Computational Science and Engineering, 10 (4), 415–422.
Sun, C., Jiang, F., & Jiang, S. (2013). Research on RFID applications in construction industry. Journal of Networks, 8 (5), 1221–1228. doi: 10.4304/jnw.8.5.1221-1228 .
Swartz, S. M., Vaidyanathan, V., & Raman, H. (2010). A post-retail consumer application of RFID in medical supply chains. Journal of Business and Industrial Marketing, 25 (8), 607–611. doi: 10.1108/08858621011088347 .
Szmerekovsky, J. G., Tilson, V., & Zhang, J. (2011). Analytical model of adoption of item level RFID in a two-echelon supply chain with shelf-space and price-dependent demand. Decision Support Systems, 51 (4), 833–841. doi: 10.1109/HICSS.2010.447 .
Tajima, M. (2007). Strategic value of RFID in supply chain management. Journal of Purchasing and Supply Management, 13 (4), 261–273. doi: 10.1016/j.pursup.2007.11.001 .
Thiesse, F., AI-Kassab, J., & Fleisch, E. (2009). Understanding the value of integrated RFID systems: A case study from apparel retail. European Journal of Information Systems, 18 (6), 592–614. doi: 10.1057/ejis.2009.33 .
Thiesse, F., & Buckel, T. (2015). A comparison of RFID-based shelf replenishment policies in retail stores under suboptimal read rates. International Journal of Production Economics, 159 , 126–136. doi: 10.1016/j.ijpe.2014.09.002 .
Thoroe, L., Knothe, B., Raabe, K., & Schumann, M. (2011). Impacts of item-level RFID on packaging waste recycling: Exploratory study of the industry’s expectations in Germany. International Journal of Innovation and Sustainable Development, 5 (4), 358–370.
Thoroe, L., Melski, A., & Schumann, M. (2009). The impact of RFID on management of returnable containers. Electronic Markets, 19 (2–3), 115–124. doi: 10.1007/s12525-009-0013-3 .
Tyagi, M., Kumar, P., & Kumar, D. (2015). Assessment of critical enablers for flexible supply chain performance measurement system using fuzzy DEMATEL approach. Global Journal of Flexible Systems Management, 16 (2), 115–132. doi: 10.1007/s40171-014-0085-6 .
Tzeng, S. F., Chen, W. H., & Pai, F. Y. (2008). Evaluating the business value of RFID: Evidence from five case studies. International Journal of Production Economics, 112 (2), 601–613. doi: 10.1016/j.ijpe.2007.05.009 .
Uckelmann, D., Hamann, T., & Zschintzsch, M. (2009). Performance increase and benefit compensation in supply chains by partial information sharing and billing based on identification of returnable transport items. International Journal of RF Technologies: Research and Applications, 1 (1), 23–43. doi: 10.1080/17545730802474039 .
Uçkun, C., Karaesmen, F., & Savaş, S. (2008). Investment in improved inventory accuracy in a decentralized supply chain. International Journal of Production Economics, 113 (2), 546–566. doi: 10.1016/j.ijpe.2007.10.012 .
Ustundag, A. (2010). Evaluating RFID investment on a supply chain using tagging cost sharing factor. International Journal of Production Research, 48 (9), 2549–2562. doi: 10.1080/00207540903564926 .
Ustundag, A. L. P., & Ikcan, E. C. E. V. (2008). Vehicle route optimization for RFID integrated waste collection system. International Journal of Information Technology and Decision Making, 7 (4), 611–625. doi: 10.1142/S0219622008003125 .
Ustundag, A., & Tanyas, M. (2009). The impacts of radio frequency identification (RFID) technology on supply chain costs. Transportation Research Part E: Logistics and Transportation Review, 45 (1), 29–38. doi: 10.1016/j.tre.2008.09.001 .
Valero, E., Adán, A., & Cerrada, C. (2015). Evolution of RFID applications in construction: A literature review. Sensors, 15 (7), 15988–16008. doi: 10.3390/s150715988 .
Vecchi, A., & Brennan, L. (2010). RFID supply chain implementation challenges for short-life products. International Journal of RF Technologies: Research and Applications, 2 (2), 117–134. doi: 10.3233/RFT-2010-008 .
Veeramani, D., Tang, J., & Gutierez, A. (2008). A framework for assessing the value of RFID implementation by tier-one suppliers to major retailers. Journal of Theoretical and Applied Electronic Commerce Research, 3 (1), 55–70.
Véronneau, S., & Roy, J. (2009). RFID benefits, costs, and possibilities: The economical analysis of RFID deployment in a cruise corporation global service supply chain. International Journal of Production Economics, 122 (2), 692–702. doi: 10.1016/j.ijpe.2009.06.038 .
Vijayaraman, B. S., & Osyk, B. A. (2006). An empirical study of RFID implementation in the warehousing industry. The International Journal of Logistics Management, 17 (1), 6–20. doi: 10.1108/09574090610663400 .
Vishwa, V. K., & Felix, T. S. C. (2010). A superiority search and optimization algorithm to solve RFID and an environmental factor embedded closed loop logistics model. International Journal of Production Research, 49 (16), 4807–4831. doi: 10.1080/00207543.2010.503201 .
Visich, J. K., & Khumawala, B. M. (2007). Enhancing product recovery value in closed-loop supply chains with RFID. Journal of Managerial Issues, 19 (3), 436–453.
Visich, J. K., Li, S., Khumawala, B. M., & Reyes, P. M. (2009). Empirical evidence of RFID impacts on supply chain performance. International Journal of Operations and Production Management, 29 (12), 1290–1315. doi: 10.1108/01443570911006009 .
Vlachos, I. P. (2013). A hierarchical model of the impact of RFID practices on retail supply chain performance. Expert Systems with Applications, 41 (1), 5–15. doi: 10.1016/j.eswa.2013.07.006 .
Vlachos, I. P. (2014). A hierarchical model of the impact of RFID practices on retail supply chain performance. Expert Systems with Applications, 41 (1), 5–15.
Wadhwa, S., Ducq, Y., Saxena, A., & Prakash, A. (2008). Supply chain as a flexible system: A KM focused competence. Global Journal of Flexible Systems Management, 9 (2/3), 15–30.
Wamba, S. F. (2012a). Achieving supply chain integration using RFID technology: The case of emerging intelligent B-to-B e-commerce processes in a living laboratory. Business Process Management Journal, 18 (1), 58–81. doi: 10.1108/14637151211215019 .
Wamba, S. F. (2012b). RFID-enabled healthcare applications, issues and benefits: An archival analysis (1997-2011). Journal of Medical Systems, 36 (6), 3393–3398. doi: 10.1007/s10916-011-9807-x .
Wamba, S. F., Anand, A., & Carter, L. (2013a). A literature review of RFID-enabled healthcare applications and issues. International Journal of Information Management, 33 (5), 875–891. doi: 10.1016/j.ijinfomgt.2013.07.005 .
Wamba, S. F., Anand, A., & Carter, L. (2013b). RFID applications, issues, methods and theory: A review of the AIS basket of TOP journals. Procedia Technology, . doi: 10.1016/j.protcy.2013.12.047 .
Wamba, S. F., & Boeck, H. (2008). Enhancing information flow in a retail supply chain using RFID and the EPC network: A proof-of-concept approach. Journal of Theoretical and Applied Electronic Commerce Research, 3 (1), 92–105.
Wamba, S. F., & Chatfield, A. T. (2009). A contingency model for creating value from RFID supply chain network projects in logistics and manufacturing environments. European Journal of Information Systems, 18 (6), 615–636. doi: 10.1057/ejis.2009.44 .
Wang, L. (2010). RFID-empowered monitoring and controlling for advanced manufacturing. International Journal of Manufacturing Technology and Management, 21 (3–4), 308–315. doi: 10.1504/IJMTM.2010.035437.308-315 .
Wang, H., Chen, S., & Xie, Y. (2010a). An RFID-based digital warehouse management system in the tobacco industry: A case study. International Journal of Production Research, 48 (9), 2513–2548. doi: 10.1080/00207540903564918 .
Wang, J., Cheng, L., & Liu, J. (2014). A complex event detection method for multi-probability RFID event stream. Journal of Software, 9 (4), 834–840.
Wang, S.-J., Huang, C.-T., Wang, W.-L., & Chen, Y.-H. (2010b). Incorporating ARIMA forecasting and service-level based replenishment in RFID-enabled supply chain. International Journal of Production Research, 48 (9), 2655–2677. doi: 10.1080/00207540903564983 .
Wang, L.-C., Lin, Y.-C., & Lin, P. H. (2007). Dynamic mobile RFID-based supply chain control and management system in construction. Advanced Engineering Informatics, 21 (4), 377–390. doi: 10.1016/j.aei.2006.09.003 .
Wang, S., Liu, S., & Chen, D. (2015). Security analysis and improvement on two RFID authentication protocols. Wireless Personal Communications, 82 (1), 21–33.
Wang, S. J., Liu, S. F., & Wang, W. L. (2008). The simulated impact of RFID-enabled supply chain on pull-based inventory replenishment in TFT-LCD industry. International Journal of Production Economics, 112 (2), 570–586. doi: 10.1016/j.ijpe.2007.05.002 .
Wang, W., Wang, X., & Archer, N. (2006). RFID implementation issues in China: Shanghai Port case study. Journal of Internet Commerce, 5 (4), 89–104. doi: 10.1300/J179v05n04_06 .
Wang, S.-J., Wang, W.-L., Huang, C.-T., & Chen, S.-C. (2011). Improving inventory effectiveness in RFID-enabled global supply chain with Grey forecasting model. The Journal of Strategic Information Systems, 20 (3), 307–322. doi: 10.1016/j.jsis.2011.03.003 .
Wei, Z., Kapoor, G., & Piramuthu, S. (2009). RFID-enabled item-level product information revelation. European Journal of Information Systems, 18 (6), 570–577. doi: 10.1057/ejis.2009.45 .
Wei, G., & Zhang, H. (2013). A lightweight authentication protocol scheme for RFID security. Wuhan University Journal of Natural Sciences, 18 (6), 504–510. doi: 10.1007/s11859-013-0964-2 .
Wen, T., & Chang, Y. (2008). Cost-benefit analysis of RFID application in apparel retailing for SME: A case from Taiwan. Transport Journal, 49 (3), 57–66.
Wen, L., Zailani, S., & Fernando, Y. (2009). Determinants of RFID adoption in supply chain among manufacturing companies in China: A discriminant analysis. Journal of Technology Management and Innovation, 4 (1), 22–33. doi: 10.4067/S0718-27242009000100003 .
Whang, S. (2010). Timing of RFID adoption in a supply Chain. Management Science, 56 (2), 343–355.
Whitaker, J., Mithas, S., & Krishnan, M. S. (2007). A field study of RFID deployment return expectations. Production and Operations Management, 16 (5), 599–612. doi: 10.1111/j.1937-5956.2007.tb00283.x .
White, A., Johnson, M., & Wilson, H. (2008). RFID in the supply chain: lessons from European early adopters. International Journal of Physical Distribution and Logistics Management, 38 (2), 88–107. doi: 10.1108/09600030810861189 .
Will, T., & Blecker, T. (2012). RFID-driven process modifications in container logistics: SOA as a solution approach. International Journal of Logistics Research and Applications, 15 (2), 71–86. doi: 10.1080/13675567.2012.674106 .
Wu, N. C., Nystrom, M. A., Lin, T. R., & Yu, H. C. (2006). Challenges to global RFID adoption. Technovation, 26 (12), 1317–1323. doi: 10.1016/j.technovation.2005.08.012 .
Wu, Y., Sheng, Q. Z., Shen, H., & Zeadally, S. (2013). Modeling object flows from distributed and federated RFID data streams for efficient tracking and tracing. IEEE Transactions on Parallel and Distributed Systems, 24 (10), 2036–2045. doi: 10.1109/TPDS.2013.99 .
Xiangsheng, K. (2014). RFID event analysis based on complex event processing. International Journal of Online Engineering, 10 (1), 5–9.
Xu, D., & Chen, Y. (2013). A safe RFID authentication protocol for Internet of things. Journal of Theoretical and Applied Information Technology, 48 (1), 215–220.
Xu, J., Feng, G., Tian, J., & Jiang, W. (2012). Comparing improvement strategies for inventory inaccuracy in a two-echelon supply chain. European Journal of Operational Research, 221 (1), 213–221. doi: 10.1016/j.ejor.2012.03.008 .
Yan, B., Hu, D., & Shi, P. (2012). A traceable platform of aquatic foods supply chain based on RFID and EPC Internet of things. International Journal of RF Technologies: Research and Applications, 4 (1), 55–70. doi: 10.3233/RFT-2012-0035 .
Yang, H., Yang, L., & Yang, S.-H. (2013). Hybrid Zigbee-RFID sensor network for humanitarian logistics centre management. Journal of Network and Computer Applications, 34 (3), 938–948. doi: 10.1016/j.jnca.2010.04.017 .
Yao, W., Chu, C., & Li, Z. (2012). The adoption and implementation of RFID technologies in healthcare: A literature review. Journal of Medical Systems, 36 (6), 3507–3525. doi: 10.1007/s10916-011-9789-8 .
Yazici, H. J. (2014). An exploratory analysis of hospital perspectives on real time information requirements and perceived benefits of RFID technology for future adoption. International Journal of Information Management, 34 (5), 603–621. doi: 10.1016/j.ijinfomgt.2014.04.010 .
Yen, C.-T., Guo, M.-H., Lo, N.-W., & Deng, D.-J. (2013). Authentication with low-cost RFID tags in mobile networks. Security and Communication Networks, 6 (8), 1021–1027.
Ygal, B. (2013). Review: RFID-enabled applications to improve the delivery of healthcare services: A typology and supporting technologies. Journal of Medical and Biological Engineering, 33 (5), 433–442. doi: 10.5405/jmbe.1279 .
Yi, H.-C., & Park, J. W. (2015). Design and implementation of an end-of-life vehicle recycling center based on IoT (Internet of Things) in Korea. Procedia CIRP, 29 , 728–733.
Yoon, E. J., & Zhou, W. (2011). Mixed strategy multiple-channel retailing with RFID information. Journal of Organizational Computing and Electronic Commerce, 21 (4), 368–383. doi: 10.1080/10919392.2011.614557 .
Yu, S.-C. (2007). RFID implementation and benefits in libraries. The Electronic Library, 25 (1), 54–64. doi: 10.1108/02640470710729119 .
Yüksel, A. S., & Yüksel, M. E. (2011). RFID technology in business systems and supply chain management. Journal of Economic and Social Studies, 1 (1), 53–71.
Zeimpekis, V., Minis, I., & Pappa, V. (2010). Real-time logistics management of dried figs using RFID technology: Case study in a Greek cooperative company. International Journal of Logistics Systems and Management, 7 (3), 265–285. doi: 10.1504/IJLSM.2010.035035 .
Zelbst, P. J., Green, K. W., & Sower, V. E. (2010). Impact of RFID technology utilization on operational performance. Management Research Review, 33 (10), 994–1004. doi: 10.1108/01409171011083996 .
Zelbst, P. J., Green, K. W., Sower, V. E., & Abshire, R. D. (2014). Impact of RFID and information sharing on JIT, TQM and operational performance. Management Research Review, 37 (11), 970–989. doi: 10.1108/MRR-10-2014-273 .
Zelbst, P. J., Green, K. W., Sower, V. E., & Reyes, P. M. (2012). Impact of RFID on manufacturing effectiveness and efficiency. International Journal of Operations and Production Management, 32 (3), 329–350. doi: 10.1108/01443571211212600 .
Zhang, Y., Huang, G. Q., Qu, T., & Ho, O. (2010). Agent-based workflow management for RFID-enabled real-time reconfigurable manufacturing. International Journal of Computer Integrated Manufacturing, 23 (2), 101–112. doi: 10.1080/09511920903440354 .
Zhang, M., & Li, P. (2012). RFID application strategy in agri-food supply chain based on safety and benefit analysis. Physics Procedia, 25 , 636–642. doi: 10.1016/j.phpro.2012.03.137 .
Zhang, X., Yue, S., & Wang, W. (2006). The review of RFID applications in global postal and courier services. Journal of China Universities of Posts and Telecommunications, 13 (4), 106–110. doi: 10.1016/S1005-8885(07)60045-4 .
Zhong, R. Y., Huang, G. Q., Lan, S., Dai, Q. Y., Chen, X., & Zhang, T. (2015). A big data approach for logistics trajectory discovery from RFID-enabled production data. International Journal of Production Economics, 165 , 260–272. doi: 10.1016/j.ijpe.2015.02.014 .
Zhong, R. Y., Huang, G. Q., Lan, S., Dai, Q. Y., Zhang, T., & Xu, C. (2015). A two-level advanced production planning and scheduling model for RFID-enabled ubiquitous manufacturing. Advanced Engineering Informatics, 29 (4), 799–812. doi: 10.1016/j.aei.2015.01.002 .
Zhou, W. (2009). RFID and item-level information visibility. European Journal of Operational Research, 198 (1), 252–258. doi: 10.1016/j.ejor.2008.09.017 .
Zhou, W., & Piramuthu, S. (2012). Consumer preference and service quality management with RFID. Annals of Operations Research, 216 (1), 1–17. doi: 10.1007/s10479-012-1082-9 .
Zhou, W., & Piramuthu, S. (2013). Remanufacturing with RFID item-level information: Optimization, waste reduction and quality improvement. International Journal of Production Economics, 145 (2), 647–657. doi: 10.1016/j.ijpe.2013.05.019 .
Zhou, W., & Piramuthu, S. (2015a). Effect of ticket-switching on inventory and shelf-space allocation. Decision Support Systems, 67 , 6931–6939. doi: 10.1016/j.dss.2014.11.004 .
Zhou, W., & Piramuthu, S. (2015b). Effects of ticket-switching on inventory management: Actual vs. information system-based data. Decision Support Systems, 77 , 7731–7740. doi: 10.1016/j.dss.2015.05.010 .
Zhou, W., Tu, Y., & Piramuthu, S. (2009). RFID-enabled item-level retail pricing. Decision Support Systems, 48 (1), 169–179. doi: 10.1016/j.dss.2009.07.008 .
Zhou, W., Yoon, E. J., & Piramuthu, S. (2012). Simultaneous multi-level RFID tag ownership and transfer in health care environments. Decision Support Systems, 54 (1), 98–108. doi: 10.1016/j.dss.2012.04.006 .
Zhu, X., Mukhopadhyay, S. K., & Kurata, H. (2012). A review of RFID technology and its managerial applications in different industries. Journal of Engineering and Technology Management, 29 (1), 152–167.
Zhuang, X., Zhu, Y., & Chang, C.-C. (2014). A new ultralight weight RFID protocol for low-cost tags: R 2 AP. Wireless Personal Communications, 79 , 1787–1802.
Zipkin, P. (2006). The best things in life were free: On the technology of transactions. Manufacturing and Service Operations Management, 8 (4), 321–329. doi: 10.1287/msom.1060.0113 .
Zipkin, P. (2007). RFID: Vision or fantasy. International Commerce Review, 7 (1), 69–71. doi: 10.1007/s12146-007-0011-3 .
Download references
Author information
Authors and affiliations.
School of Management, University of Central Lancashire, Preston, PR1 2HE, UK
Ahmed Musa & Al-Amin Abba Dabo
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Ahmed Musa .
Rights and permissions
Reprints and permissions
About this article
Musa, A., Dabo, AA.A. A Review of RFID in Supply Chain Management: 2000–2015. Glob J Flex Syst Manag 17 , 189–228 (2016). https://doi.org/10.1007/s40171-016-0136-2
Download citation
Received : 28 October 2015
Accepted : 23 April 2016
Published : 03 June 2016
Issue Date : June 2016
DOI : https://doi.org/10.1007/s40171-016-0136-2
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cost-benefit analysis
- Inventory management
- Literature review
- Manufacturing process management
- Process optimization and improvement
- Find a journal
- Publish with us
- Track your research
An official website of the United States government
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock icon ) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Publications
- Account settings
- Advanced Search
- Journal List
Radio Frequency Identification (RFID) technology and patient safety
Ahmad rajabzadeh.
- Author information
- Article notes
- Copyright and License information
Address for correspondence: Dr. Sima Ajami, Department of Management and Health Information Technology, Health Management and Economics Research Center, School of Medical Management and Information Sciences, Isfahan University of Medical Sciences, Isfahan, Iran. E-mail: [email protected]
Received 2013 Jun 28; Revised 2013 Jul 6; Accepted 2013 Jul 26.
This is an open-access article distributed under the terms of the Creative Commons Attribution-Noncommercial-Share Alike 3.0 Unported, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Background:
Radio frequency identification (RFID) systems have been successfully applied in areas of manufacturing, supply chain, agriculture, transportation, healthcare, and services to name a few. However, the different advantages and disadvantages expressed in various studies of the challenges facing the technology of the use of the RFID technology have been met with skepticism by managers of healthcare organizations. The aim of this study was to express and display the role of RFID technology in improving patient safety and increasing the impact of it in healthcare.
Materials and Methods:
This study was non-systematical review, which the literature search was conducted with the help of libraries, books, conference proceedings, PubMed databases and also search engines available at Google, Google scholar in which published between 2004 and 2013 during Febuary 2013. We employed the following keywords and their combinations; RFID, healthcare, patient safety, medical errors, and medication errors in the searching areas of title, keywords, abstract, and full text.
The preliminary search resulted in 68 articles. After a careful analysis of the content of each paper, a total of 33 papers was selected based on their relevancy.
Conclusion:
We should integrate RFID with hospital information systems (HIS) and electronic health records (EHRs) and support it by clinical decision support systems (CDSS), it facilitates processes and reduce medical, medication and diagnosis errors.
Keywords: Identification, medical errors, patients, radio, safety, technology
INTRODUCTION
At least 44,000 people, and perhaps as many as 98,000 people, die in hospitals each year as a result of medical errors that could have been prevented.[ 1 ]
Radio frequency identification (RFID) is a wireless technology capable of automatic and unambiguous identification without line of sight by extracting a unique identifier from microelectronic tags attached to objects.[ 2 ]
The RFID is a technology that uses radio waves to transfer data from an electronic tag, called RFID tag attached to an object, through a reader for the purpose of identifying and tracking the object. The RFID is already used to track and trace the victims in a disaster situation. Data can be collected in real time and be immediately available to emergency personnel and saves time by the RFID. Crisis management teams, hospitals and emergency personnel, have access to data through a computer database.[ 3 ]
The RFID was the first explored in the 1940s as a method to identify allied airplanes.[ 4 ] Today, the RFID system have been successfully applied to the areas of manufacturing, supply chain, agriculture, transportation, healthcare, and services to name a few.[ 5 ]
Medical errors could be prevented by building a safer healthcare system. Recently, the RFID has been applied in hospital management. The RFID is valuable for quickly retrieving patient information and monitoring patient locations in the hospital.[ 6 ]
In the past decade, the risk of harm caused by medical care has received increasing scrutiny. The growing sophistication of computers and software should allow information technology to play a vital part in reducing that risk — by streamlining care, catching and correcting errors, assisting with decisions, and providing feedback on performance.[ 7 ] To our knowledge, there have been few previous reports based on on-site experiments showing that the RFID is suited for usage in a hospital, specifically for medication delivery and mapping nurse practice workflow.[ 8 ] Organizational resources and technical structures such as hardware and software are very essential requirements in the redesign of electronic projects.[ 9 ]
Chao et al , in a study titled improving patient safety with RFID and mobile technology announced “These medical errors can be classified into five categories: poor decision making, poor communication, inadequate patient monitoring, patient misidentification, inability to respond rapidly and poor patient tracking. Employing innovative information technologies in correcting these deficiencies and meeting the Joint Commission on Accreditation of Healthcare Organization (JCAHO) patient safety goals is the current trend in enhancing patient safety”.[ 10 ]
The result showed that the RFID adoption though assigned with low level of awareness; adoption capital recompense and infrastructural challenges in the Nigeria health sector in particular also has high and great tendencies to thrive. The result of the second research question revealed that the Nigerian health care service delivery can harness the benefits of the information technology (IT) solution system to function in its clientele servicing in forms like authentication and identification of personnel, patients’ data and blood verification; drug dispensary among others.[ 11 ]
One study shows, “An alarming statistic from an American healthcare organization shows that an average of 195’000 people in the USA died in hospitals in each of the years 2000, 2001 and 2002 as a result of potentially preventable, in-hospital medical errors asserts that “the problem is not bad people in health care — it is that good people are working in bad systems that need to be made safer”.[ 12 ]
Barriers and critical success factors towards RFID technology adoption in South-East Asian healthcare industry showed that most respondents believed that barriers towards the RFID adoption are: (1) lack of information; (2) insufficient budget available; (3) complexity of technology and systems. Critical success factors are: (1) top management support and the commitment of leadership; (2) integrating the data collected; (3) coordinating among departments; and (4) starting with small the RFID project.[ 13 ]
Yao et al , revealed, “The RFID technology offers healthcare practitioners’ advantages to improve patient safety, save time, and reduce costs but also causes critical issues for successful implementation. To increase the acceptance and wide use of RFID in healthcare, more customized the RFID systems, more institutional support, seamless integration with existing HIS, satisfactory security/privacy measures, and mature regulations to protect privacy are needed.”[ 14 ]
How the RFID system works
The most RFID systems consist of tags that are attached to the objects to be identified. Each tag has its own “read only” or “rewrite” internal memory depending on the type and application. A typical configuration of this memory is to store product information, such as an object's unique ID manufactured date, etc. The RFID reader generates magnetic fields that enable the RFID system to locate objects (via the tags) that are within its range. The high-frequency electromagnetic energy and query signal generated by the reader triggers the tags to reply to the query; the query frequency could be up to 50 times per second. As a result communication between the main components of the system i.e. tags and reader are established. As a result large quantities of data are generated. Supply chain industries control this problem by using filters that are routed to the backend information systems. In other words, in order to control this problem, software such as Savant is used. This software acts as a buffer between the IT and the RFID reader.[ 15 ]
Components of an RFID system
The RFID system consists of various components which are integrated in a manner defined in the above section. This allows the RFID system to deduct the objects (tag) and perform various operations on it. The integration of the RFID components enables the implementation of an RFID solution.[ 15 ] The RFID system consists of following five components:
Tag (attached to an object, unique identification).
Antenna (tag detector, creates magnetic field).
Reader (receiver of tag information, manipulator).
Communication infrastructure (enable reader/RFID to work through IT infrastructure).
Application software (user database/application/interface).
In this study the role of the RFID technology in improving patient safety and increase the impact of this technology in the health care industry with was discussed.
MATERIALS AND METHODS
This study was non-systematical review, which the literature search was conducted with the help of libraries, books, conference proceedings, PubMed databases and also search engines available at Google, Google scholar in which published between 2004 and 2013 during Febuary 2013. In our searches, we employed the following keywords and their combinations; RFID, healthcare, patient safety, medical errors, and medication errors in the searching areas of title, keywords, abstract, and full text.
We employed the following keywords and their combinations; RFID, healthcare, patient safety, medical errors, and medication errors in the searching areas of titles, keywords, abstracts, and full texts. The preliminary search resulted in 68 articles. After a careful analysis of the content of each paper, a total of 33 papers was selected based on their relevancy.
The RFID technology used for three purposes: tracking, inventory management, and validation. Each of these characteristics could provide benefits that could yield cost savings and improved productivity.
The RFID is used to follow a product through the supply chain and clinical workflow. It can be used to track a product to a particular patient and identify the clinician who used to say product to a patient. The RFID reduces the amount of time involved in locating or tracking, thereby making the process less cumbersome.[ 16 ]
Inventory management
Inventory management is the most important aspect of managing an organization. It enables managers to monitor usage patterns throughout their organization. It is a complex process that asks what (what is in stock), how (how much is it), who (who has it), where (where is it), and when (when to reorder). The RFID helps manage patient inventories so that the right assets are available when and where they are needed.[ 17 ]
Validation assures that an action has taken place or that the desired item is on hand. Like tracking, the ability to validate through the RFID technology can reduce medical errors, check productivity, and help construct necessary documentation for administrative and audit purposes. The validation is an effective method of ensuring quality in a healthcare setting. The most important validating function is to verify that the patient being treated is, in fact, the right patient and that the treatment that is about to occur is appropriate.[ 18 ]
Studies examining the relationship between the use of RFID and patient safety have been expressed as follows: Patient safety will be improved and costs as well as medication errors will be reduced considerably.[ 19 ]
The RFID can help nurses to quickly identify patients and their corresponding medicine.[ 20 ]
Using the RFID technology, such administration system provides automated medication verification for inpatient's medicine doses and generates corresponding medication evidence, which may be audited later for medical dispute.[ 21 ]
The RFID had great potential for reducing medical errors and nurse workload with high efficiency.[ 22 ] The information technology has to support healthcare in developing practices and nursing patients without confronting any complications or errors. One critical and important part of healthcare is medication care, which is very vulnerable for different kind of errors, even on fatal errors. Thus, medication care needs new methods for avoiding errors in different situations during medication administration. This poster represents an RFID-based automated identification system for medication care in a hospital environment.[ 23 ] The RFID makes the prevention about human error of medicine, easy and fast access to medical staff, equipment, medicine. It is cost effectiveness. All of these factors cause to increase the quality and quantity of care in the healthcare sector.[ 24 ]
In a study that its problem was mislabeling of tissue specimens in their gastrointestinal and colorectal surgery endoscopy units and most labeling errors have been due to either the wrong patient label or no label being affixed to a specimen bottle. As a result, an initiative was created to reduce the number of specimen-labeling errors. This initiative involved the application of radiofrequency identification (RFID) technology to specimen bottles, moving to a paperless pathology requisition system and confirmation of the correct site and correct patient by both the endoscopy nursing staff and the endoscopist for each specimen bottle. Their results confirmed that these data confirm that the initiation of a new specimen-labeling system that uses RFID technology, a paperless requisition process, and confirmation of the correct site and correct patient by two healthcare providers significantly decreased specimen-labeling errors at every level in a high-volume endoscopy center.[ 25 ] Implementation of a practical combined the RFID system that is fully integrated with the clinical system, which one day could be employed in large scale for improving clinical workflow and minimizing medical errors.[ 26 ]
Wisely Aware RFID Dosage (WARD) system, which based on an integration of barcodes and RFID tags, to demonstrate effective and safe patient care environment, for preventing the risk of medication error.[ 27 ] The application of RFID can bring hospitals towards the integration of technology benefits and improved medical safety.[ 28 ]
The RFID by removing the human factor and would improve patient safety by eliminating the current surgical sponge count protocol.[ 29 ]
Table 1 shows some examples of promising completed or on- going the RFID trials, pilots and applications by country.[ 30 ]
The RFID trials, pilots and applications by country[ 30 ]
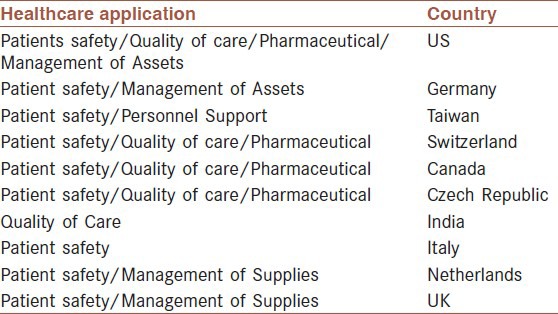
Most RFID applications in health care organizations in the above table, ultimately, patient safety has expressed that safety by Reducing medical errors, and increase the quality of pharmaceutical and diagnostic services is achieved.
The mobile nursing care system using RFID technology strengthens the capabilities of staff to track patient's vital signs across various locations and in different medical facilities. The Mobile Intelligent Medical System (MIMS) includes vital sign monitoring and alarming services, mobile nursing applications, and rule-based clinical decision support in a mobile nursing environment. The system continuously monitors critically ill patients with the objective of reducing the risk of serious harm resulting from the slow provision of health care. Further, we also believe the system can be extended to most medical domains and integrated with other hospital information systems. With more medical centers linked into the system, the MIMS will bring better and safer medical services to the healthcare industry.[ 31 , 32 , 33 ]
The RFID technology has tangible benefits such as reduced cost, time, human resources, and prevention theft.[ 16 ]
CONCLUSIONS
In the healthcare industry, there are other advantages for example; increase accuracy tasks, reduce human errors, improve safety, and patient satisfaction. No doubt, in coming years, using of the RFID will be a requirement in the healthcare industry.
Although, the sole usage of RFID will not be able meet expectation of health care organizations. If it is used alone, health care organizations will be faced with numerous challenges. But, if we integrate it with hospital information systems (HIS) and electronic health records (EHRs) and support it by clinical decision support systems (CDSS), it facilitates magically processes and reduce medical, medication and diagnosis errors.
Summary points
What was already known on this topic?
There are critical successes in improving health services for patients through tracking (staff, patients, and properties), inventory management, and validation (medication, documents, treatment, and specimen).
There are barriers to adopt the RFID that can classify into; lack of information, insufficient budget available, and the complexity of technology and systems.
What this study added to our knowledge?
This technology can facilitate to access individuals (Medical staff and patients) and shorten wait time of care processes.
The RFID technology has tangible benefits such as reduced cost and time, reduced human resources, theft prevention, improve productivity.
In addition, in the healthcare industry, there are also intangible benefits include increasing accuracy tasks, refining business processes and reduce human errors, which will ultimately improve safety and patient satisfaction.
Use of the RFID in health care industry alone will be faced with numerous challenges.
To minimize medical errors and improve clinical workflow, we can implement the RFID system with the clinical system.
If the RFID integrate with hospital information systems (HIS) and Electronic Health Records (EHRs) and supported by clinical decision support systems (CDSS), it can facilitate processes, reduce medication and diagnosis errors, and increase patient safety.
Source of Support: Nil
Conflict of Interest: None declared.
- 1. Kohn LT, Corrigan J, Donaldson MS. Sumter, South Carolina: Natl Academy Pr; 2000. To err is human: Building a safer health system; p. 6. [ PubMed ] [ Google Scholar ]
- 2. Wu Y, Ranasinghe DC, Sheng QZ, Zeadally S, Yu J. RFID enabled traceability networks: A survey. Distrib Parallel Databases. 2011;29:397–443. [ Google Scholar ]
- 3. Ajami S, Akbari B, editors. Isfahan, Iran: Health Management and Economics Research Center, Isfahan University of Medical Sciences; 2012. RFID in Earthquake Information Management System: Work in progress. In Health system, risk management And Disaster. [ Google Scholar ]
- 4. Landt J. Potentials. Vol. 24. New York: IEEE Institute of Electrical and Electronics Engineers; 2005. The history of RFID; pp. 8–11. [ Google Scholar ]
- 5. Nambiar AN. II. San Francisco, USA: 2009. RFID technology: A review of its applications. Proceeding of the World Congress on Engineering and Computer Science October 20-22. [ Google Scholar ]
- 6. Lai CL, Chien SW, Chang LH, Chen SC, Fang K. New York: IEEE Institute of Electrical and Electronics Engineers; 2007. Enhancing medication safety and healthcare for inpatients using RFID. [ Google Scholar ]
- 7. Bates DW, Gawande AA. Improving safety with information technology. N Engl J Med. 2003;348:2526–34. doi: 10.1056/NEJMsa020847. [ DOI ] [ PubMed ] [ Google Scholar ]
- 8. Britton J. An investigation into the feasibility of locating portable medical devices using radio frequency identification devices and technology. J Med Eng Technol. 2007;31:450–8. doi: 10.1080/03091900701292141. [ DOI ] [ PubMed ] [ Google Scholar ]
- 9. Ajami S, Ketabi S, Isfahani SS, Heidari A. Readiness assessment of electronic health records implementation. Acta Inform Med. 2011;19:224–7. doi: 10.5455/aim.2011.19.224-227. [ DOI ] [ PMC free article ] [ PubMed ] [ Google Scholar ]
- 10. Chao CC, Jen WY, Chi YP, Lin B. Improving patient safety with RFID and mobile technology. Int J Electron Healthc. 2007;3:175–92. doi: 10.1504/IJEH.2007.013099. [ DOI ] [ PubMed ] [ Google Scholar ]
- 11. Abiona O. Thesis. Lahti University of Applied Sciences in Lahti of Finland; 2012. Adoption possibilities and use of RFID in Nigeria health sector. [ Google Scholar ]
- 12. Fuhrer P, Guinard D. Switzerland: Proceedings of the 1st European Conference on eHealth (ECEH06), Fribourg; 2006. Oct 12-13, Building a Smart Hospital using RFID technologies. [ Google Scholar ]
- 13. Vanany I, Shaharoun AB. Barriers and critical success factors towards RFID technology adoption in South-East Asian Healthcare Industry. 2008 [ Google Scholar ]
- 14. Yao W, Chu CH, Li Z. New York: IEEE Institute of Electrical and Electronics Engineers; 2010. The use of RFID in healthcare: Benefits and barriers. [ Google Scholar ]
- 15. Ahsan K, Shah H, Kingston P. RFID applications: An introductory and exploratory study. IJCSI Int J Comput Sci Issues. 2010;7:1–7. [ Google Scholar ]
- 16. Ajami S, Arab-Chadegani R. What are the most important barriers to implement Radio Frequency Identification Device (RFID) in healthcare system? J Inform Tech Soft Engg. 2013;S7:e004. [ Google Scholar ]
- 17. Ajami S, Carter MW. The advantages and disadvantages of Radio Frequency Identification (RFID) in health-care centers; Approach in Emergency Room (ER) Pak J Med Sci. 2013;29:443–8. [ Google Scholar ]
- 18. Davis NM. USA: Masters in Communication Technology and Policy in the faculty of the College of Communication of Ohio University; 2004. Application guide for radio frequency identification in electronic medical records. In partial fulfillment of the requirements for the degree. [ Google Scholar ]
- 19. Rieche M, Komensky T, Husar P. New York: IEEE Institute of Electrical and Electronics Engineers; 2011. Radio Frequency Identification (RFID) in medical environment: Gaussian Derivative Frequency Modulation (GDFM) as a novel modulation technique with minimal interference properties. [ DOI ] [ PubMed ] [ Google Scholar ]
- 20. Chen CL, Wu CY. Using RFID Yoking proof protocol to Enhance Inpatient medication safety. J Med Syst. 2012;36:2849–64. doi: 10.1007/s10916-011-9763-5. [ DOI ] [ PubMed ] [ Google Scholar ]
- 21. Yen YC, Lo NW, Wu TC. Two RFID-Based solutions for secure inpatient medication Administration. [Last accessed on 2013 Jan 24];J Med Syst. 2012 36:2769–78. doi: 10.1007/s10916-011-9753-7. Available from: http://www.springerlink.com/content/k2616133306726w5/fulltext.pdf . [ DOI ] [ PubMed ] [ Google Scholar ]
- 22. Ohashi K, Ota S, Ohno-Machado L, Tanaka H. Smart medical environment at the point of care: Auto-tracking clinical interventions at the bed side using RFID technology. Comput Biol Med. 2010;40:545–54. doi: 10.1016/j.compbiomed.2010.03.007. [ DOI ] [ PubMed ] [ Google Scholar ]
- 23. Lahtela A, Saranto K. RFID and medication care. Stud Health Technol Inform. 2009;146:747–8. [ PubMed ] [ Google Scholar ]
- 24. Ajami S, Akbari B, Yarmohammadian MH, Hejazi M. Isfahan, Iran: Isfahan University of Medical Sciences; 2012. Evaluation Usage of “Radio Frequency Identification” in Earthquake's victims tracking Information Management System through viewpoint of Relief Experts. [ Google Scholar ]
- 25. Francis DL, Prabhakar S, Sanderson SO. A quality initiative to decrease pathology Specimen — Labeling errors using radiofrequency identification in a High-Volume Endoscopy Center. Am J Gastroenterol. 2009;104:972–5. doi: 10.1038/ajg.2008.170. [ DOI ] [ PubMed ] [ Google Scholar ]
- 26. Ohashi K, Ota S, Ohno-Machado L, Tanaka H. Bethesda, Maryland: American Medical Informatics Association; 2008. Comparison of RFID systems for tracking clinical interventions at the bedside. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- 27. Sun PR, Wang BH, Wu F. A new method to guard inpatient medication safety by the implementation of RFID. J Med Syst. 2008;32:327–32. doi: 10.1007/s10916-008-9137-9. [ DOI ] [ PubMed ] [ Google Scholar ]
- 28. Chang SI, Ou CS, Ku CY, Yang M. A study of RFID application impacts on medical safety. Int J Electron Healthc. 2008;4:1–23. doi: 10.1504/IJEH.2008.018918. [ DOI ] [ PubMed ] [ Google Scholar ]
- 29. Rogers A, Jones E, Oleynikov D. Radio frequency identification (RFID) applied to surgical sponges. Surg Endosc. 2007;21:1235–7. doi: 10.1007/s00464-007-9308-7. [ DOI ] [ PubMed ] [ Google Scholar ]
- 30. Vilamovska AM, Hatziandreu E, Schindler HR, Oranje-Nassau CV, Vries H, Krapels J. Santa Monica, CA, USA: The RAND Corporation; Study on the requirements and options for RFID application in healthcare Identifying areas for Radio Frequency Identification deployment in healthcare delivery: A review of relevant literature. Directorate General Information Society and Media, European Commission. [ Google Scholar ]
- 31. Trappey CV, Trappey AJC, Liu CS. San Antonio, TX, USA: Proceedings of the 2009 IEEE International Conference on Systems, Man, and Cybernetics; 2009. Oct, Develop Patient Monitoring and Support System Using Mobile Communication and Intelligent Reasoning. [ Google Scholar ]
- 32. Ajami S, Amini F. Evaluate the ability of Clinical Decision Support Systems (CDSSs) to improve clinical practice. Med Arh. 2013;67:126–30. doi: 10.5455/medarh.2013.67.126-130. [ DOI ] [ PubMed ] [ Google Scholar ]
- 33. Ajami S, Torabian F. Mobile Technology in Healthcare. J Inform Tech Soft Engg. 2013;S7:e006. [ Google Scholar ]
- PDF (348.5 KB)
- Collections
Similar articles
Cited by other articles, links to ncbi databases.
- Download .nbib .nbib
- Format: AMA APA MLA NLM
Add to Collections
To read this content please select one of the options below:
Please note you do not have access to teaching notes, a systematic literature review of rfid in supply chain management.
Journal of Enterprise Information Management
ISSN : 1741-0398
Article publication date: 7 June 2021
Issue publication date: 8 March 2022
The findings of this paper throw light on the focal research areas within RFID in the supply chain, which serves as an effective guideline for future research in this area. This research, therefore, contributes to filling the gap by carrying out an SLR of contemporary research studies in the area of RFID applications in supply chains. To date, SLR augmented with BA has not been used to study the developments in RFID applications in supply chains.
Design/methodology/approach
We analyze 556 articles from years 2001 to date using Systematic Literature Review (SLR). Contemporary bibliometric analysis (BA) tools are utilized. First, an exploratory analysis is carried, out revealing influential authors, sources, regions, among other key aspects. Second, a co-citation work analysis is utilized to understand the conceptual structure of the literature, followed by a dynamic co-citation network to reveal the evolution of the field. This is followed by a multivariate analysis is performed on top-100 cited papers, and k -means clustering is carried out to find optimal groups and identify research themes. The influential themes are then pointed out using factor analysis.
An exploratory analysis is carried out using BA tools to provide insights into factors such as influential authors, production countries, top-cited papers and frequent keywords. Visualization of bibliographical data using co-citation network analysis and keyword co-occurrence analysis assisted in understanding the groups (communities) of research themes. We employed k -means clustering and factor analysis methods to further develop these insights. A historiographical direct citation analysis also unveils potential research directions. We observe that RFID applications in the supply chain are likely to benefit from the Internet of Things and blockchain Technology along with the other machine learning and visualization approaches.
Originality/value
Although several researchers have researched RFID literature in relation to supply chains, these reviews are often conducted in the traditional manner where the author(s) select paper based on their area of expertise, interest and experience. Limitation of such reviews includes authors’ selection bias of studies to be included and limited or no use of advanced BA tools for analysis. This study fills this research gap by conducting an SLR of RFID in supply chains to identify important research trends in this field through the use of advanced BA tools.
- Supply chain
- Bibliometric analysis
- Systematic literature review
- Network analysis
- Cocitation analysis
- Multivariate analysis
- Factor analysis
Raza, S.A. (2022), "A systematic literature review of RFID in supply chain management", Journal of Enterprise Information Management , Vol. 35 No. 2, pp. 617-649. https://doi.org/10.1108/JEIM-08-2020-0322
Emerald Publishing Limited
Copyright © 2021, Emerald Publishing Limited
Related articles
All feedback is valuable.
Please share your general feedback
Report an issue or find answers to frequently asked questions
Contact Customer Support

IMAGES
VIDEO
COMMENTS
RFID enables identification from a distance, and unlike earlier bar-code technology, it does so without requiring a line of sight. In this paper, the author introduces the principles of RFID, discusses its primary technologies and applications, and reviews the challenges organizations will face in deploying this technology. In recent years ...
The research follows a systematic literature review approach to explore the academic research on RFID and decision support systems in light of Industry 4.0. This study identifies the significance of RFID in enhancing operations and supply chain management activities. ... This paper illustrates the role of RFID in various aspects of supply chains.
RFID is a standardized technology, its inherent advantages, which are unitary identification, wireless communication, and low cost of tags, provide it with decisive practical benefits that drive new developments in terms of concepts and applications [3].Thus, RFID has become, and will continue to be more and more desirable for implementing applications at the service of our society and humanity.
A brief history of RFID technology. RFID technology was emerged as Frederick Hertz found existence of radio frequency during his experiment in 1886 (Wyld, 2005) and developed for the purpose of defense during the Second World War Footnote 4.During 1970s and 1980s, the RFID system attracted plenty of scholars and innovators, so efforts to register patents progressed (Takahashi, 2004).
The IEEE Journal of Radio Frequency Identification (RFID) publishes peer-reviewed manuscripts addressing various aspects of RFID systems. The articles describe advances in theory, algorithms, design techniques, implementations, and applications of RFID systems. Both emerging research and commercial trends in the rapidly evolving field of RFID ...
The integration of RFID and WSN enabling IoT platforms for gaining the advantage of interoperability has been discussed in [13].Further, brief applications and challenges involved in using RFID technology as a prerequisite for IoT is presented in [14].The research trend in terms of released journals, conferences, and magazines with a search keyword 'RFID' in the last two decades is ...
Radio frequency identification (RFID) is widely used in several contexts, such as logistics, supply chains, asset tracking, and health, among others, therefore drawing the attention of many researchers. This paper presents a review of the most cited topics regarding RFID focused on applications, security, and privacy. A total of 62,685 records were downloaded from the Web of Science (WoS) and ...
This paper presents a review of the most cited topics regarding RFID focused on. applications, security, and privacy. A total of 62,685 records were downloaded from the W eb of. Science (W oS) and ...
Purpose (RFID) is a technology that uses radio waves for data collection and transfer, so data is captured efficiently, automatically and in real time without human intervention. This technology, alone or in addition to other technologies has been considered as a possible solution to reduce problems that endanger public health or to improve its management. This scoping review aims to provide ...
This research aims to identify the best source of the most cited RFID papers and to provide a comprehensive road map for the future research and development in the field of RFID technology in both academic and industrial settings. Six key findings from this review are (1) the experimental method is the most popular research methodology, (2 ...
This review paper is based on Radio Frequency Identification (RFID) technology, Wireless Sensor Networks (WSNs) and wireless information & communication networks. RFID technology use for tags and readers enclosed to shop-floor industrial stuffs such as operators, terminals, vessels, stocks and Smart Home (SH) architecture that includes sensors, data communication and data integration. The ...
(RFID) is a technology that uses radio waves for data collection and transfer, so data is captured efficiently, automatically and in real time without human intervention. ... Further research is needed, especially on data management, security, and privacy, given the sensitive nature of medical information. Graphical Abstract. ... One paper was ...
1. Introduction. Radio frequency identification (RFID) is a low-cost wireless technology that makes possible the connection of billions of things, enabling consumers and businesses to engage, identify, locate, transact, and authenticate products [].The general RFID market has seen a considerable growth over the past few years in terms of the number of RFID tags sold.
RFID is one of the admired, powerful, and effectual technology in the field of communication, defense and detection in the Indoor RFID localization and tracking systems. The remoteness between RFID reader and object is measured from acknowledged signal strength indication (RSSI) values received from RFID reader. Radio Frequency Identification (RFID) and Artificial Intelligence (AI) have ...
Conclusion, Limits and Future Research Directions In this paper, the results of comprehensive review of RFID papers within the AIS basket of top journals were presented and discussed. ... RFID research: An academic literature review (1995-2005) and future research directions. International Journal of Production Economics, 2008. 112(2): p. 510 ...
Radio frequency identification (RFID) and wireless sensors networks (WSNs) are two fundamental pillars that enable the Internet of Things (IoT). RFID systems are able to identify and track devices, whilst WSNs cooperate to gather and provide information from interconnected sensors. This involves challenges, for example, in transforming RFID systems with identification capabilities into sensing ...
185 research papers were found from experts' recommendations and previous public papers. A total of 4,445 studies were chosen through the first stage. Second, we excluded 4,121 following general eligibility criteria by screening title and abstract. More specifically, we excluded RFID studies only with one of the following criteria: 1) studies
This paper presents a systematic literature review of papers that were published in academic journals on the applications of radio frequency identification (RFID) in supply chain management between the years 2000 and 2015. As the literature on RFID is not confined to specific disciplines or repositories, this paper proposes a discipline-based framework for classifying RFID literature. Five ...
RFID research has led to the emergence of a new academic research area that builds on existing research in a host of disciplines, such as electronic engineering, information systems, computer science, and business strategy, and there has been a significant increase in the number of papers on RFID in research journals. Curtin et al. ...
At least 44,000 people, and perhaps as many as 98,000 people, die in hospitals each year as a result of medical errors that could have been prevented. [1] Radio frequency identification (RFID) is a wireless technology capable of automatic and unambiguous identification without line of sight by extracting a unique identifier from microelectronic ...
We used a multi-stage process to select relevant papers and then hand-coded the papers in terms of type of study, use of RFID and benefits reported. According to Kitchenham [34], Systematic literature reviews are performed to gain a comprehensive coverage of an area by identifying, evaluating and interpreting all available relevant research.
Purpose. The findings of this paper throw light on the focal research areas within RFID in the supply chain, which serves as an effective guideline for future research in this area. This research, therefore, contributes to filling the gap by carrying out an SLR of contemporary research studies in the area of RFID applications in supply chains.
The paper was organized into four major discussion topics: product manufacturing, shipping and distribution, inventory and retail shop management, aiming to provide an overview for academicians to establish new research domains and practitioners to consider RFID-IoT adoption to solve the real-world problem.