SYSTEMATIC REVIEW article
Knowledge hiding: current research status and future research directions.

- 1 Business School, Huaqiao University, Quanzhou, China
- 2 Department of Management, Kedge Business School, Talence, France
- 3 Business School, Beijing Normal University, Beijing, China
This article provides a review of scientific articles addressing the topic of knowledge hiding in organizations. Based on a descriptive analysis, bibliometric analysis, and content analysis of a sample of 81 articles published in the academic journals in the Web of Science from 2012 to 2020, we identify the main areas and current dynamics of knowledge hiding research. Our results show that the central research themes of knowledge hiding include five clusters: concept and dimensions, antecedents, consequences, theories, and influence mechanisms. Based on our findings, we suggest future research should further develop the concept and dimensions of knowledge hiding; probe deeper into the consequences of knowledge hiding; explore multilateral, cross-level, and collective knowledge hiding; employ innovative theoretical perspectives and research methods to study knowledge hiding; and address how cultural and other contextual factors may shape the knowledge hiding behavior.

Introduction
Knowledge management plays a crucial role in each organization, which can affect the firms' and employees' performance. However, due to the practice of “knowledge hiding,” it is often challenging to achieve satisfactory results in knowledge management ( Connelly and Kelloway, 2003 ). Previous research has pointed out that employees are not willing to share knowledge, due to reasons such as protection and control of knowledge ownership, expertise dominance, and defensive awareness ( Huo et al., 2016 ). About 50% of employees have the intention to withhold, mislead, or conceal knowledge that has been requested by another person ( Peng, 2013 ). This behavior of deliberately not providing the required knowledge to colleagues when requested is called “knowledge hiding” ( Connelly et al., 2012 ), which has become an independent concept that is different from the opposite side of knowledge sharing ( Zhao et al., 2019 ).
Obviously, knowledge hiding is very likely to reduce the efficiency of knowledge exchange among members, hinder the generation of new ideas/thoughts, or even destroy trust ( Connelly et al., 2012 ), increasing the risk of knowledge loss and inhibiting the creativity of individuals and teams ( Cerne et al., 2014 ; Bogilović et al., 2017 ). Along this vein, it makes sense to solve the dilemma of insufficient knowledge sharing through the elimination of knowledge hiding, facilitating knowledge conversion within organizations. As a result, based on a descriptive analysis, bibliometric analysis, and content analysis, we conduct an in-depth analysis of knowledge hiding publications in international Science Citation Index (SCI) and Social Science Citation Index (SSCI) journals. We aim to address these research questions:
1. What is the current publication trend in knowledge hiding?
2. Which themes involving knowledge hiding have been studied by scholars?
3. What are the areas involving knowledge hiding that seem to require future research?
Previous authors have conducted reviews on knowledge hiding (e.g., Xiao and Cooke, 2019 ; Anand et al., 2020 ; de Garcia et al., 2020 ), which are valuable. However, the review of Xiao and Cooke (2019) is based on 52 articles and all of which are written in English or Chinese, and published over the period 1997–2017. Similarly, the review of Anand et al. (2020) is drawing on 52 studies. In their work, de Garcia et al. (2020) have reviewed a total of 57 articles that are published up to April 2018, and their study focuses on distinguishing knowledge hiding and knowledge hoarding from knowledge collection and donation perspectives. Our review differs from these previous works in terms of volume, timeframe, method and the analysis. First, we have combined bibliometric analysis, content analysis and descriptive analysis in this review, which allows for incorporating rich data with less interpretative or subjectivity biases. In contrast to previous reviews, we further overview the concepts and dimensions, antecedents, consequences, theoretical foundations, and influence mechanisms of knowledge hiding. In the meantime, we have included bigger volume of articles in this review. In so doing, we are able to complement the previous reviews, offering a more objective account of evolution of this research topic.
Methodology
Our study has followed the systematic review process ( Pickering and Byrne, 2014 ). Within this process, we employ the principles of Tranfield et al. (2003) , which include (1) setting the scope, (2) conducting the search and data extraction, (3) selecting the studies and analyzing the data, and (4) extracting data and reporting the findings. To ensure the data validity and reliability, we limited our databases by searching the sample of English-written articles from the Web of Science over the period between 1995 and 2020. Further, the main reason for using SCI and SSCI databases is that web of science is “generally considered credible among the scientific community, and [are] commonly used by researchers from a wide range of fields ( de Garcia et al., 2020 , p. 4). Several reviews have used these databases (e.g., Bernatović et al., 2021 ; Vlačić et al., 2021 ).
Retrieval conditions were “Title = knowledge hiding” or “Title = knowledge withholding,” and the time span was “All years (1950–2020).” The database was “Web of Science Core Collection” and the search basis was “Web of Science Category = Unrestricted Category.” In total, we obtained a sample of 233 articles. Subsequent analysis of these 233 articles' abstracts was conducted. In order to ensure data accuracy, we carefully selected studies that fit the definition given by Connelly et al. (2012) and excluded those that belonged to disciplines such as information management. This yielded 81 articles related to knowledge hiding. For these 81 articles, we undertook the reading of full texts, using Excel to record the key findings, theoretical lens, and methodologies. Building upon the content extraction, the authors classified the core clusters in five main themes according to their characteristics: concept and dimensions, antecedents, consequences, theoretical frameworks, and influence mechanism. Figure 1 shows the flow diagram of analysis.
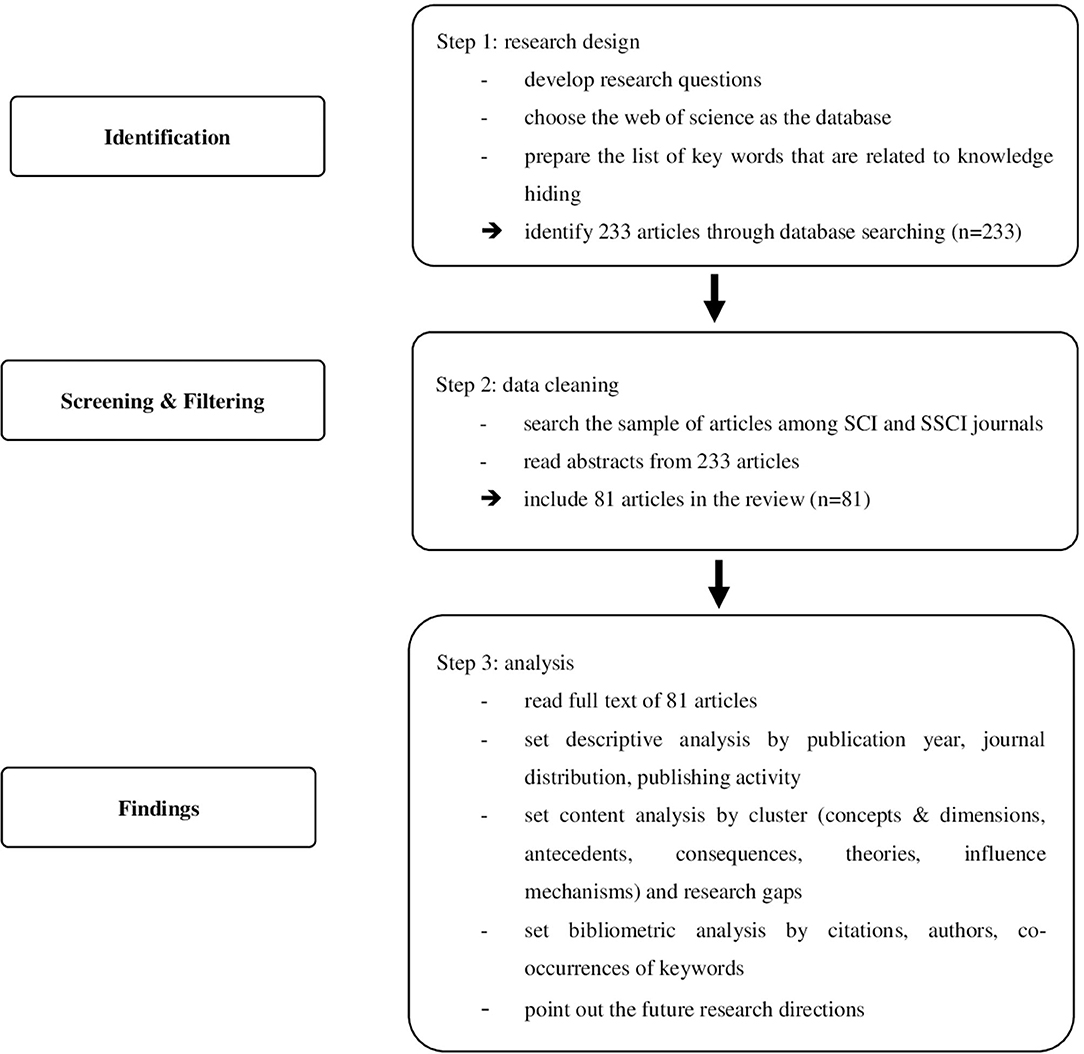
Figure 1 . Flow diagram.
Analysis and Findings
Publication by year.
The analysis of the number of publications per year on knowledge hiding in international journals (see Figure 2 ) shows that scholars started to systematically study knowledge hiding as an organizational behavior in the 2010s. A growing number of studies have addressed knowledge hiding but it dates back only to 2012, when knowledge hiding was first proposed as an independent concept in the work of Connelly et al. (2012) . Knowledge hiding research has gone through two periods: the initial stage (from 2012 to 2018) and the fast development stage (from 2019 to 2020). During the initial stage, publications on knowledge hiding in mainstream international journals were rare, and there were only between one and five articles published per year. Since 2019, there has been a sharp increase in knowledge hiding publications; the number of publications has jumped to more than 30 articles per year (see Figure 2 ).
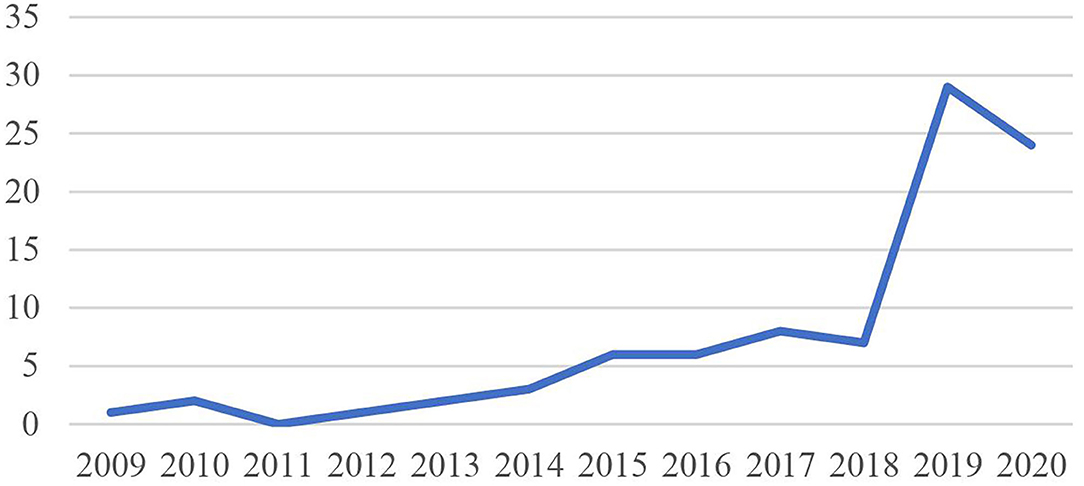
Figure 2 . Annual distribution of articles on knowledge hiding.
Journal Distribution of Knowledge Hiding Research
From 2012 to 2020, research on knowledge hiding has been published in 43 SCI/SSCI journals (see Table 1 ), with 40 articles (49.38%) published in Journal Citation Reports (JCR) Q1 journals, 19 articles (23.46%) published in JCR Q2 journals, 8 articles (9.88%) published in JCR Q3 journals, and 11 articles (13.58%) published in JCR Q4 journals; 15 articles (18.52%) published in the Chartered Association of Business Schools (ABS3) journals, 10 articles (12.35%) published in ABS4 journals, one article (1.23%) published in Financial Times (FT50) journals; and one article (1.23%) published each in UT Dallas top 100 business school research rankings (UTD24) and ABS4 * journals. The top 10 journals that published most of the knowledge hiding articles are Journal of Knowledge Management, Journal of Organizational Behavior, Management Decision, International Journal of Hospitality Management, European Journal of Work and Organizational Psychology, Knowledge Management Research and Practice, International Journal of Information Management, Asian Business and Management, Leadership and Organization Development Journal , and Journal of Managerial Psychology . The majority of knowledge hiding research has been published in JCR Q1/Q2 journals, and a considerable proportion has been published in ABS3/4 journals.
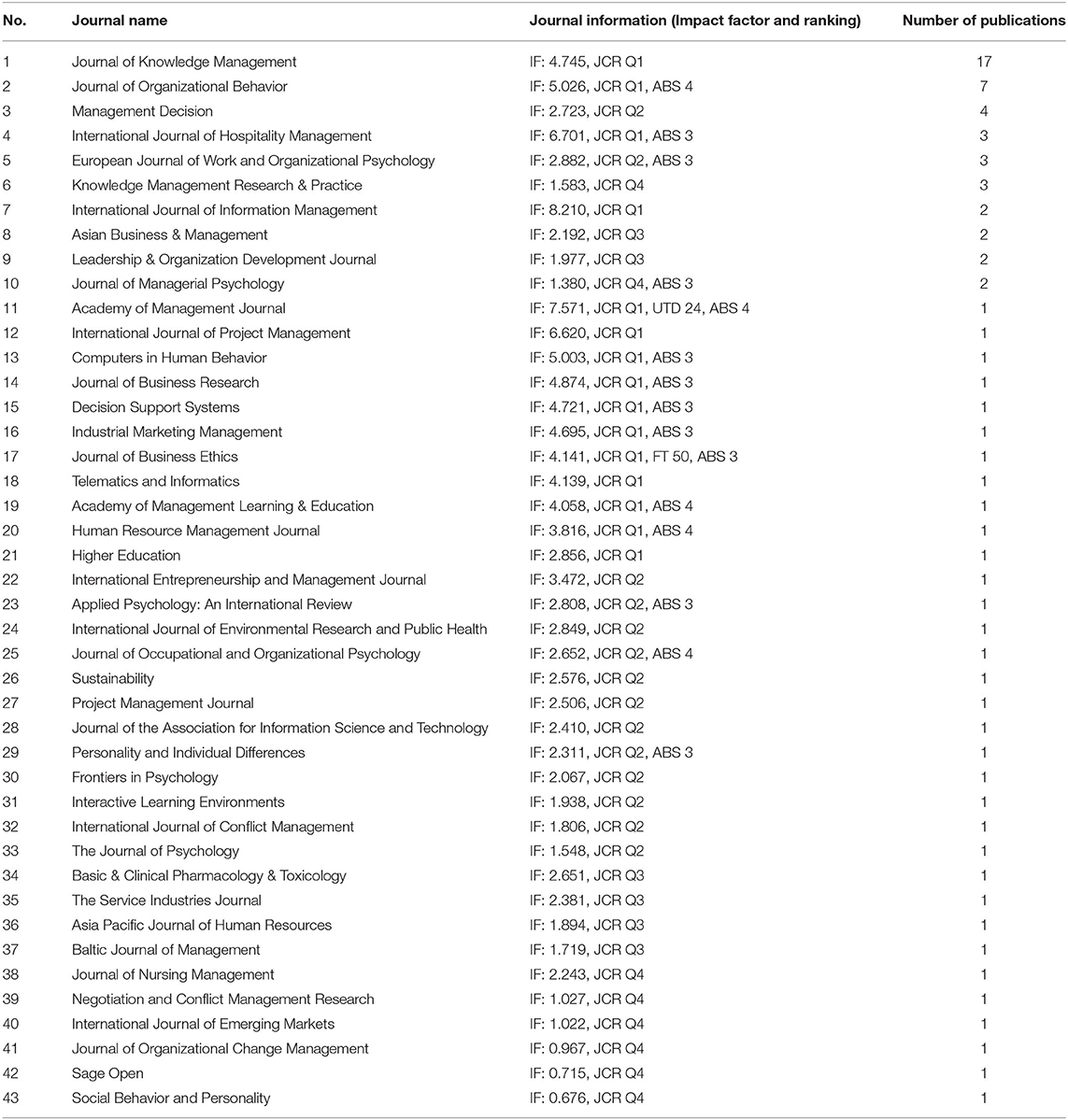
Table 1 . Top publishing journals on knowledge hiding.
Publishing Activity by Authors, Authors' Institutions, and Locations
Knowledge hiding has attracted considerable attention from researchers and practitioners. As shown in Table 2 , Matej Cerne published the most articles (eight) on knowledge hiding followed by Škerlavaj and Connelly, with seven and six articles respectively. The most active institutions in the research field of knowledge hiding were University of Ljubljana (eight publications), followed by BI Norwegian Business School, McMaster University and Tongji University, each with seven publications. Table 3 lists the locations of authors' institutions, with the top four being China, Pakistan, Canada and United Arab Emirates.
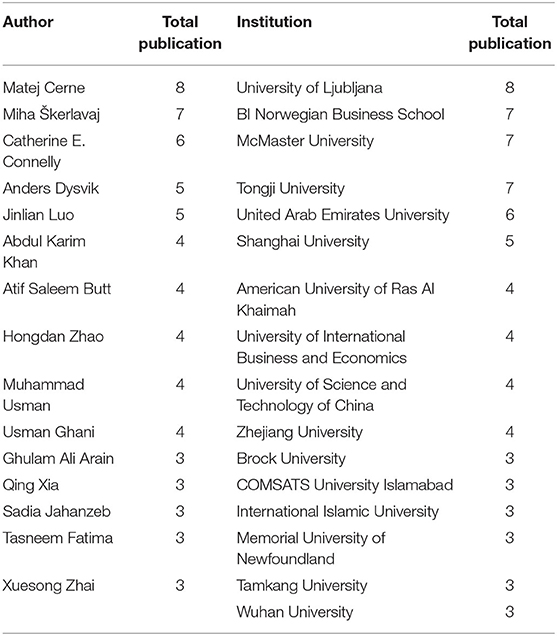
Table 2 . Top publishing authors and institutions on knowledge hiding.

Table 3 . Publishing activity by authors' institution location.
Publishing Activity by Data Sources
Our analysis shows that previous data on knowledge hiding have tended to be collected in one single location, such as China, Pakistan, United Arab Emirates, Saudi Arabia, United States, and so on (see Table 4 ). Eight publications used data that were collected from multi-countries and regions (e.g., North America, Germany and Austria, Europe, Slovenia, Croatia, Serbia, Bosnia and Herzegovina, Montenegro and Macedonia). The top three locations from which researchers have collected knowledge hiding data were China (29 publications), Pakistan (13 publications) and United Arab Emirates (5 publications).

Table 4 . Locations from which researchers have collected knowledge hiding data.
Highly Cited Publications
Citations can show the research focus of scholars and reveal their main theoretical lens. Highly cited articles are often regarded as important references in the field. Table 5 presents the top 15 highly cited publications on knowledge hiding.
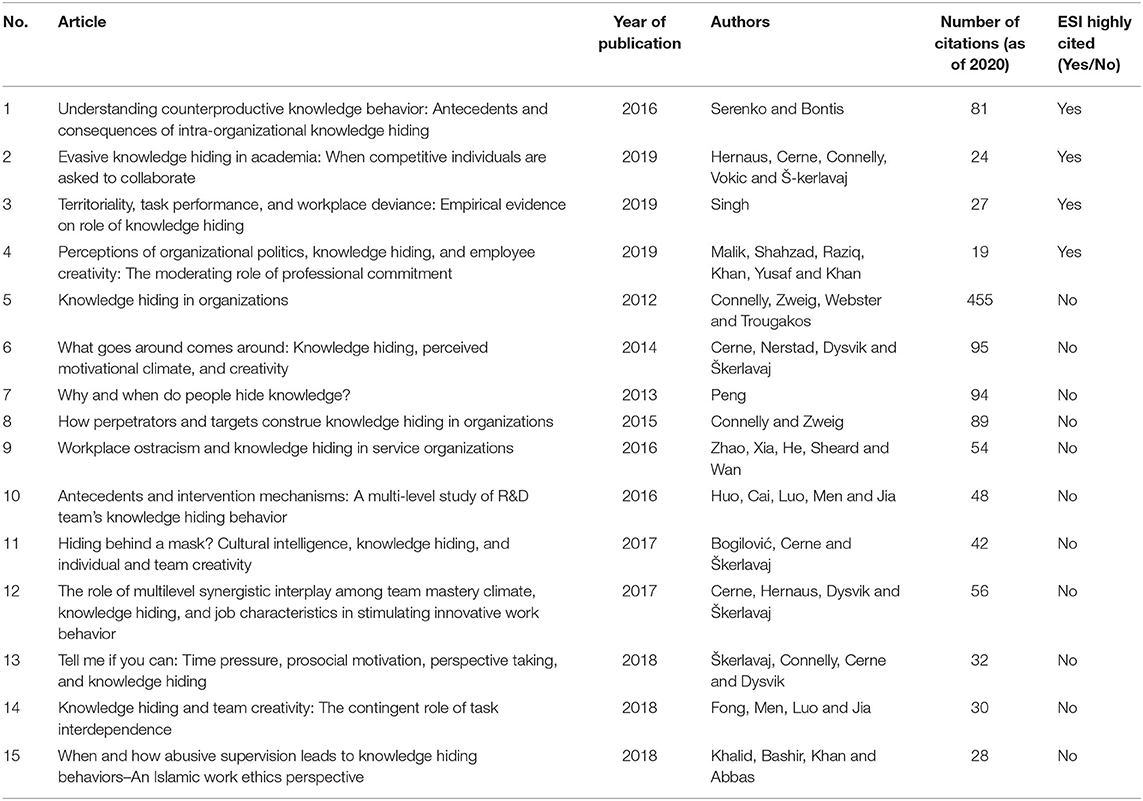
Table 5 . Top 15 articles on knowledge hiding by the number of citations.
Further, through a co-citation analysis, co-authorship analysis, keyword and co-occurrence analysis, and content analysis, we find that most research on knowledge hiding focuses on the concept and dimensions of the topic. For instance, as one of the highly cited publications, it is important to acknowledge that Connelly et al. (2012) take the lead in defining the concept of knowledge hiding and propose evasive hiding, playing dumb, and rationalized hiding as three dimensions of knowledge hiding. Based on the work of Connelly et al. (2012) ; Zhao et al. (2016) further examine the interpersonal antecedents of the three dimensions of knowledge hiding. Hernaus et al. (2019) distinguish the three dimensions of knowledge hiding and address how individual competitiveness may lead to knowledge hiding. Connelly and Zweig (2015) point out that the three dimensions of knowledge hiding are not equally and always harmful, where under certain circumstances, some knowledge hiding can be beneficial. Among the highly cited publications, scholars also focus on the antecedents of knowledge hiding, paying particular attention to workplace stressors, psychological ownership, and territoriality of knowledge. For example, Zhao et al. (2016) ; Škerlavaj et al. (2018) , and Khalid et al. (2018) have examined the influence mechanisms of workplace stressors, such as workplace ostracism, abusive supervision, and interpersonal injustice, on knowledge hiding. Peng (2013) ; Huo et al. (2016) , and Singh (2019) emphasize the predictive effect of psychological ownership and territoriality of knowledge on knowledge hiding. Serenko and Bontis (2016) ; Hernaus et al. (2019) , and Malik et al. (2019) also investigate the antecedents of knowledge hiding with different focuses (e.g., intra-organizational knowledge hiding, the individual-level and job-related factors within academia, organizational politics). These studies represent the two most important research directions of knowledge hiding.
Following, among the highly cited publications, we find that individual and team creativity, interpersonal relationships, and retaliation show the key consequences of knowledge hiding. The main contributions in the field include the work of Cerne et al. (2014) , who point out that “when employees hide knowledge, they trigger a reciprocal distrust loop in which coworkers are unwilling to share knowledge with them” (p. 172). In recent years, Connelly and Zweig (2015) , and Serenko and Bontis (2016) also prove that knowledge hiding can lead to retaliation. Cerne et al. (2017) and Malik et al. (2019) examine the destructive effect of knowledge hiding on individual creativity. Bogilović et al. (2017 ) and Fong et al. (2018) analyze the impacts of individual-level knowledge hiding on team-level creativity. These studies represent the mainstream consequences of knowledge hiding.
Additionally, we identify that the research focus on knowledge hiding has moved from the individual level to a multilevel influence mechanism. For example, Huo et al. (2016) ; Cerne et al. (2017) ; Fong et al. (2018) , and Hernaus et al. (2019) explore the moderating effect of team-level task interdependence on the relationship between individual-level variables and knowledge hiding. In addition, team-level cultural factors (e.g., mastery climate, workplace ethics) and organizational justice are variables that scholars have examined when exploring the multilevel influence mechanism of knowledge hiding ( Huo et al., 2016 ; Cerne et al., 2017 ; Khalid et al., 2018 ).
Major Research Clusters and Topics
Using CiteSpace4.0 software, we conducted the descriptive analysis, bibliometric analysis, and content analysis of the 81 knowledge hiding articles that are published in the international journals from 2012 to 2020. In order to clearly demonstrate the current status of knowledge hiding research, we structure our findings into the following five clusters (see Figure 3 ).
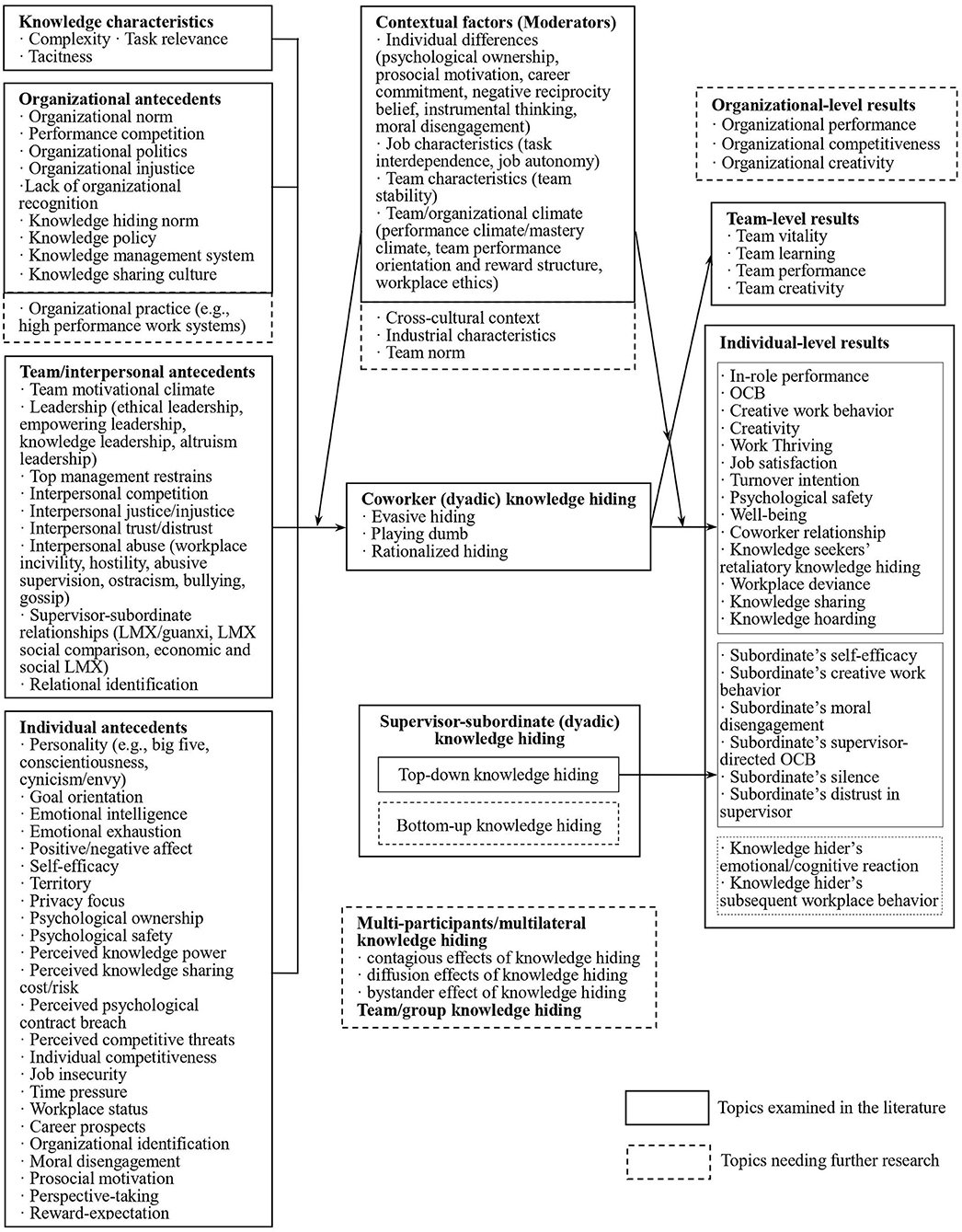
Figure 3 . Research framework of knowledge hiding. Source: extended and developed from Connelly et al. (2012) and Xiao and Cooke (2019) .
Concept and Dimensions
The bibliometric analysis suggests that keywords related to the concept of knowledge hiding include knowledge sharing, knowledge withholding, and knowledge management process. Based on these keywords and the results of our content analysis, we extract “concept and dimensions” as the first cluster that reflects the research interests in knowledge hiding.
The concept of knowledge hiding was first defined as the act of deliberately not providing knowledge or providing knowledge that is not what the seeker needs when facing a colleague's request ( Connelly et al., 2012 ). These were the first authors to discuss the linkages and differences between knowledge hiding and related concepts, such as knowledge sharing/non-sharing ( Anand et al., 2020 ), knowledge withholding ( Webster et al., 2008 ), knowledge hoarding ( Xiao and Cooke, 2019 ; de Garcia et al., 2020 ), counterproductive/deviant behavior ( Connelly and Zweig, 2015 ; Serenko and Bontis, 2016 ), workplace deception ( Connelly et al., 2012 ), and incivility ( Zhao et al., 2016 ). Later, scholars further proposed concepts such as knowledge sharing hostility ( Stenius et al., 2016 ), disengagement from knowledge sharing ( Zhao et al., 2016 ), knowledge contribution loafing ( Fang, 2017 ), and knowledge manipulation ( Bogilović et al., 2017 ). In recent years, scholars have tried to differentiate knowledge hiding from other related concepts (e.g., employee silence and knowledge protection) ( Bari et al., 2020 ).
In order to distinguish these different concepts, we compare relevant concepts through questioning whether knowledge seeking exists, the degree of knowledge sharing, and the intentionality of the behavior (see Figure 4 ). In general, scholars have widely accepted the definition of knowledge hiding given by Connelly et al. (2012) . The mainstream view believes that knowledge hiding is an important aspect of knowledge withholding, and it is not the opposite of knowledge sharing ( Connelly et al., 2012 ; Serenko and Bontis, 2016 ; Zhao et al., 2016 ). Consequently, one cannot simply equate knowledge hiding with non-sharing or a lack of knowledge sharing. In addition to subjective intention, the reasons that individuals do not share knowledge with others can be related to a lack of relevant knowledge or the inability to share the knowledge. It is worth pointing out that there are different opinions in boundaries between knowledge hiding and concepts such as knowledge non-sharing, counterproductive knowledge behavior, and knowledge protection. Hence, there still exists some confusion and cross-use of related concepts in the knowledge hiding research. In addition, the existing literature has seldom defined knowledge hiding from the indigenous/cross-cultural perspective.
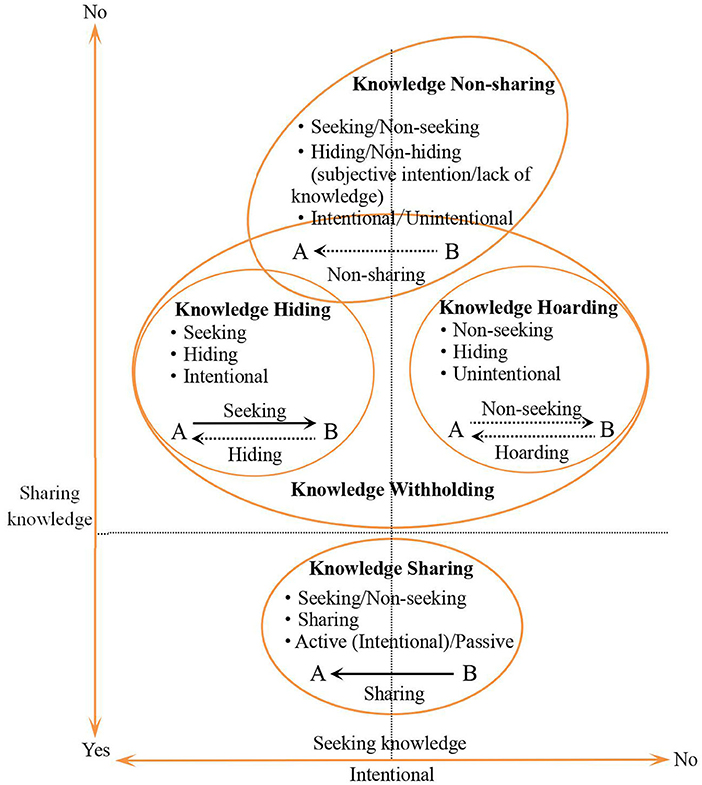
Figure 4 . Comparison between knowledge hiding and related concepts. Source: extended and developed from Connelly et al. (2012) and de Garcia et al. (2020) .
Connelly et al. (2012) have developed three dimensions of knowledge hiding and an employee self-evaluation scale with 12 items, with each dimension measuring four items. Among them, evasive hiding means that the hider provides invalid knowledge or pretends to agree to help, but lacks follow-up action. An example item is “I agreed to help him/her but never really intended to.” Playing dumb refers to pretending to be ignorant of the relevant knowledge or not understanding the knowledge seeker's question, with a sample item “I pretended I did not know what he/she was talking about.” Rationalized hiding means that the hider explains the reasons for not providing required knowledge, such as the necessity to keep it confidential or offering that knowledge sharing is not allowed by the superiors. An example item is “I explained that the information is confidential and available only to people on a particular project.” Most scholars believe that rationalized hiding is different in nature from evasive hiding and playing dumb, because rationalized hiding does not involve deception, but the evasive hiding and playing dumb do have a high degree of deception.
The scale of Connelly et al. (2012) has been proved to have high reliability and validity in a series of empirical studies. In general, scholars use this scale and its original items directly, making some contextual adaptation of expressions only according to the particular research needs. There are other knowledge hiding scales, such as Peng's ( Peng, 2013 ) three-item counterproductive knowledge behavior scale and knowledge withholding behavior scales developed by Lin and Huang (2010) ; Tsay et al. (2014) , and Serenko and Bontis (2016) . Anand et al. (2020) have advocated that knowledge hiding is composed of unintentional hiding (driven by contingent situation), motivational hiding (driven by performance and competition), controlled hiding (driven by psychological ownership), victimized hiding (driven by hostility and abuse), and favored hiding (driven by identity and norms). Jha and Varkkey (2018) identify the four strategies adopted by supervisors to hide knowledge from subordinates, namely, playing innocent, misleading, rationalized hiding, and counter-questioning.
Antecedents
The antecedents of knowledge hiding include the Big Five personality traits, abusive supervision, negative workplace gossip, and career insecurity. Combined with the research framework of knowledge hiding (see Figure 3 ), the second cluster as antecedents is popular among scholars. Inspired by the work of Connelly et al. (2012) and Xiao and Cooke (2019) , we review knowledge hiding antecedents from four aspects: knowledge characteristics, individual factors, team and interpersonal factors, and organizational factors.
Knowledge characteristic is one of the first antecedents popular among scholars. Due to the complex nature of knowledge, Connelly et al. (2012) point out that such complexity affects the willingness of individuals to provide help when facing colleagues' knowledge requests. Simply, it often requires more time and energy to generate complex knowledge that knowledge owners tend to keep the knowledge for themselves. Hernaus et al. (2019) argue that people are more likely to hide tacit knowledge rather than explicit knowledge. In addition, the task relevance and the value of knowledge have a positive relation with knowledge hiding ( Connelly et al., 2012 ; Huo et al., 2016 ).
Individual factors mainly include personality traits and psychological factors such as emotion and cognition. In terms of personality traits, scholars focus mainly on the influence of the Big Five personality traits, in particular neuroticism. For example, Pan and Zhang (2018) reveal that employees with high conscientiousness and low neuroticism are less likely to hide knowledge, while people with high neuroticism are more likely to hide knowledge ( Anaza and Nowlin, 2017 ). Pan et al. (2018) verify the effects of a “dark triad of personality” (Machiavellianism, narcissism, and psychopathy) on different dimensions of knowledge hiding. Fang (2017) and Aljawarneh and Atan (2018) examine the relationship between anxiety and knowledge hiding and the relationship between cynicism and knowledge hiding.
When it comes to the cognitive perception, prior research has focused mainly on the individual's self-efficacy, territoriality and psychological ownership, psychological safety, psychological contract breach, perceived pressure or job insecurity, perceived workplace status, and career prospects. Tsay et al. (2014) ; Jha and Varkkey (2018) , and Hernaus et al. (2019) argue that individuals' confidence in their knowledge and perception of their competitiveness affect their willingness to share knowledge. Peng (2013) ; Huo et al. (2016) ; Kang (2016) ; Singh (2019) ; Khalid et al. (2020) , and Zhai et al. (2020) believe individuals' perceived exclusivity of knowledge, knowledge power, and knowledge privacy are the primary factors that determine how much knowledge they are willing to share with colleagues. He et al. (2020) ; Lin et al. (2020) , and Wu (2020) explore the formation mechanism of knowledge hiding from the perspectives of psychological safety and perceived threats. Pradhan et al. (2019) ; Ghani et al. (2020a) , and Jahanzeb et al. (2020a) emphasize the negative impacts of employee psychological contract breaches on knowledge sharing in the organizations. Jha and Varkkey (2018) ; Škerlavaj et al. (2018) , and Feng and Wang (2019) examine the impacts of workplace stressors, such as time pressure and job insecurity, on knowledge hiding.
Prior studies have also investigated knowledge hiding from employee and supervisor perspectives. In their work, Butt (2019) and Butt and Ahmad (2019) show that concerns about career prospects are important individual-level reasons for supervisors to hide knowledge from subordinates. Liu et al. (2020) find that perceived workplace status affects knowledge hiding through two opposing mechanisms: perception of knowledge sharing obligation and perception of being envied. The goal orientation has also attracted some scholars' attention in recent years when studying knowledge hiding behavior. Research by Zhu et al. (2019) shows that performance-driven goal orientation has a positive relationship with employees' knowledge hiding behaviors, which allows employees to achieve the competitive goal of surpassing colleagues. Nadeem et al. (2021) argue that shared goals are negatively related to knowledge hiding. Moh'd et al. (2021) analyze the relationship between achievement goal orientation (e.g., learning goals, performance display/performance-avoidance goal orientation) and knowledge hiding. Some scholars highlight that individual motivational factors (such as expected results/rewards and perceived knowledge sharing costs) affect knowledge hiding ( Lin and Huang, 2010 ; Shen et al., 2019 ). Although emotion and cognition have been regarded as the two core elements that drive individual behavior (e.g., Lee and Allen, 2002 ), studies on how emotional/affective factors influence knowledge hiding are still underdeveloped. We believe only Zhao and Xia (2019) have studied the negative emotional state of nursing staff as the antecedent of their knowledge hiding behavior.
Team-level and interpersonal factors reflect leadership, interpersonal relationships, and their respective interactions. When considering leadership, scholars pay the most attention to abusive leadership, followed by ethical leadership. Khalid et al. (2018) point out that knowledge hiding is not necessarily an employee's intention to directly harm other organization members, but a negative reaction of employees to abusive supervision. Further, as indicated by displaced aggression theory, when employees encounter abusive leaders, they are more likely to retaliate by targeting innocent victims, namely, their colleagues but not the leaders. Based on the reactance theory, Feng and Wang (2019) point out that when employees experience frustration resulting from the abuse of their supervisors, they will take revenge in a direct or indirect way so that they can maintain a sense of freedom. However, because of their supervisors' supreme power and status in organizations, employees usually do not directly retaliate against supervisors so as not to cause stronger hostility and reciprocal retaliation. Ethical leadership can also influence employees' behavior intentionally or unintentionally through the role model effect. Abdullah et al. (2019) ; Anser et al. (2020) , and Men et al. (2020) argue a significant but negative correlation between ethical leadership and subordinates' knowledge hiding behavior. Interestingly, the study by Xia et al. (2019) describes an inverted U–shaped curve relationship between knowledge leadership and employee knowledge hiding. Through a multilevel model, Lin et al. (2020) find that individual-focused empowering leadership can improve the supervisor-subordinate relationship and therefore inhibit knowledge hiding, whereas differentiated empowering leadership can cause group relational conflict and then lead to knowledge hiding. Based on social exchange theories, Abdillah et al. (2020) argue that altruistic leaders' humility, patience, understanding, sympathy, and compassion will be perceived by employees as uniquely socio-emotional resources, which can enhance the positive emotion of employees, improve the quality of the exchange between supervisors and subordinates (obtaining the trust and respect of the subordinates), and encourage employees be willing to make extra efforts for the organization and eliminate selfish behaviors that harm the interests of the organization, thus effectively preventing employee knowledge hiding behaviors.
From the perspective of interpersonal abuse, prior research shows that employees who encounter interpersonal unfair treatment are less willing to share their personal knowledge assets with others ( Abubakar et al., 2019 ), whereas fair interpersonal interaction is significantly negatively correlated with the three dimensions of knowledge hiding ( Ghani et al., 2020b ). Among these, the factor of passive-aggressiveness in the workplace attracts more attention from scholars. Aljawarneh and Atan (2018) find that incivility in the workplace can drive employees to feel cynical and thus hide knowledge as a countermeasure. Zhao et al. (2016) and Riaz et al. (2019) point out that, as a typical workplace passive-aggressiveness, workplace ostracism would significantly increase employees' deceptive knowledge hiding (e.g., evasive hiding and playing dumb). Similarly, research by Yao et al. (2020a , b ) shows that negative interpersonal experiences, such as workplace bullying and negative workplace gossip, accelerate the exhaustion of employee resources, such as emotions, time, energy, and organizational identity, leading them to hide knowledge. Anand et al. (2020) also find that hostility and abusive colleagues/supervisors drive employees to hide knowledge.
Concerning the impacts of interpersonal relationship on knowledge hiding, current research has focused on exploring the effects of supervisor-subordinate relationships. Scholars first divide supervisor-subordinate relationships into formal work-related relationships (contractual relationship, Leader-Member Exchange) and informal non-work-related relationships (Chinese personal guanxi relationships, Supervisor-Subordinate Guanxi) ( He et al., 2020 ), or into economic LMX and social LMX ( Babič et al., 2019 ), and then explore their impacts on employees' knowledge hiding behaviors. Previous research reveals that LMX negatively affects evasive hiding and playing dumb ( Zhao et al., 2019 ). However, this reciprocal social exchange is more likely to reduce the level of knowledge hiding within the team, especially when the relationship between individuals and their supervisors has social LMX characteristics ( Cerne et al., 2014 ). Furthermore, upward LMX social comparison leads to envy among team members, so it is a potential interpersonal antecedent of knowledge hiding among colleagues ( Weng et al., 2020 ). It is worth noting that team prosocial motivation and social LMX (but not economic LMX) have an interaction effect on knowledge hiding ( Babič et al., 2019 ). Lin and Huang (2010) ; Butt (2019) ; Butt and Ahmad (2019) ; Semerci (2019) examine the influences of interpersonal factors such as trust, reciprocity, relationship recognition, lack of interpersonal relationship, relationship conflict, and interpersonal competition. Interestingly, Lin and Huang (2010) point out that emotional bonds such as trust and reciprocity among team members can make individuals give up hiding too much knowledge to avoid retaliation from others. In addition, task conflicts and relationship conflicts have additive effects on knowledge hiding ( Semerci, 2019 ).
At the organizational level, scholars have explored the roles of organizational culture, knowledge management policies and systems, organizational politics, organizational justice, organizational recognition, and a competitive performance environment on employees' conduct of knowledge hiding. First, the knowledge sharing culture has been proved to be closely related to the extent to which the knowledge hiding behavior can be accepted and adopted by the members of the organization ( Connelly et al., 2012 ). For example, Anaza and Nowlin (2017) point out that the lack of incentives for knowledge sharing and the lack of supervisor feedback on subordinates' knowledge sharing will lead employees to hide knowledge. Jha and Varkkey (2018) highlight that a lack of organizational recognition of knowledge sharing and workload increase due to knowledge sharing increase employee knowledge hiding.
Social norms, organization policies, and management systems have also been found to have a profound impact on employees' tendency to hide knowledge. For instance, Butt and Ahmad (2019) argue that knowledge hiding is deeply embedded in many local companies and is regarded as a common code of conduct in the United Arab Emirates. Serenko and Bontis (2016) find that organizational knowledge management systems and policies have a significant direct impact on employee knowledge hiding, whereas injustice prompts employees to spontaneously engage in knowledge hiding behavior. Malik et al. (2019) propose that perceived organizational politics positively predict knowledge hiding. Abubakar et al. (2019) find that distributional, procedural, and interactional injustice increase the level of knowledge hiding among employees. Research by Jahanzeb et al. (2020b) confirms that employees who encounter organizational unfairness consider knowledge hiding as a means to rationalize the cognitive separation between oneself and the organization in order to maintain one's dignity. Finally, some scholars have examined the impact of a competitive working environment. For example, Anaza and Nowlin (2017) explain how internal competition can lead to knowledge hiding. Similar findings can be found in the work of Anand et al. (2020) , who argue that organizational internal performance and competitive factors drive employees to hide knowledge.
Consequences
Based on the highly cited publications and the keyword analysis, we find that consequences, performance, behavior , and employee/team creativity are some keywords that reflect the outcome of knowledge hiding. Therefore, we use the term consequences to summarize the third cluster concerning the knowledge hiding research.
Current research focuses mainly on the individual- and team-level consequences of knowledge hiding. A small number of studies examine the individual-level consequences of knowledge hiding between supervisors and subordinates. In terms of individual-level results, the existing research has examined the effects of knowledge hiding on individual job performance, psychological status and attitude, workplace behavior, and supervisor-subordinate/coworker relationships. For instance, most studies have found that knowledge hiding among colleagues and between supervisors and subordinates can reduce task performance, organizational citizenship behavior (OCB), and creativity ( Connelly et al., 2012 ; Cerne et al., 2014 ; Arain et al., 2019 , 2020a , b ; Jahanzeb et al., 2019 ; Malik et al., 2019 ; Singh, 2019 ; Zhu et al., 2019 ).
However, there are some mixing findings. For example, Wang et al. (2019) argue that perceived colleague knowledge hiding does not reduce the performance of salespersons. Instead, it encourages them to work harder to improve their sales performance. Burmeister et al. (2019) find that knowledge hiding (playing dumb, in contrast to evasive hiding and rationalized hiding) has opposite effects on OCB, and knowledge hiders experience different emotions. Khoreva and Wechtler (2020) point out that evasive hiding is negatively related to in-role performance, and playing dumb is positively related to it. In addition, both evasive hiding and rationalized hiding will hinder innovation performance. Regarding psychological status and attitudes, research suggests that knowledge hiding increases employees' moral disengagement ( Arain et al., 2020a ) and decreases their psychological safety, well-being, job satisfaction, and sense of thriving ( Jiang et al., 2019 ; Offergelt et al., 2019 ; Khoreva and Wechtler, 2020 ). Furthermore, knowledge hiding can trigger knowledge seekers' deviant behaviors, turnover intention, upward silence, and non-engagement in knowledge sharing ( Connelly and Zweig, 2015 ; Offergelt et al., 2019 ; Singh, 2019 ; Arain et al., 2020a ).
Concerning interpersonal relationships, studies reveal that knowledge hiding among colleagues or between supervisors and subordinates can damage workplace relationships, which can even lead to a trust crisis ( Connelly et al., 2012 ; Cerne et al., 2014 ; Arain et al., 2020b ). In particular, Connelly et al. (2012) , Cerne et al. (2014) , and Connelly and Zweig (2015) highlight that knowledge hiding can result in a vicious circle of rejecting knowledge sharing. Studies also find that knowledge hiding has significant negative effects on team performance ( Zhang and Min, 2019 ), team creativity ( Fong et al., 2018 ; Bari et al., 2019 ), team viability ( Wang et al., 2019 ), team learning, and absorptive capability ( Fong et al., 2018 ; Zhang and Min, 2019 ).
In summary, scholars have made advancements on the impacts of knowledge hiding on the individual level, but research on its impacts on team and organizational levels is still at a nascent stage. Few scholars have recently analyzed the “boomerang effect” or “negative reinforcement cycle” of knowledge hiding—the impact of knowledge hiding on the hiders' psychological status, job performance, and creativity (e.g., Cerne et al., 2014 ; Jiang et al., 2019 )—and its double-edged sword effect ( Wang et al., 2019 ), which has opened up a new avenue for research.
Theoretical Perspectives
The fourth cluster concentrates on theories that are popular among scholars that they use to conduct knowledge hiding research. The theories applied in the field of knowledge hiding are mainly from two domains—managerial theory and psychological theory—and include theories such as “exchange” (represented by social exchange theory), “resources” [represented by Conservation of Resources (COR) Theory], “learning” (represented by social learning theory), “cognition” (represented by social cognitive theory), “ownership” (represented by psychological ownership theory), “goal orientation” (represented by achievement goal theory), “personality traits,” “job characteristics,” social identity theory, displaced aggression theory, and justice theory (see Table 6 ). Although scholars have introduced other theories to study knowledge hiding, the effectiveness of this theoretical development needs to be enhanced. For example, how to theorize individual emotions has not yet been made systematic and thus needs to be further explored in future research. Furthermore, we find that theories that are mostly used to examine the motivation/antecedents of knowledge hiding or the direct/indirect (mediating) influence of antecedent variables on knowledge hiding are less used to illustrate the consequences of knowledge hiding and the boundary conditions.
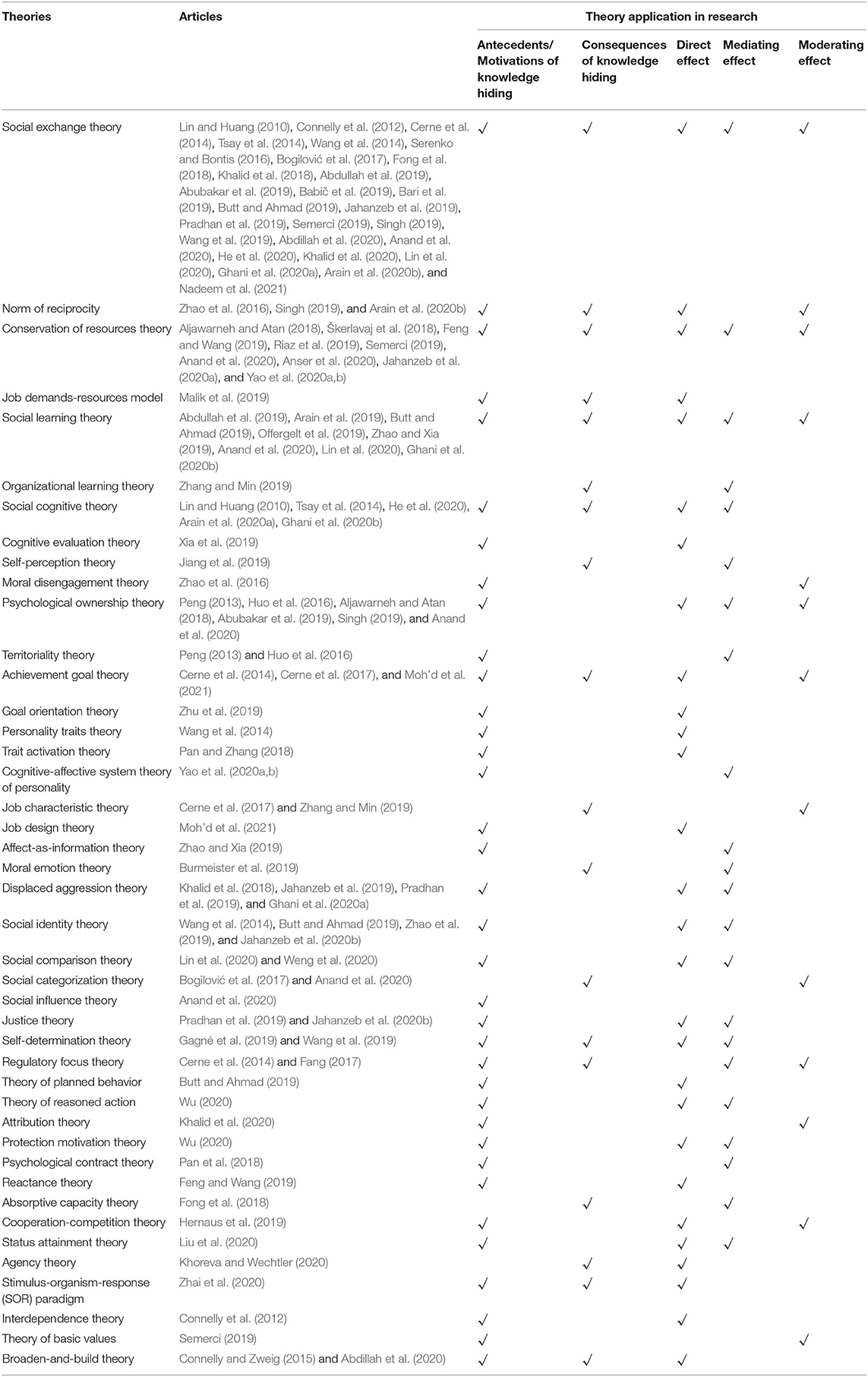
Table 6 . Theoretical perspectives used in knowledge hiding research.
Influence Mechanisms
There are findings on the mediating roles of antecedent variables that affect knowledge hiding. Emotional and cognitive factors (e.g., leadership, workplace stressors, interpersonal relationships, personality traits, and psychological ownership) can induce knowledge hiding. In terms of leadership, Abdullah et al. (2019) point out that ethical leadership inhibits employees' knowledge hiding by enhancing their relational social capital. Anser et al. (2020) find that the ethical behavior of ethical leaders can enhance the perception of “meaningful work” for service industries employees, thereby reducing the possibility of engaging in knowledge hiding behaviors. Khalid et al. (2018) find that perception of interpersonal justice mediates the relationship between abusive supervision and knowledge hiding. Feng and Wang (2019) believe that abusive supervision indirectly affects knowledge hiding through job insecurity. Pradhan et al. (2019) show that psychological contract breaching and the attacks toward supervisors play a partial mediating role in the process in which abusive supervision affects knowledge hiding. Ghani et al. (2020a) further point out that abusive supervision can easily lead to psychological contract breach, thus leading employees to attack their colleagues and deliberately hide knowledge from them. In addition, Lin et al. (2020) find that individual-focused empowering leadership enhances the psychological safety of subordinates, thereby reducing their knowledge hiding, whereas differentiated empowering leadership causes group relational conflicts, thereby increasing subordinate knowledge hiding. Abdillah et al. (2020) study the dual mediating mechanisms of altruistic leadership, which inhibits and prevents employees from knowledge hiding, pointing out that the positive emotions induced by altruistic leadership and LMX have important effects.
Regarding workplace stressors and interpersonal relationships, Aljawarneh and Atan (2018) find that cynicism mediates the relationship between tolerance of workplace incivility and knowledge hiding. Riaz et al. (2019) find that workplace ostracism has a significant impact on evasive hiding and playing dumb, and that work strain plays a mediating role. Yao et al. (2020a , b ) have shown that relational identification and interpersonal trust play a chain-mediating role in the relationship between negative workplace gossip and knowledge hiding. At the same time, emotional exhaustion and organizational identification play a chain-mediating role in the relationship between workplace bullying and knowledge hiding. Jahanzeb et al. (2020b) believe that the experience of injustice causes employees to be psychologically separated from the organization and thus employees will show more knowledge hiding behaviors. Zhao et al. (2019) demonstrate that organizational identification mediates the negative impact of LMX on evasive hiding and playing dumb. Weng et al. (2020) point out that employees' upward LMX social comparison with their colleagues leads to envy of and knowledge hiding toward their colleagues. He et al. (2020) discover that psychological safety fully mediates the influence of LMX on knowledge hiding and partially mediates the influence of supervisor-subordinate guanxi on knowledge hiding.
Another aspect is shown through personality traits. Wang et al. (2014) find that perceived social identity mediates the relationship between the Big Five personality traits and knowledge hiding. Pan et al. (2018) examine the positive relationship between the “dark triad of personality” (Machiavellianism, narcissism, and psychopathy) and knowledge hiding, as well as the mediating effect of transactional psychological contracts on this relationship. Zhao and Xia (2019) point out that the negative affect states of nurses staff can “activate” their moral disengagement mechanism, allowing them to redefine their knowledge hiding behaviors as reasonable and acceptable, and thus exacerbating their knowledge hiding tendency. The final aspect is psychological ownership. Research by Peng (2013) and Huo et al. (2016) show that employees' psychological ownership of knowledge enhances their territorial awareness, which in turn causes them to hide knowledge from colleagues. Liu et al. (2020) confirm that the influence of workplace status on employee knowledge hiding is carried out through two opposite mechanisms: perceived knowledge sharing responsibility and envy. The former negatively mediates the relationship between the two, and the latter positively mediates it.
Some scholars have also studied the mediating effect of knowledge hiding. For instance, scholars examine the process through which knowledge hiding impairs individual or team creativity and innovation performance. Cerne et al. (2014) find that the knowledge hiding makes hiders reduce their own creativity, and colleague distrust plays a mediating role. Arain et al. (2019) show that supervisor knowledge hiding can reduce subordinates' self-efficacy and thus reduce their innovation. Khoreva and Wechtler (2020) point out that playing dumb and rationalized hiding can indirectly influence employee innovation performance through the mediating effect of well-being. Fong et al. (2018) confirm that a decrease in absorptive capacity is the key mediator in the relationship between knowledge hiding and team creativity. Zhang and Min (2019) state that team learning partially mediates the relationship between knowledge hiding and project team performance.
Moreover, researchers have studied the process through which knowledge hiding affects employees' subsequent interpersonal behaviors. For instance, Burmeister et al. (2019) find that guilt and shame play opposite mediating roles in the relationship between individual knowledge hiding and its subsequent interpersonal-oriented OCB. Arain et al. (2020b) point out that supervisor knowledge hiding negatively influences subordinates' OCB toward their supervisors, and subordinate distrust in their supervisors plays a mediating role. Supervisor knowledge hiding can also activate employee moral disengagement, prompting them to reduce OCB toward their supervisors and increase silence behaviors ( Arain et al., 2020a ). Jiang et al. (2019) suggest that knowledge hiding makes the hiders feel the insecurity of self-expression and interpersonal risk, thereby reducing their psychological safety and endangering their ability to thrive at work. Despite these advancements, it is necessary to develop a robust framework that integrates multipath models based on different innovative theoretical perspectives.
Regarding the moderating role of contextual factors on knowledge hiding, the existing research mainly explores the contingency influence of individual differences, job characteristics, team characteristics, and team/organizational climate. In terms of individual differences, some scholars find that organizational psychological ownership can effectively reduce the knowledge hiding resulting from territoriality ( Peng, 2013 ). Furthermore, psychological ownership significantly moderates the inverted U-shaped relationship between knowledge leadership and knowledge hiding. This curved relationship is more obvious among employees with high psychological ownership ( Xia et al., 2019 ). High psychological ownership can also minimize the impact of abusive supervision on knowledge hiding ( Ghani et al., 2020a ). Other scholars explore the boundary effect of positive traits, such as individualism/collectivist values ( Semerci, 2019 ), positive affectivity ( Jahanzeb et al., 2020a ), benevolence or tolerance ( Jahanzeb et al., 2020b ), prosocial motivations ( Škerlavaj et al., 2018 ), harmonious work enthusiasm ( Anser et al., 2020 ), professional commitment ( Malik et al., 2019 ), trust-related affect/cognition ( Nadeem et al., 2021 ), social skills ( Wang et al., 2019 ), and cultural intelligence ( Bogilović et al., 2017 ). In addition to these studies, scholars examine the impacts of negative traits on knowledge hiding, such as negative reciprocity ( Zhao et al., 2016 ; Jahanzeb et al., 2019 ), instrumental thinking ( Abdullah et al., 2019 ), hostile attribution bias ( Khalid et al., 2020 ), moral disengagement ( Zhao et al., 2016 ), and cynicism ( Jiang et al., 2019 ).
In relation to job characteristics, task interdependence has attracted a lot of attention. Huo et al. (2016) point out that task interdependence can reduce the territorial awareness and knowledge hiding caused by psychological ownership. Hernaus et al. (2019) find that task interdependence can help reduce the probability of employees' evasive knowledge hiding due to maintaining their competitiveness. Fong et al. (2018) show that task interdependence moderates the relationship between knowledge hiding and team absorptive capacity. Weng et al. (2020) suggest that the interdependence of cooperative and competitive goals has opposite moderating effects on the relationship between upward LMX social comparison and knowledge hiding. In addition, Pan and Zhang (2018) also analyze the influence of work autonomy on the intensity of the relationship between neuroticism and knowledge hiding.
Regarding the team/organizational climate, research shows that in an environment that values information exchange and cooperation, the negative influence of knowledge hiding will be greatly weakened. Accordingly, Cerne et al. (2014) study the boundary effect of the team achievement-motivation climate (e.g., performance climate and mastery climate) on the relationship between knowledge hiding and the decrease in the hider's creativity. They discover that the negative effect of knowledge hiding on the hider's creativity is reduced in a mastery climate. Furthermore, Cerne et al. (2017) find the moderating effects of mastery climate, task interdependence, and autonomy on the relationship between knowledge hiding and innovative work behavior. Bari et al. (2019) obtain similar findings which point out that a perceived mastery climate reduces the negative impact of evasive hiding and playing dumb on team creativity. Feng and Wang (2019) find that the interaction between abusive supervision and a mastery climate is negatively related to knowledge hiding, and the interaction between abusive supervision and a performance climate is positively related to knowledge hiding. On the one hand, when the organization pays more attention to individual performance feedback, performance-prove goal orientation can positively predict knowledge hiding. On the other hand, when the organization pays more attention to group performance feedback, performance-prove goal orientation is negatively correlated with knowledge hiding ( Zhu et al., 2019 ). Compared to individual rewards, team-based rewards are more likely to reduce the distrust caused by knowledge hiding, promoting the team to work hard to achieve a common goal, forming a relatively stable team structure, and improving team viability ( Wang et al., 2019 ). Yao et al. (2020a , b ) reveal the buffering effect of a forgiveness climate on the relationship between negative workplace gossip/workplace bullying and knowledge hiding. Khalid et al. (2018) clarify the role of Islamic work ethics in moderating the relationship between abusive supervision and knowledge hiding. Among these findings, the existing research on the moderating effects still focuses more on the first stage of the antecedents–knowledge hiding–consequences linkage, but there is a lack of systematic development of the moderation mechanism in the second stage.
Future Research Directions
Based on a descriptive analysis, bibliometric analysis, and content analysis, we find that research on knowledge hiding focuses mainly on five clusters. Despite the ongoing progress, several research gaps are worth further addressing.
(1) Comprehensive studies on the concept and dimensions of knowledge hiding are needed to provide a robust conceptual framework. Although the definition and three-dimensional view of knowledge hiding by Connelly et al. (2012) are widely adopted by many scholars, more research is needed to carry out in-depth comparative analysis to clarify the connections and differences between knowledge hiding and similar concepts (e.g., knowledge non-sharing, knowledge sharing hostility, knowledge contribution loafing, counterproductive knowledge behavior, knowledge hoarding, knowledge protection, employee silence, etc.). Further, more studies should continue exploring the dimensions of knowledge hiding. There is a lack of focus on knowledge hiders' psychological motivation and respective knowledge hiding strategies. For example, research on proactive, reactive, and passive knowledge hiding could enrich the field research. In addition, more studies should further explore the unique reasons and consequences of a rationalized hiding behavior. There is a need to verify the ethical aspect of rationalized hiding, when knowledge hiding is used to protect confidential information or the interests of third parties ( Zhao et al., 2019 ).
(2) Future studies need to further explore the consequences of knowledge hiding. Based on a systematic review (see Figure 3 ), we find that previous studies have focused mainly on the antecedents of knowledge hiding. Although some studies have addressed the impacts of knowledge characteristics, individual factors, team-level and interpersonal factors, and organizational-level factors on knowledge hiding, more work is needed to provide comprehensive studies on the generating mechanisms and the respective coping strategies of knowledge hiding. Prior studies have shown that knowledge hiding has impacts on individual-level outcomes (e.g., individual creativity, in-role and extra-role performance, and coworker relationships) and team-level outcomes (e.g., team creativity). However, there is a lack of research on organizational-level outcomes. Moreover, prior studies focus mainly on the impacts of knowledge hiding on the knowledge seekers and the whole team, but seldom has the research discussed the potential effects of knowledge hiding on the knowledge hiders themselves. Therefore, future research should devote more attention to the negative effects of knowledge hiding on the knowledge hiders, the team, and the organization, and also explore the consequences of different dimensions of knowledge hiding. For example, more studies could address the research gap as to whether knowledge hiding may stimulate self-reflection and prompt moral and psychological compensation for the knowledge hiders. To enrich the multilevel mediating and moderating variables, future studies could explore the boundary conditions of knowledge hiding and their respective knowledge management strategies. In short, it is necessary to increase research on the consequences of knowledge hiding to enrich the antecedents–knowledge hiding–consequences research path.
(3) More studies on multilateral, cross-level, and collective knowledge hiding are needed, and it is appropriate to introduce new paradigms for knowledge hiding research. Existing research on knowledge hiding highlights mainly two parties: the hider (A) and the seeker (B) (i.e., B seeks knowledge from A, while A hides knowledge from B). Most studies address knowledge hiding among colleagues at the horizontal level. In recent years, some scholars have started to show interest in knowledge hiding at the vertical level, that is, the top-down knowledge hiding of superiors from subordinates. However, the research on the antecedents and the generating mechanisms of knowledge hiding at the vertical level is still in the stage of exploration. There is a lack of research on bottom-up knowledge hiding (of the subordinates from their superiors). Therefore, it is necessary to study knowledge hiding adopted by people from different hierarchies (e.g., bottom, mid, and high levels) in the organizations, comparing the differences between top-down and bottom-up knowledge hiding, so as to identify regular patterns of cross-level knowledge flow within the organizations. Future research could also examine whether the knowledge hiding of top managers could trigger a trickle-down effect, referring to the fact that the behaviors of the top leaders will affect employees in the formal vertical power chain, given that knowledge hiding can be a multi-participant phenomenon. Therefore, future research could examine the contagious effects of knowledge hiding (e.g., B seeks knowledge from A, but A hides knowledge from B; B then feels lost and hides knowledge from other colleagues), diffusion effects (e.g., B seeks knowledge from A while A hides knowledge from B; A asks C to hide knowledge from B as well), bystander effects (e.g., B seeks knowledge from A, while A hides knowledge from B; C witnesses A's knowledge hiding and is influenced by it, so C also hides knowledge from B and other colleagues), and collective knowledge hiding.
(4) Future scholars should innovate theoretical perspectives and integrate multidisciplinary theories into knowledge hiding research. At present, knowledge hiding research is based mainly on theories such as social exchange, social cognition, social capital, social learning, conservation of resources, territoriality, and psychological ownership. To enrich the field research, it is necessary to diversify the theories. For example, future studies could explore the influence of social exchange relations (e.g., relative LMX) on knowledge hiding, comparing the influence of social LMX and economic LMX on employee willingness to hide knowledge. Future scholars could also conduct multi-interdisciplinary research studies. The research on how an individual's previous workplace behavior affects his or her subsequent workplace behavior has attracted great interest from scholars and mainstream journals in organizational behavior in recent years. Given that knowledge hiding is a typical morality-related behavior, future research could introduce novel and original theoretical viewpoints. For example, a moral balance model and a moral cleansing effect in disciplines such as moral psychology and cognitive psychology, can be used to explore how an individual's previous knowledge hiding behavior influences subsequent behavior in the workplace. Furthermore, knowledge hiding is considered as an emotion-driven behavior. Therefore, scholars could consider employing Lazarus's cognitive–motivational–relational (CMR) theory of emotion ( Lazarus, 1991 ) to better understand the psychological process behind knowledge hiding. Moreover, there is a lack of research on the relationship between individual affect/emotion and knowledge hiding. Therefore, scholars could employ theories, such as affective events theory and self-conscious moral emotion theory, to analyze the subsequent behavior of the hiders and seekers who are driven by affect/emotion.
(5) Research designs need more diversification. Most of the prior studies focus on the individuals, and few research studies focus on both individual and team effects. Knowledge hiding is a complex organizational behavior that concerns individual, team/interpersonal, and organizational levels. Therefore, future research could introduce data tracking technologies, such as big data analysis, to study and compare the dynamic and static (long-term and short-term) effects of multilevel knowledge hiding. Moreover, it is necessary to diversify research methods in the field. Most existing research uses one-wave or multistage surveys, employee self-evaluation, and empirical tests, with few studies using case studies and interviews. These research methods may suffer from a lack of reliability of data sources. Future research could integrate multiple methodologies (e.g., combining case studies, experimental research, surveys, and objective data mining) to verify data, which could improve the internal and external validity of the research and enhance the robustness of conclusions. In particular, it is necessary to focus on the combination of experimental and empirical research, making full use of the strengths of each method to validate the research. Researchers could carry out preliminary tests on relevant hypotheses through experimental research and then supplement them with surveys for secondary verification.
(6) Future research should integrate more cultural, sectoral, and organizational factors to enrich the findings. As discussed in the findings, most of the knowledge hiding data were collected in China and Pakistan. It is necessary to develop the diversity of knowledge hiding data in terms of country of origin. In addition, there is a lack of cross-country academic collaboration. Collaborating across borders could help to generate new ideas and allow for collecting data from different sources. Meanwhile, it would be very interesting to promote cross-country studies to identify the different definitions, perceptions, implementations, and patterns of knowledge hiding, whilst paying more attention to the relationship between cultural dimensions and knowledge hiding. Apart from cross-cultural and cross-country variables, future research could also investigate industry characteristics (such as knowledge-intensive and non-knowledge-intensive industries and masculine and feminine industries), team standards/norms (such as team moral norms), and firm size (small medium enterprises vs. multinational companies) so as to identify the boundary conditions of individual knowledge hiding behavior. Through conducting sector-specific and cross-sector comparison for knowledge hiding, we would be able to adjust knowledge management methods.
Conclusions
This article provides a systematic review of knowledge hiding. It contributes to the identification of publication patterns on knowledge hiding between 2012 and 2020. Further, we have highlighted the most influential studies, mapped the research gaps, and provided the potential research directions in the field.
This study is not without limitations. We use SCI and SSCI web of science as the databases. Using this literature search method excludes book chapters, reports, unpublished dissertations, with/without peer reviewed conference proceedings, newsletters, government documents, and working papers. Consequently, this review may not have captured the full range of scholarly literature on knowledge hiding. In the future, to reduce the publication bias ( Kepes et al., 2012 ), it would be interesting to include other databases to search literatures, for instance, the work published in the Emerging Sources Citation Index (ESCI) journals can be considered. Second, the research on knowledge hiding is emerging, and some scholars may argue that it is not yet mature enough to review the research field. In our opinion, it is only with such a complete literature review that a clear picture of knowledge hiding research can be developed so that scholars can better define research problems, innovate the research theories and methods, and enrich the field research with a robust framework.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
Author Contributions
PH, CJ, ZX, and CS designed and supervised the study. PH collected the data. PH and ZX analyzed the data. PH, CJ, and CS wrote the manuscript. All authors contributed equally to this manuscript, reviewed, and approved this manuscript for publication.
Funding was provided by Huaqiao University's Academic Project Supported by the Fundamental Research Funds for the Central Universities (20SKGC-QT02) and the National Natural Science Foundation of China (72172048).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher's Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Abdillah, M. R., Wu, W., and Anita, R. (2020). Can altruistic leadership prevent knowledge-hiding behaviour? Testing dual mediation mechanisms. Knowl. Manag. Res. Pract . doi: 10.1080/14778238.2020.1776171
CrossRef Full Text | Google Scholar
Abdullah, M. I., Dechun, H., Ali, M., and Usman, M. (2019). Ethical leadership and knowledge hiding: a moderated mediation model of relational social capital, and instrumental thinking. Front. Psychol. 10:2403. doi: 10.3389/fpsyg.2019.02403
PubMed Abstract | CrossRef Full Text | Google Scholar
Abubakar, A. M., Behravesh, E., Rezapouraghdam, H., and Yildiz, S. B. (2019). Applying artificial intelligence technique to predict knowledge hiding behavior. J. Inf. Manag. 49, 45–57. doi: 10.1016/j.ijinfomgt.2019.02.006
Aljawarneh, N. M. S., and Atan, T. (2018). Linking tolerance to workplace incivility, service innovative, knowledge hiding, and job search behavior: the mediating role of employee cynicism. Negot. Confl. Manag. Res. 11, 298–320. doi: 10.1111/ncmr.12136
Anand, A., Centobelli, P., and Cerchione, R. (2020). Why should I share knowledge with others? A review-based framework on events leading to knowledge hiding. J. Organ. Chang. Manag . 33, 379–399. doi: 10.1108/JOCM-06-2019-0174
Anaza, N. A., and Nowlin, E. L. (2017). What's mine is mine: a study of salesperson knowledge withholding & hoarding behavior. Ind. Mark. Manag. 64, 14–24. doi: 10.1016/j.indmarman.2017.03.007
Anser, M. K., Ali, M., Usman, M., Rana, M. L. T., and Yousaf, Z. (2020). Ethical leadership and knowledge hiding: an intervening and interactional analysis. Serv. Ind. J. 41, 307–329. doi: 10.1080/02642069.2020.1739657
Arain, G. A., Bhatti, Z. A., Ashraf, N., and Fang, Y. H. (2020b). Top-down knowledge hiding in organizations: an empirical study of the consequences of supervisor knowledge hiding among local and foreign workers in the Middle East. J. Bus. Ethics 164, 611–625. doi: 10.1007/s10551-018-4056-2
Arain, G. A., Bhatti, Z. A., Hameed, I., and Fang, Y. H. (2019). Top-down knowledge hiding and innovative work behavior (IWB): a three-way moderated-mediation analysis of self-efficacy and local/foreign status. J. Knowl. Manag . 24, 127–149. doi: 10.1108/JKM-11-2018-0687
Arain, G. A., Hameed, I., Umrani, W. A., Khan, A. K., and Sheikh, A. Z. (2020a). Consequences of supervisor knowledge hiding in organizations: a multilevel mediation analysis. Appl. Psychol . 70, 1242–1266. doi: 10.1111/apps.12274
Babič, K., Cerne, M., Connelly, C. E., Dysvik, A., and Škerlavaj, M. (2019). Are we in this together? Knowledge hiding in teams, collective prosocial motivation and leader-member exchange. J. Knowl. Manag . 23, 1502–1522. doi: 10.1108/JKM-12-2018-0734
Bari, M. W., Abrar, M., Shaheen, S., Bashir, M., and Fanchen, M. (2019). Knowledge hiding behaviors and team creativity: the contingent role of perceived mastery motivational climate. Sage Open 9. doi: 10.1177/2158244019876297
Bari, M. W., Ghaffar, M., and Ahmad, B. (2020). Knowledge-hiding behaviors and employees' silence: mediating role of psychological contract breach. J. Knowl. Manag . 24, 2171–2194. doi: 10.1108/JKM-02-2020-0149
Bernatović, I., Gomezel, A. S., and Cerne, M. (2021). Mapping the knowledge-hiding field and its future prospects: a bibliometric co-citation, co-word, and coupling analysis. Knowl. Manag. Res. Pract. doi: 10.1080/14778238.2021.1945963
Bogilović, S., Cerne, M., and Škerlavaj, M. (2017). Hiding behind a mask? Cultural intelligence, knowledge hiding, and individual and team creativity. Eur. J. Work Organ. Psychol. 26, 710–723. doi: 10.1080/1359432X.2017.1337747
Burmeister, A., Fasbender, U., and Gerpott, F. H. (2019). Consequences of knowledge hiding: the differential compensatory effects of guilt and shame. J. Occup. Organ. Psychol. 92, 281–304. doi: 10.1111/joop.12249
Butt, A. S. (2019). Determinants of top-down knowledge hiding in firms: an individual-level perspective. Asian Bus. Manag. 20, 259–279. doi: 10.1057/s41291-019-00091-1
Butt, A. S., and Ahmad, A. B. (2019). Are there any antecedents of top-down knowledge hiding in firms? Evidence from the United Arab Emirates. J. Knowl. Manag. 23, 1605–1627. doi: 10.1108/JKM-04-2019-0204
Cerne, M., Hernaus, T., Dysvik, A., and Škerlavaj, M. (2017). The role of multilevel synergistic interplay among team mastery climate, knowledge hiding, and job characteristics in stimulating innovative work behavior. Hum. Resour. Manag. J. 27, 281–299. doi: 10.1111/1748-8583.12132
Cerne, M., Nerstad, C. G. L., Dysvik, A., and Škerlavaj, M. (2014). What goes around comes around: knowledge hiding, perceived motivational climate, and creativity. Acad. Manag. Ann. 57, 172–192. doi: 10.5465/amj.2012.0122
CrossRef Full Text
Connelly, C. E., and Kelloway, E. K. (2003). Predictors of employees' perceptions of knowledge sharing cultures. Leadersh. Organ. Dev. J. 24, 294–301. doi: 10.1108/01437730310485815
Connelly, C. E., and Zweig, D. (2015). How perpetrators and targets construe knowledge hiding in organizations. Eur. J. Work Organ. Psychol. 24, 479–489. doi: 10.1080/1359432X.2014.931325
Connelly, C. E., Zweig, D., Webster, J., and Trougakos, J. P. (2012). Knowledge hiding in organizations. J. Organ. Behav. 33, 64–88. doi: 10.1002/job.737
de Garcia, P. S., Oliveira, M., and Brohman, K. (2020). Knowledge sharing, hiding and hoarding: how are they related? Knowl. Manag. Res. Pract . doi: 10.1080/14778238.2020.1774434
Fang, Y. H. (2017). Coping with fear and guilt using mobile social networking applications: knowledge hiding, loafing, and sharing. Telemat. Inform. 34, 779–797. doi: 10.1016/j.tele.2017.03.002
Feng, J., and Wang, C. (2019). Does abusive supervision always promote employees to hide knowledge? From both reactance and COR perspectives. J. Knowl. Manag. 23, 1455–1474. doi: 10.1108/JKM-12-2018-0737
Fong, P. S. W., Men, C., Luo, J., and Jia, R. (2018). Knowledge hiding and team creativity: the contingent role of task interdependence. Manag. Decis. 56, 329–343. doi: 10.1108/MD-11-2016-0778
Gagné, M., Tian, A. W., Soo, C., Zhang, B., Ho, K. S. B., and Hosszu, K. (2019). Different motivations for knowledge sharing and hiding: the role of motivating work design. J. Organ. Behav. 40, 783–799. doi: 10.1002/job.2364
Ghani, U., Teo, T., Li, Y., Usman, M., Islam, Z. U., Gul, H., et al. (2020a). Tit for tat: abusive supervision and knowledge hiding-the role of psychological contract breach and psychological ownership. Int. J. Environ. Res. Public Health 17:1240. doi: 10.3390/ijerph17041240
Ghani, U., Zhai, X. S., Spector, J. M., Chen, N. S., Lin, L., Ding, D. H., et al. (2020b). Knowledge hiding in higher education: role of interactional justice and professional commitment. High. Educ. 79, 325–344. doi: 10.1007/s10734-019-00412-5
He, P., Sun, R., Zhao, H., Zheng, L., and Shen, C. (2020). Linking work-related and non-work-related supervisor–subordinate relationships to knowledge hiding: a psychological safety lens. Asian Bus. Manag. doi: 10.1057/s41291-020-00137-9
Hernaus, T., Cerne, M., Connelly, C., Vokic, N. P., and Škerlavaj, M. (2019). Evasive knowledge hiding in academia: when competitive individuals are asked to collaborate. J. Knowl. Manag. 23, 597–618. doi: 10.1108/JKM-11-2017-0531
Huo, W., Cai, Z., Luo, J., Men, C., and Jia, R. (2016). Antecedents and intervention mechanisms: a multi-level study of R & D team's knowledge hiding behavior. J. Knowl. Manag. 20, 880–897. doi: 10.1108/JKM-11-2015-0451
Jahanzeb, S., De Clercq, D., and Fatima, T. (2020a). Bridging the breach: using positive affectivity to overcome knowledge hiding after contract breaches. J. Psychol. 154, 249–272. doi: 10.1080/00223980.2019.1705235
Jahanzeb, S., De Clercq, D., and Fatima, T. (2020b). Organizational injustice and knowledge hiding: the roles of organizational dis-identification and benevolence. Manag. Decis. 59, 446–462. doi: 10.1108/MD-05-2019-0581
Jahanzeb, S., Fatima, T., Bouckenooghe, D., and Bashir, F. (2019). The knowledge hiding link: a moderated mediation model of how abusive supervision affects employee creativity. Eur. J. Work Organ. Psychol. 28, 810–819. doi: 10.1080/1359432X.2019.1659245
Jha, J. K., and Varkkey, B. (2018). Are you a cistern or a channel? Exploring factors triggering knowledge-hiding behavior at the workplace: evidence from the Indian R&D professionals. J. Knowl. Manag . 22, 824–849. doi: 10.1108/JKM-02-2017-0048
Jiang, Z., Hu, X., Wang, Z., and Jiang, X. (2019). Knowledge hiding as a barrier to thriving: the mediating role of psychological safety and moderating role of organizational cynicism. J. Organ. Behav. 40, 800–818. doi: 10.1002/job.2358
Kang, S. W. (2016). Knowledge withholding: psychological hindrance to the innovation diffusion within an organisation. Knowl. Manag. Res. Pract. 14, 144–149. doi: 10.1057/kmrp.2014.24
Kepes, S., Banks, G. C., McDaniel, M., and Whetzel, D. L. (2012). Publication bias in the organizational sciences. Organ. Res. Methods 15, 624–662. doi: 10.1177/1094428112452760
Khalid, M., Bashir, S., Khan, K. A., and Abbas, N. (2018). When and how abusive supervision leads to knowledge hiding behaviors: an Islamic work ethics perspective. Leadersh. Organ. Dev. J. 39, 794–806. doi: 10.1108/LODJ-05-2017-0140
Khalid, M., Gulzar, A., and Khan, K. A. (2020). When and how the psychologically entitled employees hide more knowledge? Int. J. Hosp. Manag. 89:102413. doi: 10.1016/j.ijhm.2019.102413
Khoreva, V., and Wechtler, H. (2020). Exploring the consequences of knowledge hiding: an agency theory perspective. J. Manag. Psychol. 35, 71–84. doi: 10.1108/JMP-11-2018-0514
Lazarus, R. S. (1991). Progress on a cognitive-motivational-relational theory of emotion. Am. Psychol. 46, 819–834. doi: 10.1037/0003-066X.46.8.819
Lee, K., and Allen, N. J. (2002). Organizational citizenship behavior and workplace deviance: the role of affect and cognitions. J. Appl. Psychol . 87, 131–142. doi: 10.1037/0021-9010.87.1.131
Lin, M., Zhang, X., Ng, B. C. S., and Zhong, L. (2020). To empower or not to empower? Multilevel effects of empowering leadership on knowledge hiding. Int. J. Hosp. Manag. 89:102540. doi: 10.1016/j.ijhm.2020.102540
Lin, T. C., and Huang, C. C. (2010). Withholding effort in knowledge contribution: the role of social exchange and social cognitive on project teams. Inf. Manag. 47, 188–196. doi: 10.1016/j.im.2010.02.001
Liu, Y., Zhu, J. N. Y., and Lam, L. W. (2020). Obligations and feeling envied: a study of workplace status and knowledge hiding. J. Manag. Psychol. 35, 347–359. doi: 10.1108/JMP-05-2019-0276
Malik, O. F., Shahzad, A., Raziq, M. M., Khan, M. M., Yusaf, S., and Khan, A. (2019). Perceptions of organizational politics, knowledge hiding, and employee creativity: the moderating role of professional commitment. Pers. Individ. Differ. 142, 232–237. doi: 10.1016/j.paid.2018.05.005
Men, C., Fong, P. S. W., Huo, W., Zhong, J., Jia, R., and Luo, J. (2020). Ethical leadership and knowledge hiding: a moderated mediation model of psychological safety and mastery climate. J. Bus. Ethics 166, 461–472. doi: 10.1007/s10551-018-4027-7
Moh'd, S. S., Cerne, M., and Zhang, P. (2021). An exploratory configurational analysis of knowledge hiding antecedents in project teams. Proj. Manag. J. 52, 31–44. doi: 10.1177/8756972820939768
Nadeem, M. A., Liu, Z., Ghani, U., Younis, A., and Xu, Y. (2021). Impact of shared goals on knowledge hiding behavior: the moderating role of trust. Manag. Decis . 59, 1312–1332. doi: 10.1108/MD-09-2019-1197
Offergelt, F., Spörrle, M., Moser, K., and Shaw, J. D. (2019). Leader-signaled knowledge hiding: effects on employees' job attitudes and empowerment. J. Organ. Behav. 40, 819–833. doi: 10.1002/job.2343
Pan, W., and Zhang, Q. (2018). Withholding knowledge in teams: an interactionist perspective of personality, justice, and autonomy. Soc. Behav. Pers. 46, 2009–2024. doi: 10.2224/sbp.7390
Pan, W., Zhang, Q., Teo, T. S. H., and Lim, V. K. G. (2018). The dark triad and knowledge hiding. J. Inf. Manag. 42, 36–48. doi: 10.1016/j.ijinfomgt.2018.05.008
Peng, H. (2013). Why and when do people hide knowledge? J. Knowl. Manag. 17, 398–415. doi: 10.1108/JKM-12-2012-0380
Pickering, C., and Byrne, J. (2014). The benefits of publishing systematic quantitative literature reviews for PhD candidates and other early-career researchers. High. Educ. Res. Dev. 33, 534–548. doi: 10.1080/07294360.2013.841651
Pradhan, S., Srivastava, A., and Mishra, D. K. (2019). Abusive supervision and knowledge hiding: the mediating role of psychological contract violation and supervisor directed aggression. J. Knowl. Manag. 24, 216–234. doi: 10.1108/JKM-05-2019-0248
Riaz, S., Xu, Y., and Hussain, S. (2019). Workplace ostracism and knowledge hiding: the mediating role of job tension. Sustainability 11:5547. doi: 10.3390/su11205547
Semerci, A. B. (2019). Examination of knowledge hiding with conflict, competition and personal values. Int. J. Confl. Manag. 30, 111–131. doi: 10.1108/IJCMA-03-2018-0044
Serenko, A., and Bontis, N. (2016). Understanding counterproductive knowledge behavior: antecedents and consequences of intra-organizational knowledge hiding. J. Knowl. Manag. 20, 1199–1224. doi: 10.1108/JKM-05-2016-0203
Shen, X., Li, Y., Sun, Y., Chen, J., and Wang, F. (2019). Knowledge withholding in online knowledge spaces: social deviance behavior and secondary control perspective. J. Assoc. Inf. Sci. Technol. 70, 385–401. doi: 10.1002/asi.24192
Singh, S. K. (2019). Territoriality, task performance, and workplace deviance: empirical evidence on role of knowledge hiding. J. Bus. Res. 97, 10–19. doi: 10.1016/j.jbusres.2018.12.034
Škerlavaj, M., Connelly, C. E., Cerne, E., and Dysvik, A. (2018). Tell me if you can: time pressure, prosocial motivation, perspective taking, and knowledge hiding. J. Knowl. Manag. 22, 1489–1509. doi: 10.1108/JKM-05-2017-0179
Stenius, M., Hankonen, N., Ravaja, N., and Haukkala, A. (2016). Why share expertise? A closer look at the quality of motivation to share or withhold knowledge. J. Knowl. Manag. 20, 181–198. doi: 10.1108/JKM-03-2015-0124
Tranfield, D., Denyer, D., and Palminder, S. (2003). Towards a methodology for developing evidence-informed management knowledge by means of systematic review. Br. J. Manag . 14, 207–222. doi: 10.1111/1467-8551.00375
Tsay, C. H. H., Lin, T. C., Yoon, J., and Huang, C. C. (2014). Knowledge withholding intentions in teams: the roles of normative conformity, affective bonding, rational choice and social cognition. Decis. Support Syst. 67, 53–65. doi: 10.1016/j.dss.2014.08.003
Vlačić, B., Corbo, L., Costa e Silva, S., and Dabi,ć, M. (2021). The evolving role of artificial intelligence in marketing: a review and research agenda. J. Bus. Res. 128, 187–203. doi: 10.1016/j.jbusres.2021.01.055
Wang, Y., Han, M., Xiang, D., and Hampson, D. P. (2019). The double-edged effects of perceived knowledge hiding: empirical evidence from the sales context. J. Knowl. Manag. 23, 279–296. doi: 10.1108/JKM-04-2018-0245
Wang, Y. S., Lin, H. H., Li, C. R., and Lin, S. J. (2014). What drives students' knowledge-withholding intention in management education? An empirical study in Taiwan. Acad. Manag. Learn. Educ. 13, 547–568. doi: 10.5465/amle.2013.0066
Webster, J., Brown, G., Zweig, D., Connelly, C. E., Brodt, S., and Sitkin, S. (2008). Beyond knowledge sharing: withholding knowledge at work. Res. Pers. Hum. Resour. Manag. 27, 1–37. doi: 10.1016/S0742-7301(08)27001-5
Weng, Q., Latif, K., Khan, A. K., Tariq, H., Butt, H. P., Obaid, A., et al. (2020). Loaded with knowledge, yet green with envy: leader–member exchange comparison and coworkers-directed knowledge hiding behavior. J. Knowl. Manag. 24, 1653–1680. doi: 10.1108/JKM-10-2019-0534
Wu, D. (2020). Empirical study of knowledge withholding in cyberspace: integrating protection motivation theory and theory of reasoned behavior. Comput. Hum. Behav. 105:106229. doi: 10.1016/j.chb.2019.106229
Xia, Q., Yan, S., Zhang, Y., and Chen, B. (2019). The curvilinear relationship between knowledge leadership and knowledge hiding: the moderating role of psychological ownership. Leadersh. Organ. Dev. J. 40, 669–683. doi: 10.1108/LODJ-10-2018-0362
Xiao, M., and Cooke, F. L. (2019). Why and when knowledge hiding in the workplace is harmful: a review of the literature and directions for future research in the Chinese context. Asia Pac. J. Hum. Resour. 57, 470–502. doi: 10.1111/1744-7941.12198
Yao, Z., Luo, J., and Zhang, X. (2020a). Gossip is a fearful thing: the impact of negative workplace gossip on knowledge hiding. J. Knowl. Manag. 24, 1755–1775. doi: 10.1108/JKM-04-2020-0264
Yao, Z., Zhang, X., Luo, J., and Huang, H. (2020b). Offense is the best defense: the impact of workplace bullying on knowledge hiding. J. Knowl. Manag. 24, 675–695. doi: 10.1108/JKM-12-2019-0755
Zhai, X., Wang, M., and Ghani, U. (2020). The SOR (Stimulus-Organism-Response) paradigm in online learning: an empirical study of students' knowledge hiding perceptions. Interact. Learn. Environ. 28, 586–601. doi: 10.1080/10494820.2019.1696841
Zhang, Z., and Min, M. (2019). The negative consequences of knowledge hiding in NPD project teams: the roles of project work attributes. Int. J. Constr. Proj. Manag. 37, 225–238. doi: 10.1016/j.ijproman.2019.01.006
Zhao, H., Liu, W., Li, J., and Yu, X. (2019). Leader–member exchange, organizational identification, and knowledge hiding: the moderating role of relative leader–member exchange. J. Organ. Behav. 40, 834–848. doi: 10.1002/job.2359
Zhao, H., and Xia, Q. (2019). Nurses' negative affective states, moral disengagement, and knowledge hiding: the moderating role of ethical leadership. J. Nurs. Manag. 27, 357–370. doi: 10.1111/jonm.12675
Zhao, H., Xia, Q., He, P., Sheard, G., and Wan, P. (2016). Workplace ostracism and knowledge hiding in service organizations. Int. J. Hosp. Manag. 59, 84–94. doi: 10.1016/j.ijhm.2016.09.009
Zhu, Y., Chen, T., Wang, M., Jin, Y., and Wang, Y. (2019). Rivals or allies: how performance-prove goal orientation influences knowledge hiding. J. Organ. Behav. 40, 849–868. doi: 10.1002/job.2372
Keywords: knowledge hiding, systematic literature review, future research directions, content analysis, bibliometric analysis, descriptive analysis
Citation: He P, Jiang C, Xu Z and Shen C (2021) Knowledge Hiding: Current Research Status and Future Research Directions. Front. Psychol. 12:748237. doi: 10.3389/fpsyg.2021.748237
Received: 27 July 2021; Accepted: 05 October 2021; Published: 29 October 2021.
Reviewed by:
Copyright © 2021 He, Jiang, Xu and Shen. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY) . The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Zhixing Xu, xuzhixing@bnu.edu.cn ; Chuangang Shen, psychshen@hqu.edu.cn
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
- Access through your organization
- Purchase PDF
Article preview
Introduction, section snippets, references (72), cited by (88).

Journal of Outdoor Recreation and Tourism
Current knowledge and future research directions for the monitoring and management of visitors in recreational and protected areas, management implications.
- ● enhance the attendance and representation of researchers from parts of Europe so far under represented and different parts of the world such as Asia, the Russian Federation and Africa to make the conference truly international,
- ● strengthen the relevance of the conference for practitioners and managers, and
- ● communicate the value of research, including how new methods and technologies can enhance sustainable decision making .
Quantifying the literature
Who does the research and where, conclusions, managers' experiences of visitor monitoring in swedish outdoor recreational areas, the impacts of trail infrastructure on vegetation and soils: current literature and future directions, journal of environmental management, public participation gis: a new method for national park planning, landscape and urban planning, comparing webshare services to assess mountain bike use in protected areas, monitoring options for visitor numbers in national parks and natural areas, journal for nature conservation, sense of place as a determinant of people's attitudes towards the environment: implications for natural resources management and planning in the great barrier reef, australia, recreation ecology research in east asia's protected areas: redefining impacts, psychological effects of forest environments on healthy adults: shinrin-yoku (forest-air bathing, walking) as a possible method of stress reduction, public health, english for research publication and dissemination in bi-/multiliterate environments: the case of romanian academics, journal of english for academic purposes, a quantitative analysis of the causes of the global climate change research distribution, global environmental change, “you don’t say what you know, only what you can”: the perceptions and practices of senior spanish academics regarding research dissemination in english, english for specific purposes, impacts of recreation and tourism on plant biodiversity and vegetation in protected areas in australia, the role of distance in peri-urban national park use: who visits them and how far do they travel, applied geography, ‘seeing red’in national parks: how visitors' values affect perceptions and park experiences, recreational activities in urban parks: spatial interactions among users, a review of the impacts of nature based recreation on birds, the use of public participation gis (ppgis) for park visitor management: a case study of mountain biking, tourism management, monitoring visitors to natural areas in wintertime: issues in counter accuracy, journal of sustainable tourism, significance: recognizing the value of research across national and linguistic boundaries, asia pacific education review, past on-site experience, crowding perceptions, and use displacement of visitor groups to a peri-urban national park, environmental management.
- A. Arnberger et al. (2002)
Tourism and recreation: A common threat to IUCN red-listed vascular plants in Europe
Biodiversity and conservation, walk on the wild side: estimating the global magnitude of visits to protected areas, is tourism damaging ecosystems in the andes current knowledge and an agenda for future research, the cognitive benefits of interacting with nature, psychological science, marine protection targets: an updated assessment of global progress, a systematic review of evidence for the added benefits to health of exposure to natural environments, bmc public health, monitoring for management of conservation and recreation in australian protected areas, shortfalls and solutions for meeting national and global conservation area targets, conservation letters, nature, race, and parks: past research and future directions for geographic research, progress in human geography, planning for environmental justice in an urban national park, journal of environmental planning and management, social values versus interpersonal conflict among hikers and mountain bikers, leisure sciences.
- Deloitte Access Economics (2013). Economic contribution of the Great Barrier Reef. Report to the Great Barrier Reef...
- Đorđije, V., Miroslav, V., Lazar, L., Vladimir, S. (2016). Monitoring and management of visitors in recreational and...
Visitors' perceptions of a trail environment and effects on experiences: A model for nature-based recreation experiences
Research priorities in park tourism, alpine vegetation in the context of climate change: a global review of past research and future directions, environmental concerns and attitudes of tourists towards national park uses and services.
- • Tourists' environmental concerns can negatively affect their attitudes towards the appropriateness of activities, facilities, and accommodations within national parks.
- • The attitudes of various groups of visitors regarding human uses of national parks vary between different cultural backgrounds.
- • To reduce the impact of tourism activities on the natural environment and minimising the environmental degradation of protected areas, decision-makers should incorporate into their management plans the environmental concerns and attitudes of visitors who use protected areas and national parks.
Using social media to assess nature-based tourism: Current research and future trends
The range of locations where research has been conducted needs to increase including research in Asia, Oceania, Africa and South America. Countries like Brazil, China and Russia have massive protected area systems that are popular with tourists but sparse research coverage in general (Pickering et al., 2018) with only one paper from China, which assessed tourist preferences for pandas in a reserve (Cong et al., 2014). This limited research may be due to language issues, as Chinese visitors are active users of social media, but typically use Mandarin Chinese, with Sina Weibo the most popular social media platform (Chen, Becken, & Stantic, 2018).
Using social media images and text to examine how tourists view and value the highest mountain in Australia
Orchid conservation and research: an analysis of gaps and priorities for globally red listed species, nature conservation and nature-based tourism: a paradox.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
The PMC website is updating on October 15, 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Front Psychol
Knowledge Hiding: Current Research Status and Future Research Directions
1 Business School, Huaqiao University, Quanzhou, China
Cuiling Jiang
2 Department of Management, Kedge Business School, Talence, France
3 Business School, Beijing Normal University, Beijing, China
Chuangang Shen
Associated data.
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
This article provides a review of scientific articles addressing the topic of knowledge hiding in organizations. Based on a descriptive analysis, bibliometric analysis, and content analysis of a sample of 81 articles published in the academic journals in the Web of Science from 2012 to 2020, we identify the main areas and current dynamics of knowledge hiding research. Our results show that the central research themes of knowledge hiding include five clusters: concept and dimensions, antecedents, consequences, theories, and influence mechanisms. Based on our findings, we suggest future research should further develop the concept and dimensions of knowledge hiding; probe deeper into the consequences of knowledge hiding; explore multilateral, cross-level, and collective knowledge hiding; employ innovative theoretical perspectives and research methods to study knowledge hiding; and address how cultural and other contextual factors may shape the knowledge hiding behavior.
Introduction
Knowledge management plays a crucial role in each organization, which can affect the firms' and employees' performance. However, due to the practice of “knowledge hiding,” it is often challenging to achieve satisfactory results in knowledge management (Connelly and Kelloway, 2003 ). Previous research has pointed out that employees are not willing to share knowledge, due to reasons such as protection and control of knowledge ownership, expertise dominance, and defensive awareness (Huo et al., 2016 ). About 50% of employees have the intention to withhold, mislead, or conceal knowledge that has been requested by another person (Peng, 2013 ). This behavior of deliberately not providing the required knowledge to colleagues when requested is called “knowledge hiding” (Connelly et al., 2012 ), which has become an independent concept that is different from the opposite side of knowledge sharing (Zhao et al., 2019 ).
Obviously, knowledge hiding is very likely to reduce the efficiency of knowledge exchange among members, hinder the generation of new ideas/thoughts, or even destroy trust (Connelly et al., 2012 ), increasing the risk of knowledge loss and inhibiting the creativity of individuals and teams (Cerne et al., 2014 ; Bogilović et al., 2017 ). Along this vein, it makes sense to solve the dilemma of insufficient knowledge sharing through the elimination of knowledge hiding, facilitating knowledge conversion within organizations. As a result, based on a descriptive analysis, bibliometric analysis, and content analysis, we conduct an in-depth analysis of knowledge hiding publications in international Science Citation Index (SCI) and Social Science Citation Index (SSCI) journals. We aim to address these research questions:
- What is the current publication trend in knowledge hiding?
- Which themes involving knowledge hiding have been studied by scholars?
- What are the areas involving knowledge hiding that seem to require future research?
Previous authors have conducted reviews on knowledge hiding (e.g., Xiao and Cooke, 2019 ; Anand et al., 2020 ; de Garcia et al., 2020 ), which are valuable. However, the review of Xiao and Cooke ( 2019 ) is based on 52 articles and all of which are written in English or Chinese, and published over the period 1997–2017. Similarly, the review of Anand et al. ( 2020 ) is drawing on 52 studies. In their work, de Garcia et al. ( 2020 ) have reviewed a total of 57 articles that are published up to April 2018, and their study focuses on distinguishing knowledge hiding and knowledge hoarding from knowledge collection and donation perspectives. Our review differs from these previous works in terms of volume, timeframe, method and the analysis. First, we have combined bibliometric analysis, content analysis and descriptive analysis in this review, which allows for incorporating rich data with less interpretative or subjectivity biases. In contrast to previous reviews, we further overview the concepts and dimensions, antecedents, consequences, theoretical foundations, and influence mechanisms of knowledge hiding. In the meantime, we have included bigger volume of articles in this review. In so doing, we are able to complement the previous reviews, offering a more objective account of evolution of this research topic.
Methodology
Our study has followed the systematic review process (Pickering and Byrne, 2014 ). Within this process, we employ the principles of Tranfield et al. ( 2003 ), which include (1) setting the scope, (2) conducting the search and data extraction, (3) selecting the studies and analyzing the data, and (4) extracting data and reporting the findings. To ensure the data validity and reliability, we limited our databases by searching the sample of English-written articles from the Web of Science over the period between 1995 and 2020. Further, the main reason for using SCI and SSCI databases is that web of science is “generally considered credible among the scientific community, and [are] commonly used by researchers from a wide range of fields (de Garcia et al., 2020 , p. 4). Several reviews have used these databases (e.g., Bernatović et al., 2021 ; Vlačić et al., 2021 ).
Retrieval conditions were “Title = knowledge hiding” or “Title = knowledge withholding,” and the time span was “All years (1950–2020).” The database was “Web of Science Core Collection” and the search basis was “Web of Science Category = Unrestricted Category.” In total, we obtained a sample of 233 articles. Subsequent analysis of these 233 articles' abstracts was conducted. In order to ensure data accuracy, we carefully selected studies that fit the definition given by Connelly et al. ( 2012 ) and excluded those that belonged to disciplines such as information management. This yielded 81 articles related to knowledge hiding. For these 81 articles, we undertook the reading of full texts, using Excel to record the key findings, theoretical lens, and methodologies. Building upon the content extraction, the authors classified the core clusters in five main themes according to their characteristics: concept and dimensions, antecedents, consequences, theoretical frameworks, and influence mechanism. Figure 1 shows the flow diagram of analysis.

Flow diagram.
Analysis and Findings
Publication by year.
The analysis of the number of publications per year on knowledge hiding in international journals (see Figure 2 ) shows that scholars started to systematically study knowledge hiding as an organizational behavior in the 2010s. A growing number of studies have addressed knowledge hiding but it dates back only to 2012, when knowledge hiding was first proposed as an independent concept in the work of Connelly et al. ( 2012 ). Knowledge hiding research has gone through two periods: the initial stage (from 2012 to 2018) and the fast development stage (from 2019 to 2020). During the initial stage, publications on knowledge hiding in mainstream international journals were rare, and there were only between one and five articles published per year. Since 2019, there has been a sharp increase in knowledge hiding publications; the number of publications has jumped to more than 30 articles per year (see Figure 2 ).

Annual distribution of articles on knowledge hiding.
Journal Distribution of Knowledge Hiding Research
From 2012 to 2020, research on knowledge hiding has been published in 43 SCI/SSCI journals (see Table 1 ), with 40 articles (49.38%) published in Journal Citation Reports (JCR) Q1 journals, 19 articles (23.46%) published in JCR Q2 journals, 8 articles (9.88%) published in JCR Q3 journals, and 11 articles (13.58%) published in JCR Q4 journals; 15 articles (18.52%) published in the Chartered Association of Business Schools (ABS3) journals, 10 articles (12.35%) published in ABS4 journals, one article (1.23%) published in Financial Times (FT50) journals; and one article (1.23%) published each in UT Dallas top 100 business school research rankings (UTD24) and ABS4 * journals. The top 10 journals that published most of the knowledge hiding articles are Journal of Knowledge Management, Journal of Organizational Behavior, Management Decision, International Journal of Hospitality Management, European Journal of Work and Organizational Psychology, Knowledge Management Research and Practice, International Journal of Information Management, Asian Business and Management, Leadership and Organization Development Journal , and Journal of Managerial Psychology . The majority of knowledge hiding research has been published in JCR Q1/Q2 journals, and a considerable proportion has been published in ABS3/4 journals.
Top publishing journals on knowledge hiding.
| . | |||
|---|---|---|---|
| 1 | Journal of Knowledge Management | IF: 4.745, JCR Q1 | 17 |
| 2 | Journal of Organizational Behavior | IF: 5.026, JCR Q1, ABS 4 | 7 |
| 3 | Management Decision | IF: 2.723, JCR Q2 | 4 |
| 4 | International Journal of Hospitality Management | IF: 6.701, JCR Q1, ABS 3 | 3 |
| 5 | European Journal of Work and Organizational Psychology | IF: 2.882, JCR Q2, ABS 3 | 3 |
| 6 | Knowledge Management Research & Practice | IF: 1.583, JCR Q4 | 3 |
| 7 | International Journal of Information Management | IF: 8.210, JCR Q1 | 2 |
| 8 | Asian Business & Management | IF: 2.192, JCR Q3 | 2 |
| 9 | Leadership & Organization Development Journal | IF: 1.977, JCR Q3 | 2 |
| 10 | Journal of Managerial Psychology | IF: 1.380, JCR Q4, ABS 3 | 2 |
| 11 | Academy of Management Journal | IF: 7.571, JCR Q1, UTD 24, ABS 4 | 1 |
| 12 | International Journal of Project Management | IF: 6.620, JCR Q1 | 1 |
| 13 | Computers in Human Behavior | IF: 5.003, JCR Q1, ABS 3 | 1 |
| 14 | Journal of Business Research | IF: 4.874, JCR Q1, ABS 3 | 1 |
| 15 | Decision Support Systems | IF: 4.721, JCR Q1, ABS 3 | 1 |
| 16 | Industrial Marketing Management | IF: 4.695, JCR Q1, ABS 3 | 1 |
| 17 | Journal of Business Ethics | IF: 4.141, JCR Q1, FT 50, ABS 3 | 1 |
| 18 | Telematics and Informatics | IF: 4.139, JCR Q1 | 1 |
| 19 | Academy of Management Learning & Education | IF: 4.058, JCR Q1, ABS 4 | 1 |
| 20 | Human Resource Management Journal | IF: 3.816, JCR Q1, ABS 4 | 1 |
| 21 | Higher Education | IF: 2.856, JCR Q1 | 1 |
| 22 | International Entrepreneurship and Management Journal | IF: 3.472, JCR Q2 | 1 |
| 23 | Applied Psychology: An International Review | IF: 2.808, JCR Q2, ABS 3 | 1 |
| 24 | International Journal of Environmental Research and Public Health | IF: 2.849, JCR Q2 | 1 |
| 25 | Journal of Occupational and Organizational Psychology | IF: 2.652, JCR Q2, ABS 4 | 1 |
| 26 | Sustainability | IF: 2.576, JCR Q2 | 1 |
| 27 | Project Management Journal | IF: 2.506, JCR Q2 | 1 |
| 28 | Journal of the Association for Information Science and Technology | IF: 2.410, JCR Q2 | 1 |
| 29 | Personality and Individual Differences | IF: 2.311, JCR Q2, ABS 3 | 1 |
| 30 | Frontiers in Psychology | IF: 2.067, JCR Q2 | 1 |
| 31 | Interactive Learning Environments | IF: 1.938, JCR Q2 | 1 |
| 32 | International Journal of Conflict Management | IF: 1.806, JCR Q2 | 1 |
| 33 | The Journal of Psychology | IF: 1.548, JCR Q2 | 1 |
| 34 | Basic & Clinical Pharmacology & Toxicology | IF: 2.651, JCR Q3 | 1 |
| 35 | The Service Industries Journal | IF: 2.381, JCR Q3 | 1 |
| 36 | Asia Pacific Journal of Human Resources | IF: 1.894, JCR Q3 | 1 |
| 37 | Baltic Journal of Management | IF: 1.719, JCR Q3 | 1 |
| 38 | Journal of Nursing Management | IF: 2.243, JCR Q4 | 1 |
| 39 | Negotiation and Conflict Management Research | IF: 1.027, JCR Q4 | 1 |
| 40 | International Journal of Emerging Markets | IF: 1.022, JCR Q4 | 1 |
| 41 | Journal of Organizational Change Management | IF: 0.967, JCR Q4 | 1 |
| 42 | Sage Open | IF: 0.715, JCR Q4 | 1 |
| 43 | Social Behavior and Personality | IF: 0.676, JCR Q4 | 1 |
Publishing Activity by Authors, Authors' Institutions, and Locations
Knowledge hiding has attracted considerable attention from researchers and practitioners. As shown in Table 2 , Matej Cerne published the most articles (eight) on knowledge hiding followed by Škerlavaj and Connelly, with seven and six articles respectively. The most active institutions in the research field of knowledge hiding were University of Ljubljana (eight publications), followed by BI Norwegian Business School, McMaster University and Tongji University, each with seven publications. Table 3 lists the locations of authors' institutions, with the top four being China, Pakistan, Canada and United Arab Emirates.
Top publishing authors and institutions on knowledge hiding.
| Matej Cerne | 8 | University of Ljubljana | 8 |
| Miha Škerlavaj | 7 | BI Norwegian Business School | 7 |
| Catherine E. Connelly | 6 | McMaster University | 7 |
| Anders Dysvik | 5 | Tongji University | 7 |
| Jinlian Luo | 5 | United Arab Emirates University | 6 |
| Abdul Karim Khan | 4 | Shanghai University | 5 |
| Atif Saleem Butt | 4 | American University of Ras Al Khaimah | 4 |
| Hongdan Zhao | 4 | University of International Business and Economics | 4 |
| Muhammad Usman | 4 | University of Science and Technology of China | 4 |
| Usman Ghani | 4 | Zhejiang University | 4 |
| Ghulam Ali Arain | 3 | Brock University | 3 |
| Qing Xia | 3 | COMSATS University Islamabad | 3 |
| Sadia Jahanzeb | 3 | International Islamic University | 3 |
| Tasneem Fatima | 3 | Memorial University of Newfoundland | 3 |
| Xuesong Zhai | 3 | Tamkang University | 3 |
| Wuhan University | 3 |
Publishing activity by authors' institution location.
| China | 40 |
| Pakistan | 16 |
| Canada | 11 |
| United Arab Emirates | 11 |
| Slovenia | 8 |
| United States | 7 |
| Norway | 7 |
| Taiwan | 6 |
| Australia | 5 |
| Singapore | 4 |
| United Kingdom | 3 |
| Croatia | 2 |
| Turkey | 2 |
| India | 2 |
| Finland | 2 |
| Germany | 2 |
| Saudi Arabia | 2 |
| Italy | 2 |
| France | 2 |
| Iraq | 2 |
| Indonesia | 1 |
| Spain | 1 |
| Cyprus | 1 |
| Portugal | 1 |
| Austria | 1 |
| Switzerland | 1 |
| Brazil | 1 |
Publishing Activity by Data Sources
Our analysis shows that previous data on knowledge hiding have tended to be collected in one single location, such as China, Pakistan, United Arab Emirates, Saudi Arabia, United States, and so on (see Table 4 ). Eight publications used data that were collected from multi-countries and regions (e.g., North America, Germany and Austria, Europe, Slovenia, Croatia, Serbia, Bosnia and Herzegovina, Montenegro and Macedonia). The top three locations from which researchers have collected knowledge hiding data were China (29 publications), Pakistan (13 publications) and United Arab Emirates (5 publications).
Locations from which researchers have collected knowledge hiding data.
| China | 29 |
| Pakistan | 13 |
| Multi-countries and regions | 8 |
| United Arab Emirates | 5 |
| Literature review | 4 |
| Saudi Arabia | 3 |
| United States | 3 |
| Finland | 2 |
| India | 2 |
| Slovenia | 2 |
| Myanmar | 2 |
| Taiwan | 2 |
| Turkey | 2 |
| Canada | 1 |
| Indonesia | 1 |
| Jordan | 1 |
| One European Union member state | 1 |
| Total | 81 |
Highly Cited Publications
Citations can show the research focus of scholars and reveal their main theoretical lens. Highly cited articles are often regarded as important references in the field. Table 5 presents the top 15 highly cited publications on knowledge hiding.
Top 15 articles on knowledge hiding by the number of citations.
| . | |||||
|---|---|---|---|---|---|
| 1 | Understanding counterproductive knowledge behavior: Antecedents and consequences of intra-organizational knowledge hiding | 2016 | Serenko and Bontis | 81 | Yes |
| 2 | Evasive knowledge hiding in academia: When competitive individuals are asked to collaborate | 2019 | Hernaus, Cerne, Connelly, Vokic and Š-kerlavaj | 24 | Yes |
| 3 | Territoriality, task performance, and workplace deviance: Empirical evidence on role of knowledge hiding | 2019 | Singh | 27 | Yes |
| 4 | Perceptions of organizational politics, knowledge hiding, and employee creativity: The moderating role of professional commitment | 2019 | Malik, Shahzad, Raziq, Khan, Yusaf and Khan | 19 | Yes |
| 5 | Knowledge hiding in organizations | 2012 | Connelly, Zweig, Webster and Trougakos | 455 | No |
| 6 | What goes around comes around: Knowledge hiding, perceived motivational climate, and creativity | 2014 | Cerne, Nerstad, Dysvik and Škerlavaj | 95 | No |
| 7 | Why and when do people hide knowledge? | 2013 | Peng | 94 | No |
| 8 | How perpetrators and targets construe knowledge hiding in organizations | 2015 | Connelly and Zweig | 89 | No |
| 9 | Workplace ostracism and knowledge hiding in service organizations | 2016 | Zhao, Xia, He, Sheard and Wan | 54 | No |
| 10 | Antecedents and intervention mechanisms: A multi-level study of R&D team's knowledge hiding behavior | 2016 | Huo, Cai, Luo, Men and Jia | 48 | No |
| 11 | Hiding behind a mask? Cultural intelligence, knowledge hiding, and individual and team creativity | 2017 | Bogilović, Cerne and Škerlavaj | 42 | No |
| 12 | The role of multilevel synergistic interplay among team mastery climate, knowledge hiding, and job characteristics in stimulating innovative work behavior | 2017 | Cerne, Hernaus, Dysvik and Škerlavaj | 56 | No |
| 13 | Tell me if you can: Time pressure, prosocial motivation, perspective taking, and knowledge hiding | 2018 | Škerlavaj, Connelly, Cerne and Dysvik | 32 | No |
| 14 | Knowledge hiding and team creativity: The contingent role of task interdependence | 2018 | Fong, Men, Luo and Jia | 30 | No |
| 15 | When and how abusive supervision leads to knowledge hiding behaviors–An Islamic work ethics perspective | 2018 | Khalid, Bashir, Khan and Abbas | 28 | No |
Further, through a co-citation analysis, co-authorship analysis, keyword and co-occurrence analysis, and content analysis, we find that most research on knowledge hiding focuses on the concept and dimensions of the topic. For instance, as one of the highly cited publications, it is important to acknowledge that Connelly et al. ( 2012 ) take the lead in defining the concept of knowledge hiding and propose evasive hiding, playing dumb, and rationalized hiding as three dimensions of knowledge hiding. Based on the work of Connelly et al. ( 2012 ); Zhao et al. ( 2016 ) further examine the interpersonal antecedents of the three dimensions of knowledge hiding. Hernaus et al. ( 2019 ) distinguish the three dimensions of knowledge hiding and address how individual competitiveness may lead to knowledge hiding. Connelly and Zweig ( 2015 ) point out that the three dimensions of knowledge hiding are not equally and always harmful, where under certain circumstances, some knowledge hiding can be beneficial. Among the highly cited publications, scholars also focus on the antecedents of knowledge hiding, paying particular attention to workplace stressors, psychological ownership, and territoriality of knowledge. For example, Zhao et al. ( 2016 ); Škerlavaj et al. ( 2018 ), and Khalid et al. ( 2018 ) have examined the influence mechanisms of workplace stressors, such as workplace ostracism, abusive supervision, and interpersonal injustice, on knowledge hiding. Peng ( 2013 ); Huo et al. ( 2016 ), and Singh ( 2019 ) emphasize the predictive effect of psychological ownership and territoriality of knowledge on knowledge hiding. Serenko and Bontis ( 2016 ); Hernaus et al. ( 2019 ), and Malik et al. ( 2019 ) also investigate the antecedents of knowledge hiding with different focuses (e.g., intra-organizational knowledge hiding, the individual-level and job-related factors within academia, organizational politics). These studies represent the two most important research directions of knowledge hiding.
Following, among the highly cited publications, we find that individual and team creativity, interpersonal relationships, and retaliation show the key consequences of knowledge hiding. The main contributions in the field include the work of Cerne et al. ( 2014 ), who point out that “when employees hide knowledge, they trigger a reciprocal distrust loop in which coworkers are unwilling to share knowledge with them” (p. 172). In recent years, Connelly and Zweig ( 2015 ), and Serenko and Bontis ( 2016 ) also prove that knowledge hiding can lead to retaliation. Cerne et al. ( 2017 ) and Malik et al. ( 2019 ) examine the destructive effect of knowledge hiding on individual creativity. Bogilović et al. ( 2017 ) and Fong et al. ( 2018 ) analyze the impacts of individual-level knowledge hiding on team-level creativity. These studies represent the mainstream consequences of knowledge hiding.
Additionally, we identify that the research focus on knowledge hiding has moved from the individual level to a multilevel influence mechanism. For example, Huo et al. ( 2016 ); Cerne et al. ( 2017 ); Fong et al. ( 2018 ), and Hernaus et al. ( 2019 ) explore the moderating effect of team-level task interdependence on the relationship between individual-level variables and knowledge hiding. In addition, team-level cultural factors (e.g., mastery climate, workplace ethics) and organizational justice are variables that scholars have examined when exploring the multilevel influence mechanism of knowledge hiding (Huo et al., 2016 ; Cerne et al., 2017 ; Khalid et al., 2018 ).
Major Research Clusters and Topics
Using CiteSpace4.0 software, we conducted the descriptive analysis, bibliometric analysis, and content analysis of the 81 knowledge hiding articles that are published in the international journals from 2012 to 2020. In order to clearly demonstrate the current status of knowledge hiding research, we structure our findings into the following five clusters (see Figure 3 ).

Research framework of knowledge hiding. Source: extended and developed from Connelly et al. ( 2012 ) and Xiao and Cooke ( 2019 ).
Concept and Dimensions
The bibliometric analysis suggests that keywords related to the concept of knowledge hiding include knowledge sharing, knowledge withholding, and knowledge management process. Based on these keywords and the results of our content analysis, we extract “concept and dimensions” as the first cluster that reflects the research interests in knowledge hiding.
The concept of knowledge hiding was first defined as the act of deliberately not providing knowledge or providing knowledge that is not what the seeker needs when facing a colleague's request (Connelly et al., 2012 ). These were the first authors to discuss the linkages and differences between knowledge hiding and related concepts, such as knowledge sharing/non-sharing (Anand et al., 2020 ), knowledge withholding (Webster et al., 2008 ), knowledge hoarding (Xiao and Cooke, 2019 ; de Garcia et al., 2020 ), counterproductive/deviant behavior (Connelly and Zweig, 2015 ; Serenko and Bontis, 2016 ), workplace deception (Connelly et al., 2012 ), and incivility (Zhao et al., 2016 ). Later, scholars further proposed concepts such as knowledge sharing hostility (Stenius et al., 2016 ), disengagement from knowledge sharing (Zhao et al., 2016 ), knowledge contribution loafing (Fang, 2017 ), and knowledge manipulation (Bogilović et al., 2017 ). In recent years, scholars have tried to differentiate knowledge hiding from other related concepts (e.g., employee silence and knowledge protection) (Bari et al., 2020 ).
In order to distinguish these different concepts, we compare relevant concepts through questioning whether knowledge seeking exists, the degree of knowledge sharing, and the intentionality of the behavior (see Figure 4 ). In general, scholars have widely accepted the definition of knowledge hiding given by Connelly et al. ( 2012 ). The mainstream view believes that knowledge hiding is an important aspect of knowledge withholding, and it is not the opposite of knowledge sharing (Connelly et al., 2012 ; Serenko and Bontis, 2016 ; Zhao et al., 2016 ). Consequently, one cannot simply equate knowledge hiding with non-sharing or a lack of knowledge sharing. In addition to subjective intention, the reasons that individuals do not share knowledge with others can be related to a lack of relevant knowledge or the inability to share the knowledge. It is worth pointing out that there are different opinions in boundaries between knowledge hiding and concepts such as knowledge non-sharing, counterproductive knowledge behavior, and knowledge protection. Hence, there still exists some confusion and cross-use of related concepts in the knowledge hiding research. In addition, the existing literature has seldom defined knowledge hiding from the indigenous/cross-cultural perspective.

Comparison between knowledge hiding and related concepts. Source: extended and developed from Connelly et al. ( 2012 ) and de Garcia et al. ( 2020 ).
Connelly et al. ( 2012 ) have developed three dimensions of knowledge hiding and an employee self-evaluation scale with 12 items, with each dimension measuring four items. Among them, evasive hiding means that the hider provides invalid knowledge or pretends to agree to help, but lacks follow-up action. An example item is “I agreed to help him/her but never really intended to.” Playing dumb refers to pretending to be ignorant of the relevant knowledge or not understanding the knowledge seeker's question, with a sample item “I pretended I did not know what he/she was talking about.” Rationalized hiding means that the hider explains the reasons for not providing required knowledge, such as the necessity to keep it confidential or offering that knowledge sharing is not allowed by the superiors. An example item is “I explained that the information is confidential and available only to people on a particular project.” Most scholars believe that rationalized hiding is different in nature from evasive hiding and playing dumb, because rationalized hiding does not involve deception, but the evasive hiding and playing dumb do have a high degree of deception.
The scale of Connelly et al. ( 2012 ) has been proved to have high reliability and validity in a series of empirical studies. In general, scholars use this scale and its original items directly, making some contextual adaptation of expressions only according to the particular research needs. There are other knowledge hiding scales, such as Peng's (Peng, 2013 ) three-item counterproductive knowledge behavior scale and knowledge withholding behavior scales developed by Lin and Huang ( 2010 ); Tsay et al. ( 2014 ), and Serenko and Bontis ( 2016 ). Anand et al. ( 2020 ) have advocated that knowledge hiding is composed of unintentional hiding (driven by contingent situation), motivational hiding (driven by performance and competition), controlled hiding (driven by psychological ownership), victimized hiding (driven by hostility and abuse), and favored hiding (driven by identity and norms). Jha and Varkkey ( 2018 ) identify the four strategies adopted by supervisors to hide knowledge from subordinates, namely, playing innocent, misleading, rationalized hiding, and counter-questioning.
Antecedents
The antecedents of knowledge hiding include the Big Five personality traits, abusive supervision, negative workplace gossip, and career insecurity. Combined with the research framework of knowledge hiding (see Figure 3 ), the second cluster as antecedents is popular among scholars. Inspired by the work of Connelly et al. ( 2012 ) and Xiao and Cooke ( 2019 ), we review knowledge hiding antecedents from four aspects: knowledge characteristics, individual factors, team and interpersonal factors, and organizational factors.
Knowledge characteristic is one of the first antecedents popular among scholars. Due to the complex nature of knowledge, Connelly et al. ( 2012 ) point out that such complexity affects the willingness of individuals to provide help when facing colleagues' knowledge requests. Simply, it often requires more time and energy to generate complex knowledge that knowledge owners tend to keep the knowledge for themselves. Hernaus et al. ( 2019 ) argue that people are more likely to hide tacit knowledge rather than explicit knowledge. In addition, the task relevance and the value of knowledge have a positive relation with knowledge hiding (Connelly et al., 2012 ; Huo et al., 2016 ).
Individual factors mainly include personality traits and psychological factors such as emotion and cognition. In terms of personality traits, scholars focus mainly on the influence of the Big Five personality traits, in particular neuroticism. For example, Pan and Zhang ( 2018 ) reveal that employees with high conscientiousness and low neuroticism are less likely to hide knowledge, while people with high neuroticism are more likely to hide knowledge (Anaza and Nowlin, 2017 ). Pan et al. ( 2018 ) verify the effects of a “dark triad of personality” (Machiavellianism, narcissism, and psychopathy) on different dimensions of knowledge hiding. Fang ( 2017 ) and Aljawarneh and Atan ( 2018 ) examine the relationship between anxiety and knowledge hiding and the relationship between cynicism and knowledge hiding.
When it comes to the cognitive perception, prior research has focused mainly on the individual's self-efficacy, territoriality and psychological ownership, psychological safety, psychological contract breach, perceived pressure or job insecurity, perceived workplace status, and career prospects. Tsay et al. ( 2014 ); Jha and Varkkey ( 2018 ), and Hernaus et al. ( 2019 ) argue that individuals' confidence in their knowledge and perception of their competitiveness affect their willingness to share knowledge. Peng ( 2013 ); Huo et al. ( 2016 ); Kang ( 2016 ); Singh ( 2019 ); Khalid et al. ( 2020 ), and Zhai et al. ( 2020 ) believe individuals' perceived exclusivity of knowledge, knowledge power, and knowledge privacy are the primary factors that determine how much knowledge they are willing to share with colleagues. He et al. ( 2020 ); Lin et al. ( 2020 ), and Wu ( 2020 ) explore the formation mechanism of knowledge hiding from the perspectives of psychological safety and perceived threats. Pradhan et al. ( 2019 ); Ghani et al. ( 2020a ), and Jahanzeb et al. ( 2020a ) emphasize the negative impacts of employee psychological contract breaches on knowledge sharing in the organizations. Jha and Varkkey ( 2018 ); Škerlavaj et al. ( 2018 ), and Feng and Wang ( 2019 ) examine the impacts of workplace stressors, such as time pressure and job insecurity, on knowledge hiding.
Prior studies have also investigated knowledge hiding from employee and supervisor perspectives. In their work, Butt ( 2019 ) and Butt and Ahmad ( 2019 ) show that concerns about career prospects are important individual-level reasons for supervisors to hide knowledge from subordinates. Liu et al. ( 2020 ) find that perceived workplace status affects knowledge hiding through two opposing mechanisms: perception of knowledge sharing obligation and perception of being envied. The goal orientation has also attracted some scholars' attention in recent years when studying knowledge hiding behavior. Research by Zhu et al. ( 2019 ) shows that performance-driven goal orientation has a positive relationship with employees' knowledge hiding behaviors, which allows employees to achieve the competitive goal of surpassing colleagues. Nadeem et al. ( 2021 ) argue that shared goals are negatively related to knowledge hiding. Moh'd et al. ( 2021 ) analyze the relationship between achievement goal orientation (e.g., learning goals, performance display/performance-avoidance goal orientation) and knowledge hiding. Some scholars highlight that individual motivational factors (such as expected results/rewards and perceived knowledge sharing costs) affect knowledge hiding (Lin and Huang, 2010 ; Shen et al., 2019 ). Although emotion and cognition have been regarded as the two core elements that drive individual behavior (e.g., Lee and Allen, 2002 ), studies on how emotional/affective factors influence knowledge hiding are still underdeveloped. We believe only Zhao and Xia ( 2019 ) have studied the negative emotional state of nursing staff as the antecedent of their knowledge hiding behavior.
Team-level and interpersonal factors reflect leadership, interpersonal relationships, and their respective interactions. When considering leadership, scholars pay the most attention to abusive leadership, followed by ethical leadership. Khalid et al. ( 2018 ) point out that knowledge hiding is not necessarily an employee's intention to directly harm other organization members, but a negative reaction of employees to abusive supervision. Further, as indicated by displaced aggression theory, when employees encounter abusive leaders, they are more likely to retaliate by targeting innocent victims, namely, their colleagues but not the leaders. Based on the reactance theory, Feng and Wang ( 2019 ) point out that when employees experience frustration resulting from the abuse of their supervisors, they will take revenge in a direct or indirect way so that they can maintain a sense of freedom. However, because of their supervisors' supreme power and status in organizations, employees usually do not directly retaliate against supervisors so as not to cause stronger hostility and reciprocal retaliation. Ethical leadership can also influence employees' behavior intentionally or unintentionally through the role model effect. Abdullah et al. ( 2019 ); Anser et al. ( 2020 ), and Men et al. ( 2020 ) argue a significant but negative correlation between ethical leadership and subordinates' knowledge hiding behavior. Interestingly, the study by Xia et al. ( 2019 ) describes an inverted U–shaped curve relationship between knowledge leadership and employee knowledge hiding. Through a multilevel model, Lin et al. ( 2020 ) find that individual-focused empowering leadership can improve the supervisor-subordinate relationship and therefore inhibit knowledge hiding, whereas differentiated empowering leadership can cause group relational conflict and then lead to knowledge hiding. Based on social exchange theories, Abdillah et al. ( 2020 ) argue that altruistic leaders' humility, patience, understanding, sympathy, and compassion will be perceived by employees as uniquely socio-emotional resources, which can enhance the positive emotion of employees, improve the quality of the exchange between supervisors and subordinates (obtaining the trust and respect of the subordinates), and encourage employees be willing to make extra efforts for the organization and eliminate selfish behaviors that harm the interests of the organization, thus effectively preventing employee knowledge hiding behaviors.
From the perspective of interpersonal abuse, prior research shows that employees who encounter interpersonal unfair treatment are less willing to share their personal knowledge assets with others (Abubakar et al., 2019 ), whereas fair interpersonal interaction is significantly negatively correlated with the three dimensions of knowledge hiding (Ghani et al., 2020b ). Among these, the factor of passive-aggressiveness in the workplace attracts more attention from scholars. Aljawarneh and Atan ( 2018 ) find that incivility in the workplace can drive employees to feel cynical and thus hide knowledge as a countermeasure. Zhao et al. ( 2016 ) and Riaz et al. ( 2019 ) point out that, as a typical workplace passive-aggressiveness, workplace ostracism would significantly increase employees' deceptive knowledge hiding (e.g., evasive hiding and playing dumb). Similarly, research by Yao et al. ( 2020a , b ) shows that negative interpersonal experiences, such as workplace bullying and negative workplace gossip, accelerate the exhaustion of employee resources, such as emotions, time, energy, and organizational identity, leading them to hide knowledge. Anand et al. ( 2020 ) also find that hostility and abusive colleagues/supervisors drive employees to hide knowledge.
Concerning the impacts of interpersonal relationship on knowledge hiding, current research has focused on exploring the effects of supervisor-subordinate relationships. Scholars first divide supervisor-subordinate relationships into formal work-related relationships (contractual relationship, Leader-Member Exchange) and informal non-work-related relationships (Chinese personal guanxi relationships, Supervisor-Subordinate Guanxi) (He et al., 2020 ), or into economic LMX and social LMX (Babič et al., 2019 ), and then explore their impacts on employees' knowledge hiding behaviors. Previous research reveals that LMX negatively affects evasive hiding and playing dumb (Zhao et al., 2019 ). However, this reciprocal social exchange is more likely to reduce the level of knowledge hiding within the team, especially when the relationship between individuals and their supervisors has social LMX characteristics (Cerne et al., 2014 ). Furthermore, upward LMX social comparison leads to envy among team members, so it is a potential interpersonal antecedent of knowledge hiding among colleagues (Weng et al., 2020 ). It is worth noting that team prosocial motivation and social LMX (but not economic LMX) have an interaction effect on knowledge hiding (Babič et al., 2019 ). Lin and Huang ( 2010 ); Butt ( 2019 ); Butt and Ahmad ( 2019 ); Semerci ( 2019 ) examine the influences of interpersonal factors such as trust, reciprocity, relationship recognition, lack of interpersonal relationship, relationship conflict, and interpersonal competition. Interestingly, Lin and Huang ( 2010 ) point out that emotional bonds such as trust and reciprocity among team members can make individuals give up hiding too much knowledge to avoid retaliation from others. In addition, task conflicts and relationship conflicts have additive effects on knowledge hiding (Semerci, 2019 ).
At the organizational level, scholars have explored the roles of organizational culture, knowledge management policies and systems, organizational politics, organizational justice, organizational recognition, and a competitive performance environment on employees' conduct of knowledge hiding. First, the knowledge sharing culture has been proved to be closely related to the extent to which the knowledge hiding behavior can be accepted and adopted by the members of the organization (Connelly et al., 2012 ). For example, Anaza and Nowlin ( 2017 ) point out that the lack of incentives for knowledge sharing and the lack of supervisor feedback on subordinates' knowledge sharing will lead employees to hide knowledge. Jha and Varkkey ( 2018 ) highlight that a lack of organizational recognition of knowledge sharing and workload increase due to knowledge sharing increase employee knowledge hiding.
Social norms, organization policies, and management systems have also been found to have a profound impact on employees' tendency to hide knowledge. For instance, Butt and Ahmad ( 2019 ) argue that knowledge hiding is deeply embedded in many local companies and is regarded as a common code of conduct in the United Arab Emirates. Serenko and Bontis ( 2016 ) find that organizational knowledge management systems and policies have a significant direct impact on employee knowledge hiding, whereas injustice prompts employees to spontaneously engage in knowledge hiding behavior. Malik et al. ( 2019 ) propose that perceived organizational politics positively predict knowledge hiding. Abubakar et al. ( 2019 ) find that distributional, procedural, and interactional injustice increase the level of knowledge hiding among employees. Research by Jahanzeb et al. ( 2020b ) confirms that employees who encounter organizational unfairness consider knowledge hiding as a means to rationalize the cognitive separation between oneself and the organization in order to maintain one's dignity. Finally, some scholars have examined the impact of a competitive working environment. For example, Anaza and Nowlin ( 2017 ) explain how internal competition can lead to knowledge hiding. Similar findings can be found in the work of Anand et al. ( 2020 ), who argue that organizational internal performance and competitive factors drive employees to hide knowledge.
Consequences
Based on the highly cited publications and the keyword analysis, we find that consequences, performance, behavior , and employee/team creativity are some keywords that reflect the outcome of knowledge hiding. Therefore, we use the term consequences to summarize the third cluster concerning the knowledge hiding research.
Current research focuses mainly on the individual- and team-level consequences of knowledge hiding. A small number of studies examine the individual-level consequences of knowledge hiding between supervisors and subordinates. In terms of individual-level results, the existing research has examined the effects of knowledge hiding on individual job performance, psychological status and attitude, workplace behavior, and supervisor-subordinate/coworker relationships. For instance, most studies have found that knowledge hiding among colleagues and between supervisors and subordinates can reduce task performance, organizational citizenship behavior (OCB), and creativity (Connelly et al., 2012 ; Cerne et al., 2014 ; Arain et al., 2019 , 2020a , b ; Jahanzeb et al., 2019 ; Malik et al., 2019 ; Singh, 2019 ; Zhu et al., 2019 ).
However, there are some mixing findings. For example, Wang et al. ( 2019 ) argue that perceived colleague knowledge hiding does not reduce the performance of salespersons. Instead, it encourages them to work harder to improve their sales performance. Burmeister et al. ( 2019 ) find that knowledge hiding (playing dumb, in contrast to evasive hiding and rationalized hiding) has opposite effects on OCB, and knowledge hiders experience different emotions. Khoreva and Wechtler ( 2020 ) point out that evasive hiding is negatively related to in-role performance, and playing dumb is positively related to it. In addition, both evasive hiding and rationalized hiding will hinder innovation performance. Regarding psychological status and attitudes, research suggests that knowledge hiding increases employees' moral disengagement (Arain et al., 2020a ) and decreases their psychological safety, well-being, job satisfaction, and sense of thriving (Jiang et al., 2019 ; Offergelt et al., 2019 ; Khoreva and Wechtler, 2020 ). Furthermore, knowledge hiding can trigger knowledge seekers' deviant behaviors, turnover intention, upward silence, and non-engagement in knowledge sharing (Connelly and Zweig, 2015 ; Offergelt et al., 2019 ; Singh, 2019 ; Arain et al., 2020a ).
Concerning interpersonal relationships, studies reveal that knowledge hiding among colleagues or between supervisors and subordinates can damage workplace relationships, which can even lead to a trust crisis (Connelly et al., 2012 ; Cerne et al., 2014 ; Arain et al., 2020b ). In particular, Connelly et al. ( 2012 ), Cerne et al. ( 2014 ), and Connelly and Zweig ( 2015 ) highlight that knowledge hiding can result in a vicious circle of rejecting knowledge sharing. Studies also find that knowledge hiding has significant negative effects on team performance (Zhang and Min, 2019 ), team creativity (Fong et al., 2018 ; Bari et al., 2019 ), team viability (Wang et al., 2019 ), team learning, and absorptive capability (Fong et al., 2018 ; Zhang and Min, 2019 ).
In summary, scholars have made advancements on the impacts of knowledge hiding on the individual level, but research on its impacts on team and organizational levels is still at a nascent stage. Few scholars have recently analyzed the “boomerang effect” or “negative reinforcement cycle” of knowledge hiding—the impact of knowledge hiding on the hiders' psychological status, job performance, and creativity (e.g., Cerne et al., 2014 ; Jiang et al., 2019 )—and its double-edged sword effect (Wang et al., 2019 ), which has opened up a new avenue for research.
Theoretical Perspectives
The fourth cluster concentrates on theories that are popular among scholars that they use to conduct knowledge hiding research. The theories applied in the field of knowledge hiding are mainly from two domains—managerial theory and psychological theory—and include theories such as “exchange” (represented by social exchange theory), “resources” [represented by Conservation of Resources (COR) Theory], “learning” (represented by social learning theory), “cognition” (represented by social cognitive theory), “ownership” (represented by psychological ownership theory), “goal orientation” (represented by achievement goal theory), “personality traits,” “job characteristics,” social identity theory, displaced aggression theory, and justice theory (see Table 6 ). Although scholars have introduced other theories to study knowledge hiding, the effectiveness of this theoretical development needs to be enhanced. For example, how to theorize individual emotions has not yet been made systematic and thus needs to be further explored in future research. Furthermore, we find that theories that are mostly used to examine the motivation/antecedents of knowledge hiding or the direct/indirect (mediating) influence of antecedent variables on knowledge hiding are less used to illustrate the consequences of knowledge hiding and the boundary conditions.
Theoretical perspectives used in knowledge hiding research.
| Social exchange theory | Lin and Huang ( ), Connelly et al. ( ), Cerne et al. ( ), Tsay et al. ( ), Wang et al. ( ), Serenko and Bontis ( ); Bogilović et al. ( ), Fong et al. ( ), Khalid et al. ( ), Abdullah et al. ( ), Abubakar et al. ( ), Babič et al. ( ), Bari et al. ( ), Butt and Ahmad ( ), Jahanzeb et al. ( ), Pradhan et al. ( ), Semerci ( ), Singh ( ), Wang et al. ( ), Abdillah et al. ( ), Anand et al. ( ), He et al. ( ), Khalid et al. ( ), Lin et al. ( ), Ghani et al. ( ), Arain et al. ( ), and Nadeem et al. ( ) | √ | √ | √ | √ | √ |
| Norm of reciprocity | Zhao et al. ( ), Singh ( ), and Arain et al. ( ) | √ | √ | √ | √ | |
| Conservation of resources theory | Aljawarneh and Atan ( ), Škerlavaj et al. ( ), Feng and Wang ( ), Riaz et al. ( ), Semerci ( ), Anand et al. ( ), Anser et al. ( ), Jahanzeb et al. ( ), and Yao et al. ( , ) | √ | √ | √ | √ | √ |
| Job demands-resources model | Malik et al. ( ) | √ | √ | √ | ||
| Social learning theory | Abdullah et al. ( ), Arain et al. ( ), Butt and Ahmad ( ), Offergelt et al. ( ), Zhao and Xia ( ), Anand et al. ( ), Lin et al. ( ), Ghani et al. ( ) | √ | √ | √ | √ | √ |
| Organizational learning theory | Zhang and Min ( ) | √ | √ | |||
| Social cognitive theory | Lin and Huang ( ), Tsay et al. ( ), He et al. ( ), Arain et al. ( ), Ghani et al. ( ) | √ | √ | √ | √ | |
| Cognitive evaluation theory | Xia et al. ( ) | √ | √ | |||
| Self-perception theory | Jiang et al. ( ) | √ | √ | |||
| Moral disengagement theory | Zhao et al. ( ) | √ | √ | |||
| Psychological ownership theory | Peng ( ), Huo et al. ( ), Aljawarneh and Atan ( ), Abubakar et al. ( ), Singh ( ), and Anand et al. ( ) | √ | √ | √ | √ | |
| Territoriality theory | Peng ( ) and Huo et al. ( ) | √ | √ | |||
| Achievement goal theory | Cerne et al. ( ), Cerne et al. ( ), and Moh'd et al. ( ) | √ | √ | √ | √ | |
| Goal orientation theory | Zhu et al. ( ) | √ | √ | |||
| Personality traits theory | Wang et al. ( ) | √ | √ | |||
| Trait activation theory | Pan and Zhang ( ) | √ | √ | |||
| Cognitive-affective system theory of personality | Yao et al. ( , ) | √ | √ | |||
| Job characteristic theory | Cerne et al. ( ) and Zhang and Min ( ) | √ | √ | |||
| Job design theory | Moh'd et al. ( ) | √ | √ | |||
| Affect-as-information theory | Zhao and Xia ( ) | √ | √ | |||
| Moral emotion theory | Burmeister et al. ( ) | √ | √ | |||
| Displaced aggression theory | Khalid et al. ( ), Jahanzeb et al. ( ), Pradhan et al. ( ), and Ghani et al. ( ) | √ | √ | √ | ||
| Social identity theory | Wang et al. ( ), Butt and Ahmad ( ), Zhao et al. ( ), and Jahanzeb et al. ( ) | √ | √ | √ | ||
| Social comparison theory | Lin et al. ( ) and Weng et al. ( ) | √ | √ | √ | ||
| Social categorization theory | Bogilović et al. ( ) and Anand et al. ( ) | √ | √ | |||
| Social influence theory | Anand et al. ( ) | √ | ||||
| Justice theory | Pradhan et al. ( ) and Jahanzeb et al. ( ) | √ | √ | √ | ||
| Self-determination theory | Gagné et al. ( ) and Wang et al. ( ) | √ | √ | √ | √ | |
| Regulatory focus theory | Cerne et al. ( ) and Fang ( ) | √ | √ | √ | √ | |
| Theory of planned behavior | Butt and Ahmad ( ) | √ | √ | |||
| Theory of reasoned action | Wu ( ) | √ | √ | √ | ||
| Attribution theory | Khalid et al. ( ) | √ | √ | |||
| Protection motivation theory | Wu ( ) | √ | √ | √ | ||
| Psychological contract theory | Pan et al. ( ) | √ | √ | |||
| Reactance theory | Feng and Wang ( ) | √ | √ | |||
| Absorptive capacity theory | Fong et al. ( ) | √ | √ | |||
| Cooperation-competition theory | Hernaus et al. ( ) | √ | √ | √ | ||
| Status attainment theory | Liu et al. ( ) | √ | √ | √ | ||
| Agency theory | Khoreva and Wechtler ( ) | √ | √ | |||
| Stimulus-organism-response (SOR) paradigm | Zhai et al. ( ) | √ | √ | √ | ||
| Interdependence theory | Connelly et al. ( ) | √ | √ | |||
| Theory of basic values | Semerci ( ) | √ | √ | |||
| Broaden-and-build theory | Connelly and Zweig ( ) and Abdillah et al. ( ) | √ | √ | √ | ||
Influence Mechanisms
There are findings on the mediating roles of antecedent variables that affect knowledge hiding. Emotional and cognitive factors (e.g., leadership, workplace stressors, interpersonal relationships, personality traits, and psychological ownership) can induce knowledge hiding. In terms of leadership, Abdullah et al. ( 2019 ) point out that ethical leadership inhibits employees' knowledge hiding by enhancing their relational social capital. Anser et al. ( 2020 ) find that the ethical behavior of ethical leaders can enhance the perception of “meaningful work” for service industries employees, thereby reducing the possibility of engaging in knowledge hiding behaviors. Khalid et al. ( 2018 ) find that perception of interpersonal justice mediates the relationship between abusive supervision and knowledge hiding. Feng and Wang ( 2019 ) believe that abusive supervision indirectly affects knowledge hiding through job insecurity. Pradhan et al. ( 2019 ) show that psychological contract breaching and the attacks toward supervisors play a partial mediating role in the process in which abusive supervision affects knowledge hiding. Ghani et al. ( 2020a ) further point out that abusive supervision can easily lead to psychological contract breach, thus leading employees to attack their colleagues and deliberately hide knowledge from them. In addition, Lin et al. ( 2020 ) find that individual-focused empowering leadership enhances the psychological safety of subordinates, thereby reducing their knowledge hiding, whereas differentiated empowering leadership causes group relational conflicts, thereby increasing subordinate knowledge hiding. Abdillah et al. ( 2020 ) study the dual mediating mechanisms of altruistic leadership, which inhibits and prevents employees from knowledge hiding, pointing out that the positive emotions induced by altruistic leadership and LMX have important effects.
Regarding workplace stressors and interpersonal relationships, Aljawarneh and Atan ( 2018 ) find that cynicism mediates the relationship between tolerance of workplace incivility and knowledge hiding. Riaz et al. ( 2019 ) find that workplace ostracism has a significant impact on evasive hiding and playing dumb, and that work strain plays a mediating role. Yao et al. ( 2020a , b ) have shown that relational identification and interpersonal trust play a chain-mediating role in the relationship between negative workplace gossip and knowledge hiding. At the same time, emotional exhaustion and organizational identification play a chain-mediating role in the relationship between workplace bullying and knowledge hiding. Jahanzeb et al. ( 2020b ) believe that the experience of injustice causes employees to be psychologically separated from the organization and thus employees will show more knowledge hiding behaviors. Zhao et al. ( 2019 ) demonstrate that organizational identification mediates the negative impact of LMX on evasive hiding and playing dumb. Weng et al. ( 2020 ) point out that employees' upward LMX social comparison with their colleagues leads to envy of and knowledge hiding toward their colleagues. He et al. ( 2020 ) discover that psychological safety fully mediates the influence of LMX on knowledge hiding and partially mediates the influence of supervisor-subordinate guanxi on knowledge hiding.
Another aspect is shown through personality traits. Wang et al. ( 2014 ) find that perceived social identity mediates the relationship between the Big Five personality traits and knowledge hiding. Pan et al. ( 2018 ) examine the positive relationship between the “dark triad of personality” (Machiavellianism, narcissism, and psychopathy) and knowledge hiding, as well as the mediating effect of transactional psychological contracts on this relationship. Zhao and Xia ( 2019 ) point out that the negative affect states of nurses staff can “activate” their moral disengagement mechanism, allowing them to redefine their knowledge hiding behaviors as reasonable and acceptable, and thus exacerbating their knowledge hiding tendency. The final aspect is psychological ownership. Research by Peng ( 2013 ) and Huo et al. ( 2016 ) show that employees' psychological ownership of knowledge enhances their territorial awareness, which in turn causes them to hide knowledge from colleagues. Liu et al. ( 2020 ) confirm that the influence of workplace status on employee knowledge hiding is carried out through two opposite mechanisms: perceived knowledge sharing responsibility and envy. The former negatively mediates the relationship between the two, and the latter positively mediates it.
Some scholars have also studied the mediating effect of knowledge hiding. For instance, scholars examine the process through which knowledge hiding impairs individual or team creativity and innovation performance. Cerne et al. ( 2014 ) find that the knowledge hiding makes hiders reduce their own creativity, and colleague distrust plays a mediating role. Arain et al. ( 2019 ) show that supervisor knowledge hiding can reduce subordinates' self-efficacy and thus reduce their innovation. Khoreva and Wechtler ( 2020 ) point out that playing dumb and rationalized hiding can indirectly influence employee innovation performance through the mediating effect of well-being. Fong et al. ( 2018 ) confirm that a decrease in absorptive capacity is the key mediator in the relationship between knowledge hiding and team creativity. Zhang and Min ( 2019 ) state that team learning partially mediates the relationship between knowledge hiding and project team performance.
Moreover, researchers have studied the process through which knowledge hiding affects employees' subsequent interpersonal behaviors. For instance, Burmeister et al. ( 2019 ) find that guilt and shame play opposite mediating roles in the relationship between individual knowledge hiding and its subsequent interpersonal-oriented OCB. Arain et al. ( 2020b ) point out that supervisor knowledge hiding negatively influences subordinates' OCB toward their supervisors, and subordinate distrust in their supervisors plays a mediating role. Supervisor knowledge hiding can also activate employee moral disengagement, prompting them to reduce OCB toward their supervisors and increase silence behaviors (Arain et al., 2020a ). Jiang et al. ( 2019 ) suggest that knowledge hiding makes the hiders feel the insecurity of self-expression and interpersonal risk, thereby reducing their psychological safety and endangering their ability to thrive at work. Despite these advancements, it is necessary to develop a robust framework that integrates multipath models based on different innovative theoretical perspectives.
Regarding the moderating role of contextual factors on knowledge hiding, the existing research mainly explores the contingency influence of individual differences, job characteristics, team characteristics, and team/organizational climate. In terms of individual differences, some scholars find that organizational psychological ownership can effectively reduce the knowledge hiding resulting from territoriality (Peng, 2013 ). Furthermore, psychological ownership significantly moderates the inverted U-shaped relationship between knowledge leadership and knowledge hiding. This curved relationship is more obvious among employees with high psychological ownership (Xia et al., 2019 ). High psychological ownership can also minimize the impact of abusive supervision on knowledge hiding (Ghani et al., 2020a ). Other scholars explore the boundary effect of positive traits, such as individualism/collectivist values (Semerci, 2019 ), positive affectivity (Jahanzeb et al., 2020a ), benevolence or tolerance (Jahanzeb et al., 2020b ), prosocial motivations (Škerlavaj et al., 2018 ), harmonious work enthusiasm (Anser et al., 2020 ), professional commitment (Malik et al., 2019 ), trust-related affect/cognition (Nadeem et al., 2021 ), social skills (Wang et al., 2019 ), and cultural intelligence (Bogilović et al., 2017 ). In addition to these studies, scholars examine the impacts of negative traits on knowledge hiding, such as negative reciprocity (Zhao et al., 2016 ; Jahanzeb et al., 2019 ), instrumental thinking (Abdullah et al., 2019 ), hostile attribution bias (Khalid et al., 2020 ), moral disengagement (Zhao et al., 2016 ), and cynicism (Jiang et al., 2019 ).
In relation to job characteristics, task interdependence has attracted a lot of attention. Huo et al. ( 2016 ) point out that task interdependence can reduce the territorial awareness and knowledge hiding caused by psychological ownership. Hernaus et al. ( 2019 ) find that task interdependence can help reduce the probability of employees' evasive knowledge hiding due to maintaining their competitiveness. Fong et al. ( 2018 ) show that task interdependence moderates the relationship between knowledge hiding and team absorptive capacity. Weng et al. ( 2020 ) suggest that the interdependence of cooperative and competitive goals has opposite moderating effects on the relationship between upward LMX social comparison and knowledge hiding. In addition, Pan and Zhang ( 2018 ) also analyze the influence of work autonomy on the intensity of the relationship between neuroticism and knowledge hiding.
Regarding the team/organizational climate, research shows that in an environment that values information exchange and cooperation, the negative influence of knowledge hiding will be greatly weakened. Accordingly, Cerne et al. ( 2014 ) study the boundary effect of the team achievement-motivation climate (e.g., performance climate and mastery climate) on the relationship between knowledge hiding and the decrease in the hider's creativity. They discover that the negative effect of knowledge hiding on the hider's creativity is reduced in a mastery climate. Furthermore, Cerne et al. ( 2017 ) find the moderating effects of mastery climate, task interdependence, and autonomy on the relationship between knowledge hiding and innovative work behavior. Bari et al. ( 2019 ) obtain similar findings which point out that a perceived mastery climate reduces the negative impact of evasive hiding and playing dumb on team creativity. Feng and Wang ( 2019 ) find that the interaction between abusive supervision and a mastery climate is negatively related to knowledge hiding, and the interaction between abusive supervision and a performance climate is positively related to knowledge hiding. On the one hand, when the organization pays more attention to individual performance feedback, performance-prove goal orientation can positively predict knowledge hiding. On the other hand, when the organization pays more attention to group performance feedback, performance-prove goal orientation is negatively correlated with knowledge hiding (Zhu et al., 2019 ). Compared to individual rewards, team-based rewards are more likely to reduce the distrust caused by knowledge hiding, promoting the team to work hard to achieve a common goal, forming a relatively stable team structure, and improving team viability (Wang et al., 2019 ). Yao et al. ( 2020a , b ) reveal the buffering effect of a forgiveness climate on the relationship between negative workplace gossip/workplace bullying and knowledge hiding. Khalid et al. ( 2018 ) clarify the role of Islamic work ethics in moderating the relationship between abusive supervision and knowledge hiding. Among these findings, the existing research on the moderating effects still focuses more on the first stage of the antecedents–knowledge hiding–consequences linkage, but there is a lack of systematic development of the moderation mechanism in the second stage.
Future Research Directions
Based on a descriptive analysis, bibliometric analysis, and content analysis, we find that research on knowledge hiding focuses mainly on five clusters. Despite the ongoing progress, several research gaps are worth further addressing.
- (1) Comprehensive studies on the concept and dimensions of knowledge hiding are needed to provide a robust conceptual framework. Although the definition and three-dimensional view of knowledge hiding by Connelly et al. ( 2012 ) are widely adopted by many scholars, more research is needed to carry out in-depth comparative analysis to clarify the connections and differences between knowledge hiding and similar concepts (e.g., knowledge non-sharing, knowledge sharing hostility, knowledge contribution loafing, counterproductive knowledge behavior, knowledge hoarding, knowledge protection, employee silence, etc.). Further, more studies should continue exploring the dimensions of knowledge hiding. There is a lack of focus on knowledge hiders' psychological motivation and respective knowledge hiding strategies. For example, research on proactive, reactive, and passive knowledge hiding could enrich the field research. In addition, more studies should further explore the unique reasons and consequences of a rationalized hiding behavior. There is a need to verify the ethical aspect of rationalized hiding, when knowledge hiding is used to protect confidential information or the interests of third parties (Zhao et al., 2019 ).
- (2) Future studies need to further explore the consequences of knowledge hiding. Based on a systematic review (see Figure 3 ), we find that previous studies have focused mainly on the antecedents of knowledge hiding. Although some studies have addressed the impacts of knowledge characteristics, individual factors, team-level and interpersonal factors, and organizational-level factors on knowledge hiding, more work is needed to provide comprehensive studies on the generating mechanisms and the respective coping strategies of knowledge hiding. Prior studies have shown that knowledge hiding has impacts on individual-level outcomes (e.g., individual creativity, in-role and extra-role performance, and coworker relationships) and team-level outcomes (e.g., team creativity). However, there is a lack of research on organizational-level outcomes. Moreover, prior studies focus mainly on the impacts of knowledge hiding on the knowledge seekers and the whole team, but seldom has the research discussed the potential effects of knowledge hiding on the knowledge hiders themselves. Therefore, future research should devote more attention to the negative effects of knowledge hiding on the knowledge hiders, the team, and the organization, and also explore the consequences of different dimensions of knowledge hiding. For example, more studies could address the research gap as to whether knowledge hiding may stimulate self-reflection and prompt moral and psychological compensation for the knowledge hiders. To enrich the multilevel mediating and moderating variables, future studies could explore the boundary conditions of knowledge hiding and their respective knowledge management strategies. In short, it is necessary to increase research on the consequences of knowledge hiding to enrich the antecedents–knowledge hiding–consequences research path.
- (3) More studies on multilateral, cross-level, and collective knowledge hiding are needed, and it is appropriate to introduce new paradigms for knowledge hiding research. Existing research on knowledge hiding highlights mainly two parties: the hider (A) and the seeker (B) (i.e., B seeks knowledge from A, while A hides knowledge from B). Most studies address knowledge hiding among colleagues at the horizontal level. In recent years, some scholars have started to show interest in knowledge hiding at the vertical level, that is, the top-down knowledge hiding of superiors from subordinates. However, the research on the antecedents and the generating mechanisms of knowledge hiding at the vertical level is still in the stage of exploration. There is a lack of research on bottom-up knowledge hiding (of the subordinates from their superiors). Therefore, it is necessary to study knowledge hiding adopted by people from different hierarchies (e.g., bottom, mid, and high levels) in the organizations, comparing the differences between top-down and bottom-up knowledge hiding, so as to identify regular patterns of cross-level knowledge flow within the organizations. Future research could also examine whether the knowledge hiding of top managers could trigger a trickle-down effect, referring to the fact that the behaviors of the top leaders will affect employees in the formal vertical power chain, given that knowledge hiding can be a multi-participant phenomenon. Therefore, future research could examine the contagious effects of knowledge hiding (e.g., B seeks knowledge from A, but A hides knowledge from B; B then feels lost and hides knowledge from other colleagues), diffusion effects (e.g., B seeks knowledge from A while A hides knowledge from B; A asks C to hide knowledge from B as well), bystander effects (e.g., B seeks knowledge from A, while A hides knowledge from B; C witnesses A's knowledge hiding and is influenced by it, so C also hides knowledge from B and other colleagues), and collective knowledge hiding.
- (4) Future scholars should innovate theoretical perspectives and integrate multidisciplinary theories into knowledge hiding research. At present, knowledge hiding research is based mainly on theories such as social exchange, social cognition, social capital, social learning, conservation of resources, territoriality, and psychological ownership. To enrich the field research, it is necessary to diversify the theories. For example, future studies could explore the influence of social exchange relations (e.g., relative LMX) on knowledge hiding, comparing the influence of social LMX and economic LMX on employee willingness to hide knowledge. Future scholars could also conduct multi-interdisciplinary research studies. The research on how an individual's previous workplace behavior affects his or her subsequent workplace behavior has attracted great interest from scholars and mainstream journals in organizational behavior in recent years. Given that knowledge hiding is a typical morality-related behavior, future research could introduce novel and original theoretical viewpoints. For example, a moral balance model and a moral cleansing effect in disciplines such as moral psychology and cognitive psychology, can be used to explore how an individual's previous knowledge hiding behavior influences subsequent behavior in the workplace. Furthermore, knowledge hiding is considered as an emotion-driven behavior. Therefore, scholars could consider employing Lazarus's cognitive–motivational–relational (CMR) theory of emotion (Lazarus, 1991 ) to better understand the psychological process behind knowledge hiding. Moreover, there is a lack of research on the relationship between individual affect/emotion and knowledge hiding. Therefore, scholars could employ theories, such as affective events theory and self-conscious moral emotion theory, to analyze the subsequent behavior of the hiders and seekers who are driven by affect/emotion.
- (5) Research designs need more diversification. Most of the prior studies focus on the individuals, and few research studies focus on both individual and team effects. Knowledge hiding is a complex organizational behavior that concerns individual, team/interpersonal, and organizational levels. Therefore, future research could introduce data tracking technologies, such as big data analysis, to study and compare the dynamic and static (long-term and short-term) effects of multilevel knowledge hiding. Moreover, it is necessary to diversify research methods in the field. Most existing research uses one-wave or multistage surveys, employee self-evaluation, and empirical tests, with few studies using case studies and interviews. These research methods may suffer from a lack of reliability of data sources. Future research could integrate multiple methodologies (e.g., combining case studies, experimental research, surveys, and objective data mining) to verify data, which could improve the internal and external validity of the research and enhance the robustness of conclusions. In particular, it is necessary to focus on the combination of experimental and empirical research, making full use of the strengths of each method to validate the research. Researchers could carry out preliminary tests on relevant hypotheses through experimental research and then supplement them with surveys for secondary verification.
- (6) Future research should integrate more cultural, sectoral, and organizational factors to enrich the findings. As discussed in the findings, most of the knowledge hiding data were collected in China and Pakistan. It is necessary to develop the diversity of knowledge hiding data in terms of country of origin. In addition, there is a lack of cross-country academic collaboration. Collaborating across borders could help to generate new ideas and allow for collecting data from different sources. Meanwhile, it would be very interesting to promote cross-country studies to identify the different definitions, perceptions, implementations, and patterns of knowledge hiding, whilst paying more attention to the relationship between cultural dimensions and knowledge hiding. Apart from cross-cultural and cross-country variables, future research could also investigate industry characteristics (such as knowledge-intensive and non-knowledge-intensive industries and masculine and feminine industries), team standards/norms (such as team moral norms), and firm size (small medium enterprises vs. multinational companies) so as to identify the boundary conditions of individual knowledge hiding behavior. Through conducting sector-specific and cross-sector comparison for knowledge hiding, we would be able to adjust knowledge management methods.
Conclusions
This article provides a systematic review of knowledge hiding. It contributes to the identification of publication patterns on knowledge hiding between 2012 and 2020. Further, we have highlighted the most influential studies, mapped the research gaps, and provided the potential research directions in the field.
This study is not without limitations. We use SCI and SSCI web of science as the databases. Using this literature search method excludes book chapters, reports, unpublished dissertations, with/without peer reviewed conference proceedings, newsletters, government documents, and working papers. Consequently, this review may not have captured the full range of scholarly literature on knowledge hiding. In the future, to reduce the publication bias (Kepes et al., 2012 ), it would be interesting to include other databases to search literatures, for instance, the work published in the Emerging Sources Citation Index (ESCI) journals can be considered. Second, the research on knowledge hiding is emerging, and some scholars may argue that it is not yet mature enough to review the research field. In our opinion, it is only with such a complete literature review that a clear picture of knowledge hiding research can be developed so that scholars can better define research problems, innovate the research theories and methods, and enrich the field research with a robust framework.
Data Availability Statement
Author contributions.
PH, CJ, ZX, and CS designed and supervised the study. PH collected the data. PH and ZX analyzed the data. PH, CJ, and CS wrote the manuscript. All authors contributed equally to this manuscript, reviewed, and approved this manuscript for publication.
Funding was provided by Huaqiao University's Academic Project Supported by the Fundamental Research Funds for the Central Universities (20SKGC-QT02) and the National Natural Science Foundation of China (72172048).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher's Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
- Abdillah M. R., Wu W., Anita R. (2020). Can altruistic leadership prevent knowledge-hiding behaviour? Testing dual mediation mechanisms . Knowl. Manag. Res. Pract . 10.1080/14778238.2020.1776171 [ CrossRef ] [ Google Scholar ]
- Abdullah M. I., Dechun H., Ali M., Usman M. (2019). Ethical leadership and knowledge hiding: a moderated mediation model of relational social capital, and instrumental thinking . Front. Psychol. 10 :2403. 10.3389/fpsyg.2019.02403 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Abubakar A. M., Behravesh E., Rezapouraghdam H., Yildiz S. B. (2019). Applying artificial intelligence technique to predict knowledge hiding behavior . J. Inf. Manag. 49 , 45–57. 10.1016/j.ijinfomgt.2019.02.006 [ CrossRef ] [ Google Scholar ]
- Aljawarneh N. M. S., Atan T. (2018). Linking tolerance to workplace incivility, service innovative, knowledge hiding, and job search behavior: the mediating role of employee cynicism . Negot. Confl. Manag. Res. 11 , 298–320. 10.1111/ncmr.12136 [ CrossRef ] [ Google Scholar ]
- Anand A., Centobelli P., Cerchione R. (2020). Why should I share knowledge with others? A review-based framework on events leading to knowledge hiding . J. Organ. Chang. Manag . 33 , 379–399. 10.1108/JOCM-06-2019-0174 [ CrossRef ] [ Google Scholar ]
- Anaza N. A., Nowlin E. L. (2017). What's mine is mine: a study of salesperson knowledge withholding & hoarding behavior . Ind. Mark. Manag. 64 , 14–24. 10.1016/j.indmarman.2017.03.007 [ CrossRef ] [ Google Scholar ]
- Anser M. K., Ali M., Usman M., Rana M. L. T., Yousaf Z. (2020). Ethical leadership and knowledge hiding: an intervening and interactional analysis . Serv. Ind. J. 41 , 307–329. 10.1080/02642069.2020.1739657 [ CrossRef ] [ Google Scholar ]
- Arain G. A., Bhatti Z. A., Ashraf N., Fang Y. H. (2020b). Top-down knowledge hiding in organizations: an empirical study of the consequences of supervisor knowledge hiding among local and foreign workers in the Middle East . J. Bus. Ethics 164 , 611–625. 10.1007/s10551-018-4056-2 [ CrossRef ] [ Google Scholar ]
- Arain G. A., Bhatti Z. A., Hameed I., Fang Y. H. (2019). Top-down knowledge hiding and innovative work behavior (IWB): a three-way moderated-mediation analysis of self-efficacy and local/foreign status . J. Knowl. Manag . 24 , 127–149. 10.1108/JKM-11-2018-0687 [ CrossRef ] [ Google Scholar ]
- Arain G. A., Hameed I., Umrani W. A., Khan A. K., Sheikh A. Z. (2020a). Consequences of supervisor knowledge hiding in organizations: a multilevel mediation analysis . Appl. Psychol . 70 , 1242–1266. 10.1111/apps.12274 [ CrossRef ] [ Google Scholar ]
- Babič K., Cerne M., Connelly C. E., Dysvik A., Škerlavaj M. (2019). Are we in this together? Knowledge hiding in teams, collective prosocial motivation and leader-member exchange . J. Knowl. Manag . 23 , 1502–1522. 10.1108/JKM-12-2018-0734 [ CrossRef ] [ Google Scholar ]
- Bari M. W., Abrar M., Shaheen S., Bashir M., Fanchen M. (2019). Knowledge hiding behaviors and team creativity: the contingent role of perceived mastery motivational climate . Sage Open 9. 10.1177/2158244019876297 [ CrossRef ] [ Google Scholar ]
- Bari M. W., Ghaffar M., Ahmad B. (2020). Knowledge-hiding behaviors and employees' silence: mediating role of psychological contract breach . J. Knowl. Manag . 24 , 2171–2194. 10.1108/JKM-02-2020-0149 [ CrossRef ] [ Google Scholar ]
- Bernatović I., Gomezel A. S., Cerne M. (2021). Mapping the knowledge-hiding field and its future prospects: a bibliometric co-citation, co-word, and coupling analysis . Knowl. Manag. Res. Pract. 10.1080/14778238.2021.1945963 [ CrossRef ] [ Google Scholar ]
- Bogilović S., Cerne M., Škerlavaj M. (2017). Hiding behind a mask? Cultural intelligence, knowledge hiding, and individual and team creativity . Eur. J. Work Organ. Psychol. 26 , 710–723. 10.1080/1359432X.2017.1337747 [ CrossRef ] [ Google Scholar ]
- Burmeister A., Fasbender U., Gerpott F. H. (2019). Consequences of knowledge hiding: the differential compensatory effects of guilt and shame . J. Occup. Organ. Psychol. 92 , 281–304. 10.1111/joop.12249 [ CrossRef ] [ Google Scholar ]
- Butt A. S. (2019). Determinants of top-down knowledge hiding in firms: an individual-level perspective . Asian Bus. Manag. 20 , 259–279. 10.1057/s41291-019-00091-1 [ CrossRef ] [ Google Scholar ]
- Butt A. S., Ahmad A. B. (2019). Are there any antecedents of top-down knowledge hiding in firms? Evidence from the United Arab Emirates . J. Knowl. Manag. 23 , 1605–1627. 10.1108/JKM-04-2019-0204 [ CrossRef ] [ Google Scholar ]
- Cerne M., Hernaus T., Dysvik A., Škerlavaj M. (2017). The role of multilevel synergistic interplay among team mastery climate, knowledge hiding, and job characteristics in stimulating innovative work behavior . Hum. Resour. Manag. J. 27 , 281–299. 10.1111/1748-8583.12132 [ CrossRef ] [ Google Scholar ]
- Cerne M., Nerstad C. G. L., Dysvik A., Škerlavaj M. (2014). What goes around comes around: knowledge hiding, perceived motivational climate, and creativity . Acad. Manag. Ann. 57 , 172–192. 10.5465/amj.2012.0122 [ CrossRef ] [ Google Scholar ]
- Connelly C. E., Kelloway E. K. (2003). Predictors of employees' perceptions of knowledge sharing cultures . Leadersh. Organ. Dev. J. 24 , 294–301. 10.1108/01437730310485815 [ CrossRef ] [ Google Scholar ]
- Connelly C. E., Zweig D. (2015). How perpetrators and targets construe knowledge hiding in organizations . Eur. J. Work Organ. Psychol. 24 , 479–489. 10.1080/1359432X.2014.931325 [ CrossRef ] [ Google Scholar ]
- Connelly C. E., Zweig D., Webster J., Trougakos J. P. (2012). Knowledge hiding in organizations . J. Organ. Behav. 33 , 64–88. 10.1002/job.737 [ CrossRef ] [ Google Scholar ]
- de Garcia P. S., Oliveira M., Brohman K. (2020). Knowledge sharing, hiding and hoarding: how are they related? Knowl. Manag. Res. Pract . 10.1080/14778238.2020.1774434 [ CrossRef ] [ Google Scholar ]
- Fang Y. H. (2017). Coping with fear and guilt using mobile social networking applications: knowledge hiding, loafing, and sharing . Telemat. Inform. 34 , 779–797. 10.1016/j.tele.2017.03.002 [ CrossRef ] [ Google Scholar ]
- Feng J., Wang C. (2019). Does abusive supervision always promote employees to hide knowledge? From both reactance and COR perspectives . J. Knowl. Manag. 23 , 1455–1474. 10.1108/JKM-12-2018-0737 [ CrossRef ] [ Google Scholar ]
- Fong P. S. W., Men C., Luo J., Jia R. (2018). Knowledge hiding and team creativity: the contingent role of task interdependence . Manag. Decis. 56 , 329–343. 10.1108/MD-11-2016-0778 [ CrossRef ] [ Google Scholar ]
- Gagné M., Tian A. W., Soo C., Zhang B., Ho K. S. B., Hosszu K. (2019). Different motivations for knowledge sharing and hiding: the role of motivating work design . J. Organ. Behav. 40 , 783–799. 10.1002/job.2364 [ CrossRef ] [ Google Scholar ]
- Ghani U., Teo T., Li Y., Usman M., Islam Z. U., Gul H., et al.. (2020a). Tit for tat: abusive supervision and knowledge hiding-the role of psychological contract breach and psychological ownership . Int. J. Environ. Res. Public Health 17 :1240. 10.3390/ijerph17041240 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Ghani U., Zhai X. S., Spector J. M., Chen N. S., Lin L., Ding D. H., et al.. (2020b). Knowledge hiding in higher education: role of interactional justice and professional commitment . High. Educ. 79 , 325–344. 10.1007/s10734-019-00412-5 [ CrossRef ] [ Google Scholar ]
- He P., Sun R., Zhao H., Zheng L., Shen C. (2020). Linking work-related and non-work-related supervisor–subordinate relationships to knowledge hiding: a psychological safety lens . Asian Bus. Manag. 10.1057/s41291-020-00137-9 [ CrossRef ] [ Google Scholar ]
- Hernaus T., Cerne M., Connelly C., Vokic N. P., Škerlavaj M. (2019). Evasive knowledge hiding in academia: when competitive individuals are asked to collaborate . J. Knowl. Manag. 23 , 597–618. 10.1108/JKM-11-2017-0531 [ CrossRef ] [ Google Scholar ]
- Huo W., Cai Z., Luo J., Men C., Jia R. (2016). Antecedents and intervention mechanisms: a multi-level study of R & D team's knowledge hiding behavior . J. Knowl. Manag. 20 , 880–897. 10.1108/JKM-11-2015-0451 [ CrossRef ] [ Google Scholar ]
- Jahanzeb S., De Clercq D., Fatima T. (2020a). Bridging the breach: using positive affectivity to overcome knowledge hiding after contract breaches . J. Psychol. 154 , 249–272. 10.1080/00223980.2019.1705235 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Jahanzeb S., De Clercq D., Fatima T. (2020b). Organizational injustice and knowledge hiding: the roles of organizational dis-identification and benevolence . Manag. Decis. 59 , 446–462. 10.1108/MD-05-2019-0581 [ CrossRef ] [ Google Scholar ]
- Jahanzeb S., Fatima T., Bouckenooghe D., Bashir F. (2019). The knowledge hiding link: a moderated mediation model of how abusive supervision affects employee creativity . Eur. J. Work Organ. Psychol. 28 , 810–819. 10.1080/1359432X.2019.1659245 [ CrossRef ] [ Google Scholar ]
- Jha J. K., Varkkey B. (2018). Are you a cistern or a channel? Exploring factors triggering knowledge-hiding behavior at the workplace: evidence from the Indian R&D professionals . J. Knowl. Manag . 22 , 824–849. 10.1108/JKM-02-2017-0048 [ CrossRef ] [ Google Scholar ]
- Jiang Z., Hu X., Wang Z., Jiang X. (2019). Knowledge hiding as a barrier to thriving: the mediating role of psychological safety and moderating role of organizational cynicism . J. Organ. Behav. 40 , 800–818. 10.1002/job.2358 [ CrossRef ] [ Google Scholar ]
- Kang S. W. (2016). Knowledge withholding: psychological hindrance to the innovation diffusion within an organisation . Knowl. Manag. Res. Pract. 14 , 144–149. 10.1057/kmrp.2014.24 [ CrossRef ] [ Google Scholar ]
- Kepes S., Banks G. C., McDaniel M., Whetzel D. L. (2012). Publication bias in the organizational sciences . Organ. Res. Methods 15 , 624–662. 10.1177/1094428112452760 [ CrossRef ] [ Google Scholar ]
- Khalid M., Bashir S., Khan K. A., Abbas N. (2018). When and how abusive supervision leads to knowledge hiding behaviors: an Islamic work ethics perspective . Leadersh. Organ. Dev. J. 39 , 794–806. 10.1108/LODJ-05-2017-0140 [ CrossRef ] [ Google Scholar ]
- Khalid M., Gulzar A., Khan K. A. (2020). When and how the psychologically entitled employees hide more knowledge? Int. J. Hosp. Manag. 89 :102413. 10.1016/j.ijhm.2019.102413 [ CrossRef ] [ Google Scholar ]
- Khoreva V., Wechtler H. (2020). Exploring the consequences of knowledge hiding: an agency theory perspective . J. Manag. Psychol. 35 , 71–84. 10.1108/JMP-11-2018-0514 [ CrossRef ] [ Google Scholar ]
- Lazarus R. S. (1991). Progress on a cognitive-motivational-relational theory of emotion . Am. Psychol. 46 , 819–834. 10.1037/0003-066X.46.8.819 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Lee K., Allen N. J. (2002). Organizational citizenship behavior and workplace deviance: the role of affect and cognitions . J. Appl. Psychol . 87 , 131–142. 10.1037/0021-9010.87.1.131 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Lin M., Zhang X., Ng B. C. S., Zhong L. (2020). To empower or not to empower? Multilevel effects of empowering leadership on knowledge hiding . Int. J. Hosp. Manag. 89 :102540. 10.1016/j.ijhm.2020.102540 [ CrossRef ] [ Google Scholar ]
- Lin T. C., Huang C. C. (2010). Withholding effort in knowledge contribution: the role of social exchange and social cognitive on project teams . Inf. Manag. 47 , 188–196. 10.1016/j.im.2010.02.001 [ CrossRef ] [ Google Scholar ]
- Liu Y., Zhu J. N. Y., Lam L. W. (2020). Obligations and feeling envied: a study of workplace status and knowledge hiding . J. Manag. Psychol. 35 , 347–359. 10.1108/JMP-05-2019-0276 [ CrossRef ] [ Google Scholar ]
- Malik O. F., Shahzad A., Raziq M. M., Khan M. M., Yusaf S., Khan A. (2019). Perceptions of organizational politics, knowledge hiding, and employee creativity: the moderating role of professional commitment . Pers. Individ. Differ. 142 , 232–237. 10.1016/j.paid.2018.05.005 [ CrossRef ] [ Google Scholar ]
- Men C., Fong P. S. W., Huo W., Zhong J., Jia R., Luo J. (2020). Ethical leadership and knowledge hiding: a moderated mediation model of psychological safety and mastery climate . J. Bus. Ethics 166 , 461–472. 10.1007/s10551-018-4027-7 [ CrossRef ] [ Google Scholar ]
- Moh'd S. S., Cerne M., Zhang P. (2021). An exploratory configurational analysis of knowledge hiding antecedents in project teams . Proj. Manag. J. 52 , 31–44. 10.1177/8756972820939768 [ CrossRef ] [ Google Scholar ]
- Nadeem M. A., Liu Z., Ghani U., Younis A., Xu Y. (2021). Impact of shared goals on knowledge hiding behavior: the moderating role of trust . Manag. Decis . 59 , 1312–1332. 10.1108/MD-09-2019-1197 [ CrossRef ] [ Google Scholar ]
- Offergelt F., Spörrle M., Moser K., Shaw J. D. (2019). Leader-signaled knowledge hiding: effects on employees' job attitudes and empowerment . J. Organ. Behav. 40 , 819–833. 10.1002/job.2343 [ CrossRef ] [ Google Scholar ]
- Pan W., Zhang Q. (2018). Withholding knowledge in teams: an interactionist perspective of personality, justice, and autonomy . Soc. Behav. Pers. 46 , 2009–2024. 10.2224/sbp.7390 [ CrossRef ] [ Google Scholar ]
- Pan W., Zhang Q., Teo T. S. H., Lim V. K. G. (2018). The dark triad and knowledge hiding . J. Inf. Manag. 42 , 36–48. 10.1016/j.ijinfomgt.2018.05.008 [ CrossRef ] [ Google Scholar ]
- Peng H. (2013). Why and when do people hide knowledge? J. Knowl. Manag. 17 , 398–415. 10.1108/JKM-12-2012-0380 [ CrossRef ] [ Google Scholar ]
- Pickering C., Byrne J. (2014). The benefits of publishing systematic quantitative literature reviews for PhD candidates and other early-career researchers . High. Educ. Res. Dev. 33 , 534–548. 10.1080/07294360.2013.841651 [ CrossRef ] [ Google Scholar ]
- Pradhan S., Srivastava A., Mishra D. K. (2019). Abusive supervision and knowledge hiding: the mediating role of psychological contract violation and supervisor directed aggression . J. Knowl. Manag. 24 , 216–234. 10.1108/JKM-05-2019-0248 [ CrossRef ] [ Google Scholar ]
- Riaz S., Xu Y., Hussain S. (2019). Workplace ostracism and knowledge hiding: the mediating role of job tension . Sustainability 11 :5547. 10.3390/su11205547 [ CrossRef ] [ Google Scholar ]
- Semerci A. B. (2019). Examination of knowledge hiding with conflict, competition and personal values . Int. J. Confl. Manag. 30 , 111–131. 10.1108/IJCMA-03-2018-0044 [ CrossRef ] [ Google Scholar ]
- Serenko A., Bontis N. (2016). Understanding counterproductive knowledge behavior: antecedents and consequences of intra-organizational knowledge hiding . J. Knowl. Manag. 20 , 1199–1224. 10.1108/JKM-05-2016-0203 [ CrossRef ] [ Google Scholar ]
- Shen X., Li Y., Sun Y., Chen J., Wang F. (2019). Knowledge withholding in online knowledge spaces: social deviance behavior and secondary control perspective . J. Assoc. Inf. Sci. Technol. 70 , 385–401. 10.1002/asi.24192 [ CrossRef ] [ Google Scholar ]
- Singh S. K. (2019). Territoriality, task performance, and workplace deviance: empirical evidence on role of knowledge hiding . J. Bus. Res. 97 , 10–19. 10.1016/j.jbusres.2018.12.034 [ CrossRef ] [ Google Scholar ]
- Škerlavaj M., Connelly C. E., Cerne E., Dysvik A. (2018). Tell me if you can: time pressure, prosocial motivation, perspective taking, and knowledge hiding . J. Knowl. Manag. 22 , 1489–1509. 10.1108/JKM-05-2017-0179 [ CrossRef ] [ Google Scholar ]
- Stenius M., Hankonen N., Ravaja N., Haukkala A. (2016). Why share expertise? A closer look at the quality of motivation to share or withhold knowledge . J. Knowl. Manag. 20 , 181–198. 10.1108/JKM-03-2015-0124 [ CrossRef ] [ Google Scholar ]
- Tranfield D., Denyer D., Palminder S. (2003). Towards a methodology for developing evidence-informed management knowledge by means of systematic review . Br. J. Manag . 14 , 207–222. 10.1111/1467-8551.00375 [ CrossRef ] [ Google Scholar ]
- Tsay C. H. H., Lin T. C., Yoon J., Huang C. C. (2014). Knowledge withholding intentions in teams: the roles of normative conformity, affective bonding, rational choice and social cognition . Decis. Support Syst. 67 , 53–65. 10.1016/j.dss.2014.08.003 [ CrossRef ] [ Google Scholar ]
- Vlačić B., Corbo L., Costa e Silva S., Dabi,ć M. (2021). The evolving role of artificial intelligence in marketing: a review and research agenda . J. Bus. Res. 128 , 187–203. 10.1016/j.jbusres.2021.01.055 [ CrossRef ] [ Google Scholar ]
- Wang Y., Han M., Xiang D., Hampson D. P. (2019). The double-edged effects of perceived knowledge hiding: empirical evidence from the sales context . J. Knowl. Manag. 23 , 279–296. 10.1108/JKM-04-2018-0245 [ CrossRef ] [ Google Scholar ]
- Wang Y. S., Lin H. H., Li C. R., Lin S. J. (2014). What drives students' knowledge-withholding intention in management education? An empirical study in Taiwan . Acad. Manag. Learn. Educ. 13 , 547–568. 10.5465/amle.2013.0066 [ CrossRef ] [ Google Scholar ]
- Webster J., Brown G., Zweig D., Connelly C. E., Brodt S., Sitkin S. (2008). Beyond knowledge sharing: withholding knowledge at work . Res. Pers. Hum. Resour. Manag. 27 , 1–37. 10.1016/S0742-7301(08)27001-5 [ CrossRef ] [ Google Scholar ]
- Weng Q., Latif K., Khan A. K., Tariq H., Butt H. P., Obaid A., et al.. (2020). Loaded with knowledge, yet green with envy: leader–member exchange comparison and coworkers-directed knowledge hiding behavior . J. Knowl. Manag. 24 , 1653–1680. 10.1108/JKM-10-2019-0534 [ CrossRef ] [ Google Scholar ]
- Wu D. (2020). Empirical study of knowledge withholding in cyberspace: integrating protection motivation theory and theory of reasoned behavior . Comput. Hum. Behav. 105 :106229. 10.1016/j.chb.2019.106229 [ CrossRef ] [ Google Scholar ]
- Xia Q., Yan S., Zhang Y., Chen B. (2019). The curvilinear relationship between knowledge leadership and knowledge hiding: the moderating role of psychological ownership . Leadersh. Organ. Dev. J. 40 , 669–683. 10.1108/LODJ-10-2018-0362 [ CrossRef ] [ Google Scholar ]
- Xiao M., Cooke F. L. (2019). Why and when knowledge hiding in the workplace is harmful: a review of the literature and directions for future research in the Chinese context . Asia Pac. J. Hum. Resour. 57 , 470–502. 10.1111/1744-7941.12198 [ CrossRef ] [ Google Scholar ]
- Yao Z., Luo J., Zhang X. (2020a). Gossip is a fearful thing: the impact of negative workplace gossip on knowledge hiding . J. Knowl. Manag. 24 , 1755–1775. 10.1108/JKM-04-2020-0264 [ CrossRef ] [ Google Scholar ]
- Yao Z., Zhang X., Luo J., Huang H. (2020b). Offense is the best defense: the impact of workplace bullying on knowledge hiding . J. Knowl. Manag. 24 , 675–695. 10.1108/JKM-12-2019-0755 [ CrossRef ] [ Google Scholar ]
- Zhai X., Wang M., Ghani U. (2020). The SOR (Stimulus-Organism-Response) paradigm in online learning: an empirical study of students' knowledge hiding perceptions . Interact. Learn. Environ. 28 , 586–601. 10.1080/10494820.2019.1696841 [ CrossRef ] [ Google Scholar ]
- Zhang Z., Min M. (2019). The negative consequences of knowledge hiding in NPD project teams: the roles of project work attributes . Int. J. Constr. Proj. Manag. 37 , 225–238. 10.1016/j.ijproman.2019.01.006 [ CrossRef ] [ Google Scholar ]
- Zhao H., Liu W., Li J., Yu X. (2019). Leader–member exchange, organizational identification, and knowledge hiding: the moderating role of relative leader–member exchange . J. Organ. Behav. 40 , 834–848. 10.1002/job.2359 [ CrossRef ] [ Google Scholar ]
- Zhao H., Xia Q. (2019). Nurses' negative affective states, moral disengagement, and knowledge hiding: the moderating role of ethical leadership . J. Nurs. Manag. 27 , 357–370. 10.1111/jonm.12675 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Zhao H., Xia Q., He P., Sheard G., Wan P. (2016). Workplace ostracism and knowledge hiding in service organizations . Int. J. Hosp. Manag. 59 , 84–94. 10.1016/j.ijhm.2016.09.009 [ CrossRef ] [ Google Scholar ]
- Zhu Y., Chen T., Wang M., Jin Y., Wang Y. (2019). Rivals or allies: how performance-prove goal orientation influences knowledge hiding . J. Organ. Behav. 40 , 849–868. 10.1002/job.2372 [ CrossRef ] [ Google Scholar ]
- DOI: 10.3389/fpsyg.2021.748237
- Corpus ID: 240075796
Knowledge Hiding: Current Research Status and Future Research Directions
- Peixu He , Cuiling Jiang , +1 author Chuangang Shen
- Published in Frontiers in Psychology 29 October 2021
- Business, Computer Science
Figures and Tables from this paper

78 Citations
A bibliometric analysis of knowledge-hiding research.
- Highly Influenced
Knowledge Hiding in Organizations: Meta-Analysis 10 Years Later
Insights into the use of theories in knowledge hiding studies: a systematic review, creating a culture to avoid knowledge hiding within an organization: the role of management support, temporary team performance and knowledge hiding: mediated by interpersonal mistrust, of performance, influencing mechanism of justice sensitivity on knowledge hiding in the chinese context, openness to experience moderates the effect of abusive supervision on knowledge-hiding behavior, whose lips are sealed gender differences in knowledge hiding at work, impact of organizational dehumanization on employee knowledge hiding, 86 references, mapping the knowledge-hiding field and its future prospects: a bibliometric co-citation, co-word, and coupling analysis.
- Highly Influential
Knowledge hiding in organizations
- 10 Excerpts
The double-edged effects of perceived knowledge hiding: empirical evidence from the sales context
Understanding counterproductive knowledge behavior: antecedents and consequences of intra-organizational knowledge hiding, why and when knowledge hiding in the workplace is harmful: a review of the literature and directions for future research in the chinese context, examination of knowledge hiding with conflict, competition and personal values, exploring the consequences of knowledge hiding: an agency theory perspective, evasive knowledge hiding in academia: when competitive individuals are asked to collaborate, why and when do people hide knowledge, how perpetrators and targets construe knowledge hiding in organizations, related papers.
Showing 1 through 3 of 0 Related Papers

Emergency Alert and Warning Systems: Current Knowledge and Future Research Directions (2018)
Chapter: front matter.
EMERGENCY ALERT AND WARNING SYSTEMS
CURRENT KNOWLEDGE AND FUTURE RESEARCH DIRECTIONS
Committee on the Future of Emergency Alert and Warning Systems: Research Directions
Computer Science and Telecommunications Board
Division on Engineering and Physical Sciences
A Consensus Study Report of
THE NATIONAL ACADEMIES PRESS Washington, DC www.nap.edu
THE NATIONAL ACADEMIES PRESS 500 Fifth Street, NW Washington, DC 20001
Support for this project was provided by the Department of Homeland Security Science and Technology Directorate, with assistance from the Department of Health and Human Services under award number HHSP233201400020B. Any opinions, findings, conclusions, or recommendations expressed in this publication do not necessarily reflect the views of any organization or agency that provided support for the project.
International Standard Book Number-13: 978-0-309-46737-7 International Standard Book Number-10: 0-309-46737-3 Digital Object Identifier: https://doi.org/10.17226/24935
This report is available from:
Computer Science and Telecommunications Board National Research Council 500 Fifth Street, NW Washington, DC 20001
Additional copies of this publication are available for sale from the National Academies Press, 500 Fifth Street, NW, Keck 360, Washington, DC 20001; (800) 624-6242 or (202) 334-3313; http://www.nap.edu .
Copyright 2018 by the National Academy of Sciences. All rights reserved.
Printed in the United States of America
Suggested citation: National Academies of Sciences, Engineering, and Medicine. 2018. Emergency Alert and Warning Systems: Current Knowledge and Future Research Directions . The National Academies Press, Washington, DC. doi: https://doi.org/10.17226/24935 .
The National Academy of Sciences was established in 1863 by an Act of Congress, signed by President Lincoln, as a private, nongovernmental institution to advise the nation on issues related to science and technology. Members are elected by their peers for outstanding contributions to research. Dr. Marcia McNutt is president.
The National Academy of Engineering was established in 1964 under the charter of the National Academy of Sciences to bring the practices of engineering to advising the nation. Members are elected by their peers for extraordinary contributions to engineering. Dr. C. D. Mote, Jr., is president.
The National Academy of Medicine (formerly the Institute of Medicine) was established in 1970 under the charter of the National Academy of Sciences to advise the nation on medical and health issues. Members are elected by their peers for distinguished contributions to medicine and health. Dr. Victor J. Dzau is president.
The three Academies work together as the National Academies of Sciences, Engineering, and Medicine to provide independent, objective analysis and advice to the nation and conduct other activities to solve complex problems and inform public policy decisions. The National Academies also encourage education and research, recognize outstanding contributions to knowledge, and increase public understanding in matters of science, engineering, and medicine.
Learn more about the National Academies of Sciences, Engineering, and Medicine at www.nationalacademies.org .
Consensus Study Reports published by the National Academies of Sciences, Engineering, and Medicine document the evidence-based consensus on the study’s statement of task by an authoring committee of experts. Reports typically include findings, conclusions, and recommendations based on information gathered by the committee and the committee’s deliberations. Each report has been subjected to a rigorous and independent peer-review process and it represents the position of the National Academies on the statement of task.
Proceedings published by the National Academies of Sciences, Engineering, and Medicine chronicle the presentations and discussions at a workshop, symposium, or other event convened by the National Academies. The statements and opinions contained in proceedings are those of the participants and are not endorsed by other participants, the planning committee, or the National Academies.
For information about other products and activities of the National Academies, please visit www.nationalacademies.org/about/whatwedo .
COMMITTEE ON THE FUTURE OF EMERGENCY ALERT AND WARNING SYSTEMS: RESEARCH DIRECTIONS
RAMESH RAO, University of California San Diego, Chair
JAMES CAVERLEE, Texas A&M University
ROOP DAVE, Information Technology Research Academy, New Delhi
EVE GRUNTFEST, California Polytechnic State University
BROOKE LIU, University of Maryland
LESLIE LUKE, Los Angeles County Office of Emergency Management
DENNIS MILETI, University of Colorado, Boulder
NAMBIRAJAN SESHADRI, Broadcom Corporation (retired)
DOUGLAS SICKER, Carnegie Mellon University
KATE STARBIRD, University of Washington
CHARLES L. WERNER, ParadeRest and Commonwealth of Virginia
JON EISENBERG, Director, Computer Science and Telecommunications Board
VIRGINIA BACON TALATI, Program Officer
KATIRIA ORTIZ, Research Associate
JANEL DEAR, Senior Program Assistant
COMPUTER SCIENCE AND TELECOMMUNICATIONS BOARD
FARNAM JAHANIAN, Carnegie Mellon University, Chair
LUIZ BARROSO, Google, Inc.
STEVEN M. BELLOVIN, NAE, 1 Columbia University
ROBERT F. BRAMMER, Brammer Technology, LLC
DAVID CULLER, NAE, University of California, Berkeley
EDWARD FRANK, Cloud Parity, Inc.
LAURA HAAS, NAE, University of Massachusetts, Amherst
MARK HOROWITZ, NAE, Stanford University
ERIC HORVITZ, NAE, Microsoft
VIJAY KUMAR, NAE, University of Pennsylvania
BETH MYNATT, Georgia Institute of Technology
CRAIG PARTRIDGE, Raytheon BBN Technologies
DANIELA RUS, NAE, Massachusetts Institute of Technology
FRED B. SCHNEIDER, NAE, Cornell University
MARGO SELTZER, Harvard University
MOSHE VARDI, NAS 2 /NAE, Rice University
KATHERINE YELICK, NAE, University of California, Berkeley
JON EISENBERG, Senior Director
LYNETTE I. MILLETT, Associate Director, CSTB, and Director, Cyber Resilience Forum
SHENAE BRADLEY, Administrative Assistant
EMILY GRUMBLING, Program Officer
RENEE HAWKINS, Financial and Administrative Manager
KATIRIA ORTIZ, Associate Program Officer
JANKI PATEL, Senior Program Assistant
For more information on CSTB, see its website at http://www.cstb.org , write to CSTB at National Academies of Sciences, Engineering and Medicine, 500 Fifth Street, NW, Washington, DC 20001, call (202) 334-2605, or email the CSTB at [email protected].
___________________
1 Member, National Academy of Engineering.
2 Member, National Academy of Sciences.
More than 60 years of research on disaster response has yielded many insights about how people respond to information indicating that they are at risk and under what circumstances they are most likely to take appropriate protective action. This work was largely done in the context of traditional media. The landscape for public alerts and warnings changed with the introduction of the Internet, mobile phones, and their applications, such as social media. Following a series of natural disasters, including Hurricane Katrina, that revealed shortcomings in the nation’s ability to effectively alert populations at risk, Congress passed the Warning, Alert, and Response Network (WARN) Act in 2006. This legislation encouraged the adoption of much newer technologies, including the dissemination of alerts and warning messages via mobile devices, which previous alerting technologies did not reach.
Less is known about how the use of new technologies for message dissemination and receipt changes the public response or alters how public safety officials can best employ the alerting capabilities. For example, fairly little is known about how to maximize the effectiveness of messages whose content is limited by technology constraints or policy decisions, or how best to make use of alerts and warnings in today’s information-rich environments. Additionally, formal study of the use of social media in disasters has been limited, and there are many outstanding questions, including how they can be used by government officials to both alert the public and gain situational awareness, the challenges and opportunities additional input from citizens provides, the associated
safety and privacy risks, and strategies for coping with rumors and also false information.
Research, including recent work sponsored by the Department of Homeland Security (DHS), has provided some insight into these issues. Additionally, the National Academies had previously convened three workshops under DHS sponsorship, one focusing on alerting via cell phones, one considering the use of social media, and one examining how to geographically target alerts and warnings. As part of this study, workshops were convened on August 9-10, 2016, and September 1, 2016. Workshop participants included DHS-supported researchers and other experts in disaster sociology, emergency response, and technologies. Additional briefings were held on November 1-2, 2016, January 26-27 2017, and March 23, 2017 ( Appendix C provides a list of briefings received).
This report reviews results from DHS-sponsored research ( Appendix B includes summaries of this work), the Academies workshops, and other sociotechnical research on the public response to alerts and warnings. Building on that review, the committee sets forth a research agenda that highlights areas where future research should be focused. ( Box P.1 contains the full statement of task.)
As the committee was wrapping up its work, the nation experienced a series of major natural disasters, with devastation from hurricanes Harvey, Irma, and Maria, and the October 1, 2017, shootings on the Las Vegas Strip. Each of these events was a sober reminder of the impacts of disasters on our communities and the important role that timely and effective communication with the public plays in responding to such events. Early reports on the October 2017 California wildfires further underscore
the importance of public alerting and potential benefits of enhancing the reach and effectiveness of the Wireless Emergency Alerts system, which allows public officials to deliver alerts to cell phones in an affected area.
We have attempted to outline a research agenda that not only examines questions about past disasters and recent technologies but also envisions what future integrated alert and warning technologies and systems might look like. As both natural and humanmade hazards occur with more frequency or severity, we hope that a future system will more readily adapt to a new set of hazards and more quickly integrate newer technologies.
Ramesh Rao, Chair Committee on the Future of Emergency Alert and Warning Systems: Research Directions
This page intentionally left blank.
Acknowledgment of Reviewers
This Consensus Study Report was reviewed in draft form by individuals chosen for their diverse perspectives and technical expertise. The purpose of this independent review is to provide candid and critical comments that will assist the National Academies of Sciences, Engineering, and Medicine in making each published report as sound as possible and to ensure that it meets the institutional standards for quality, objectivity, evidence, and responsiveness to the study charge. The review comments and draft manuscript remain confidential to protect the integrity of the deliberative process.
We wish to thank the following individuals for their review of this report:
Ellen Bass, Drexel University,
Art Botterell, California Governor’s Office of Emergency Services,
Louise K. Comfort, University of Pittsburgh,
Michael Ettenberg, NAE, 1 Dolce Technologies,
W. Craig Fugate, Federal Emergency Management Agency (retired),
Dale Hatfield, University of Colorado, Boulder,
Anthony (Tony) F. Lemieux, Georgia State University,
Craig Partridge, Raytheon BBN Technologies,
Francisco Sanchez, Harris County (Texas) Office of Homeland Security and Emergency Management,
Alberto Sangiovanni-Vincentelli, NAE, University of California, Berkeley, and
Sharon Wood, NAE, University of Texas, Austin.
Although the reviewers listed here provided many constructive comments and suggestions, they were not asked to endorse the conclusions or recommendations of this report nor did they see the final draft before its release. The review of this report was overseen by Phillip M. Neches, Teradata Corporation. He was responsible for making certain that an independent examination of this report was carried out in accordance with the standards of the National Academies and that all review comments were carefully considered. Responsibility for the final content rests entirely with the authoring committee and the National Academies.
1 UNDERSTANDING PUBLIC RESPONSE TO ALERTS AND WARNINGS
Results from Earlier Decades of Research
Recent Research
2 BUILDING AN INTEGRATED ALERT AND WARNING ECOSYSTEM
Need for an Integrated Alert and Warning Ecosystem
Properties of an Integrated Alert and Warning System
Evolution of an Integrated Alert and Warning Ecosystem
3 A RESEARCH AGENDA
Public Response to Alerts and Warnings
Post-Alert Feedback and Monitoring for Emergency Organizations
Technical Challenges and Their Impact
4 CHALLENGES TO BUILDING BETTER ALERTING SYSTEMS
Adoption of Alert and Warning Systems
Ever Changing Technology
Coupling Research with Emergency Managers and the Private Sector
Incentives to Participate
Limits in Forecasting
A Current Alert and Warning Systems and Their Characteristics
B Summaries of Research Results from DHS-Supported Principal Investigators
C Briefers to the Committee
Following a series of natural disasters, including Hurricane Katrina, that revealed shortcomings in the nation's ability to effectively alert populations at risk, Congress passed the Warning, Alert, and Response Network (WARN) Act in 2006. Today, new technologies such as smart phones and social media platforms offer new ways to communicate with the public, and the information ecosystem is much broader, including additional official channels, such as government social media accounts, opt-in short message service (SMS)-based alerting systems, and reverse 911 systems; less official channels, such as main stream media outlets and weather applications on connected devices; and unofficial channels, such as first person reports via social media. Traditional media have also taken advantage of these new tools, including their own mobile applications to extend their reach of beyond broadcast radio, television, and cable. Furthermore, private companies have begun to take advantage of the large amounts of data about users they possess to detect events and provide alerts and warnings and other hazard-related information to their users.
More than 60 years of research on the public response to alerts and warnings has yielded many insights about how people respond to information that they are at risk and the circumstances under which they are most likely to take appropriate protective action. Some, but not all, of these results have been used to inform the design and operation of alert and warning systems, and new insights continue to emerge. Emergency Alert and Warning Systems reviews the results of past research, considers new possibilities for realizing more effective alert and warning systems, explores how a more effective national alert and warning system might be created and some of the gaps in our present knowledge, and sets forth a research agenda to advance the nation's alert and warning capabilities.
READ FREE ONLINE
Welcome to OpenBook!
You're looking at OpenBook, NAP.edu's online reading room since 1999. Based on feedback from you, our users, we've made some improvements that make it easier than ever to read thousands of publications on our website.
Do you want to take a quick tour of the OpenBook's features?
Show this book's table of contents , where you can jump to any chapter by name.
...or use these buttons to go back to the previous chapter or skip to the next one.
Jump up to the previous page or down to the next one. Also, you can type in a page number and press Enter to go directly to that page in the book.
Switch between the Original Pages , where you can read the report as it appeared in print, and Text Pages for the web version, where you can highlight and search the text.
To search the entire text of this book, type in your search term here and press Enter .
Share a link to this book page on your preferred social network or via email.
View our suggested citation for this chapter.
Ready to take your reading offline? Click here to buy this book in print or download it as a free PDF, if available.
Get Email Updates
Do you enjoy reading reports from the Academies online for free ? Sign up for email notifications and we'll let you know about new publications in your areas of interest when they're released.
- Open access
- Published: 01 June 2023
The state of loneliness and social isolation research: current knowledge and future directions
- Harry Owen Taylor 1 ,
- Thomas K.M. Cudjoe 2 ,
- Feifei Bu 3 &
- Michelle H. Lim 4 , 5
BMC Public Health volume 23 , Article number: 1049 ( 2023 ) Cite this article
15k Accesses
21 Citations
129 Altmetric
Metrics details
In this editorial, we consider the current state of loneliness and social isolation research around the world, including knowledge gaps in the empirical literature.
Peer Review reports
For centuries, scholars have examined how social conditions influence human relationships and how these relationships influence health—from cell to society [ 1 , 2 ]. Two important features of research on social relationships include loneliness and social isolation. Loneliness is defined as a perceived/subjective condition in which an individual is dissatisfied with the quality and/or quantity of their social relationships [ 3 ]. Social isolation is an objective condition characterized by a lack of contact with other people and being disengaged from groups and social activities [ 3 ]. Loneliness and social isolation are sometimes misconstrued as the same phenomena in public discourse and media; however, previous research has shown they are distinct psychosocial constructs that are weakly to moderately correlated with each other [ 3 ]. As a result, it is possible to be lonely and socially isolated, lonely but not isolated, and isolated but not lonely. Additionally, loneliness and social isolation are mechanistically associated with different health outcomes [ 4 ].
Findings from empirical studies indicate increases in loneliness and/or social isolation are independently associated with poorer health [ 5 ]. Loneliness and social isolation have a mortality risk similar to cigarette smoking, alcohol consumption, physical inactivity, and obesity. Other health outcomes associated with these pernicious conditions include cardiovascular disease, dementia and cognitive decline, and worsening anxiety and depressive symptoms to name a few [ 5 ]. Perhaps most notable about this research is the consistency of findings, especially given the multitude of methods in operationalizing loneliness and social isolation, and the diversity of populations and contexts/settings in which these issues are studied [ 5 ].
Rates of loneliness and social isolation vary around the world. A recent meta-analysis on country-level differences found loneliness in adolescents was lowest in Southeast Asian countries and highest in Eastern Mediterranean countries [ 6 ]. From within Europe, loneliness was highest in Eastern European countries and lowest in Northern European countries [ 6 ]. Lim and colleagues [ 7 ] found 34% of adults in Australia were lonely, with 21% having episodic loneliness and 13% having chronic loneliness. In the United States, 43% of adults felt they lack companionship, 43% felt that their relationships are not meaningful, 43% felt isolated from others, and 39% no longer feel close to anyone [ 8 ]. There are fewer studies of country-level differences in social isolation for the general population; however, in Australia, 17% of the general population were classified as socially isolated, with 13% having episodic and 4% having chronic isolation [ 7 ]. Moreover, studies focused on the prevalence of social isolation are often conducted among older adults. A recent Canadian survey, for example, found approximately one out of every four older adults were socially isolated [ 9 ]. The COVID-19 pandemic has also brought issues of loneliness and isolation to the fore, especially given the enforcement of social distancing policies from local and federal governments. Evidence on the prevalence rates of loneliness and isolation during the COVID-19 pandemic are mixed with some finding increased rates, and others finding no difference to before the pandemic [ 10 , 11 , 12 ].
Given the negative health outcomes and overall prevalence of loneliness and social isolation around the world, we contend these are global public health issues. In many countries, there is investment in policy to ameliorate loneliness and social isolation. Notable movements to address loneliness and isolation include the Campaign to End Loneliness in the United Kingdom, Ending Loneliness Together in Australia, the Foundation for Social Connection in the United States, the World Health Organization’s Social Isolation and Loneliness initiatives, and the Global Initiative on Loneliness and Connection [ 13 ]. Other countries [ 5 ] have commissioned a body of expert scientific knowledge and policy work to better understand these issues. But loneliness and social isolation are not issues constrained to developed countries. In prevalence studies, these issues occur all over the world [ 6 , 14 ]; hence global policy and advocacy is sorely needed.
Nevertheless, there are notable gaps in the loneliness and social isolation research literature. There is substantially less research on loneliness and isolation among certain racial/ethnic groups, immigrant communities, diverse gender identities and sexual orientations, disability and neurodivergent population, populations with severe mental illness, people living in poverty, and other social/cultural groups. This is important given those at the greatest social disadvantage and marginalization may have the highest rates of loneliness and social isolation, and may also have heightened risk for becoming lonely and/or isolated [ 15 ].
Measurement/operationalization of loneliness and social isolation is also a topic of debate. If loneliness and social isolation are multidomained, how many types of loneliness and isolation are there? What items are important to include to accurately prove the psychometric reliability and validity of loneliness and isolation measurement tools, and how do we ensure that these tools are invariant across age? How do we know if loneliness and social isolation are perceived similarly across cultures? What novel methods exist for measuring loneliness and isolation? How often should we collect data on loneliness and social isolation in longitudinal studies to adequately capture fluctuations and temporal changes? Additionally, there is limited conceptual and empirical work on understanding the interrelationship(s) between loneliness and isolation [ 3 ]. This work would be useful for determining the causal mechanisms in which some individuals become lonely and/or isolated, for further understanding how loneliness and isolation influence health and wellbeing, and for the development of evidence-based interventions to address these psychosocial issues.
Lastly, it is important to use this knowledge to inform policy and interventions. What type of interventions, from individual-focused to societal-level, are most impactful, sustainable and/or cost-efficient? Should we use different types of interventions for preventing the onset of loneliness and isolation (primary prevention) versus mitigating these conditions among those who are chronically lonely and isolated (tertiary prevention)? And how do we scale-up these interventions to inform applied clinical or community practice and change public opinion/perceptions on loneliness and social isolation?
The aim of the BMC Public Health collection on loneliness and social isolation is to further our understanding of these psychosocial issues. We hope to propagate this collection of articles to advance research, practice, advocacy, and policy efforts by researchers, scientists, clinicians, policy-makers, community-based and non-profit organizations, governments, and the lay public around the world to facilitate greater social connection for better health and wellbeing for all.
Data Availability
Berkman LF, Glass T, Brissette I, Seeman TE. From social integration to health: Durkheim in the new millennium ☆ . Soc Sci Med. 2000;51(6):843–57. https://doi.org/10.1016/S0277-9536(00)00065-4 .
Article CAS PubMed Google Scholar
Cudjoe TKM, Selvakumar S, Chung SE, et al. Getting under the skin: social isolation and biological markers in the National Health and Aging Trends Study. J Am Geriatr Soc. 2022;70(2):408–14. https://doi.org/10.1111/jgs.17518 .
Article PubMed Google Scholar
Taylor HO. Social isolation’s influence on loneliness among older adults. Clin Soc Work J. 2020;48(1):140–51. https://doi.org/10.1007/s10615-019-00737-9 .
Holt-Lunstad J, Steptoe A. Social isolation: an underappreciated determinant of physical health. Curr Opin Psychol. 2022;43:232–7. https://doi.org/10.1016/j.copsyc.2021.07.012 .
National Academies of Sciences, Engineering, and, Medicine. Social isolation and loneliness in older adults: Opportunities for the Health Care System. National Academies Press; 2020.
Surkalim DL, Luo M, Eres R, et al. The prevalence of loneliness across 113 countries: systematic review and meta-analysis. BMJ. 2022;376:e067068. https://doi.org/10.1136/bmj-2021-067068 .
Article PubMed PubMed Central Google Scholar
Lim M, Manera K, Owen K, Phongsavan P, Smith B. Chronic and episodic loneliness and social isolation: prevalence and sociodemographic analyses from a longitudinal australian survey. Published online 2022. doi: https://doi.org/10.21203/rs.3.rs-1607036/v1 .
CIGNA. CIGNA U.S. Loneliness Index. ; 2018. https://www.cigna.com/static/www-cigna-com/docs/about-us/newsroom/studies-and-reports/combatting-loneliness/loneliness-survey-2018-full-report.pdf .
Gilmour H, Ramage-Morin PL. Social isolation and mortality among canadian seniors. Health Rep. 2020;31(3):27–38.
PubMed Google Scholar
Su Y, Rao W, Li M, Caron G, D’Arcy C, Meng X. Prevalence of loneliness and social isolation among older adults during the COVID-19 pandemic: a systematic review and meta-analysis. Int Psychogeriatr Published online 2022:1–13.
Bu F, Steptoe A, Fancourt D. Who is lonely in lockdown? Cross-cohort analyses of predictors of loneliness before and during the COVID-19 pandemic. Public Health. 2020;186:31–4. https://doi.org/10.1016/j.puhe.2020.06.036 .
Peng S, Roth AR. Social isolation and loneliness before and during the COVID-19 pandemic: a longitudinal study of US adults older than 50. J Gerontol Ser B. 2022;77(7):e185–90.
Article Google Scholar
Global Initiative on Loneliness and Connection. Position Statements on Addressing Social Isolation, Loneliness, and the Power of Human Connection. ; 2022. Accessed March 14, 2023. https://www.gilc.global/_files/ugd/410bdf_74fffc2d18984b0e8217288b1b12d199.pdf .
Teo RH, Cheng WH, Cheng LJ, Lau Y, Lau ST. Global prevalence of social isolation among community-dwelling older adults: a systematic review and meta-analysis. Arch Gerontol Geriatr. 2023;107:104904. https://doi.org/10.1016/j.archger.2022.104904 .
Madani MT, Madani L, Ghogomu ET, et al. Is equity considered in systematic reviews of interventions for mitigating social isolation and loneliness in older adults? BMC Public Health. 2022;22(1):2241. https://doi.org/10.1186/s12889-022-14667-8 .
Download references
Acknowledgements
Funding to HOT: USA National Institute of Health, National Institute of Aging: P30 AG072959. Funding to TKMC: supported by the National Institute on Aging 1K23 AG075191, the Johns Hopkins University Center for Innovative Medicine Human Aging Project as a Caryl & George Bernstein Scholar, and the Robert and Jane Meyerhoff Endowed Professorship.
Author information
Authors and affiliations.
Factor-Inwentash Faculty of Social Work, University of Toronto, Toronto, Canada
Harry Owen Taylor
Division of Geriatric Medicine and Gerontology, Johns Hopkins University School of Medicine, Baltimore, USA
Thomas K.M. Cudjoe
Research Department of Behavioural Science and Health, Insititute of Epidemiology & Health Care, University College London, London, England
Prevention Research Collaboration, Sydney School of Public Health, Charles Perkins Centre, The University of Sydney, Sydney, NSW, Australia
Michelle H. Lim
Iverson Health Innovation Research Institute, Swinburne University of Technology, Victoria, Australia
You can also search for this author in PubMed Google Scholar

Contributions
HOT is the first author. He wrote the first draft of the editorial and helped manage feedback and edits to the editorial. TKMC, FB, and MHL each reviewed the editorial and provided critique and feedback to the editorial.
Corresponding author
Correspondence to Harry Owen Taylor .
Ethics declarations
Ethics approval and consent to participate, consent for publication, competing interests, authors’ information (optional), additional information, publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Taylor, H.O., Cudjoe, T.K., Bu, F. et al. The state of loneliness and social isolation research: current knowledge and future directions. BMC Public Health 23 , 1049 (2023). https://doi.org/10.1186/s12889-023-15967-3
Download citation
Received : 23 March 2023
Accepted : 24 May 2023
Published : 01 June 2023
DOI : https://doi.org/10.1186/s12889-023-15967-3
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
BMC Public Health
ISSN: 1471-2458
- General enquiries: [email protected]
Trauma Informed Care in Medicine: Current Knowledge and Future Research Directions
- Family & Community Health 38(3):216-26

- University of Illinois at Chicago

- U.S. Department of Health and Human Services
- This person is not on ResearchGate, or hasn't claimed this research yet.
Abstract and Figures

Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations
- J CLIN PSYCHOL MED S

- Matthew J. Cordova
- PATIENT EDUC COUNS
- Beatriz Nicolau Soares
- Andreia Teixeira

- Taylor Brown
- Allison Fialkowski

- Jaqueline K. P. Niit
- Emilia Nerström

- COMMUNITY MENT HLT J

- Safal Kumar Paikray

- Pediatr Ann
- Kelsey L Jones
- Aubri M Milano
- Allison E Dunnigan
- Rachel A Fusco

- Charlotte Rees
- J TRAUMA STRESS

- ACAD EMERG MED
- MPH Deirdre Anglin MD

- AM J COMMUN PSYCHOL
- Rebecca Campbell

- William Miller
- Stephen Rollnick
- J AM ACAD CHILD PSY
- Frank W. Putnam
- AM POLIT SCI REV
- Michael Lipsky
- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Journal Proposal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu

- Subscribe SciFeed
- Recommended Articles
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
Digital twin framework for aircraft lifecycle management based on data-driven models.

1. Introduction
1.1. background and motivation, 1.2. existing methods and technologies in adt, 1.3. related works, 1.4. research gap and contributions of this study, 1.5. paper structure, 2. study framework for aircraft lifecycle management based on data-driven models, 2.1. framework development as the core methodology.
- Identification and analysis of key components necessary for an effective aircraft digital twin.
- Integration of cutting-edge technologies such as IoT, AI, and 6G into the framework.
- Development of novel models for data processing, simulation, and decision-making within the digital twin ecosystem.
- Design of supporting components to ensure the framework’s practical implementation.
2.2. Digital Twin Framework
2.3. lifecycle phases, 2.4. new technologies, 2.5. models for digital twins, 2.6. supporting components, 3.1. the challenge of creating a digital twin of an aircraft during technical operation and maintenance, 3.2. architecture of the aircraft digital twin ecosystem.
- Aircraft digital twin ecosystem.
- Aircraft health monitoring systems (AHMSs) with sensors embedded within the aircraft continuously collect data on various parameters such as structural integrity, engine performance, and environmental conditions. These data are crucial for updating the digital twin in real time.
- The digital twin is a virtual replica of the physical aircraft, continuously updated with data from the AHMS and other sources. It provides a real-time representation of the aircraft’s condition and is used for predictive maintenance, performance optimization, and operational planning.
- Aircraft manufacturers provide the initial digital model and design specifications that serve as the foundation for the digital twin. They also contribute data on component performance and manufacturing processes.
- Original equipment manufacturer (OEM) suppliers contribute data on specific parts and systems they produce, which are integrated into the digital twin to reflect the detailed behavior and lifecycle of each component.
- Airlines operate the aircraft and generate vast amounts of operational data, including usage patterns, flight hours, and maintenance records. These data are fed into the digital twin to enhance its accuracy and predictive capabilities.
- MRO providers are responsible for the upkeep and repair of the aircraft. They contribute data on maintenance activities, which is essential for maintaining an accurate digital twin and predicting future maintenance needs.
- Airports provide data on environmental conditions, runway usage, and other operational factors that affect the aircraft. This information is used to update the digital twin with relevant contextual data.
- Air traffic control (ATC) systems provide data on flight paths, airspace conditions, and other factors that impact the aircraft during flight. These data are integrated into the digital twin for real-time operational insights.
- Data aggregation by the AIoT platform, which collects data from various sources within the ADT ecosystem, including AHMS, MROs, airlines, and more.
- Advanced analytics integrated into the platform, which use AI and machine learning algorithms to analyze the aggregated data, identify patterns, predict failures, and optimize operational efficiency.
- Model training by the AIoT platform, which is also responsible for training machine learning models that are used within the digital twin to improve its predictive capabilities.
- Model updates in the process when each stakeholder trains a local model using its own data. The model updates (gradients) are then shared with a central server or aggregation mechanism.
- Central aggregation is the process where the central server aggregates these updates to create a global model, which is then distributed back to the stakeholders.
- Since raw data never leave the local environment, federated learning ensures that sensitive information remains secure while still benefiting from collaborative learning.
- Ultra-fast data transfer rates are provided by 6G, which are necessary for transmitting large volumes of data generated by AHMS and other sensors in real time.
- The low latency of 6G networks ensures that data are transmitted with minimal delay, enabling real-time updates of the digital twin and rapid response to emerging issues.
- Several 6G networks, including satellite communication across different orbits (LEO, MEO, GEO), provide continuous connectivity even in remote or high-altitude regions, ensuring that data flow uninterruptedly between the aircraft and the AIoT platform, essential for continuous data transmission in areas where terrestrial networks may not be available. This includes UAVs, airships, and high-altitude platforms that enhance connectivity and provide additional data collection capabilities, ensuring that the digital twin is updated with the latest information from the aircraft.
3.3. Distinguishing between the Aircraft Lifecycle and the Digital Twin Lifecycle
- The Aircraft Lifecycle.
- Physical vs. Virtual. The aircraft lifecycle deals with the tangible, physical aspects of the aircraft’s existence, from its construction to its eventual dismantling. In contrast, the digital twin lifecycle is virtual, driven by data and simulation rather than physical processes. The digital twin mirrors the aircraft, but it exists in a digital realm.
- Static vs. Dynamic. The aircraft lifecycle progresses through relatively static stages, each marked by discrete events such as production, operation, and maintenance. The digital twin, however, is a dynamic entity that evolves continuously throughout the aircraft’s lifecycle. It adapts to new data and changing conditions, making it a real-time tool for analysis and decision-making.
- Creation Timing. The digital twin is created in tandem with the aircraft but evolves more rapidly during the early phases. It provides real-time insights from the moment the aircraft is manufactured and continues to update and evolve with every new data input. The aircraft itself, by contrast, remains in a relatively fixed state during certain phases, particularly in operation and maintenance.
- Utility Beyond Decommissioning. While the aircraft lifecycle typically ends at decommissioning, the digital twin may continue to provide value after the aircraft has been retired. The data stored in the digital twin can be used for post-decommissioning analysis, informing the design and operational strategies of future aircraft models.
3.4. Lifecycle Phases as a Component of the ADT Framework
- Design Phase
- f s t r u c t denotes the function or algorithm that defines how the structural model processes the input variables. It could involve a set of equations or a computational method (e.g., finite element analysis) that describes the physical principles governing the aircraft’s structural behavior.
- f a e r o denotes the function or algorithm that defines how the aerodynamic model processes the input variables. This could involve a set of equations, such as those derived from Navier–Stokes equations, or a computational method like computational fluid dynamics that simulates the airflow and aerodynamic forces acting on the aircraft.
- f s y s t e m s denotes the function or algorithm that defines how the systems model processes the input variables. This function models the interactions and behaviors of the aircraft’s systems based on physical laws, system dynamics, and control algorithms.
- g denotes the function or algorithm that processes historical data to build the data-driven model. The function g could be a machine learning algorithm such as a neural network, regression model, decision tree, or any other statistical model that can learn from data.
- Y s i m represents the simulated outputs or results. It is the predicted behavior or performance metrics generated by the initial digital twin model M 0 when it processes the input conditions. Examples of Y s i m might include predicted stress levels in the structure, estimated aerodynamic forces, or expected system performance under specific conditions.
- X s i m refers to the input features or conditions used in the simulation. These are the specific variables or parameters that are fed into the digital twin model to simulate the aircraft’s behavior. X s i m could include factors like the aircraft’s speed, altitude, angle of attack, environmental conditions (such as temperature and pressure), and other relevant operational inputs.
3.5. Modern Technologies as Component of ADT Framework
- IoT sensors
- p t are physical parameters (e.g., temperature, pressure, vibration) affecting the sensor.
- ϵ i is noise or error in the sensor reading.
3.6. Models as Component of ADT Framework
- Physics-based models
3.7. Supporting Components in the ADT Framework
- Data management and integration
4. Discussion
4.1. differentiating digital twins from real-time monitoring systems.
- Digital twins use data-driven and physics-based models to predict future behaviors and potential failures. This predictive capability allows for proactive maintenance and optimization rather than reactive responses.
- A digital twin can simulate various operational scenarios and predict the outcomes of different decisions. This goes beyond simply monitoring the system in real time and allows stakeholders to test different approaches in a virtual environment.
- Digital twins provide insights that support strategic decision-making. They are not only concerned with monitoring but also assist in optimizing operations, improving efficiency, and reducing downtime through integrated analytics.
- Predictive Capabilities
4.2. Advantages of Hybrid Models over Standalone Data-Driven or Physics-Based Models
- Improved Predictive Accuracy
4.3. Decision-Making in Aviation Digital Twin Framework
- The predictive maintenance decision model aims to decide when and how maintenance should be performed to prevent failures and extend the lifespan of components. This model uses real-time and historical data to predict the remaining useful life of aircraft components, incorporating stochastic models such as the Weibull distribution and Bayesian updating to refine predictions. Based on these estimates, the model recommends optimal maintenance schedules, balancing the risks of failure against the costs of maintenance, enabling proactive maintenance, and reducing unplanned downtime.
- The operational optimization model focuses on optimizing flight operations for fuel efficiency, safety, and performance. Using real-time operational data, this model continuously adjusts flight parameters such as speed, altitude, and engine settings through optimization algorithms. The goal is to minimize fuel consumption while ensuring safety and compliance with operational constraints. The model provides real-time recommendations to pilots or autonomous systems, facilitating dynamic adjustments in response to changing environmental factors.
- The design iteration decision model integrates feedback loops from various lifecycle phases, including operation, maintenance, and production, to improve aircraft design based on operational feedback and evolving technological requirements. This model employs regression analysis and machine learning to identify design elements that need improvement and to predict the impact of potential design changes. Engineers can then use these insights to iterate on the design, ensuring continuous improvement over successive generations of the aircraft.
- In the case of emergencies or anomalies during flight, the incident response decision model uses real-time data and scenario simulations to evaluate different response strategies. Incorporating decision trees and risk assessment algorithms, this model determines the best course of action, providing immediate recommendations to the flight crew or autonomous systems to minimize risk and ensure safety.
- The lifecycle cost management model is designed to optimize the total cost of ownership of the aircraft throughout its lifecycle. By integrating data from all lifecycle phases, this model uses cost modeling and optimization techniques to forecast and minimize lifecycle costs, considering factors such as fuel consumption, maintenance expenses, and depreciation. Strategic recommendations are then provided to management, aiding in investment decisions, budget planning, and the scheduling of upgrades or replacements based on cost-benefit analysis.
4.4. Knowledge-Driven Framework of Aircraft Digital Twins
4.5. challenges and limitations in implementing aircraft digital twins, 4.6. future directions of research, 5. conclusions, data availability statement, conflicts of interest.
- Jones, D.; Snider, C.; Nassehi, A.; Yon, J.; Hicks, B. Characterising the digital twin: A systematic literature review. CIRP J. Manuf. Sci. Technol. 2020 , 29 , 36–52. [ Google Scholar ] [ CrossRef ]
- Hochhalter, J.; Leser, W.P.; Newman, J.A.; Gupta, V.K.; Yamakov, V.; Cornell, S.R.; Willard, S.A.; Heber, G. Coupling Damage-Sensing Particles to the Digitial Twin Concept ; Technical Memorandum NASA/TM–2014-218257; NASA—National Aeronautics and Space Administration: Washington, DC, USA, 2014.
- Richstein, R.; Schröder, K.-U. Characterizing the Digital Twin in Structural Mechanics. Designs 2024 , 8 , 8. [ Google Scholar ] [ CrossRef ]
- Arthur, R.; French, M.; Ganguli, J.; Kinard, D.A.; Kraft, E.; Marks, I.; Matlik, J.; Fischer, O.; Sangid, M.; Seal, D.; et al. Digital Twin: Definition & Value—AIAA and AIA Position Paper. AIAA Digital Engineering Integration Committee. 2020. Available online: https://www.aia-aerospace.org/publications/digital-twin-definition-value-an-aiaa-and-aia-position-paper/ (accessed on 30 August 2024).
- Li, L.; Aslam, S.; Wileman, A.; Perinpanayagam, S. Digital Twin in Aerospace Industry: A Gentle Introduction. IEEE Access 2022 , 10 , 9543–9562. [ Google Scholar ] [ CrossRef ]
- Chen, X.; Riaz, A.; Guenov, M.D. Cloud-based environment for aircraft design collaboration. In Proceedings of the 32nd Congress of the International Council of the Aeronautical Sciences, Online, 6–10 September 2021. [ Google Scholar ]
- Benaouali, A.; Kachel, S. Multidisciplinary design optimization of aircraft wing using commercial software integration. Aerosp. Sci. Technol. 2019 , 92 , 766–776. [ Google Scholar ] [ CrossRef ]
- Kochkov, D.; Smith, J.A.; Alieva, A.; Wang, Q.; Brenner, M.P.; Hoyer, S. Machine learning–accelerated computational fluid dynamics. Proc. Natl. Acad. Sci. USA 2021 , 118 , e2101784118. [ Google Scholar ] [ CrossRef ]
- Vurtur Badarinath, P.; Chierichetti, M.; Davoudi Kakhki, F. A Machine Learning Approach as a Surrogate for a Finite Element Analysis: Status of Research and Application to One Dimensional Systems. Sensors 2021 , 21 , 1654. [ Google Scholar ] [ CrossRef ]
- Zhang, L.; Cheng, L.; Li, H.; Gao, J.; Yu, C.; Domel, R.; Yang, Y.; Tang, S.; Liu, W.K. Hierarchical deep-learning neural networks: Finite elements and beyond. Comput. Mech. 2021 , 67 , 207–230. [ Google Scholar ] [ CrossRef ]
- Tavares, S.M.O.; Ribeiro, J.A.; Ribeiro, B.A.; de Castro, P.M.S.T. Aircraft Structural Design and Life-Cycle Assessment through Digital Twins. Designs 2024 , 8 , 29. [ Google Scholar ] [ CrossRef ]
- Srivastava, A.N. Greener aviation with virtual sensors: A case study. Data Min. Knowl. Discov. 2012 , 24 , 443–471. [ Google Scholar ] [ CrossRef ]
- Liu, X.; Jiang, D.; Tao, B.; Xiang, F.; Jiang, G.; Sun, Y.; Kong, J.; Li, G. A systematic review of digital twin about physical entities, virtual models, twin data, and applications. Adv. Eng. Inform. 2023 , 55 , 101876. [ Google Scholar ] [ CrossRef ]
- Fentaye, A.D.; Gilani, S.I.U.-H.; Baheta, A.T.; Li, Y.-G. Performance-based fault diagnosis of a gas turbine engine using an integrated support vector machine and artificial neural network method. Proc. Inst. Mech. Eng. Part A J. Power Energy 2019 , 233 , 786–802. [ Google Scholar ] [ CrossRef ]
- Lu, F.; Jiang, C.; Huang, J.; Wang, Y.; You, C. A Novel Data Hierarchical Fusion Method for Gas Turbine Engine Performance Fault Diagnosis. Energies 2016 , 9 , 828. [ Google Scholar ] [ CrossRef ]
- Xiong, M.; Wang, H.; Fu, Q.; Xu, Y. Digital twin–driven aero-engine intelligent predictive maintenance. Int. J. Adv. Manuf. Technol. 2021 , 114 , 3751–3761. [ Google Scholar ] [ CrossRef ]
- Zhou, L.; Wang, H.; Xu, S. Aero-engine gas path system health assessment based on depth digital twin. Eng. Fail. Anal. 2022 , 142 , 106790. [ Google Scholar ] [ CrossRef ]
- Yanhua, M.A.; Xian, D.U.; Ximing, S.U. Adaptive modification of turbofan engine nonlinear model based on LSTM neural networks and hybrid optimization method. Chin. J. Aeronaut. 2022 , 35 , 314–332. [ Google Scholar ] [ CrossRef ]
- Bondarenko, O.; Fukuda, T. Development of a diesel engine’s digital twin for predicting propulsion system dynamics. Energy 2020 , 196 , 117126. [ Google Scholar ] [ CrossRef ]
- Wang, Z.; Wang, Y.; Wang, X.; Yang, K.; Zhao, Y. A Novel Digital Twin Framework for Aeroengine Performance Diagnosis. Aerospace 2023 , 10 , 789. [ Google Scholar ] [ CrossRef ]
- Zaccaria, V.; Stenfelt, M.; Aslanidou, I.; Kyprianidis, K.G. Fleet monitoring and diagnostics framework based on digital twin of aeroengines. In Proceedings of the ASME Turbo Expo, Oslo, Norway, 11–15 June 2018; Volume 6. [ Google Scholar ] [ CrossRef ]
- Yang, Y.; Ma, M.; Zhou, Z.; Sun, C.; Yan, R. Dynamic model-based digital twin for crack detection of aeroengine disk. In Proceedings of the 2021 International Conference on Sensing, Measurement & Data Analytics in the Era of Artificial Intelligence (ICSMD), Chongqing, China, 15–17 October 2021; pp. 1–6. [ Google Scholar ] [ CrossRef ]
- Wang, T.; Liu, Z.; Liao, M.; Mrad, N. Life prediction for aircraft structure based on Bayesian inference: Towards a digital twin ecosystem. In Proceedings of the Annual Conference of the PHM Society, Virtual, 9–13 November 2020; Volume 12, p. 8. [ Google Scholar ] [ CrossRef ]
- Chowdhury, S.H.; Ali, F.; Jennions, I.K. A methodology for the experimental validation of an aircraft ECS digital twin targeting system level diagnostics. In Proceedings of the Annual Conference of the PHM Society, Scottsdale, AZ, USA, 21–26 September 2019. [ Google Scholar ]
- Ezhilarasu, C.M.; Jennions, I.K. A System-Level Failure Propagation Detectability Using ANFIS for an Aircraft Electrical Power System. Appl. Sci. 2020 , 10 , 2854. [ Google Scholar ] [ CrossRef ]
- Ezhilarasu, C.M.; Jennions, I.K. Development and implementation of a framework for aerospace vehicle reasoning (FAVER). IEEE Access 2021 , 9 , 108028–108048. [ Google Scholar ] [ CrossRef ]
- Ezhilarasu, C.M.; Skaf, Z.; Jennions, I.K. A generalised methodology for the diagnosis of aircraft systems. IEEE Access 2021 , 9 , 11437–11454. [ Google Scholar ] [ CrossRef ]
- Ramesh, G.; Garza, P.; Perinpanayagam, S. Digital simulation and identification of faults with neural network reasoners in brushed actuators employed in an E-brake system. Appl. Sci. 2021 , 11 , 9171. [ Google Scholar ] [ CrossRef ]
- Huang, Y.; Tao, J.; Sun, G.; Wu, T.; Yu, L.; Zhao, X. A novel digital twin approach based on deep multimodal information fusion for aero-engine fault diagnosis. Energy 2023 , 270 , 126894. [ Google Scholar ] [ CrossRef ]
- Hazbon Alvarez, O.; Gutierrez Zea, L.; Bil, C.; Napolitano, M.; Fravolini, M.L. Digital twin concept for aircraft sensor failure. In Advances in Transdisciplinary Engineering ; IOS Press: Amsterdam, The Netherlands, 2019; Volume 10, pp. 370–379. [ Google Scholar ] [ CrossRef ]
- Peng, C.-C.; Chen, Y.-H. Digital twins-based online monitoring of TFE-731 turbofan engine using fast orthogonal search. IEEE Syst. J. 2021 , 16 , 3060–3071. [ Google Scholar ] [ CrossRef ]
- Lufthansa Technik. AVIATAR. Available online: https://www.lufthansa-technik.com/de/aviatar (accessed on 30 August 2024).
- Airbus. Skywise. Available online: https://aircraft.airbus.com/en/services/enhance/skywise (accessed on 30 August 2024).
- GE Digital. PREDIX Analytics Framework. Available online: https://www.ge.com/digital/documentation/predix-platforms/afs-overview.html (accessed on 30 August 2024).
- AFI KLM E&M. PROGNOS—Predictive Maintenance. Available online: https://www.afiklmem.com/en/solutions/about-prognos (accessed on 30 August 2024).
- Boeing Global Services. Enhanced Digital Solutions Focus on Customer Speed and Operational Efficiency. Available online: https://investors.boeing.com/investors/news/press-release-details/2018/Boeing-Global-Services-Enhanced-Digital-Solutions-Focus-on-Customer-Speed-and-Operational-Efficiency/default.aspx (accessed on 30 August 2024).
- Kabashkin, I.; Shoshin, L. Artificial Intelligence of Things as New Paradigm in Aviation Health Monitoring Systems. Future Internet 2024 , 16 , 276. [ Google Scholar ] [ CrossRef ]
- Grieves, M.; Vickers, J. Digital Twin: Mitigating Unpredictable, Undesirable Emergent Behavior in Complex Systems. In Transdisciplinary Perspectives on Complex Systems ; Kahlen, J., Flumerfelt, S., Alves, A., Eds.; Springer: Cham, Switzerland, 2017; pp. 85–113. [ Google Scholar ] [ CrossRef ]
- Airbus. Airbus Annual Report: Overview 2019. Airbus SE. 2019. Available online: https://www.airbus.com/sites/g/files/jlcbta136/files/2021-07/Airbus-Overview-2019.pdf (accessed on 16 September 2024).
- van Dinter, R.; Tekinerdogan, B.; Catal, C. Predictive Maintenance Using Digital Twins: A Systematic Literature Review. Inf. Softw. Technol. 2022 , 151 , 107008. [ Google Scholar ] [ CrossRef ]
- Rolls-Royce. Rolls-Royce Launches IntelligentEngine. 5 February 2018. Available online: https://www.rolls-royce.com/media/press-releases/2018/05-02-2018-rr-launches-intelligentengine.aspx (accessed on 26 February 2024).
- SGI Aviation. Aircraft Decommissioning Study. Final Report Prepared for IATA. May 2018. Available online: https://www.sgiaviation.com/wp-content/uploads/2020/03/IATA_Aircraft_Decommissioning_Study_May-2018.pdf (accessed on 16 September 2024).
Click here to enlarge figure
| Symbols | Definition |
|---|---|
| Model parameter that represents the set of parameters that define the digital twin’s behavior, such as structural properties, aerodynamic coefficients, and system performance metrics. | |
| Initial digital twin model created during the design phase, incorporating physics-based models, data-driven models, and initial conditions. | |
| The structural model of the digital twin. It is a specific model that focuses on simulating the structural dynamics and behavior of the aircraft. This model includes aspects such as how the aircraft’s frame and materials respond to various forces, stresses, and environmental conditions. | |
| The aerodynamic model of the digital twin. It is a specific model that focuses on simulating the aerodynamic behavior of the aircraft. This model would typically include calculations related to how air flows around the aircraft, the forces generated by this airflow (like lift and drag), and how these forces affect the aircraft’s performance. | |
| The systems model of the digital twin. It focuses on simulating the behavior and performance of various onboard systems of the aircraft, such as the propulsion system, avionics, electrical systems, hydraulic systems, and other critical components that ensure the aircraft’s functionality. | |
| The data-driven model within the digital twin framework. This model is based on empirical data and statistical or machine learning methods rather than purely physics-based equations. It is used to predict the behavior of the aircraft by learning from historical data patterns. | |
| The input features or conditions relevant to the structural model. These inputs could include material properties (such as Young’s modulus, Poisson’s ratio, and material density), geometric properties (such as dimensions of the aircraft’s components, thickness of materials, and cross-sectional areas), loading conditions (such as external forces, moments, pressure distributions, and thermal loads), and boundary conditions (such as fixed supports, constraints, and connections between components). | |
| The input features or conditions relevant to the aerodynamic model. These inputs could include flight conditions (such as airspeed, altitude, angle of attack, and Mach number), aircraft geometry (such as the shape and size of the wings, fuselage, and control surfaces), environmental conditions (such as air density, temperature, and atmospheric pressure), and control inputs (such as deflections of control surfaces (e.g., ailerons, elevators, rudders)). | |
| The input features or conditions relevant to the systems model. These inputs could include system configurations (such as engine settings, hydraulic pressures, and electrical loads), control inputs (such as throttle position, autopilot settings, and actuator commands), environmental conditions (such as temperature, altitude, and external forces that might impact system performance), and operational condition (such as flight phase and power demands). | |
| The historical data inputs that are used to train or inform the data-driven model. These inputs might include past operational data (such as flight logs, performance metrics, and environmental conditions experienced by the aircraft over time), maintenance records (information on past repairs, inspections, and component replacements), failure data (instances of system or component failures and the conditions under which they occurred), and usage patterns (data on how the aircraft has been used over time, including flight hours, routes, and load factors). | |
| Real-time data at time —the set of data collected from sensors and systems at a specific time ttt, including operational and environmental conditions. | |
| Feature vector at time —a vector representing the input features or conditions observed at time ttt, such as sensor readings, environmental factors, and operational parameters. | |
| Target variable at time —the observed output or target variable at time ttt, such as system performance metrics, component wear levels, or other measurable outcomes. | |
| The loss function is a function that measures the difference between the predicted outcomes and the actual observed outcomes, used to optimize the model parameters. | |
| Gradient of the loss function with respect to , which represents the direction and rate of change in the loss function with respect to the model parameters , used in optimization algorithms. | |
| Learning rate—a scalar value that controls the step size in the gradient descent optimization process, determining how much the model parameters are adjusted at each iteration. | |
| Local model update for stakeholder at time —the change in model parameters computed by stakeholder based on local data and used in federated learning to update the global model. | |
| Global model parameters at time —the set of model parameters that define the state of the digital twin at a specific time , updated continuously through federated learning and real-time data integration. | |
| The time to failure of the component or system. It is a random variable that represents the point in time when the failure is expected to occur. | |
| Predicted time to failure—the estimated time at which a component or system is expected to fail, based on current operational conditions and historical data. | |
| The objective function is a function representing the goal of optimization (e.g., minimizing fuel consumption, maximizing performance) as a function of the model parameters and current conditions. | |
| The cost function for maintenance is a function that represents the cost associated with maintenance activities, depending on the predicted time to failure and other factors. | |
| Constraints—a set of conditions or limits (e.g., safety regulations, operational limits) that must be satisfied during optimization. | |
| Anomaly score—the squared difference between the observed outcomes and the predicted outcomes, used to detect deviations from normal behavior. |
| The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
Share and Cite
Kabashkin, I. Digital Twin Framework for Aircraft Lifecycle Management Based on Data-Driven Models. Mathematics 2024 , 12 , 2979. https://doi.org/10.3390/math12192979
Kabashkin I. Digital Twin Framework for Aircraft Lifecycle Management Based on Data-Driven Models. Mathematics . 2024; 12(19):2979. https://doi.org/10.3390/math12192979
Kabashkin, Igor. 2024. "Digital Twin Framework for Aircraft Lifecycle Management Based on Data-Driven Models" Mathematics 12, no. 19: 2979. https://doi.org/10.3390/math12192979
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
Bibliometric analysis of endoplasmic reticulum stress in hepatocellular carcinoma: trends and future directions
- Open access
- Published: 27 September 2024
- Volume 15 , article number 481 , ( 2024 )
Cite this article
You have full access to this open access article

- Yaping Zhang 1 ,
- Yinting Tian 2 ,
- Zheyuan Wang 2 ,
- Yawu Zhang 2 &
- Gennian Wang 2
31 Accesses
Explore all metrics
Over the past three decades, endoplasmic reticulum (ER) stress has gained considerable attention in the field of hepatocellular carcinoma (HCC) with an increasing number of publications. It is crucial to reveal the global status, research hotspots and future research trends of ER stress in HCC. The aim of this study is to analyze the publications related to ER stress in HCC through bibliometric analysis in order to better understand the current status of ER stress research in HCC and to identify potential new research directions.
In this study, articles and reviews on ER stress in HCC up to December 31, 2023 were searched and downloaded from the Science Citation Index-Expanded (SCIE) of the Web of Science Core Collection (WoSCC), Pubmed, Scopus and Embase databases. Using CiteSpace 6.2.R6, VOSviewer 1.6.19, Scimago Graphica and Microsoft Office Excel 2019, the knowledge networks of a variety of countries, regions, authors, references, keywords and journals were analyzed.
A total of 1239 publications were retrieved, including 843 articles and 396 review articles. The number of global publications is increasing every year, with the majority of publications coming from China and the USA. Ih-Jen Su, Wenya Huang and Wei Wei are the top 3 prolific authors. “Progression”, “inflammation”, “cell cycle arrest”, “metabolism”, “snsignaling pathways”, “pathogenesis” and “non-alcoholic fatty liver disease” have emerged as research hotspots in recent years. The journal with the greatest co-citation is Hepatology.
Conclusions: Based on current global trends, the total number of publications on ER stress in HCC research will continue to increase, but there is a need for more cooperation between authors and countries/regions. ER stress in HCC will continue to be a research priority.
Conclusions
Based on current global trends, the total number of publications on ER stress in HCC research will continue to increase, but there is a need for more cooperation between authors and countries/regions. ER stress in HCC will continue to be a research priority.
Avoid common mistakes on your manuscript.
1 Introduction
HCC is one of the leading causes of cancer-related deaths worldwide. Currently, treatments for HCC include surgery, radiofrequency ablation, chemotherapy and immunotherapy. Despite advancements in treatment options, the high rate of recurrence and metastasis in HCC patients remains a significant challenge that necessitates urgent attention. The specific mechanisms underlying HCC recurrence and metastasis post-treatment are not yet fully elucidated, highlighting the pressing need for further research in this area [ 1 , 2 , 3 ].
The ER is an important membrane organelle with secretory functions that are essential for maintaining normal physiological functions in eukaryotic cells. It plays an important role in many intracellular biochemical reactions, including protein synthesis, transport, modification and processing, lipid secretion, detoxification, and maintenance of calcium homeostasis [ 4 , 5 , 6 ]. However, under physiological or pathological conditions, proteins can become misfolded or unfolded due to various factors such as hypoxia, nutrient deficiency, energy deficiency, oxidative stress, altered glycosylation, calcium imbalance, and DNA damage. These disruptions in protein folding efficiency result in the accumulation of misfolded or unfolded proteins within the cells. As a response to these stressors, the ER initiates a series of signals known as ER stress. The activation of ER stress signifies the cell’s attempt to cope with the increased burden of misfolded proteins. This cascade of signals serves as a protective mechanism to restore protein folding homeostasis and promote cell survival. However, sustained or severe ER stress can lead to cell dysfunction and ultimately cell death [ 8 , 9 ]. In recent years, research has shown that ER stress is connected to the onset, advancement, and resistance to medication of HCC. A thorough comprehension of the connection between ER stress and HCC could be crucial for creating innovative treatments and enhancing outlook [ 10 ].
Bibliometric analysis is a method of statistical and quantitative analysis of scholarly publications [ 11 ]. However, there is still a lack of the bibliometric analysis on ER stress in HCC. In this study, a comprehensive bibliometric analysis related to ER stress in HCC was carried out using CiteSpace and VOS viewer, aiming to provide new clues and ideas for the future research.
2 Materials and methods
2.1 data collection.
For this study, all relevant publications on ER stress in HCC from January 1, 2001 to December 31, 2023 using the WoSCC, Pubmed, Scopus and Embase databases were systematically retrieved. The search term employed was TS= (“endoplasmic reticulum stress” OR “ER stress”AND “primary hepatic cancer” OR “primary liver cancer” OR “hepatocellular carcinoma” OR “malignant hepatoma” OR “primary liver carcinoma” OR “primary hepatic carcinoma” OR “HCC”). The topic words were searched for MeSH terms in the NCBI database and only articles and review articles were considered for subsequent analysis and visualization. Non-English publications, early access, meeting abstract, editorial material, correction, book chapter, note, letter, retracted publication were excluded. The initial literature was screened by two independent reviewers (YT and YZ), duplicates and irrelevant studies were removed, and disagreements were resolved by a third reviewer (GW).
2.2 Statistical methods
In this study, the full records publications retrieved from the WoSCC, Pubmed, Scopus and Embase databases with cited references were exported. The characteristics of publications were analyzed and visualized using Microsoft Office Excel 2019 and Scimago Graphica [ 12 ]. VOSviewer 1.6.19 was used to explore collaboration networks between countries/regions, authors, references, keywords and journals [ 13 ]. CiteSpace 6.2.R6 was used for the burst analysis of references and keywords [ 14 ]. Figure 1 demonstrates how data selection and analysis were carried out.

The flowchart of data selection and analysis process
3.1 The overall trend of publication
A total of 3304 publications were retrieved, and a total of 1239 articles and reviews were analyzed and visualized (Fig. 1 ). As shown in Fig. 2 , these papers were published between 2001 and 2023, and there were fewer than 10 publications per year from 2001 to 2006, which is relatively low for this period. Since 2007, the publications have gradually increased. According to our fitting, the number of publications and the year were statistically significantly related (R 2 = 0.9622), indicating an increasing attention and interest in the study of ER stress in HCC.

The annual publication trend of ER stress in HCC
3.2 Co-authorship analysis of countries/regions
Figure 3 A shows the network map of publications and the cooperation among different countries/regions. Among the countries with the most publications, China has the most, followed closely by the USA. Additionally, China exhibits the strongest partnership with the USA. Figure 3 B also shows that China and the USA are the countries with the most publications on ER stress in HCC and what’s more, Russia, Iran, India, Iraq, Finland, Egypt and China showed more interesting in the study of ER stress in HCC in recent years. Figure 3 C illustrates the network map of the citation frequency of publications from different countries/regions, indicating that publications from France, Austria, Chile, Portugal, Greece, the USA, Germany, Italy, and Span were cited more frequently. What’ more, as shown in Supplementary Fig. 1, China, the USA, Germany, South Korea, France and Brazil were marked with purples, indicating that they had a greater centrality and played a particularly important role in this field. The characteristics of the top 10 countries/regions with the greatest number of publications are shown in Table 1 .

The network map of worldwide spread and collaboration of ER stress in HCC research. A The global geographical distribution of publications. B An overlay map of publications in different countries/regions. C A map overlay displaying the distribution of published citations across various countries/regions. Countries/regions are represented by nodes, and the strength of collaboration between different countries is indicated by the thickness of the lines. The larger the node is, the more papers that are published. The colors vary from blue (representing the lowest score) to green and finally to yellow (indicating the highest score)
3.3 Co-authorship analysis of institutions
In total, 1598 institutions participated in these publications, and 136 institutions with more than 5 publications were selected to conduct co-authorship analyses using VOSviewer. Figure 4 A shows the cooperation network of different institutions. Different color represents different clusters. All the institutions are divided into 8 clusters and 5 of them have no cooperation with each other (Fig. 4 A). In the analysis of institutional overlay map, we observed that institutions had fewer publications before 2014 but increased their interest and publication output in the field thereafter (Fig. 4 B). As shown in Supplementary Fig. 2, Chinese Academy of Sciences, Institut National de la Sante et de la Recherche Medicale (inserm), the University of Texas System, Fudan University, National Health Research Institutes, the National Institutes of Health and Nanjing University are marked with purple circles which mean that they had a centrality over 0.1. Interestingly, although the National Health Research Institutes had only 12 publications and Fudan University had only 6 publications, their centrality reached up to 0.11. Table 1 shows the characteristics of the top 10 institutions with the most publications.

The network map of institutions of ER stress in HCC research. A A network map of institutions engaged in ER stress in HCC. Different colors represent different clusters. B An overlay map of publications in different institutions. Institutions are represented by nodes and the strength of collaboration between different countries/regions is indicated by the thickness of the lines. The larger the node is, the more publications there are. The colors vary from blue (representing the lowest score) to green and finally to yellow (indicating the highest score)
3.4 Co-authorship analysis of authors
A total of 7250 authors have contributed to the study of ER stress in HCC, and 65 authors had more than 5 publications were chosen for co-authorship analysis by the use of VOSviewer. Figure 5 A shows the cooperation network of different authors. Different color represents different clusters. All the authors are divided into 16 clusters based on their collaborative relationships. Figure 5 B shows the density map of different authors. Figure 5 C and D show the publications over year and the citation frequency of publications, respectively. Ih-Jen Su from National Health Research Institutes had the greatest number of publications ( n = 19) followed by Huang wenya ( n = 18). However, the collaborative relationship between authors is not strong. The characteristics of the top 10 authors with the greatest number of publications are shown in Table 2 .

Analysis of co-authorship of authors. A The network map of co-authorship of authors. Different colors represent different clusters. B An density map of co-authorship of authors. C An overlay map of co-authorship of authors over year. D An overlay map of frequency of citations of authors. The authors are symbolized by the nodes, and the strength of the connections between different authors indicates the level of their collaboration. The larger the node is, the more papers that are published. The colors vary from blue (representing the lowest score) to green and finally to yellow (indicating the highest score)
3.5 Co-cited references analysis
A total of 74,359 references were included in this study and the references with a minimum citation of 30 were visualized via VOSviewer (Fig. 6 A). As shown in Fig. 6 A, “shuda m, 2003, j heptol, v38” was the reference with the greatest citation ( n = 121) followed by “malhi h, 2011, j heptol, v54” ( n = 100). Additionally, citation burst analysis using CiteSpace was conducted to identify the 25 strongest references with the strongest burst (Fig. 6 B). From the Fig. 6 B, we can find that “malhi h, 2011, j heptol, v54” is also the reference with the strongest burst citation (strength = 19.36). 10 out of 25 references were still in burst. The details of the top 10 co-cited references are shown in Table 3 .

Analysis of Co-cited references. A VOSviewer generates a network map of co-cited references. The nodes symbolize co-cited sources, while the thickness of the lines connecting distinct references indicates the strength of their relationship. The larger the node is, the more frequently the reference is cited. Different colors represent different clusters. B The top 25 references exhibiting the most significant citation bursts as identified by CiteSpace. Strength is a measure of the strength of citation bursts, and it is proportional to the number of bursts. The reference was published is indicated by the blue bars, while the red bars indicate citation burstness
Keyword Co-occurrence analysis .
VOSviewer was used to extract 134 keywords with greater than 5 occurrences from the author keywords (Fig. 7 A). “Apoptosis” is the keyword with the greatest occurrence followed by “autophagy” (Fig. 7 A). The top 25 keywords with the strongest citation bursts were analyzed by Citespace (Fig. 7 B). In addition, up to 2023, keywords “hepatocellular carcinoma”(strength = 5.6), “progression”(strength = 4.81), “inflammation”(strength = 4.78), “cell cycle arrest” (strength = 4.05), “metabolism” (strength = 3.71), “signaling pathways”(strength = 6.14), “risk”(strength = 5.83), “pathogenesis”(strength = 5.41) “non-alcoholic fatty liver disease”(strength = 5.07), “pathogenesis”(strength = 4.49), “liver cancer”(strength = 4.25) were still in burst.

Analysis of the co-occurrence of keywords. A VOSviewer generates an overlay network map of keywords that have at least 10 co-occurrences. Keywords are symbolized by nodes, and the strength of the connections between different keywords is depicted by the thickness of the lines. The colors vary from blue (representing the lowest score) to green and finally to yellow (indicating the highest score). B The top 25 keywords exhibiting the most significant citation bursts as identified by CiteSpace. Strength is a measure of the strength of citation bursts, and it is proportional to the number of bursts. Keyword occurrence is represented by the blue bars, while citation burstness is represented by the red bars
3.6 Journal analysis
In this study, a total of 5931 journals with a minimum of 300 citations on the subject of ER stress in HCC were analyzed using VOSviewer. Figure 8 A shows the cation relationship between journals and the density map also shows the most cited journals (Fig. 8 B). As shown in Table 4 , among the top 10 co-cited journals, 8 journals were at the Q1 JCR division and were from the USA. 7 journals with an Impact Factor (IF) of more than 10. Hepatology has the most co-citations, followed by the Journal of Biological Chemistry and Journal of Hepatology.

The analysis of co-cited journals. A A diagram displaying the interconnections between journals that are frequently cited together. The citations of publications in various journals are represented by the nodes, while the strength of the connections between different journals is indicated by the width of the lines. Different colors represent different clusters. B Density visualization of co-cited journals. The color at each point indicates the density of citations of the journal. The colors vary from blue (representing the lowest score) to green and finally to yellow (indicating the highest score)
4 Discussion
4.1 global trends on er stress in hcc.
In this study, we analyzed publications related to ER stress in HCC from 2001 to 2023, and a total of 843 articles and 396 review articles were included in this study. As shown in Fig. 2 , ER stress research has received considerable attention in recent years, with a general upward trend in the number of publications related to this topic.
4.2 Countries/regions
As shown in Fig. 3 , China ranks the first in terms of the number of publications, followed by the USA, and there is close cooperation between the two countries. However, despite the fact that there are more publications in China than in the USA, the frequency of citations for publications of the USA is higher than that of China, suggesting that their articles may have a higher impact. Surprisingly, despite having fewer publications, France, Austria, Chile, Portugal and Greece were cited more frequently than China and the USA, suggesting that these countries may have higher quality research results. Although China and the USA have many elite institutions and researchers, more efforts are needed to improve the quality of research in this field. The academic exchanges between different countries/regions should be strengthened.
There are some successful examples of international collaboration in the medical fields. One of them is the Human Genome Project, which involved researchers from multiple countries working together to map the entire human genome and set a precedent for international collaboration in genomics and biotechnology. CERN (European Organization for Nuclear Research) is another successful example. CERN is a prime example of international collaboration in particle physics, with scientists from over 100 countries working together on groundbreaking research, including the discovery of the Higgs boson. By implementing these strategies and learning from successful examples, the research community can foster a more connected and collaborative environment that transcends national boundaries.
4.3 Institutions
The distribution of organizations corresponded to the countries/regions, as China and the USA accounted for half of the top 10 organizations. This distribution reflected the global impact of research in this field. As a leading force in the field of ER stress in HCC, China boasted seven of the top 10 institutions in terms of publications. The National Health Research Institutes is ranked the first with the greatest publications. However, Citations and total link strength were relatively low among different institutions, suggesting limited collaboration with other countries/regions and organizations. For enhancing academic impact, it is crucial that greater collaborations and partnerships are fostered with reputable international institutions. Institutions highlighted with purple circles, such as the Chinese Academy of Sciences, Institut National de la Sante et de la Recherche Medicale (inserm), the University of Texas System, Fudan University, National Health Research Institutes, the National Institutes of Health and Nanjing University, exhibited the highest betweenness centrality, indicating their significant contributions to the study of ER stress in HCC. It is recommended that collaboration with these institutions should be enhanced.
4.4 Authors
In addition, we also analyzed influential authors in this field. Table 2 lists the top 10 co-authorship of authors with a minimum publications of 5, which suggests that these influential authors may be potential collaborators in the field of ER stress in HCC. Ih-Jen Su and Wenya Huang are the top 2 authors with the greatest number of publications and citations who are both from National Health Research Institutes. Their research mainly focuses on the molecular mechanism of pre-S mutations and ER stress in HBV tumorigenesis [ 14 , 15 , 16 ]. However, most of the authors do not have strong collaborative relationships, which requires a concerted effort to further promote cooperation and exchanges between different countries/regions and institutions.
Increasing collaboration between researchers and countries is essential for addressing global challenges and advancing knowledge across various fields. There some strategies that may increase the collaboration between researchers and countries. Firstly, we should establish International Research Networks. Create formal networks that connect researchers across borders, focusing on specific themes or disciplines, which can facilitate communication, resource sharing, and joint projects. Secondly, we can establish Collaborative Platforms and Databases. Create shared online platforms where researchers can share data, resources, and findings. This encourages transparency and accessibility. Thirdly, the utilization of technology for remote collaboration enables researchers to work together irrespective of geographic barriers.
4.5 References and keywords
Commonly referenced articles are typically regarded as the most crucial and impactful studies within the discipline. The most highly cited article titled “Activation of the ATF6, XBP1 and grp78 genes in human hepatocellular carcinoma: a possible involvement of the ER stress pathway in hepatocarcinogenesis” written by Masahiro Shuda et al. illustrated that the ATF6 and IRE1-XBP1 systems mediate the ER stress pathway appears to be crucial for the transformation-associated upregulation of the GRP78 gene in HCCs [ 18 ]. In addition, Dai et al. [ 19 ]. demonstrated that p28GANK could protect hepatocellular carcinoma cells from destruction by enhancing the expression of UPR and GRP78, and its mechanism of action mainly involves the p38 MAPK, PI3K/Akt and NF-κB pathways. Further study of p28GANK expression under ERS could help to gain insight into the pathogenesis of hepatocellular carcinoma and provide an important reference for new therapeutic strategies [ 20 ]. Of the top 25 references experiencing the most significant citation bursts, 10 references still exhibited bursts. These 10 articles mainly focused on signaling and the pathogenesis of ER stress in HCC (Fig. 6 ).
Due to the fact that keywords represent the central themes of a research project, an analysis of keyword co-occurrence can pinpoint frequently utilized keywords across various studies [ 21 , 22 ]. This method aids researchers in efficiently understanding prevalent research areas. As shown in Fig. 7 A, keywords “apoptosis” and “autophagy” have a higher frequency of occurrences in early stage. Currently, researches manly focused on inflammation, metabolism, signaling pathways and pathogenesis of ER stress in HCC, which is consistent with the analysis of co-cited references.
Previous studies have found that ER stress can up-regulate mesencephalic astrocyte-derived neurotrophic factor (MANF), which inhibits ERS-induced injury [ 23 , 24 ]. MANF combined with SUMOylated p65 can effectively inhibit the activation of NF-κB, block NF-κB/Snail signaling pathways, and limit the development of hepatic inflammation [ 24 , 25 , 26 , 27 ]. Intracellularly, ERS induces the activation of different signaling pathways, including the CHOP, Caspase-12, and JNK pathways, leading to apoptosis. During ER stress, the protein kinase RNA-like endoplasmic reticulum kinase (PERK) dissociates from Grp78/BiP and is activated by phosphorylation, attenuating protein synthesis. Activation of PERK also promotes transcription of genes associated with cell survival, while increasing the synthesis of the pro-apoptotic factor CHOP. The effects of CHOP include the down-regulation of the anti-apoptotic protein Bcl-2, which alters cellular oxidation and reduction state, thereby contributing to apoptosis of HCC [ 28 , 29 ]. In addition, CHOP also promotes the expression of Growth arrest and DNA damage 45 (GADD45), which triggers apoptosis by blocking protein synthesis [ 30 ]. Taken together, ERS induces apoptosis by activating different pathways, especially CHOP and GADD45, which may be important for HCC treatment. Autophagy is a protective mechanism that promotes the survival of hepatocellular carcinoma cells under severe ERS conditions [ 31 , 32 ]. Researchers have identified Cyclic AMP-responsive element-binding protein H (CREBH) as a major transcriptional regulator of hepatic autophagy, which may play an important role in preventing hepatic lipid accumulation and regulating related metabolic diseases [ 34 ]. In addition, it was found that Atg9b could induce autophagy through LC3 and p62 binding, while the accumulation of p62 might activate NF-κB signaling pathway and induce ROS production, which could lead to death of hepatocellular carcinoma cells [ 34 ]. In addition, Geng et al. [ 35 ]. investigated the mechanism of drug resistance in recurring HCC following liver transplantation and discovered that the IP10 expression was linked to drug resistance in both in vivo and in vitro settings. Over expression of IP10 during chemotherapy enhanced drug resistance in cisplatin-treated HCC cells and facilitated tumor growth through the activation of the ATF6/GRP78 signaling pathway. Additionally, a potential supplemental treatment for enhancing cisplatin sensitivity could involve the use of an IP10-neutralizing antibody. In a separate study, Liu et al. [ 36 ] observed that insulin resistance in HepG2 cells resulted in increased GRP78 expression, triggering the protective UPR signal to activate the PERK-mediated ER stress pathway. This process inhibited the expression and activation of apoptotic proteins, ultimately promoting the survival of liver cancer cells while concurrently inducing resistance to cisplatin and other chemotherapy agents in HCC cells.
4.6 Journals
The co-citation analysis of journals helps to understand the influence and popularity of journals in the academic community and has important benchmark value for researchers and institutions. Of the top 10 co-cited journals, 70% have an IF exceeding 10, and are classified in the Q1 division of the JCR, which includes journals such as Nature, Cell and Science. The Journal of Hepatology, a reputable scholarly publication showcasing recent advancements in molecular research and clinical research of liver disease, is ranked as the most frequently referenced journal. This research offers a direction for researches to promptly and precisely comprehend the evolution of this area, demonstrating that the present focal points in ER stress encompass a range of molecular mechanisms. Although the main goal of medical research is to enhance human health and theoretical research is important, it is essential for these discoveries to be applied in clinical settings. Thus, the emphasis of future investigations should focus on clinical research related to ER stress in HCC.
Recent studies have shown that there is a close relationship between HCC and ER stress. Future research on ER stress and HCC shows great potential, particularly in understanding the intricate molecular mechanisms of ER stress and finding ways to connect these mechanisms with potential drug therapy targets for HCC. The study of ER stress in the context of HCC holds significant promise for uncovering new insights into the development and progression of this deadly cancer. By delving deeper into the molecular intricacies of ER stress and its relationship with HCC, researchers can potentially identify novel therapeutic strategies that target specific pathways involved in the pathogenesis of HCC. This line of research could ultimately lead to the development of more effective and targeted treatments for patients with HCC, offering new hope in the fight against this devastating disease.
5 Limitations
Compared with traditional reviews, bibliometric analysis provides better research focus and trends, and may indicate directions for future research, but it also has certain limitations. Firstly, although the publications coverage of the WoSCC, Pubmed, Scopus and Embase databases is the most complete, some publications from other different databases cannot be retrieved, which may lead to incomplete data collection and result in selection bias. Secondly, this study included only English-language publications, which may have resulted in the exclusion of valuable perspectives from non-English publications. This language bias may limit the expression of certain research findings and perspectives. Thirdly, although this study included publications from before December 31, 2023, the WoSCC, Pubmed, Scopus and Embase are open databases that include new publications every day. Nonetheless, the vast majority of publications have been included in this study, and even if a small amount of new data were to appear, it would not affect the conclusions.
6 Conclusions
Research on ER stress in HCC has continued to grow over the past three decades, with high contributions from China and the USA. Researches are widely distributed around the world, but there is a need for more cooperation between authors and countries. Future research on HCC and ER stress holds great potential. This is particularly true in understanding the molecular pathways of ER stress and how they can be connected to potential drug targets for treating HCC.
Data availability
The raw data supporting the conclusion of this article will be made available by the authors, without undue reservation.
Ito T, Nguyen MH. Perspectives on the underlying etiology of HCC and its effects on treatment outcomes. J Hepatocell Carcinoma. 2023;10:413–28. https://doi.org/10.2147/JHC.S347959 .
Article PubMed PubMed Central Google Scholar
Wang Y, Deng B. Hepatocellular carcinoma: molecular mechanism, targeted therapy, and biomarkers. Cancer Metastasis Rev. 2023;42(3):629–52. https://doi.org/10.1007/s10555-023-10084-4 .
Article PubMed Google Scholar
Asafo-Agyei KO, Samant H. Hepatocellular Carcinoma. StatPearls. St. Petersburg: StatPearls Publishing; 2023.
Google Scholar
Divya S, Ravanan P. Cellular battle against endoplasmic reticulum stress and its adverse effect on health. Life Sci. 2023;323:121705. https://doi.org/10.1016/j.lfs.2023.121705 .
Article CAS PubMed Google Scholar
Wang S, Tan J, Miao Y, et al. Mitochondrial dynamics, mitophagy, and mitochondria-endoplasmic reticulum contact sites crosstalk under hypoxia. Front Cell Dev Biol. 2022;10:848214. https://doi.org/10.3389/fcell.2022.848214 .
Wenzel EM, Elfmark LA, Stenmark H, et al. ER as master regulator of membrane trafficking and organelle function. J Cell Biol. 2022;221(10):e202205135. https://doi.org/10.1083/jcb.202205135 .
Article CAS PubMed PubMed Central Google Scholar
Ajoolabady A, Kaplowitz N, Lebeaupin C, et al. Endoplasmic reticulum stress in liver diseases. Hepatology (Baltimore MD). 2023;77(2):619–39. https://doi.org/10.1002/hep.32562 .
Bonsignore G, Martinotti S, Ranzato E. Endoplasmic reticulum stress and cancer: could unfolded protein response be a druggable target for cancer therapy? Int J Mol Sci. 2023;24(2):1566. https://doi.org/10.3390/ijms24021566 .
Wei J, Fang D. Endoplasmic reticulum stress signaling and the pathogenesis of Hepatocarcinoma. Int J Mol Sci. 2021;22(4):1799. https://doi.org/10.3390/ijms22041799 .
Xu G, Jin B, Xian X, et al. Evolutions in the management of hepatocellular Carcinoma over last 4 decades: an analysis from the 100 most influential articles in the field. Liver Cancer. 2021;10(2):137–50. https://doi.org/10.1159/000513412 .
Roldan-Valadez E, Salazar-Ruiz SY, Ibarra-Contreras R, et al. Current concepts on bibliometrics: a brief review about impact factor, eigenfactor score, CiteScore, SCImago Journal Rank, source-normalised impact per paper, H-index, and alternative metrics. Ir J Med Sci. 2019;188(3):939–51. https://doi.org/10.1007/s11845-018-1936-5 .
Arruda H, Silva ER, Lessa M, et al. VOSviewer and Bibliometrix. J Med Libr Association: JMLA. 2022;110(3):392–5. https://doi.org/10.5195/jmla.2022.1434 .
Article Google Scholar
Shen J, Shen H, Ke L, et al. Knowledge mapping of Immunotherapy for Hepatocellular Carcinoma: a bibliometric study. Front Immunol. 2022;13:815575. https://doi.org/10.3389/fimmu.2022.815575 .
Su IJ, Wang LH, Hsieh WC et al. The emerging role of hepatitis B virus pre-S2 deletion mutant proteins in HBV tumorigenesis. J Biomed Sci. 2014;21(1):98. Published 2014 Oct 15. https://doi.org/10.1186/s12929-014-0098-7
Wang LH, Huang W, Lai MD, Su IJ. Aberrant cyclin A expression and centrosome overduplication induced by hepatitis B virus pre-S2 mutants and its implication in hepatocarcinogenesis. Carcinogenesis. 2012;33(2):466–72. https://doi.org/10.1093/carcin/bgr296 .
Yang JC, Teng CF, Wu HC, et al. Enhanced expression of vascular endothelial growth factor-A in ground glass hepatocytes and its implication in hepatitis B virus hepatocarcinogenesis. Hepatology. 2009;49(6):1962–71. https://doi.org/10.1002/hep.22889 .
Shuda M, Kondoh N, Imazeki N, et al. Activation of the ATF6, XBP1 and grp78 genes in human hepatocellular carcinoma: a possible involvement of the ER stress pathway in hepatocarcinogenesis. J Hepatol. 2003;38(5):605–14. https://doi.org/10.1016/s0168-8278(03)00029-1 .
Dai RY, Chen Y, Fu J, et al. p28GANK inhibits endoplasmic reticulum stress-induced cell death via enhancement of the endoplasmic reticulum adaptive capacity. Cell Res. 2009;19(11):1243–57. https://doi.org/10.1038/cr.2009.104 .
Fu J, Chen Y, Cao J, et al. p28GANK overexpression accelerates hepatocellular carcinoma invasiveness and metastasis via phosphoinositol 3-kinase/AKT/hypoxia-inducible factor-1α pathways. Hepatology (Baltimore MD). 2011;53(1):181–92. https://doi.org/10.1002/hep.24015 .
Jiang S, Liu Y, Zheng H, et al. Evolutionary patterns and research frontiers in neoadjuvant immunotherapy: a bibliometric analysis. Int J Surg. 2023;109(9):2774–83. https://doi.org/10.1097/JS9.0000000000000492 . Published 2023 Sep 1.
Radhakrishnan S, Erbis S, Isaacs JA, et al. Novel keyword co-occurrence network-based methods to foster systematic reviews of scientific literature. PLoS ONE. 2017;12(3):e0172778. https://doi.org/10.1371/journal.pone.0172778 .
Zeng T, Zhou Y, Yu Y, et al. rmMANF prevents sepsis-associated lung injury via inhibiting endoplasmic reticulum stress-induced ferroptosis in mice. Int Immunopharmacol. 2023;114:109608. https://doi.org/10.1016/j.intimp.2022.2023;109608 .
Cheng D, Zhou T, Liu H, et al. MANF inhibits Sjögren’s syndrome salivary gland epithelial cell apoptosis and antigen expression of Ro52/SSA through endoplasmic reticulum stress/autophagy pathway. Int Immunopharmacol. 2023;122:110582. https://doi.org/10.1016/j.intimp.2023.110582 .
Liu J, Wu Z, Han D, et al. Mesencephalic astrocyte-derived neurotrophic factor inhibits Liver Cancer through small ubiquitin-related modifier (SUMO)ylation-Related suppression of NF-κB/Snail signaling pathway and epithelial-mesenchymal transition. Hepatology (Baltimore MD). 2020;71(4):1262–78. https://doi.org/10.1002/hep.30917 .
Wang H, Mi K. Emerging roles of endoplasmic reticulum stress in the cellular plasticity of cancer cells. Front Oncol. 2023. https://doi.org/10.3389/fonc.2023.1110881 . 13, 2023;1110881.
Wu S, Ye S, Lin X, et al. Small hepatitis B virus surface antigen promotes malignant progression of hepatocellular carcinoma via endoplasmic reticulum stress-induced FGF19/JAK2/STAT3 signaling. Cancer Lett. 2021;499:175–87. https://doi.org/10.1016/j.canlet.2020.11.032 .
Jiang C, Zhang C, Dai M, et al. Interplay between SUMO1-related SUMOylation and phosphorylation of p65 promotes hepatocellular carcinoma progression. Biochim et Biophys acta Mol cell Res. 2024;1871(1):119595. https://doi.org/10.1016/j.bbamcr.2023.119595 .
Article CAS Google Scholar
Rozpedek W, Pytel D, Mucha B, et al. The role of the PERK/eIF2α/ATF4/CHOP signaling pathway in Tumor Progression during endoplasmic reticulum stress. Curr Mol Med. 2016;16(6):533–44. https://doi.org/10.2174/1566524016666160523143937 .
Li J, Zhuo JY, Zhou W, et al. Endoplasmic reticulum stress triggers delanzomib-induced apoptosis in HCC cells through the PERK/eIF2α/ATF4/CHOP pathway. Am J Translational Res. 2020;12(6):2875–89.
CAS Google Scholar
Lei Y, Wang S, Ren B, et al. CHOP favors endoplasmic reticulum stress-induced apoptosis in hepatocellular carcinoma cells via inhibition of autophagy. PLoS ONE. 2017;12(8):e0183680. https://doi.org/10.1371/journal.pone.0183680 .
Li Z, Zhang L, Gao M, et al. Retraction note: endoplasmic reticulum stress triggers Xanthoangelol-induced protective autophagy via activation of JNK/c-Jun Axis in hepatocellular carcinoma. J Experimental Clin cancer Research: CR. 2020;39(1):164. https://doi.org/10.1186/s13046-020-01668-x .
Article CAS PubMed Central Google Scholar
Cui J, Liu J, Fan L, et al. A zinc finger family protein, ZNF263, promotes hepatocellular carcinoma resistance to apoptosis via activation of ER stress-dependent autophagy. Translational Oncol. 2020;13(12):100851. https://doi.org/10.1016/j.tranon.2020.100851 .
Kim H, Williams D, Qiu Y, et al. Regulation of hepatic autophagy by stress-sensing transcription factor CREBH. FASEB J Off Publ Federat Am Soc Exp Biol. 2019;33(7):7896–914. https://doi.org/10.1096/fj.201802528R .
Wang N, Tan HY, Li S, et al. Atg9b Deficiency suppresses autophagy and potentiates endoplasmic reticulum stress-associated hepatocyte apoptosis in Hepatocarcinogenesis. Theranostics. 2017;7(8):2325–38. https://doi.org/10.7150/thno.18225 .
Geng W, Lo C-M, Ng KTP, Ling C-C, Qi X, Li C-X, Zhai Y, Liu X-B, Ma Y-Y, Man K. Interferon-gamma inducible protein 10 (IP10) induced cisplatin resistance of HCC after liver transplantation through ER stress signaling pathway. Oncotarget. 2015;6:28042–56.
Liu X, Li L, Li J, Cheng Y, Chen J, Shen M, Zhang S, Wei H. Insulin resistance contributes to multidrug resistance in HepG2 cells via activation of the PERK signaling pathway and upregulation of Bcl-2 and P-gp. Oncol Rep. 2016;35(5):3018–24. https://doi.org/10.3892/or.2016.4632 .
Download references
Acknowledgements
This work was supported by Natural Science Foundation of Gansu Province (23JRRA0975).
Author information
Authors and affiliations.
Department of Hepatopathy, The Second Hospital of Lanzhou University, Lanzhou, Gansu, China
Yaping Zhang
Department of General Surgery, The Second Hospital of Lanzhou University, 82 Cuiyingmen, Linxia Road, Chengguan District, Lanzhou, 730030, Gansu, China
Yinting Tian, Zheyuan Wang, Yawu Zhang & Gennian Wang
You can also search for this author in PubMed Google Scholar
Contributions
GNW: Conception and design of the aticle; YPZ: Data collection and analysis, manuscript writing; YTT: Data collection ; GNW, ZYW and YWZ: Review and editing of the manuscript.All authors reviewed the manuscript.
Corresponding author
Correspondence to Gennian Wang .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary material 3, rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/ .
Reprints and permissions
About this article
Zhang, Y., Tian, Y., Wang, Z. et al. Bibliometric analysis of endoplasmic reticulum stress in hepatocellular carcinoma: trends and future directions. Discov Onc 15 , 481 (2024). https://doi.org/10.1007/s12672-024-01377-3
Download citation
Received : 03 May 2024
Accepted : 20 September 2024
Published : 27 September 2024
DOI : https://doi.org/10.1007/s12672-024-01377-3
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Endoplasmic reticulum
- Bibliometrics
- Research trends
- Hepatocellular carcinoma
- Find a journal
- Publish with us
- Track your research
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
- My Bibliography
- Collections
- Citation manager
Save citation to file
Email citation, add to collections.
- Create a new collection
- Add to an existing collection
Add to My Bibliography
Your saved search, create a file for external citation management software, your rss feed.
- Search in PubMed
- Search in NLM Catalog
- Add to Search
Male circumcision and HIV prevention: current knowledge and future research directions
Affiliation.
- 1 Division of Epidemiology and Biostatistics, University of Illinois, Chicago 60612, USA. [email protected]
- PMID: 11871509
- DOI: 10.1016/S1473-3099(01)00117-7
Over the past decade, numerous epidemiological studies have reported a significant association between lack of male circumcision and risk for HIV infection, leading to recommendations for male circumcision to be added to the armamentarium of effective HIV prevention strategies. We review the epidemiological data from studies that have investigated this association, including ecological, cross-sectional/case-control, and prospective studies. We discuss problematic issues in interpreting the epidemiological data, including the presence of other sexually transmitted infections, age of circumcision, and potential confounders such as religion, cultural practices, and genital hygiene. In addition, we review studies of biological mechanisms by which the presence of the foreskin may increase HIV susceptibility, data on risks associated with the circumcision procedure, and available data on the acceptability and feasibility of introducing male circumcision in societies where it is traditionally not practised. Although the evidence in support of male circumcision as an effective HIV prevention measure is compelling, residual confounding in observational studies cannot be excluded. Taken together with concerns over the potential disinhibiting effect of male circumcision on risk behaviour, and safety of the circumcision procedure, randomised trials of male circumcision to prevent HIV infection are recommended. An individual's choice to undergo male circumcision or a community's decision to promote the practice should be made in the light of the best available scientific evidence. More knowledge is required to assist individuals and communities in making those decisions. We conclude with recommendations for future research.
PubMed Disclaimer
Similar articles
- The association between lack of male circumcision and risk for HIV infection: a review of the epidemiological data. Moses S, Plummer FA, Bradley JE, Ndinya-Achola JO, Nagelkerke NJ, Ronald AR. Moses S, et al. Sex Transm Dis. 1994 Jul-Aug;21(4):201-10. doi: 10.1097/00007435-199407000-00004. Sex Transm Dis. 1994. PMID: 7974070 Review.
- Male circumcision: a role in HIV prevention? de Vincenzi I, Mertens T. de Vincenzi I, et al. AIDS. 1994 Feb;8(2):153-60. AIDS. 1994. PMID: 8043224
- The acceptability of male circumcision to reduce HIV infections in Nyanza Province, Kenya. Bailey RC, Muga R, Poulussen R, Abicht H. Bailey RC, et al. AIDS Care. 2002 Feb;14(1):27-40. doi: 10.1080/09540120220097919. AIDS Care. 2002. PMID: 11798403
- Male circumcision. American Academy of Pediatrics Task Force on Circumcision. American Academy of Pediatrics Task Force on Circumcision. Pediatrics. 2012 Sep;130(3):e756-85. doi: 10.1542/peds.2012-1990. Epub 2012 Aug 27. Pediatrics. 2012. PMID: 22926175
- Male circumcision to reduce the risk of HIV and sexually transmitted infections among men who have sex with men. Templeton DJ, Millett GA, Grulich AE. Templeton DJ, et al. Curr Opin Infect Dis. 2010 Feb;23(1):45-52. doi: 10.1097/QCO.0b013e328334e54d. Curr Opin Infect Dis. 2010. PMID: 19935420 Review.
- Comments by opponents on the British Medical Association's guidance on non-therapeutic male circumcision of children seem one-sided and may undermine public health. Moreton S, Cox G, Sheldon M, Bailis SA, Klausner JD, Morris BJ. Moreton S, et al. World J Clin Pediatr. 2023 Dec 9;12(5):244-262. doi: 10.5409/wjcp.v12.i5.244. eCollection 2023 Dec 9. World J Clin Pediatr. 2023. PMID: 38178933 Free PMC article.
- Factors Associated with Low Uptake of Voluntary Medical Male Circumcision as HIV-Prevention Strategy among Men Aged 18-49 Years from Nyanza District, Rwanda. Nzamwita P, Biracyaza E. Nzamwita P, et al. HIV AIDS (Auckl). 2021 Apr 1;13:377-388. doi: 10.2147/HIV.S301045. eCollection 2021. HIV AIDS (Auckl). 2021. PMID: 33833586 Free PMC article.
- Finding Hidden HIV Clusters to Support Geographic-Oriented HIV Interventions in Kenya. Waruru A, Achia TNO, Tobias JL, Ngʼangʼa J, Mwangi M, Wamicwe J, Zielinski-Gutierrez E, Oluoch T, Muthama E, Tylleskär T. Waruru A, et al. J Acquir Immune Defic Syndr. 2018 Jun 1;78(2):144-154. doi: 10.1097/QAI.0000000000001652. J Acquir Immune Defic Syndr. 2018. PMID: 29474269 Free PMC article.
- The influence of socioeconomic factors on choice of infant male circumcision provider in rural Ghana; a community level population based study. Gyan T, McAuley K, Strobel N, Newton S, Owusu-Agyei S, Edmond K. Gyan T, et al. BMC Pediatr. 2017 Aug 29;17(1):185. doi: 10.1186/s12887-017-0937-2. BMC Pediatr. 2017. PMID: 28851410 Free PMC article.
- CDC's Male Circumcision Recommendations Represent a Key Public Health Measure. Morris BJ, Krieger JN, Klausner JD. Morris BJ, et al. Glob Health Sci Pract. 2017 Mar 28;5(1):15-27. doi: 10.9745/GHSP-D-16-00390. Print 2017 Mar 24. Glob Health Sci Pract. 2017. PMID: 28351877 Free PMC article.
Publication types
- Search in MeSH
Related information
- Cited in Books
LinkOut - more resources
Full text sources.
- Elsevier Science
- MedlinePlus Health Information
Miscellaneous
- NCI CPTAC Assay Portal
- Citation Manager
NCBI Literature Resources
MeSH PMC Bookshelf Disclaimer
The PubMed wordmark and PubMed logo are registered trademarks of the U.S. Department of Health and Human Services (HHS). Unauthorized use of these marks is strictly prohibited.

IMAGES
VIDEO
COMMENTS
This report reviews the current knowledge and future research directions for improving the nation's alert and warning system. It covers topics such as public response, information ecosystem, and research agenda.
This article provides a comprehensive analysis of 81 articles on knowledge hiding in organizations, published in international journals from 2012 to 2020. It identifies the main themes, trends, and gaps of knowledge hiding research, and suggests future directions for scholars.
Current knowledge and future research directions for the monitoring and management of visitors in recreational and protected areas ... P., Stenseke, M., Mossing, A., Liljendahl, H., Laven, D. (2012). Outdoor recreation in change-current knowledge and future challenges. In Proceedings of the 6th international conference on monitoring and ...
Systems: Current Knowledge and Future Research Directions, a report from the National Academies of Sciences, Engineering, and Medicine, explores how a more effective national alert and warning system might be created, identifies some of the gaps in our present knowledge, and sets forth a research agenda to advance the nation's
Trauma informed care in medicine: current knowledge and future research directions Fam Community Health. 2015 Jul-Sep;38(3):216-26. doi: 10.1097/FCH.0000000000000071. Authors Sheela Raja 1 , Memoona Hasnain, Michelle Hoersch, Stephanie Gove-Yin, Chelsea Rajagopalan. Affiliation 1 Department of ...
Definitions, Current Knowledge, and Future Directions Nicholas H. Steneck University of Michigan, Ann Arbor, Michigan, USA ... Current framework for Defining Research Behaviors.
Burnout and Health Review: Current Knowledge and Future Research Directions. Arie Shirom, Arie Shirom. Faculty of Management. Tel Aviv University, PO Box 39010, Ramat Aviv, Tel Aviv 69978, Israel. ... Directions for Future Research. Final Reflections. References. Citing Literature. International Review of Industrial and Organizational ...
This report reviews the current knowledge and future research directions for improving emergency alert and warning systems in the United States. It examines how people respond to alerts and warnings, how new technologies can enhance communication, and what gaps exist in the national system.
The state of loneliness and social isolation research: current knowledge and future directions. Harry Owen Taylor, 1 Thomas K.M. Cudjoe, 2 Feifei Bu, 3 and Michelle H. Lim 4, 5 Author ... There is substantially less research on loneliness and isolation among certain racial/ethnic groups, immigrant communities, diverse gender identities and ...
Current Knowledge and Future Research Directions Article in Family & community health · July 2015 DOI: 10.1097/FCH.0000000000000071 · Source: PubMed CITATIONS 11 READS 756 ... Current Knowledge and Future Research Directions Sheela Raja, PhD; Memoona Hasnain, MD, MHPE, PhD;
to suggest that future research examine if, and under what conditions, burnout would be positively associated with adverse health beha viors, including smoking, lack of exercise, and ex cessive ...
Current knowledge and future research directions for the monitoring and management of visitors in recreational and protected areas. ... Alpine vegetation in the context of climate change: A global review of past research and future directions. 2020, Science of the Total Environment.
This article provides a review of scientific articles addressing the topic of knowledge hiding in organizations. Based on a descriptive analysis, bibliometric analysis, and content analysis of a sample of 81 articles published in the academic journals in the Web of Science from 2012 to 2020, we identify the main areas and current dynamics of knowledge hiding research.
It is suggested that the central research themes of knowledge hiding include five clusters: concept and dimensions, antecedents, consequences, theories, and influence mechanisms, and how cultural and other contextual factors may shape the knowledge hiding behavior. This article provides a review of scientific articles addressing the topic of knowledge hiding in organizations. Based on a ...
Violence and reproductive health: current knowledge and future research directions Matern Child Health J. 2000 Jun;4(2):79-84. doi: 10.1023/a:1009514119423. ... Methods: The current knowledge base for several issues specific to violence and reproductive health, including association of violence with pregnancy, ...
This report reviews the current knowledge and future research directions of emergency alert and warning systems, including their equipment, technology, and effectiveness. It covers topics such as natural hazards, terrorism, public health, and communication challenges.
This editorial reviews the state of loneliness and social isolation research around the world, including knowledge gaps and policy implications. It defines loneliness and social isolation as distinct psychosocial constructs that are associated with poorer health outcomes and discusses the prevalence, measurement, and interventions of these issues.
Pathogenesis of Perianal Fistulising Crohn's Disease: Current Knowledge, Gaps in Understanding, and Future Research Directions J Crohns Colitis. 2023 Jun 16;17(6):1010-1022. doi: 10.1093/ecco-jcc/jjad008. ... At the end, we discussed future directions in basic, translational, and clinical research that may dramatically improve our understanding ...
Over the last 25 years, a small but growing body of research on research behavior has slowly provided a more complete and critical understanding of research practices, particularly in the biomedical and behavioral sciences. The results of this research suggest that some earlier assumptions about irresponsible conduct are not reliable, leading to the conclusion that there is a need to change ...
Implications for clinical practice and future research are discussed in this article. Summary of Suggested Research Directions in TIC Figures - uploaded by Sheela Raja
response to studies showing the benefits of undergraduate research internships and to national calls to engage many more STEM undergraduates in doing research. The purpose of this paper is to summarize the state of knowledge about CURE instruction, including shortcomings in the knowledge base and recommendations for future research and practice.
Transmission routes of African swine fever virus to domestic pigs: current knowledge and future research directions Vet Rec. 2016 Mar 12 ... This will provide an improved scientific basis to optimise current interventions and develop new tools and strategies to reduce the risk of ASFV transmission to domestic pigs.
This paper also examines decision-making models, a knowledge-driven approach, limitations of current implementations, and future research directions. This holistic framework aims to transform fragmented aircraft data into comprehensive, real-time digital representations that can enhance safety, efficiency, and sustainability throughout the ...
It is crucial to reveal the global status, research hotspots and future research trends of ER stress in HCC. The aim of this study is to analyze the publications related to ER stress in HCC through bibliometric analysis in order to better understand the current status of ER stress research in HCC and to identify potential new research directions.
An individual's choice to undergo male circumcision or a community's decision to promote the practice should be made in the light of the best available scientific evidence. More knowledge is required to assist individuals and communities in making those decisions. We conclude with recommendations for future research.